Journal Entry-Week 1
Q) Review the NICE Workforce Framework. Are there certain areas that you
would want to focus your career on? Explain which areas would appeal
the most to you and which would appeal the least.
A) After reviewing the NICE Framework, it has prepared me to understand the cybersecurity workforce. The structured and organized approach helps individuals navigate specific career paths that categorizes seven high level cybersecurity functions. Now that I have reviewed the seven categories I am most interested in Analysis and Investigation. Being able to analyze cyber threats and intelligence requires a deep understanding of cybersecurity and evolving threats. Analyzing incidents help determine the severity of each potential crime or vulnerability. This is very important as well as effective communication along with writing and reporting skills. Investigating and responding to security incidents is very exciting to me as well. I enjoy problem solving which requires critical thinking skills to find solutions to diverse situations. Oversee and Govern is a category I am least interested in at this moment. This role is less hands on and more administrative to policy and compliance. I would like to showcase my skills and provide a immediate impact. This would allow my employers to see what value I am brining the company. Oversee and Govern in my opinion require a long term strategic planning. I do understand that this role is very important and my opinion is very subjective and varies from person to person
Journal Entry- Week 2
Q) Explain how the principles of science relate to cybersecurity.
A) The principles of science provide a organized and structured approach to difficult problems. It opens a new avenue for making a positive impact on preventing cyber incidents. First, relativism. This principle teaches us that there’s no one size fits all solution. Changes in one system lead to changes in other systems. You must adapt and plan for potential changes to occur. Parsimony, as a rule of thumb try to keep it simple. Make an effort to explain human behavior from a social science perspective as much as possible. Skepticism, creates the urge to question question everything. Ethical neutrality, refers to the ethical standards when conducting research. Working in cybersecurity we must remain ethical and respect the rights and values while safeguarding against cyber threats. Objectivity, is vital in maintaining the integrity and effectiveness of cybersecurity. It refers to make decisions based on concrete evidence rather than personal bias. Emotions will not work in this concept and should be backed by data and analysis. Lastly determinism, is about finding the root cause of security issues. As a science principle it means that behavior is caused, determined, or influenced by preceding events. Determinism in security incidents present a cause or set of causes that require investigation. The aim is to identify what caused the breach.
Journal Entry- Week 3
Q) Visit PrivacyRights.org to see the types of publicly available information
about data breaches. How might researchers use this information to
study breaches? Enter a paragraph in your journal.
A) This website provides a wealth of information on the several legislation and privacy rules. To check for correctness and understand the variations in each state’s policies, the data may be seen by state. This website also offers a substantial number of statistics and information about historical data breaches that have happened throughout the years. Researchers can develop future action plans with the aid of the recording of past studies and cyber occurrences. Researchers can learn how to manage problems or how not to handle them by understanding how past breaches occurred. Researchers may do studies on data breaches in a good manner by learning from earlier studies and research that has been done. The website also provides a ton of advice and makes an effort to teach visitors to lessen the possibility of breaches. Overall, this website provides a researcher with a more efficient means of learning about breaches.
Journal Entry- Week 4
Q) Review Maslow’s Hierarchy of Needs and explain how each level
relates to your experiences with technology. Give specific examples of
how your digital experiences relate to each level of need.
A) Maslow’s hierarchy of needs is a psychological motivational theory that consists of a five-tier model of human wants, which is commonly shown as hierarchical tiers within a pyramid Needs . Individuals at the bottom of the hierarchy must be satisfied before they can attend to needs at the top.
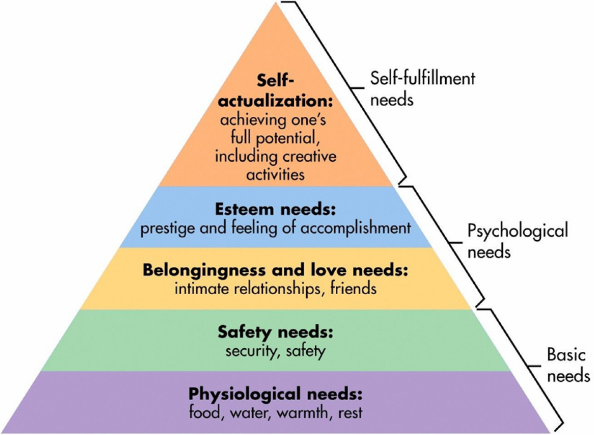
Physiological– For a person to survive, they need to have access to things like air, food, water, shelter, and sleep. If these requirements are not satisfied, the human body cannot perform at its best. According to Maslow, physiological requirements come first since, unless they are met, all other wants are secondary.
Many individuals believe that food, air, and water are less vital than technology.
Safety needs– When I was younger, one of my passwords had been stolen or someone other than me had tried to get into one of my accounts. At this time, I was concerned about my personal security of my social media accounts.
Belongingness and love needs– Belongingness is the term used to describe a human emotional need for social relationships, affiliation, togetherness, and group membership. Examples of belongingness requirements include friendship, closeness, trust, and acceptance, as well as receiving and giving love and affection. I can communicate with my loved ones and friends more effectively thanks to technology. figuring out a method to improve my relationship with the individuals in my life who are not in close proximity to me.
Esteem needs– With the rise of social media, I began to judge my worth by how I thought I was perceived online. This had both positive and bad effects on my self-esteem. worrying about the number of likes a photo received or my lack of following. Maslow’s hierarchy has four levels, with self-worth, success, and respect making up the fourth level. Maslow classified esteem requirements into two categories: esteem for others (reputation or respect) (e.g., position, prestige) and esteem for oneself (dignity, success, mastery, independence).
Self-actualization needs– Self-actualization is the pursuit of one’s own personal development, creativity, and potential. Numerous options for self-actualization are made available through technology. Technology has made it possible for me to self-teach, which has greatly aided me in developing new hobbies and skill sets via trial and error.
Journal Entry- Week 5
Q) Review the articles linked with each individual motive. Rank the motives from 1 to 7 as the motives that you think make the most sense (being 1) to the least sense (being 7). Explain why you rank each
motive the way you rank it.
A) Money- Due to the profitability of cybercrime, money and financial gain are the main driving forces in cybersecurity. To swiftly profit from their acts, cybercriminals target valuable resources like financial data and personal information. The expansion of the digital economy and recent technology developments present fresh chances for illegal financial gain.
Entertainment- I think for a variety of people looking for excitement, curiosity-driven research, experimentation, and even mischief, entertainment may be a cybersecurity motivator. Some people find hacking to be an enjoyable activity because of the obstacles and adrenaline rush it offers.
Revenge-Within the field of cybersecurity, revenge porn, a damaging and unlawful activity, is motivated by personal vengeance. To cause their victims mental distress and damage to their reputations, perpetrators utilize graphic photographs or videos of people without getting their permission. This evil deed frequently entails the unlawful dissemination of private information in vengeance against a person the offender has had a personal contact with.
Recognition-Recognition is a driving force in cybersecurity because some hackers want recognition for their technological prowess and achievements. They take part in high-profile cyberattacks or data breaches to garner recognition from other hackers.
Multiple reasons-The article emphasizes that a variety of motivations, not only financial gain, motivate cybercriminals. These reasons include socioeconomic factors, technological know-how, and psychological factors like ego and retaliation. It demonstrates how money, fame, and the challenge of overthrowing existing systems are allures for many hackers. The research also implies that understanding these motives may help in identifying cybercriminals and could even make it easier for certain people to go from being cybercriminals to ethical hackers. In summary, personal, monetary, and psychological motivations play a complicated interplay in the motivations of cybercriminals, underscoring the need of comprehending these drives in order to successfully battle cybercrime.
Boredom- Boredom is identified as a factor, particularly in the context of children and teenagers, that might indirectly encourage hackers. Boredom might cause kids to look for alternate forms of entertainment online when they have access to digital devices and the internet, which could include participating in harmful activities. According to the report, boredom makes kids more susceptible to these online risks and makes them more prone to act in ways that endanger their online security.
Journal Entry- Week 6
Q) Can you spot three fake websites and compare the three fake websites to three real websites, plus showcase what makes the fake websites fake?
A) Examining a number of essential factors is necessary to spot fake websites. First, check the domain name and URL of the website for typos or dubious versions. Next, evaluate the website’s design, keeping an eye out for indications of professionalism or a lack thereof, such as blurry photographs or uneven typefaces. Thirdly, look for contact information, as fake websites sometimes lack it or give ambiguous information. Last but not least, keep an eye out for errors in grammar and spelling in the information and avoid deals that appear too good to be true because reputable websites usually keep prices reasonable. By taking them into account, people may more easily tell real websites from fake ones and safeguard themselves from possible online frauds.
https://web.archive.org/web/20050224090555/http://www.martinlutherking.org/
https://zapatopi.net/treeoctopus/
https://www.househippofoundation.org/
Journal Entry- Week 7
Q) Review the following ten photos through a cybersecurity human systems integration framework.
Create a meme explaining what is going on in the individual’s or individuals’ mind(s).
A) The dog is a metaphor for someone studying cybersecurity in front of a computer, protecting their precious item, a bone. It hilariously portrays the concept that people are ready to educate themselves about protecting their digital possessions just as much as their physical ones.

Journal Entry- Week 8
Q) Watch this video and pay attention to the way that movies distort hackers.
A) Hackers and their powers are frequently distorted in films. Movies then inflate certain characteristics of hackers, such as the speed with which anything may be hacked. In most movies, it appears that you can hack something or understand code in minutes. When combing through the code or hacking into anything would take a long time. Another thing that movies do is manufacture products that do not exist in real life, giving the impression that hackers have such skills. In general, movies exaggerate a hacker’s ability. Films make it appear like expert hackers may easily gain access to everything they desire. This promotes the idea that no one is truly safe or secure when using the internet.
Journal Entry- Week 9
Q) Complete the Social Media Disorder scale. How did you score? What do you think about the items in the scale? Why do you think that different patterns are found across the world?
A)
Journal Entry- Week 10
Q) Read this and write a journal entry summarizing your response to the article on social cybersecurity
https://www.armyupress.army.mil/Journals/Military-Review/English-Edition-Archives/Mar-Apr-2019/117-Cybersecurity/b/
A) The article explores social cybersecurity, a new topic of national security that focuses on how technology is used to affect human behavior and society. It illustrates how this is becoming a critical feature of combat, with a focus on information manipulation in particular. The employment of information warfare methods by Russia is used to demonstrate the impact of utilizing technology to sow strife among civilizations. The BEND model is introduced in this article to describe several methods in which information and networks are exploited in the cyber realm. It also emphasizes the significance of bots as automated means for disseminating information, both good and negative. The susceptibility of open societies to such manipulation, as well as the necessity for legislation and education to overcome these difficulties, are explored.
Journal Entry- Week 11
Q) A later module addresses cybersecurity policy through a social science framework. At this point, attention can be drawn to one type of policy, known as bug bounty policies. These policies pay individuals for identifying vulnerabilities in a company’s cyber infrastructure. To identify the vulnerabilities, ethical hackers are invited to try explore the cyber infrastructure using their penetration testing skills. The policies relate to economics in that they are based on cost/benefits principles. Read this article https://academic.oup.com/cybersecurity/article/7/1/tyab007/6168453?login=true and write a summary reaction to the use of the policies in your journal. Focus primarily on the literature review and the
discussion of the findings.
A) The article delves at bug bounty programs in the context of cybersecurity, which is paying individuals, generally ethical hackers, to find flaws in a company’s digital systems. The policies are based on cost/benefit concepts and allow ethical hackers to examine a company’s cyber infrastructure using their penetration testing expertise. The review of the literature dives into current studies on bug bounty schemes, sheds light on their evolution and usefulness. The results discussion delves into different facets of bug bounty policies, such as their influence on vulnerability discovery, the importance of monetary prizes, and the ethical concerns involved.
Journal Entry- Week 12
Q) Andriy Slynchuk has described eleven things Internet users do that may be illegal. Review what the author says and write a paragraph describing the five most serious violations and why you think those offenses are serious.
A) Andriy Slynchuk illuminates eleven potentially criminal behaviors that internet users may unknowingly engage in. The five most serious infractions entail breaking into another person’s computer, publishing copyrighted content without permission, spreading malware, engaging in identity theft, and engaging in online harassment. These acts are extremely serious since they directly violate personal privacy, violate intellectual property rights, and endanger online safety. The concept of someone invading my personal space by hacking or distributing malware feels extremely intrusive, and the prospect of becoming a victim of identity theft is quite terrifying. Furthermore, the emotional toll of online harassment is something that affects individuals, stressing the critical necessity for responsible and courteous behavior.
Journal Entry- Week 14
Q) Digital Forensics | Davin Teo | TEDxHongKongSalon – YouTube Watch this video and think about how the career of digital forensics investigators relate to the social sciences. Write a journal entry describing what you think about the speaker’s pathway to his career.
A) I was impressed by the unorthodox nature of Davin Teo’s career path after seeing his TEDxHongKongSalon lecture on Digital Forensics. Teo’s path into digital forensics appears to be a break from standard professional paths. It’s fascinating to see how he combines technical skill with a profound grasp of human behavior. Teo’s journey, in contrast to more traditional career routes, demonstrates the unexpected union of computer technology and social sciences, demonstrating the changing nature of professions in the digital era. His story emphasizes the significance of not only technological abilities but also a keen understanding of the social milieu around cybercrime. This one-of-a-kind combination of skills defies the idea of fixed professional boundaries and illustrates the necessity for a multidisciplinary approach to managing the complexity of digital investigations.