This is a little About me!
Hello my name is Jason Daamash!
I am a detail-oriented Information Technology professional currently pursuing a Bachelor’s in BS Cybersecurity at Old Dominion University (ODU). Previously, I completed coursework at George Mason University and earned an Associate of Applied Science (AAS) in Information Technology from Northern Virginia Community College (NOVA).
I hold a Google Cybersecurity Certificate (completion in July 2024) and CompTIA Security+ (SY0-701) certification, with expertise in threat detection, risk management, and technical support. My goal is to leverage my skills in IT and cybersecurity to contribute effectively to an organization’s success.
My picture!

Experience
💼 Associate – Friendly Rent-A-Car, VA (Jan 2023 – Present)
Provided excellent customer service and resolved concerns regarding rentals.
Maintained rental records and ensured timely returns.
Addressed basic automotive issues for a smooth rental experience.
Education
🎓 Old Dominion University (ODU), VA – Bachelor’s in Information Technology (Present)
🎓 George Mason University, VA – Completed Coursework in IT
🎓 Northern Virginia Community College (NOVA), VA – Associate of Applied Science (AAS) in Information Technology (2019 – 2021)
🎓 Fairfax High School, VA – High School Diploma (2015 – 2019)
🛡 Certifications
- Google Cybersecurity Certificate (July 2024)
- Expertise in threat detection, risk management, and incident response
- Hands-on experience with cybersecurity tools and best practices
- CompTIA Security+ (SY0-701) (Completed)
- Strong knowledge of network security, cryptography, and risk management
- Proficiency in security controls, penetration testing, and vulnerability assessment
Extracurricular Activities & Interests
- I workout daily. go to the gym and swim actively
- Passionate about problem-solving and troubleshooting technical issues
- Avid learner, always expanding knowledge in cybersecurity and IT trends
Image
Upload an image file, pick one from your media library, or add one with a URL.UploadMedia LibraryInsert from URL



Citations for Images:
BeeSmart City. (n.d.). Cybersecurity social graphic [Image]. BeeSmart City. Retrieved from https://www.beesmart.city/hubfs/04-insights/06-blog-posts-strategy/17-cybersecurity/cybersecurity-social.jpg
Consultants Review. (n.d.). Cybersecurity image [Image]. Consultants Review. Retrieved from https://www.consultantsreview.com/newstransfer/upload/cbi3617165557736704171014806759213472.jpg
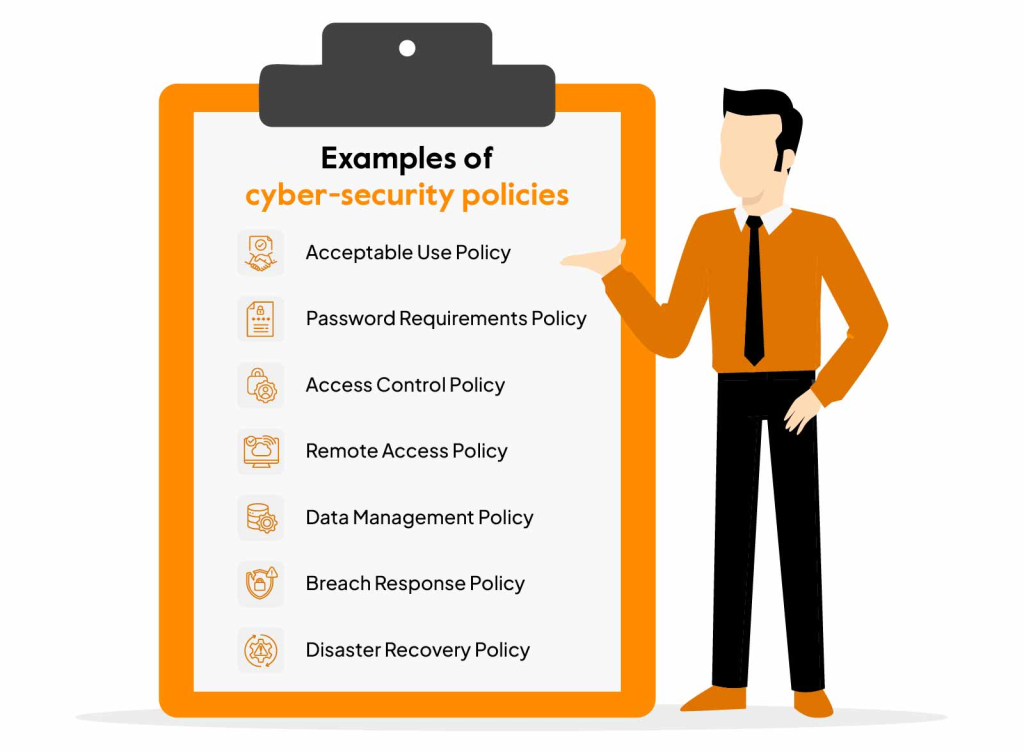
Sprinto. (2023). Examples of cybersecurity policies [Image]. Sprinto. Retrieved from https://sprinto.com/wp-content/uploads/2023/10/Examples-of-cyber-security-policies.jpg
Cyber JIF. (2024). Cybersecurity Awareness Month 2024 poster [Image]. Cyber JIF. Retrieved from https://cyberjif.org/wp-content/uploads/2024/10/Cybersecurity-Awareness-Month-2024-Posters_Page_2-768×1024.jpg
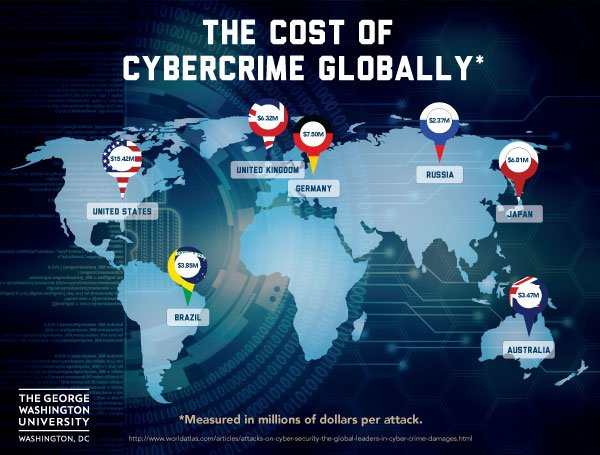
Edcor. (2017). GW University news image [Image]. Edcor. Retrieved from https://www.edcor.com/wp-content/uploads/2017/01/gwuniv-news1.jpg