Vulnerabilities that exist in critical infrastructure systems should not be ignored (Devasia). Reading through articles on this issue provides evidence to consider the vulnerabilities and show what is possible with SCADA applications in controlling these risks. There should be effective provision of comprehensive security measures that would be helpful in dealing with cyber threats, which will continue to evolve (Soriano).
SCADA Systems Overview
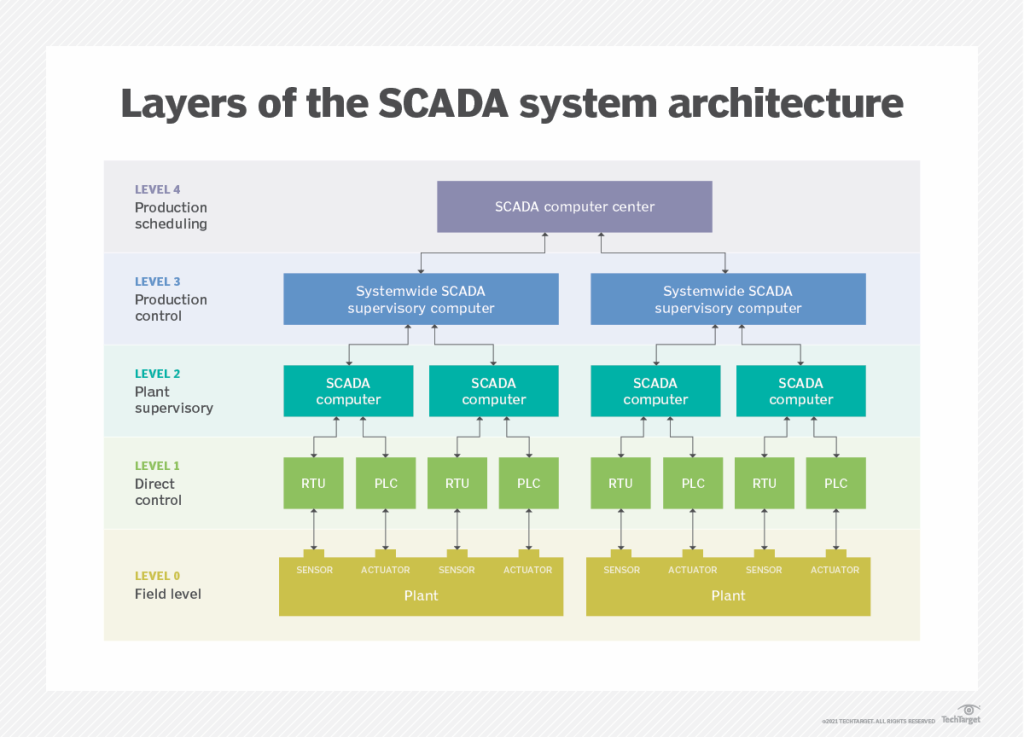
SCADA plays a significant role in the operation of critical infrastructure since it provides for real time control and monitoring of operational processes. These are made up of various components, a supervisory system, Programmable Logic Controllers (PLCs), Remote Terminal Units (RTUs), including a
human-machine interface (HMI), and communication infrastructure.
Data Acquisition and Tag Databases
Data from various sources is collected and processed in the SCADA systems where it is classified into soft and hard points. By doing so, these points provide information about the equipment state as well as support operational decision-making.
Supervisory Station
The supervisory station acts as a hub between the field instruments and the HMI software. Several server controls might be put in place to enable continuous monitoring of the equipment.
Human Machine Interface (HMI)
HMI connects operators to the SCADA system and provides them access to live data and process control features. They provide customization options so that the interface can suit the specific needs of operators.
Hardware
In SCADA systems, the incorporation of Distributed Control Systems is accompanied by the utilization of intelligent PLCs and RTUs. Integrating with HMI/SCADA packages makes configuration and maintenance easier.
Architecture
From monolithic or distributed architecture to networked systems, SCADA system has come a long way. Nowadays, many use IP and it could serve as further reinforcements for the systems.
Alarm Systems
Alarms are also generated by SCADA systems that give out notices when certain conditions are met. These alarms have been found to be very important in contacting operators and managers whenever they are needed.
Remote Terminal Units (RTU)
Enabling equipment control and digitizing electrical signals is the responsibility of RTUs, which interface with physical equipment and aid in data collection.
Operational Philosophy
Systems utilizing SCADA aim to minimize the likelihood of failures. Processes are kept safe through the use of multiple communication channels and hardware redundancies, which helps avoid interruptions and promotes reliable system operation.
Communications Methods/Infrastructure
Employed in SCADA systems are diverse communication methods, encompassing both standard and legacy protocols. These current systems frequently utilize Ethernet and TCP/IP, facilitating seamless integration with commonplace networking technologies.
Security Issues
Safety is paramount for SCADA systems. It faces issues like unauthorized access, soft spots, and network segment infections. Sellers regularly address these challenges by using safety rules, barriers, and industry-specific secure networks that are all designed to safeguard such structures (Soriano).
To summarize, it is crucial to emphasize the significance of addressing weaknesses in critical infrastructure systems. The aforementioned articles shed light on the possible ramifications associated with these vulnerabilities and emphasized the pivotal role that SCADA applications play in mitigating such risks. In order to safeguard these systems against cyber threats, intricate security measures need to be implemented and continually enhanced (Devasia).
Works Cited:
Devasia, Anish. “Securing SCADA Systems from Cyber Attacks – Technical Articles.” Control.com, 1 July 2020, control.com/technical-articles/securing-scada-systems-from-cyber-attacks/.
“SCADA Systems – SCADA Systems.” Www.scadasystems.net, www.scadasystems.net/.
Soriano, Raymond. “Best Practices for Securing Your IoT/SCADA Systems.” Eisner, Amper, 19 July 2023, www.eisneramper.com/insights/ea-digital/securing-scada-iot-0723/. Accessed 5 Nov. 2023.