Cybersecurity, Technology, and Society
Students in IT/CYSE 200T will explore how technology is related to cybersecurity from an interdisciplinary orientation. Attention is given to the way that technologically-driven cybersecurity issues are connected to cultural, political, legal, ethical, and business domains. The learning outcomes for this course are as follows:
- Describe how cyber technology creates opportunities for criminal behavior,
- Identify how cultural beliefs interact with technology to impact cybersecurity strategies,
- Understand and describe how the components, mechanisms, and functions of cyber systems produce security concerns,
- Discuss the impact that cyber technology has on individuals’ experiences with crime and victimization,
- Understand and describe ethical dilemmas, both intended and unintended, that cybersecurity efforts, produce for individuals, nations, societies, and the environment,
- Describe the costs and benefits of producing secure cyber technologies,
- Understand and describe the global nature of cybersecurity and the way that cybersecurity efforts have produced and inhibited global changes,
- Describe the role of cybersecurity in defining definitions of appropriate an inappropriate behavior,
- Describe how cybersecurity produces ideas of progress and modernism.
Course Material
Open Access materials will be used for the course. The books include:
- Floridi, L. (2015). The Onlife Manifesto: Being Human in a Hyperconnected Era. Springer-Verlag GmbH. https://link.springer.com/book/10.1007%2F978-3-319-04093-6.
- Van Ommeren, E., Borrett M., & Kuivenhoven, M. (2014). Staying Ahead in the Cyber Security Game. Sogeti. https://www.ict-books.com/topics/cyber-security-pdf-info.
- Readings include additional articles from open access journals and government reports
Discussion Posts
Using the article 50 Cybersecurity Titles That Every Job Seeker Should Know AboutLinks to an external site., research two or more of these jobs that are of interest to you. What disciplines do you see represented in these 50 jobs? What skills are required for the two jobs you selected? What was your biggest surprise? Be sure to include links to your research.
Initial Post
The two jobs I selected that interested me were penetration tester or pen tester and security auditor. The field that I am most interested in is penetration testing. The discipline requires understanding how an attacker might feel and act to find vulnerabilities in a system. They would need to understand and be able to utilize reconnaissance tools, vulnerability scanners, proxy tools, exploitation tools, and post-exploitation tools. The biggest surprise I found about pen testers is the number of different categories of vulnerabilities out there some examples include; web apps, mobile apps, the cloud, embedded devices/ IoT (Internet of Things), and more. The second career I selected was security auditor. A security auditor needs skills in overall cybersecurity, penetration testing, and policy development. The thing I found most interesting about selecting the security auditor second was that it included my first choice as a skill set to learn first. I think this would be a very interesting thing to work towards once I feel I have gained a good deal of knowledge about penetration testing and carrying out various types of tests.
https://www.synopsys.com/glossary/what-is-penetration-testing.htmlLinks to an external site.
https://www.cyberdegrees.org/jobs/security-auditor/Links to an external site.
Response 1
I selected a security auditor as well. In the research I completed I found that it probably would include some hands-on experience to follow this career path. Many companies would want to see a demonstration of your knowledge and abilities in your work history. It would be difficult to audit a company’s security policy without knowledge, understanding, and experience of vulnerabilities and attacks. Most companies would want to know they are getting a quality assessment. I don’t think all of the jobs in the posted article are appropriate for people fresh out of school with no prior experience. However, entry-level in a field that requires a lot of knowledge isn’t a bad thing either. It shows there are lots of things to know and ways to grow.
Response 2
I almost selected a vulnerability accessor to research and write about. I agree that this discipline would require a lot of technical knowledge. It seems to me like it would require some of the same knowledge as my first choice a penetration tester. If someone is going to break into a computer system they would have to know where the vulnerabilities are that will allow them in. I would think that both disciplines need knowledge about vulnerability scanners and exploitation software. From reading the article that you used as a source I believe the biggest difference between penetration testing and a vulnerability scanner is pen testers attempt to break into a system undetected to find holes and exploits while a vulnerability accessor looks for vulnerabilities from within a system. I would wager that both have their pros and cons in helping companies find weaknesses in their systems.
From your readings of pages 1 – 21 of the NIST Cybersecurity Framework Links to an external site., what benefit can organizations gain from using this framework, and how would you use it at your future workplace?
Initial Post
The top benefit that all organizations can gain from the NIST Framework is its flexibility. Despite this document’s creation was developed to advance the cybersecurity risk management of the structure of various organizations it can be used by any organization from any background. This flexibility allows organizations with a variety of risks to adopt and implement safeguards that may have been previously overlooked regardless of their discipline. Another benefit that organizations can gain from the utilization of the Framework is that it is completely voluntary and organizations can adopt as much or as little as they need for their best possible outcome. This allows organizations to weigh the pros and cons of adopting certain aspects of the Framework based on the cost and likely outcomes. This flexibility in adoption in how it can benefit organizations in creating security policies to ensure they get the most benefit for their needs.
Response
I too think it’s a great benefit that organizations can adopt different aspects of the NIST Framework into their existing foundations. The Framework was created to complement not replace the already existing risk management process of an organization. The Framework breaks down the various topics of risk so organizations can identify opportunities for improvement and security. The implementation tiers help provide some conditions that allow organizations to assess their level of risk, levels of countermeasures, and structures that are needed to protect against threats without becoming too cost-prohibitive.
In this discussion board, you are the CISO for a publicly traded company. What protections would you implement to ensure availability of your systems (and why)?
Initial Post
Availability is a core pillar of the cybersecurity CIA triad making it a crucial factor in keeping organizations running. Some mitigating measures that I would take as CISO of an organization to protect IT availability are using IDS (intrusion detection software), strong authentication, using antivirus software, creating a DRP (disaster recovery plan) and keeping software up to date and patched. IDS helps monitor a network and alerts IT if anything unusual or suspicious is detected on the system. Using this software can be the first notification of a potential attack. If the organization is made aware when an attack is being launched it can sometimes stop the intrusion before too much damage is done, potentially preserving availability. Using strong authentication like multi-factor can help prevent intruders from gaining access to a network through incidents such as a brute force or a dictionary attack. It is much harder for cyber criminals to break into a system if they must overcome multiple levels of security safeguards. When hackers are able to break into systems it can challenge availability if they upload malicious code, change important sections of code, or change who is authorized to access the network. Using antivirus software is a real-time solution to preserve availability by scanning all information that is being transmitted for known virus signatures. This software can stop viruses before they can do damage. A DRP is crucial to keep businesses running when the unexpected happens. Without a DRP a disaster could leave the infrastructure of an organization in complete chaos because people could potentially be working against each other making it impossible to bring availability back. Ensuring regular updating and patching helps prevent breakdowns when vulnerabilities are identified. If organizations fail to update and patch known vulnerabilities, attackers may take advantage of those weaknesses infiltrating a system and compromise its availability. There are many more activities that should be considered for sustainable availability like company wide IT training on cybersecurity, building solid security policies, protecting the physical location and infrastructure of host servers, risk assessment, data back-ups, etc… Continuously monitoring and reassessing the security of an organization is a never ending process since new vulnerabilities and attacks are constantly being realized, making it perpetual work that is never finished.
Response 1
I liked how you started with the NIST’s Framework. This is a terrific tool to use when deciding how to build your companies security policy to foster availability. The framework is adaptable to just about any business and offers flexibility, suggestions, and ideas for key areas that could be overlooked. Your second point is great too, highlighting the need for a defense-in-depth. Using multiple security measures that is structured layer by layer will help protect a companies availability by requiring attackers to break through each mitigating factor to do damage.
Response 2
Redundancies are a terrific way to ensure continued availability. Keeping data backed-up is crucial when dealing with challenges like disasters, attacks, and ransomware. Other redundancies would also benefit organizations to prevent downtime like power back-ups and alternative command centers. If there is a power failure having back-up energy will keep servers running through the disruption. Having an alternate command center will allow for operations to continue through potential disasters.
Discussion Board: Ethical Considerations of CRISPR Gene Editing
Based on your readings related to the BioCybersecurity section of this course, identify possible ethical considerations and explain your position.
Initial Post
The concept that malicious code can be written to a sequence of DNA and uploaded and infect a PCR computer that reads it is an example of how cyber vulnerabilities are spreading out from their original discipline in computer science and affecting our whole society in many interdisciplinary ways. The CRISPR gene editing tool is opening up opportunities for new innovative ways to promote life and cure illness, while at the same time opening up new vulnerabilities and threats in biomedical medicine and beyond. DNA could be partially understood as code that is written for how biological machines run and work. Like computer code DNA could be written to help people or hurt them. DNA could be manipulated with CRISPR to cause destruction in many unthought of ways. If it was coded like a logic bomb it could be embedded in something’s genetic make-up and when specific conditions are met it could kill the host or launch an infection that could spread to other hosts. DNA could be coded to destroy specific types of molecules eroding specific materials that people use and rely on. It could also be manipulated in microorganisms that take the first steps in setting off an ecological collapse by using up resources that are a necessity for an entire ecological web of organisms. The possibilities for how gene editing can offer new life saving and preserving technologies will likely be countered with malicious and devastating inventions through accidents or threats created by attackers. These threats and vulnerabilities are similar to the challenges faced by computers and computer systems which will be a challenge in securing the future.
Response 1
I agree that there is a divide on gene editing. However, I believe it goes farther than just ethics. I think there is an even larger divide in understanding the basics of the technology. If people don’t understand the basics of how a technology works how will they be able to understand if it is ethical. I was reading an article today about how the Supreme Court of Alabama just ruled that embryos are people and when asked about this ruling and how it will affect Invitro Fertilization (IVF) the Alabama Senator Tommy Tuberville didn’t understand what IVF had to do with embryos. If our lawmakers are having trouble understanding the basics of a technology that helps people who are challenged conceiving children than how will we be able to depend on legislation that dictates how a complicated tool like CRISPR is used, which allows for the rewriting of gene sequences. Depending on how technologies are pitched to lawmakers it could create a major ethical dilemma for all of society. This is only looking at it from an American perspective, but how about these ethical questions that are being answered by the other 194ish countries in the world. What will the ramifications of their decisions be for us?
Response 2
I agree that there are ethical implications of using CRISPR to change the genetic make-up of unborn babies through lack of consent, possible religious implications, and the potential disenfranchisement of marginalized communities. However, I wonder if the focus on CRISPR with designer babies instead of all the other instances of how biology affects our world is overlooked. All living things in the world have DNA even viruses which aren’t considered living. If any of that DNA can be rewritten however the designer wants what are all of the other implications that could be a threat to our world. One of the assigned readings showed how CRISPR created a computer virus written in DNA that infected the computer that translated it. This shows how the ethical questions go above and beyond just biological ethics.
In the end of your discussion post you mentioned food crops, great point. People have been manipulating genes for centuries now, however, using tools like CRISPR for much shorter period of time. These manipulations have been geared to increase crops sizes, yields, and to ensure sustainable food sources. Companies are now manipulating genetics by coding plants to make their own pesticides. These genetic manipulations through breeding and technology have created their own ethical dilemmas. For example monocropping has removed a lot of the genetic biodiversity that was at once abundant in nature. Now as new diseases emerge their isn’t the same level of biodiversity that would allow these species to survive and thrive. If CRISPR were used maliciously could it cause crop failure or famine?
The “Short Arm” of Predictive Knowledge
From this week’s Jonas Reading: How should we approach the development of cyber-policy and infrastructure given the “short arm” of predictive knowledge?
Initial Post
The creation of cyber-policy and infrastructure should be developed using a predictive perspective through the lens of philosophical understanding of what possible consequences could result from new technologies and innovations to help determine what the ramifications are for society, culture, and the environment. There was a shift in history where the effects that people had on the world changed from only affecting human interaction to affecting nature itself. A good example that Professor Wittkower raised in his lecture was the unthought-of challenges that arose out of the Industrial Revolution. The technological changes that took place during that time drastically changed the effect people had on their food sources, the ways people lived and interacted with each other, how ecology functioned, and how the environment existed. The predictive ramifications of new innovations are still seldom studied before being made available to the general public. These questions are crucial in understanding what challenges and implications that could result. Cyber-policy and infrastructure would benefit immensely from studying these potential outcomes possibly contributing to the prevention of natural disasters, political conflict, organism population crashes, and deleterious living conditions.
Response 1
Great post covering the many ways that cyber technologies should be studied and discussed during the process of policy creation. Including stakeholders, technologists, ethicists, policymakers, and the public will provide helpful dialog when working through potential implications and unforeseen outcomes. Including education and development in this policy will help spread some introspective awareness that could help provide continuous predictive monitoring from the whole organization. Another idea that could be paired with education in the security policy that could promote predictive knowledge is including a good ideas program. Organizations that empower employees to offer suggestions about ways to improve policy and increase positive outcomes could increase their ability to prevent unwanted results.
Response 2
Good post! You referred to looking at the broader implications instead of just mitigating against immediate and apparent security concerns. Your suggestion of remaining flexible and studying the broader scope of topics that intersect with cyber technology like ethics and sociology is key to predictive prevention of unforeseen outcomes. It is common for organizations to only view cyber policy creation through the lens of computer and data sciences, however, this is short-cited when being compared and contrasted with the “short arm” of predictive knowledge. Studying philosophical questions that relate to the implementation of policy could broaden the scope of mitigation and security that organizations use for protection and foresight.
Assignments
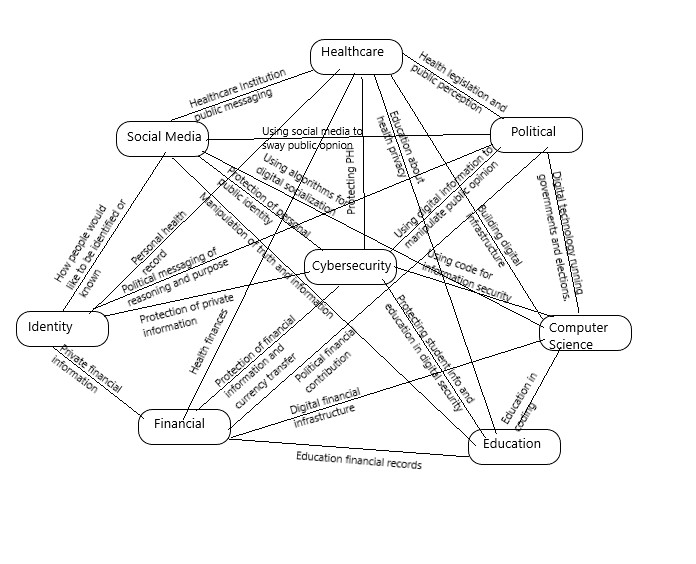
Cybersecurity Interdisciplinary Concept Map
Article Write-Ups
Using the Chai Article (Links to an external site.), along with additional research you will conduct on your own, describe the CIA Triad, and the differences between Authentication & Authorization, including an example.
Adam C. Haas
1/23/2024
CYSE 200T
26759
Understanding the CIA Security Triad
Introduction
Organizations that want information security for their operations should, at a minimum, ensure their system meets the CIA security triad by keeping their information confidential, establishing integrity, and being available when requested. One of the key ways to ensure this is completed correctly is by requiring authentication and authorization. Organizations that implement safeguards to their information boost consumer confidence and help make sure their systems are functioning as intended.
Confidentiality
Confidentiality is one part of the triad and is paramount to ensuring that sensitive information is only available to those that have been approved. It certifies that data is accessed by only those who are authorized to do so (Kim and Solomon 2018, pp. 14–128). Chai (n.d.), writing about the CIA Triad, lists some good examples of ways to keep information private: data encryption, user ids, passwords, two-factor authentication, biometric verification, and security tokens. Organizations need to know they can trust that their systems won’t reveal private information that could have unintended consequences for their mission.
Integrity
Integrity is another part of the security triad that requires keeping data safe and unchanged. Like Kim and Solomon (2018, pp. 14–128) explain, it is ensuring that data is accurate and valid. Organizations need to be able to certify that their information hasn’t been tampered with. Chai (n.d.) gives some great examples of this including: checksums, identity verification, back-ups, and digital signatures as ways to ensure non-repudiation of their data. Organizations’ reliance on accurate data is important to ensure honesty and truthfulness.
Availability
Availability is the final third of the triad ensuring information is attainable when needed. Users need to be able to access data confidently when there is a need. Kim and Solomon (2018, pp. 14–128) hold that availability is expressed when data and systems are accessible and achievable. According to Chai (n.d.), there are different ways to accomplish this. Some examples include maintaining hardware, keeping software free of issues, providing sufficient bandwidth, redundancy, and a robust disaster recovery plan. Having systems and data available is a core need for function and success of an organization. Most businesses rely heavily on digital operations for many of their functions. A break in availability could inhibit or halt productivity.
Authentication Versus Authorization
The CIA security triad is fortified by two key functions of an organization: authentication and authorization. These two functions are closely entwined to make sure only the correct people have access to information systems. Kim and Solomon (2018, pp. 14–128) share that authentication is proving a user is who they say they are and authorization is the operation of giving access to an organization’s data and systems. Examples of authentication are passwords, tokens, or biometric readings. Examples of authorization are access control lists, physical access control, connection and access policy filters, and network traffic filters. To keep information systems secure, users must be able to show they are authentically who they say they are and that they have been authorized by the organization for entry into their systems and data.
Conclusion
The CIA triad is the foundation of information security within an organization. This is represented through the protection of information by keeping data confidential, non-repudiated, and available. These three aspects of the security triad are the bases for forming a complete and functioning security policy and rely heavily on authorization and authentication to confirm users have been given permission and they are who they say they are. Digital information is one of the major drivers of our culture making data security a top concern.
References
Chai, W. (n.d.). What is the CIA Triad? | Definition from TechTarget. WhatIs. Retrieved January 23, 2024, from http://www.techtarget.com/whatis/definition/Confidentiality-integrity-and-availability-CIA?
Kim, D., & Solomon, M. (2018). Fundamentals of information systems security (3rd ed., pp. 14–128). Jones & Bartlett Learning.
In this write-up you will use the SCADA Systems Links to an external site. article, along with your own research, to explain the vulnerabilities associated with critical infrastructure systems, and the role SCADA applications play in mitigating these risks.
Understanding SCADA Vulnerabilities
By Adam Haas
Professor Kirkpatrick
Introduction
SCADA (supervisory control and data acquisition) are systems that facilitate utilities like water supply, wind farms, fuel pipelines, wastewater treatment, transportation equipment, and electricity. These systems are centralized and monitor the control of operations of entire sites. SCADA has evolved from isolated standalone equipment to advanced integrated networked systems. This evolution has opened vulnerabilities to infrastructure from cyber threats creating challenges that could cause major utility supply crises. These vulnerabilities require mitigation and protection through stronger security and policy to uphold system integrity and availability.
History
SCADA has evolved over three generational iterations from its original isolated infrastructure to a complex, interconnected network that operates on the World Wide Web. The first generation was monolithic meaning it was a standalone computer system that wasn’t able to connect with other computers or systems. The second generation was more distributed because it could connect with other computers on a local area network. This generation allowed for the cost and size of computers that operated this system to shrink since it was interconnected with other computers allowing for cheaper and better functionality. Finally, the third and current generation is the networked generation that operates across the internet through a wide area network (SCADA Systems, n.d.). The current generation is the most distributed and most vulnerable due to its widespread interconnectedness and many components. With each iteration, new vulnerabilities have emerged requiring new and stronger security practices.
SCADA Mechanisms
These systems have several components that allow for normal operations of the utilities and interactions with its operators and users. SCADA consists of hardware that allows for supervisory control, data acquisition, data exchange, and data storage. The supervisory controls are composed of an HMI (human-machine interface) which allows operators to interact with it to provide diagnostic information, management of the components, logistical information, machine operations, procedures, and help with troubleshooting (SCADA Systems, n.d.). The data that these systems use is acquired from a PLC (programmable logic controller) and RTUs (remote terminal units). The PLC is a device that operates the decision-making, usually on the local level, continuously monitoring and controlling physical processes. The RTUs are similar, smaller devices that operate in the field and communicate with a core system. Both devices act as interfaces between the SCADA system and the physical utilities they interact with. Data exchange is the collection of communication protocols used for communication of the system with its components. Data storage is the location and device that holds and records data computed by SCADA (Alanazi et al., 2022). The many different parts and components of SCADA each have their own challenges and vulnerabilities that need to be consistently monitored and assessed to ensure continuous fluid operation.
SCADA Vulnerabilities
SCADA is continuously and increasingly faced with threats as technology development has more people and devices progressively interdependent and interconnected. These structures monitor and control physical utilities such as water, fuel, traffic regulation, and electricity. Security breaches of SCADA can have catastrophic effects on the basic functions of communities if they disrupt these critical services. The two most common types of malicious threats that plague these systems are inappropriate access to software and improper access to packet transmissions (SCADA Systems, n.d.). Inappropriate access to the software can be a vulnerability if encryption isn’t used or has insufficient strength, the use of weak passwords, injection of malware into the system, pernicious changes to the system, or other problems associated with the host computer system. Packet transmission vulnerabilities occur when packets of information are stolen, faked, changed, or disrupted. Examples of packet vulnerabilities include DOS (denial of service) attacks, data interception, packet modification, buffer overload attacks, cross-site scripting attacks, and SQL injection attacks (Alanazi et al., 2022). These threats to SCADA systems can have detrimental effects on utility availability and functionality. If attackers are able to infiltrate these systems, they can cause major stresses to users, organizations, and governments that rely on the services.
Conclusion
Modern society has come to rely on SCADA systems as technology has evolved to manage these resources with increasing control and functionality. This evolution has opened up previously unrealized vulnerabilities that need mitigation and protection. These vulnerabilities mainly consist of unauthorized access to software and packet transmission which can have catastrophic consequences to the societies that rely upon the services. The organizations and governments that manage these systems must develop good security policies, laws, and mitigating practices to protect systems and components from breaches and events that could disrupt the normal function of their services to keep society operating normally.
References
Alanazi, M., Mahmood, A., & Chowdhury, M. J. M. (2022). SCADA Vulnerabilities and Attacks: A Review of the State-of-the-Art and Open Issues. Computers & Security, 125(0167-4048), 103028. https://doi.org/10.1016/j.cose.2022.103028
SCADA Systems. (n.d.). SCADA Systems. http://www.scadasystems.net
During this week’s reading, you’ve been exposed to different points of view regarding human contribution to cyber threats. Now, put on your Chief Information Security Officer hat. Realizing that you have a limited budget (the amount is unimportant), how would you balance the tradeoff of training and additional cybersecurity technology? That is, how would you allocate your limited funds? Explain your reasoning.
Prioritizing Cybersecurity Resources in an Organization
By Adam Haas
Professor Kirkpatrick
March 17th, 2024
Introduction
Determining the use of resources in a security policy is one of the most important tasks that is essential in establishing the continuity and future of an organization. A clear security policy helps the entire organization understand the objectives and the use of resources to secure and protect its information technology from disruption and threats. A document that can be used to best determine how policies should be created ensuring resources are dispensed optimally is the NIST (National Institute of Standards and Technology) Framework. When developing a security policy, difficult decisions need to be made to balance and determine how those resources are used to fortify against cyber threats. Ensuring that security budgets are ideally utilized can be the deciding factor between success and failure.
Security Policy
Organizations have a complicated combination of factors that determine how they should use and distribute their resources to ensure their security including laws, regulations, needs, competitors, and partners. A clear plan and direction should be outlined in its security policy so everyone has a transparent understanding of direction and allocations. A security policy is the documentation of the organization’s security goals and objectives that outlines the essentials and their resolution to meet those objectives. Using a well-developed policy helps ensure staff respect the organization’s assets and goals (Kim & Solomon, 2018, pp. 192-193). Keeping this policy clear, concise, and overreaching will channel personnel to dispense resources directly in line with their ambitions and objectives.
NIST Framework
The United States has a clear interest in ensuring information technology is safe and secure because it is a part of its critical infrastructure. Accomplishing this goal the NIST created the Framework for “a prioritized, flexible, repeatable, performance-based, and cost-effective approach, including information security measures and controls that may be voluntarily adopted by owners and operators of critical infrastructure to help them identify, assess, and manage cyber risks” (NIST, 2018, pp. 1). When developing a security policy the Framework’s implementation tiers can be used to determine the scope and size of risk management practices adopted by the organization. Once it has decided the level of security needed, a framework profile should be created to display how its goals align with the use of a business’s resources and how it is following standards, guidelines, and practices (NIST, 2018, pp. 3-4). The NIST Framework functions as a helpful guide to efficiently determine the best use of resources to protect a company through the cyber landscape.
Balancing of Resources
Resources for organizations are limited and should be distributed with scrutiny so maximum benefit is sustained. Protection against all threats isn’t realistic or affordable so it is a necessity to prioritize the best use of resources. When determining how to spend a security budget two key principles should be considered; don’t spend more protecting assets than they are worth, and countermeasures without a matching risk don’t account for cost (Kim & Solomon, 2018, pp. 253). A risk assessment should be the first step in determining the prioritization of resources. There are several risk assessment methodologies that organizations can use to determine this analysis; Risk Management Guide for Information Technology Systems (NIST SP800-30), CCTA Risk Analysis and Management Method (CRAMM), Operationally Critical Threat, Asset, and Vulnerability Evaluation (OCTAVE), and ISO/IEC 27005 “Information Security Risk Management” (Kim & Solomon, 2018, pp. 122-123). Once a security policy is developed sometimes there are vulnerabilities missed that could cause problems within an organization. In this instance, a gap analysis should be completed which compares the security controls that are in place versus the controls needed to manage all discovered threats (Kim & Solomon, 2018, pp. 123-124). To determine the best use of resources it should invest in a couple of activities that may help determine how to best allocate funding. Some examples include a group brainstorming meeting, employee surveys, interviews, working groups, checklists, and historical information (Kim & Solomon, 2018, pp. 256). Assessing how resources are distributed across the cybersecurity of an organization is an ongoing process that needs input from a variety of people. Understanding what potential threats are and how to mitigate them is a challenging process that needs careful planning and execution to ensure safety and success.
Conclusion
The process of setting up cybersecurity protections can be costly and challenging to execute, requiring careful planning and decision-making. Organizations should have a straightforward security policy to ensure everyone understands the expectations, resources, and plans that are available to achieve this goal. The NIST Framework is a valuable document that offers suggestions and insights on how this can be constructed for any organization. The balancing of resources is a challenging process that requires research and planning. If resources are squandered due to poor planning it could result in major losses or business failure. The prompt for this write-up asked “How would you balance the tradeoff of training and additional cybersecurity technology? That is, how would you allocate your limited funds?”, This is a challenging task without knowing what the company is and who the users of the information technology are. Asking how a company like Google would accomplish this task is very different from how a small private high school would achieve this same activity. Careful planning and understanding are required to achieve the best possible outcome in attaining cybersecurity. The allocation of resources is a difficult process that needs lots of inputs and assessment to properly protect an organization.
References
Kim, D., & Solomon, M. (2018). Fundamentals of information systems security (3rd ed., pp. 14–36). Jones & Bartlett Learning.
NIST. (2018). Framework for Improving Critical Infrastructure Cybersecurity, Version 1.1. Framework for Improving Critical Infrastructure Cybersecurity, 1.1(1.1). https://doi.org/10.6028/nist.cswp.04162018
The Analytical Paper
Analytical Paper. For this assignment, you will produce a paper-length analysis of the social meaning and impact of cybersecurity-related technical systems. It’ll be easier than it sounds. You’ll produce a rough draft of most the paper by combining two of the journal entry assignments you’ve already completed. After that, you’ll edit and revise so that it reads smoothly, and then add a final section with a concluding analysis. In the end, you’ll have a 1200+ word paper that draws from and draws together work that you’ve done throughout the course.
“Facing Challenges of Changing Technology”
Professor Charles Kirkpatrick
Old Dominion University
By Adam Haas
April 13th, 2024
Introduction
Technology is changing rapidly creating unforeseen challenges resulting in complications in the security of information systems that our society depends on. Predictive research and philosophical assessment is needed to address emerging challenges of technological innovation in cyber-policy creation to ensure the three tenets of the Confidentiality, Integrity, and Availability (CIA) triad are preserved in the information systems of our society through preserving trust, operations, and connections that people have with each other. Organizations that want information security for their operations should, at a minimum, ensure their system meets the CIA security triad by keeping their information confidential, establishing integrity, and being available when requested. Organizations that implement safeguards to their information boost consumer confidence and help make sure their systems are functioning as intended and are fortified with safeguards for our posterity . The creation of cyber-policy and infrastructure should be developed using a predictive perspective through the lens of philosophical understanding of what possible consequences could result from new technologies to help determine what the ramifications are for our society, culture, and environment.
Challenges of Unforeseen Effects of Technology
Without predictive foresight in the adoption of technological innovations, unexpected repercussions can result as obstacles with deleterious consequences. There should be clear boundaries set for individuals and groups protecting people from activities that are collectively considered wrong. While state power is diminishing with the adoption of new technologies and access to information, this shouldn’t be understood as an opportunity to ignore wrong behaviors. Markets, businesses, groups, and individuals should continue to engage in challenges to find solutions. Communication and community is key to a progressive fruitful future. An example that comes to mind is the fear that foreign-based social media and device companies from adversarial countries are recording and stockpiling data for future use. A representation of this is the movement to ban the application Tik Tok or Huawei devices. Many argue that these companies are owned by the Chinese and they are using user information for malicious, weaponized purposes. Perhaps a diverse cross-functional team could be made of various industry professionals, policy makers, users, and foreign nationals to discuss these issues and create recommendations for a path forward. The outcomes could then be discussed and commented on in public forums so society can collectively find the best path forward. This recommendation would create transparency, community, and common fellowship in creating solutions allowing each representative attributing to the discussion to have some ownership of the outcome. The predictive ramifications of innovations are still seldom studied before being made available to the general public. These questions are crucial in understanding what challenges and implications can consequently result. Predictive research in policy planning can be a valuable resource for preparing for unknown future vulnerabilities and preserving the tenets of the CIA triad in business continuity and positive outcomes.
Confidentiality
Confidentiality is one part of the triad and is paramount to ensuring that sensitive information is only available to those that have approved access. This is accomplished by a certification that data is acquired by only those who are authorized to do so (Kim and Solomon 2018, pp. 14–128). Chai (n.d.), writing about the CIA Triad, lists some good examples of ways to keep information private: data encryption, user ids, passwords, two-factor authentication, biometric verification, and security tokens. Organizations need to know they can trust that their systems won’t reveal private information that could have unintended consequences for their mission. Planning and assessment during policy creation helps ensure confidentiality from the unknown threats of the future.
Integrity
Integrity is another part of the security triad that requires keeping data safe and unchanged. As Kim and Solomon (2018, pp. 14–128) explain, it is ensuring that data is accurate and valid. Organizations need to be able to certify that their information hasn’t been tampered with without authorization. Chai (n.d.) gives some great examples of this including checksums, identity verification, back-ups, and digital signatures as ways to ensure non-repudiation of their data. Organizations’ reliance on accurate data is important in ensuring honesty and truthfulness. Consistent integrity is an ongoing challenge through the rapidly changing digital landscape of cyberspace that requires planning and predictive policy that anticipates unknown challenges and threats.
Availability
Availability is the final third of the triad ensuring information is attainable when needed. Users need to have access to data confidently when it is necessary. Kim and Solomon (2018, pp. 14–128) hold that availability is expressed when data and systems are accessible and achievable. According to Chai (n.d.), there are different ways to accomplish this. Some examples include maintaining hardware, keeping software free of issues, providing sufficient bandwidth, redundancy, and a robust disaster recovery plan (DRP). Having systems and data available is a core need for the function and success of an organization. Most businesses rely heavily on digital operations for many of their functions. A break in availability could inhibit or halt productivity. This paper further addresses activities needed to protect availability that should be included in cyber-policy from unknown challenges of the future in the next section. Ensuring availability should consistently be considered a goal by organizations and governments when constructing policy and planning for posterity.
Policy Measures to Ensure the Best Future of Information Systems
I assess that mitigating measures of cybersecurity can best preserve the tenets of the CIA triad making them a crucial factor in keeping organizations running through unexpected disruptions of business continuity. Some activities that can help protect IT availability are using intrusion detection software (IDS), strong authentication, using antivirus software, creating a DRP, and keeping software up to date and patched. IDS helps monitor a network and alerts IT if anything unusual or suspicious is detected on the system. This software can be the first notification of a potential attack. If the organization is made aware when an attack is being launched it can sometimes stop the intrusion before too much damage is done, potentially preserving availability (Kim & Solomon, 2018, pp. 234–239). Using strong authentication like multi-factor can help prevent intruders from gaining access to a network through incidents such as a brute force or a dictionary attack. It is much harder for cyber criminals to break into a system if they must overcome multiple levels of security safeguards. When hackers are able to break into systems it can challenge availability if they upload malicious code, change important sections of code, or change who is authorized to access the network (Kim & Solomon, 2018, pp. 137–151). Using antivirus software is a real-time solution in protecting availability by scanning all information that is being transmitted for known virus signatures. This software can stop viruses before they can do damage (Kim & Solomon, 2018, pp. 391). A DRP is crucial to keep businesses running when the unexpected happens. Without a DRP a disaster could leave the infrastructure of an organization in complete chaos because people could potentially be working against each other, making it impossible to bring availability back (Kim & Solomon, 2018, pp. 118-122). Ensuring regular updating and patching helps prevent breakdowns when vulnerabilities are identified. If organizations fail to update and patch known vulnerabilities, attackers may take advantage of those weaknesses infiltrating a system and compromise its availability (Kim & Solomon, 2018, pp. 375–390). There are many more activities that should be considered for sustainable availability like company wide IT training on cybersecurity, building solid security policies, protecting the physical location and infrastructure of host servers, risk assessment, data back-ups, etc… (Kim & Solomon, 2018, pp. 14–390). Continuously monitoring and reassessing the security of an organization is a never ending process since new vulnerabilities and attacks are constantly being realized, making it perpetual work that is never finished. Using a defense in depth approach by applying multiple mitigating strategies in cyber-policy creation is the best way to protect an organization’s assets, reputation, and business continuity through disruptions and emerging challenges from the rapidly changing and advancing technological landscape of the world we operate in.
Conclusion
Understanding and predicting unknown and unexpected harmful repercussions of new adopted technologies should be considered when developing appropriate use policies for activities in cyberspace by companies and governments. The CIA triad is the foundation of information security within an organization which is represented through the protection of information by keeping data confidential, non-repudiated, and available which can be useful in making these predictions to protect our organizations and way of life. These tenets of the CIA triad are supported and emboldened with mitigation practices that are enshrined in the security policies and laws that dictate appropriate cyber behaviors. While some may argue that education and awareness alone is sufficient to protect information, I believe strong predictive policy coupled with multiple mitigating safeguards and community and communication among organizations and governments will ensure the best protections. Digital information is one of the major drivers of our culture making data security foresight and protections a top priority. Using predictive assessment in policy creation is crucial for anticipating the best mitigation practices that will support and protect organizations from emerging threats of technological innovations that have been expeditiously changing our world.
References
Chai, W. (n.d.). What is the CIA Triad? | Definition from TechTarget. WhatIs. Retrieved January 23, 2024, from http://www.techtarget.com/whatis/definition/Confidentiality-integrity-and-availability-CIA?
Kim, D., & Solomon, M. (2018). Fundamentals of information systems security (3rd ed., pp. 14–390). Jones & Bartlett Learning.