My name is Jacob Waller, I’m a cyber security major at Old Dominion University. Ive recently started my sophomore year. This year my mind is a lot different looking into cyber security instead of thinking of assignment as a con or a stick in the mud, Im going to look at them as an opportunity to grow and really immerse with the problem at hand. I want to become so good at my job that I can recreate a solution in every way fit needed. I want to be able to help my companions as well as help myself. Im a very team oriented individual and I’m very sensible or extroverted some would say. I believe this a skill some may lack in my field which I use as an advantage, what solution can be found if you can’t speak to a person to hear the problem?

Week 1 – Journal Entry
After reviewing the NICE framework and the work role categories in a cyber security setting I now know, work role categories include Oversight and governance(OG), Design and development(DD), Implementation and Operation (IO), Protection and Defense(PD), Investigation(IN). Class Journal entry includes: After reviewing the NICE workforce framework. My preference would be to oversight and govern the whole operation. I believe the leader should be someone who is outgoing and can speak to
his team aiding them on the operation. Another role that strikes my interest is the protection and
defense. They are responsible for looking at different cyber security tools and using them to find
how to mitigate attacks. I’m not a big fan of the design and development, I feel its a very strict
rule that can go south very easily with a lack of information and policies. The NICE framework is
very interesting as a whole. I hope to learn more.
Week 2 – Journal Entry 2
How does the principle of empiricism enhance the effectiveness of cybersecurity practices? Reflect on how empirical data collection and analysis can help identify emerging threats, assess the effectiveness of current security measures, and guide the development of new strategies to protect information systems.
Empiricism is the philosophical approach that involves looking at previous outcomes or
sensory observations and use them as a primary source or knowledge. In cyber security
we do the same thing using real world data to predict or prevent threats such as logs
and incident reports rather than waiting for theoretical assumptions. This can be used to
develop an entirely new defense protocol if used the right way. Threat detection,
vulnerability assessment, incident response and a malware analysis all of these are
uses of empirical data using background knowledge to seize a threat. The world is
already becoming more dangerous behind closed doors, using technology and other
methods with the technology we are more prepared than even to stop a threat.
Week 3 – Journal Entry 3-Visit PrivacyRights.orgLinks to an external site. to see the types of publicly available information about data breaches. How might researchers use this information to study breaches and forecast future data breach trends ? Enter a paragraph in your journal.
A researcher may use the following publicly displayed information for numerous
methods. They use key points such as the privacy rights of the company hacked, the
company size and what was attacked. They then will look for trends using the following
data. Following a trend is often a common solution when trying to find information.
Along with these trends, researchers find patterns within the phishing method which
often leads to the antagonist making a mistake or leaving a footprint as to what software
was used for the attack. Another way researchers may use this information to study
breaches is looking at the humanity side and seeing if anyone had a victim role into
attacking the software.
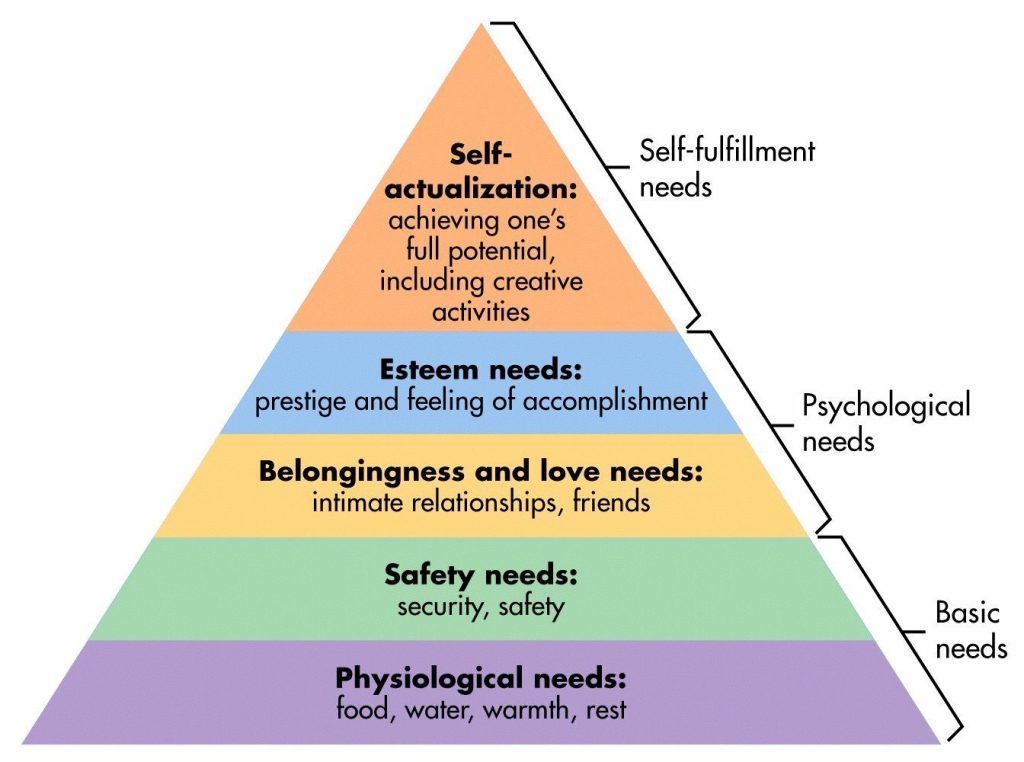
Week 4 – Journal Entry 4-Review Maslow’s Hierarchy of Needs and explain how each level relates to your experiences with technology.
After reviewing Maslow’s hierarchy of needs I believe the way you perceive it depends on the
person’s perspective. Using it in a technological sense a person only needs a source of power,
a screen and whatever information they are trying to display. Those are the actual needs, no
special modifications. That goes at the bottom but someone else may not even think of a basic
need, they may even say they need the most expensive monitor out for all the bells and
whistles. That’s not a need. As for me I believe I would need a good monitor for a basic need for
the games I play because I play high fps shooter. As for the next safety needs, instead of a
basic power strip, I invested in a surge protector.
Week 5 – Journal Entry 5- Rank the motives from 1 to 8 as the motives that you think make the most sense (being 1) to the least sense (being 8).
I rank the following motives from making the most sense to least sense in the order of.
1. Money– I believe putting money has the motive that makes the most sense because that the default for
any criminal in today’s world.
2. Revenge– I believe revenge is a close second to money because we as humans are very selfish people
naturally. When other people make us upset we tend to let our emotions get the best of us except usually when people are in person and more in their right mind knowing not to do something.
3. Political– Political being a motive I believe should be in any criminal background check reviewing a
criminal case. The way the world is, policitics have a lot of power this can be a motive for anyone whos not in the same political party. Even a person who just wants to get back at the “higher ups” of the world.
4. Multiple reasons– I believe this piggy backs off of those who want to “stick it to the man”(Kacy Zurkus.)
5. Recognition- Recognition falls similar to multiple reasons, why commit a crime and then want people to know you did it. Legacy? Fame? What legacy is behind bars, this is why it is so low on the list.
6. Curiosity – Curiosity may be one of the worst reasons to commit a cyber crime but I can see how the Curiosity of the human mind may can play a part in this.
7. Entertainment– Multipl groups who have this motive are often larger, they have become to powerful in a
Hacker world they believe the realworld cant touch them so they begin playing games with their crimes. I would
Infer that a larger hacker group would go for the biggest targets in the world but they dont.
8. Boredom– Boredom is excactly how it sounds, why would you risk you life committing crime out of
boredom. Thats like a millionaire trying out bank robbing for the first time because he wants to know how he can become one. The millionair felt boredom then curiosity because boredom makes no sense. So you must put another label or reason.
Article review #1-social science cybersecurity studies from two different journals in this semester.
Week 6 – Journal Entry 6
For week 6 we watched a YouTube video and wrote about what we thought about the “human firewall.” A security that revolved around social cybersecurity being the first line of defense. Below is my entry about the data we received.
A big risk is being able to run cyber crimes through an AI algorithm. The internet is
global, most hackers are hiked by nation states, they are attacking/defending. Lots of money
involved. After watching the video I believe a Human Fire wall is critical in a cyber security
setting. AI is developing faster than we can imagine. They adapt very quickly to software but
against a human who is trained correctly to see any incorrect information it is no match.
Week 7 – Journal Entry 7
For Journal entry 7 we were instructed to create memes about a human-centered cybersecurity frame work picture.
Explanation relates to Human-centered Cybersecurity: They are all mutually
hacking on their computers, sometimes hacking may require an extra set of eyes from a
coworker.
Photo #13-MEME-”when my friend’s parlay is about to hit so he invites me to watch his
succession”
Explanation relates to Human-centered Cybersecurity: This is another example of
multiple users being on one screen, perhaps to back the other’s technique solving the
conflict.
Photo#12-MEME- ” Me looking at my 3 screen setup after christmas morning(this is
amazing)”
Explanation relates to Human-centered Cybersecurity: This is an example of a
hacker or cyber security worker using 3 screens to review a very large code.
Week 8 – Journal Entry 8- write a journal entry about how you think the media influences our understanding about cybersecurity
I believe social media has revolutionized cyber security forever. With the effect that the media
has influenced simple things in our daily lives that involve cyber security. Instagram, snap chat,
face book and other social media platforms now force the user to make a 2factor security pass
code or method. Hacking is such a common use of social media now, a person can wake up
with their account hacked and now that hacker has all the data of their friends, messages and
pictures. We also see an influence in Artificial intelligence, social media has become so realistic
that Ai is now being used to catfish as important leaders of the world doing illegal things, there
has to be a line that needs to be drawn.
Article Review #2
Cybersecurity Professional Career Paper
Week 9 – Journal Entry 9
For week 9 we were to take a social media usage quiz and analyze our answers based off of the test below.
How did you score? I scored a 1 on the social media disorder scale.
What do you think about the items in the scale?
I don’t think the options are extreme at all. People generally do use social media too much and for the wrong reasons. They think social media is a need. As far as needing to lie to their parents or friends about how much they use it.
Why do you think that different patterns are found across the world?
I think places with less technology will naturally be on social media less. Larger
technological advanced countries will naturally have a large social media usage pattern.
When we think of smaller places with less social media usage we may think of the
middle east countries, versus a larger country like America the usage will be spiked.
Week 10 – Journal Entry 10-
Read this and write a journal entry summarizing your response to the article on social cybersecurity
https://www.sciencedirect.com/science/article/pii/S2451958825000831Links to an external site.
Social cybersecurity is a field centered around human factors. They strive to
protect individuals and organizations from threats emanating from social manipulation
and malicious digital activities. Below are 6 reasons humans are often identified as the
weakest link in cybersecurity.
1.The inherent human struggle with effective risk perception and analysis.
2.The inadequacy of human intuition for processing infrequent events.
3.The perilous overreliance and unwarranted trust people place in computers.
4.The impractical expectation for consistent, intelligent security decisions by
everyone.
5.The frequent origination of security breaches from malicious insiders.
6.The commonplace and seemingly effortless occurrences of security lapses due
to social engineering.
Social cybersecurity merges applied research in computational science with
computational social science techniques to discern, counter, and understand threats
associated with social communication.
Week 10 – Journal Entry 11-Write a paragraph describing social themes that arise in the presentation.
The role of a cybersecurity analyst intersects deeply with social behaviors, revealing
themes of trust, vigilance, and collective responsibility. Cyber security analysts must anticipate
and respond to human tendencies—such as susceptibility to phishing, oversharing on social
media, or neglecting security protocols—that often become entry points for cyber threats. An
example of this would be when you receive an unknown call. Apple’s security will give the option
to turn it to voice mail because calls like this are dangerous. Cybersecurity is not just a technical
challenge but a social one, requiring empathy, communication, and an understanding of human
nature. Human centered cyber security is a very undermined task. A computer cannot defend a
malicious act styled specifically for that computer. We need human analyst to work along side
the computer security, a “human firewall”.
Week 11 – Journal Entry 12-Read this https://dojmt.gov/wp-content/uploads/Glasswasherparts.com_.pdfLinks to an external site. sample breach letter “SAMPLE DATA BREACH NOTIFICATION” and describe how two different economics theories and two different psychological social sciences theories relate to the letter.
The breach letter illustrates how economic theories like Information Asymmetry and
Externalities, and psychological theories like Protection Motivation Theory and Cognitive
Dissonance, help explain consumer and organizational behavior in response to cybersecurity
incidents. PMT explains how individuals respond to threats based on perceived severity,
vulnerability, and efficacy of coping strategies.In the breach letter, the company outlines the
severity of the intrusion (malware accessing payment card data), vulnerability (customers
affected during transactions), and coping strategies (monitoring accounts, replacing
cards). Cognitive Dissonance Theory on the other hand, This theory suggests that
people suggests that people experience discomfort experience discomfort when their
beliefs when their beliefs conflict with new conflict with new information. The economic
theories change the framework completely. Information AsymInformation Asymmetry,
This occurs when one party has when one party has more or better information more or
better information than the other. than the other.
Week 11 – Journal Entry 13
Policy vs. Practice Gap: Many organizations have policies on paper but fail to
enforce them consistently. This disconnect can leave systems vulnerable despite
having a framework in place.
● Adaptability Issues: Cyber threats evolve rapidly, and static policies may become
obsolete. Effective policies must be dynamic and regularly updated.
● Human Factors: Policies often overlook the role of user behavior. Without proper
training and awareness, even the best policies can be undermined by human error.
● Regulatory Pressure: Compliance-driven policies may prioritize checkbox
adherence over actual security outcomes, which can dilute their effectiveness.
Cybersecurity policies are a foundational tool, but their success depends on
implementation, organizational culture, and continuous improvement. The article
likely advocates for a more integrated, proactive approach that aligns
technical controls with human and organizational factors.
Week 12 – Journal Entry 14-Andriy site.Slynchuk.has described eleven things Internet users do that may be illegal. Review what the author says and write a paragraph describing the five most serious violations and why you think those offenses are serious.

Collecting information about people younger than 13 is wrong because it violates child
protection laws like COPPA and exploits the vulnerability of minors who cannot give informed
consent. Similarly, faking your identity online undermines trust, spreads misinformation, and can
lead to fraud or harassment, showing how deception corrodes digital communities. Recording a
VoIP call without consent is also unethical and often illegal, since it disregards privacy rights
and exposes individuals to surveillance without their knowledge. Bullying and trolling, whether
online or offline, cause emotional harm, silence voices, and foster toxic environments that
discourage healthy dialogue. Finally, conducting illegal searches on the internet disregards both
legal boundaries and ethical norms, often leading to exposure of private or restricted information
that was never meant to be accessed. Together, these practices demonstrate how dishonesty,
exploitation, and disregard for privacy erode the safety and integrity of digital life