Week 1 – Journal Entry
Q: Review the NICE Workforce Framework. Are there certain areas that you would want to focus your career on? Explain which areas would appeal the most to you and which would appeal the least.
The NICE Workforce Framework offers a range of career paths in cybersecurity and among them, I am most interested in investigation. Roles such as cybercrime investigation and digital forensics fascinate me because they contribute to bringing cybercriminals to justice. These roles also require critical thinking and problem-solving, which I consider my strengths.
On the other hand, I am less interested in areas focused on design and development, such as creating systems or new software. Although these are important skills in the cybersecurity field, they do not necessarily align with my interests. However, if I become more familiar with this area and strengthen my development skills, my perspective might change.
Week 2 – Journal Entry
Q: Explain how the principles of science [Empiricism, Determinism, Parsimony, Objectivity etc.,] relate to cybersecurity?
The principles of science play a crucial role in cybersecurity. For example, empiricism emphasizes the importance of experience and observation. This is significant in cybersecurity because observations from breaches or incidents can guide future security practices. Determinism, the understanding of an outcome, can help predict future threats. Understanding why something happens can help prevent the same mistake from happening again in security practices. Parsimony is important for solutions. This helps simplify solutions to avoid complications. Keeping things simple can help tighten up the system to avoid vulnerabilities. When reviewing the principles of science, the principles provide a solid foundation for strengthening cybersecurity practices.
Week 3 – Journal Entry
Q: Visit PrivacyRights.orgLinks to an external site. to see the types of publicly available information about data breaches. How might researchers use this information to study breaches?
After reviewing the data breach information at privacyrights.org, researchers can analyze the nature of the breach and which industries are most affected. Industries that can be affected are healthcare, marketing, government agencies, and much more. For example, healthcare organizations are often targeted due to the sensitive nature of patient data. This can further tell which organizations or individuals might be attacked in the future. By figuring out the main targets for these data breaches, researchers can predict risk and develop strategies. This can further help with the development of security protocols and frameworks that can be implemented within the organization. Focusing on high-risk sectors can allow for more protection measures to be adopted.
Week 4 – Journal Entry
Q: Review Maslow’s Hierarchy of Needs and explain how each level relates to your experiences with technology.
Maslow’s Hierarchy of Needs is a helpful way to understand how different aspects of life, including technology, shape our well being. At the bottom of the pyramid, we have physiological needs. Technology helps by providing things like food delivery apps or wearable health trackers, like apple watch. Next, we have safety needs. An example of this can be online banking and security apps. Then social needs are filled through social media and messaging apps, connecting us with friends, like facebook. For esteem, platforms like LinkedIn allow us to showcase achievements. Finally, self-actualization is supported by using tech for creativity, such as photography or music production software.
Week 5 – Journal Entry
Q: Review the articles linked with each individual motive in the presentation page or Slide #4. Rank the motives from 1 to 7 as the motives that you think make the most sense (being 1) to the least sense (being 7). Explain why you rank each motive the way you rank it.
- For money
- Political
- Multiple reasons
- Recognition
- Entertainment
- Boredom
- Revenge
After reviewing individual motives I will rank them in the following order with one being the motive that makes the most sense to me. I am personally not a political person, so the main motive that makes sense to me would be for money. Times are hard and the economy is not in the best state right now. This leads to my second pick, political motive. Like I stated the economy is struggling and this can be tied to our political system. Even other counties are unhappy with the way the United States is being handled. This gives motive to many criminals to commit cyber crime. This already transitions into my third pick, multiple reasons. If you are a criminal and you need a reason to commit a crime. Most likely it will take multiple reasons to convince yourself. As we move further down the list, recognition and entertainment are close in terms I feel as pointless. No need to gain recognition or entertain yourself with crime. These are ranked higher than boredom and revenge as they are the worst of the group in my opinion and should never be a motive for anyone to commit a crime
Week 6- Journal Entry
Q: Can you spot three fake websites? Compare the three fake websites to three real websites and highlight the features that identify them as fraudulent.
When spotting a fake website, there are a few key identifying features one can pay attention to spot out a fake. One can inspect a website by carefully checking the URL. Fraudulent websites often use slightly altered or misspelled domain names that are designed to be legitimate ones, making them harder to detect. For instance, we see this with phishing emails. The attacker is attempting to copy the original name and pretend to be someone else. Instead of a trusted “.com” domain, they might use “.net” or any unfamiliar domain. Also another way to identify fraudulent websites is taking note of the padlock symbol in the address bar. If the padlock is missing or open, the site is not secure, which increases the likelihood of it being a fake. Ensure the URL starts with “https” to verify the site’s encryption is legitimate.
Week 7 – Journal Entry
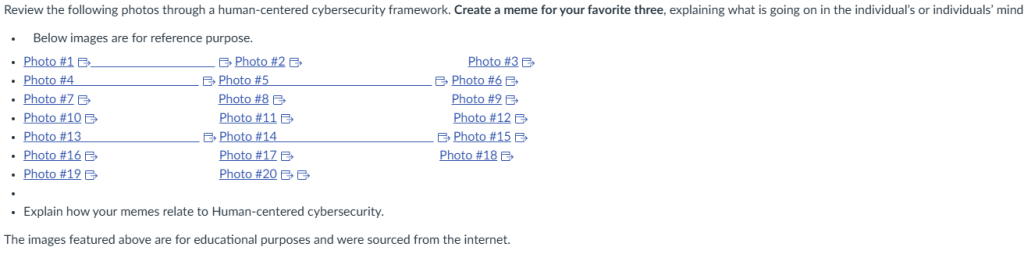



Week 8 – Journal Entry
Q: Watch this video and pay attention to the way that movies distort hackers.Hacker Rates 12 Hacking Scenes In Movies And TV | How Real Is It? – YouTubeLinks to an external site.
- After watching the video, write a journal entry about how you think the media influences our understanding about cybersecurity
The media tends to make major stories seem more dramatic, they focus on attention-grabbing headlines than providing accurate information. When a major data breach or cyberattack happens, news outlets tend to make it seem like a major hack or international threat. This often leads to confusion and misunderstanding. As a result this can lead the public to become fearful or questioning their own cybersecurity practices. The media should focus on educating the public about simple and realistic ways to protect themselves from common cyber threats, and not stretch the truth of what reality is. This will help not create false threats that could happen.
Week 9 – Journal Entry
Q: Watch this Video:
Social media and cybersecurityLinks to an external site.
Complete the Social Media Disorder scale Download Social Media Disorder scale.
How did you score?
What do you think about the items in the scale?
Why do you think that different patterns are found across the world?
I scored a zero because I personally don’t enjoy social media and see many problems with it. I tend to stay away from it as much as possible. It’s easy to get drawn in and use it as a distraction. I think people’s social media habits differ from person to person due to social influence. Different cultures around the world have different interests, and if you break it down further, the social groups someone is part of and how they were raised also play a role. There are a lot of factors to consider, but it’s important to be aware of how much we share on social media and the impact it can have.
Week 10 – Journal Entry
Q: Read this and write a journal entry summarizing your response to the article on social cybersecurity
Social cybersecurity is how technology can influence human behavior, social, cultural, and political outcomes. Unlike traditional cybersecurity, which focuses on protecting information systems. Social cybersecurity deals with using technology to “hack” human behavior, affecting how people think, feel and act. This can be done through targeted messages, persuasive tactics, and social media. The passage also notes this is considered an emerging area within national security. This is considered a new type of warfare, information warfare. This aims to disrupt societies by targeting their values, institutions, and trust. The article argues that the U.S Department of Defense must understand and prepare for the growing threat by social cybersecurity in order to defend effectively.
Week 11 – Journal Entry
Q: Watch this videoLinks to an external site.. As you watch the videohttps://www.youtube.com/watch?v=iYtmuHbhmS0Links to an external site.

, think about how the description of the cybersecurity analyst job relates to social behaviors.
The role of a cybersecurity analyst can be considered an entry level job, but the entry level role does not lack importance in cybersecurity. The analyst must also understand the psychology behind why people share or believe in certain narratives, as this impacts the effectiveness of cyber threats. This job involves understanding how information impacts human behavior, beliefs, and social interactions. A cybersecurity analyst needs to recognize how the manipulation of information can also shape public opinion and create distrust within society. This connection between cybersecurity and social behavior highlights the importance of cybersecurity analyst within the cyber field, as it is not only restricted to technical skills.
Week 12 – Journal Entry
Q: Read this https://dojmt.gov/wp-content/uploads/Glasswasherparts.com_.pdfLinks to an external site. sample breach letter “SAMPLE DATA BREACH NOTIFICATION” and describe how two different economics theories and two different psychological social sciences theories relate to the letter.
The data breach letter notice reflects Marxian economic theory and Rational Choice Theory. From a Marxian perspective, the company operates within a capitalist system. They prioritized profit and control over transparency and consumer protection. As they decided to delay notifying customers, despite the breach happening for some time. This shows how power and information are unequally distributed. Customers are at risk, while the provider maintains control. According to Rational Choice Theory, once customers are informed, they are likely to act in their own best interest. An example of this can be canceling cards. Customers must make decisions in response to the company’s failure to protect their data. Cognitive Theory explains the discomfort customers can feel after a trusting company failed to protect their data, possibly leading them to change behavior or discontinued their use.
Week 13 – Journal Entry
Q: A later module addresses cybersecurity policy through a social science framework. At this point, attention can be drawn to one type of policy, known as bug bounty policies. These policies pay individuals for identifying vulnerabilities in a company’s cyber infrastructure. To identify the vulnerabilities, ethical hackers are invited to try explore the cyber infrastructure using their penetration testing skills. The policies relate to economics in that they are based on cost/benefits principles. Read this article https://academic.oup.com/cybersecurity/article/7/1/tyab007/6168453?login=trueLinks to an external site. and write a summary reaction to the use of the policies in your journal. Focus primarily on the literature review and the discussion of the findings.
The article “Hacking for Good” explores how bug bounty programs, like HackerOne, help improve cybersecurity. This is by rewarding ethical hackers for finding system vulnerabilities. In the literature review, the authors states how traditional security methods are no longer enough. Companies have found out approaches like bug bounties offer a flexible, cost-effective solution. They also have money incentives to find these bugs which can shape hacker behavior. In the discussion about the findings, the authors show a model showing that higher rewards attract better hackers and lead to more valuable discoveries. The article shows that with the right policies and bounty programs, companies can turn potential threats into protection by working with hackers.
Week 14 – Journal Entry
Q: Andriy Links to an external site.SlynchukLinks to an external site. Links to an external site.has described eleven things Internet users do that may be illegal. Review what the author says and write a paragraph describing the five most serious violations and why you think those offenses are serious.
The author talks about many things that are illegal or unsafe to do online, but the five I consider the most serious. First, watching pirated movies or using torrent sites breaks copyright laws. This can lead to someone receiving fines. Sharing someone’s personal information, like their home address, without asking is very dangerous as well. This can put the person at risk. Then we have cyberbullying and online trolling, this can hurt someones mental health and lead to worst consequence for the victim. Also recording online calls without permission is illegal. Lastly, searching for things like child abuse or how to make weapons can get you in trouble with law enforcement.
Week 15 – Journal Entry
Although the career of a digital forensic investigator is typically considered a technical role that involves computer science, a closer look in the field shows the intersection of social science is present.
Every file or record of communication reflects choices, behavior, intent, and social relationships. This is where the social sciences come into play. Sociology plays a role in understanding how online communities form and how social norms can be shaped online. Examples of this would be communities in hacker forums on the dark web or fandom groups on platforms like Reddit or Discord.
I found the speaker’s input about his career interesting for a few reasons. He didn’t study digital forensics originally, he fell into it by interest. Then at the very end of his talk he describes what catches the interest of an investigator and he said not tech support like fixing wifi. They rather be asked how to recover data.