Cybersecurity, Technology, and Society
Students in IT/CYSE 200T will explore how technology is related to cybersecurity from an interdisciplinary orientation. Attention is given to the way that technologically-driven cybersecurity issues are connected to cultural, political, legal, ethical, and business domains. The learning outcomes for this course are as follows:
- Describe how cyber technology creates opportunities for criminal behavior,
- Identify how cultural beliefs interact with technology to impact cybersecurity strategies,
- Understand and describe how the components, mechanisms, and functions of cyber systems produce security concerns,
- Discuss the impact that cyber technology has on individuals’ experiences with crime and victimization,
- Understand and describe ethical dilemmas, both intended and unintended, that cybersecurity efforts, produce for individuals, nations, societies, and the environment,
- Describe the costs and benefits of producing secure cyber technologies,
- Understand and describe the global nature of cybersecurity and the way that cybersecurity efforts have produced and inhibited global changes,
- Describe the role of cybersecurity in defining definitions of appropriate an inappropriate behavior,
- Describe how cybersecurity produces ideas of progress and modernism.
Course Material
Two write ups, a discussion board post, and the final reflective paper have been included as examples of course material completed.
The first artifact is a write-up on exploring the CIA triad. It relates in part to learning outcome 3 described above, as it demonstrates the competing needs to provide services through technology while remaining cybersecure. This is illustrated below through the various risk factors and their corresponding mitigation techniques. This write-up was an interesting challenge as it was the first one I had ever completed for any class.



The second artifact is a short write up on SCADA systems. This relates to learning outcome 1 in that it showcases that while technology is advancing and becoming more cybersecure, it still can introduce new vulnerabilities or boost the old. This write up was far easier than the previous one, as I felt far more confident in using business writing skills by this point.

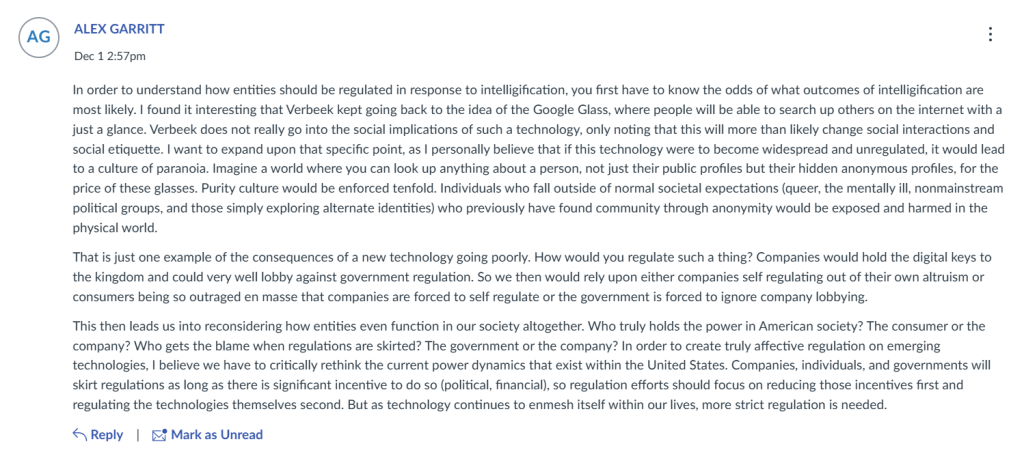
The third artifact is from a discussion board on Verbeek’s writing, Designing the Public Sphere: Information Technologies and the Politics of Mediation. This post most closely relates to learning outcome 2, as I discuss how I believe culture would react to emerging cybertechnologies if they continue to go unregulated. This discussion board was incredibly thought provoking as Verbeek’s writing indicates such broad ethical considerations.
The final artifact is a reflection paper wherein three topics from the course were picked and discussed. This relates to learning outcome 1 as it shows how human nature inevitably conflicts with emerging technology to create cybercrime. This paper was a challenge as I tried to keep the themes interconnected while having such visible separation through the required business writing skills and structure.




