Module 1 Journal: Review the NICE Workforce Framework. Explain which areas would appeal the most to you and which would appeal the least.
After I review the NICE Workforce Framework that has 7 categories viz Analyze, Collect and Operate, Investigate, Operate and Maintain, Oversee and Govern, Protect and Defend, and Securely Provision with 33 specialty areas. So, if you ask me what area I want to focus my career on or the most appeal to me, I think it will be the digital forensics area in investigating categories because I think I am a person that good about investigating and analyzing skills, and love to do some activities with it. So, digital forensics is an area where you need to collect, process, analyze, investigate, and present evidence that relates to computers to support network vulnerability mitigation or criminal investigation, is will the best choice for me, and that more easily appeal to me than any areas in the NICE Workforce Framework even some areas in analyzing categories such as Threat Analysis also look interesting in my opinion.
Even though other areas also have interesting but if you ask me what area I appeal to the least in the NICE Workforce Framework, I think it will be Customer Service and Technical Support in operating and maintaining categories because it is an area that needs to address problems such as installing, troubleshooting, training in response to customer requirements or inquiries, etc. That also needs people who have a service heart to do it, but I am a person who doesn’t like to give service so if I can avoid this area, I will avoid it. That makes this area become the least appealing area.

Module 2 Journal: How the principles of science relate to cybersecurity
Cybersecurity is an interdisciplinary study or career that needs to relate to some STEM fields such as information technology, computer science, mathematics, etc., and some social sciences such as criminology, psychology, political science, etc. So, we can see cybersecurity is one of the science or especially in social science careers that makes we can use the principles of science to it.
For the principle of science, the relativism that principle says all things are related, we can use in cybersecurity such as seeing a relationship between technology and something (cybercriminal, people’s behavior, etc.) then making us recognize how broader technology can affect people and society, for example, “how the social system changed with behaviors driven by technology” or “how the criminal justice system developed new ways to respond to crime.”
For the principle of science, an objectivity that scientists need to be neutral and not show their opinion on the study topic, we can use it in cybersecurity because in cybersecurity studies we also need to be neutral when doing some research for the correctness of the data even if we have some strong opinion about it such as the question “how should hackers be punished?”
For the principle of science, parsimony that scientists need to keep the explanation as simple as possible, we can use it in cybersecurity because when we do research about cybersecurity, we need to make sure it is easy to make people understand our research for people who want to study or want to develop the research in the future even it is hard to use a simple explanation for cybersecurity topic that relates to social science such as human behavior.
For the principle of science, empiricism that scientists can only study behavior that is real to sense or something people can experience, we can use it in cybersecurity which we also can’t trust opinions or hunches to frame our cybersecurity knowledge because it will make an error to data, so cybersecurity knowledge must only come from empirical research.
For the principle of science, ethical neutrality that scientists need to adhere to ethical standards when they do research, we can and must use it in cybersecurity because we need to protect the right of people in the cybersecurity research that we study because it easily to have ethic issues when we study or talk about human behavior such as the question “should the police use digital technologies that track human behavior?” or “Can a professor or teacher monitor their student for online course work?”
For the last principle, determinism that principle says behavior is caused by preceding events, we can use it in cybersecurity so that we can understand why some people choose to engage in certain behavior such as “why people choose to commit phishing and internet fraud” or “why people choose to share personal information with a stranger on the online” by looking reason in the past or the previous event. So, all of this is how the principle of science relates to the cybersecurity discipline in my opinion.
Module 3 Journal: Visit PrivacyRights.org to see the types of publicly available information about data breaches. How might researchers use this information to study breaches?
Data breach is one of the significant problems that people can find especially in an organization or working place that can crucially damage society. After I study and do some research on the type of data breach, it shows me that we can distinguish data breaches into 8 types and each type has a unique characteristic. For example, HACK type that data breach happens from hacking by an outside party or infected malware, or INSD type that data breach happens from an insider (employee and contractor). If you ask me how researchers can use this information to study breaches, I think they can use this information about the type of data breach to make them know or understand more about a data breach that data breach not just has only way or a fixed way to happen, but it can possibly happen in many ways instead such as losing document, hacking computer, skimming device, etc. Moreover, they can use this information to help them to do their research on the data breach which they can use the type of the data breach as the variable of research or use it as a citation to the research.

Module 4 Journal: Review Maslow’s Hierarchy of Needs and explain how each level relates to your experiences with technology. Give specific examples of how your digital experiences relate to each level of need.
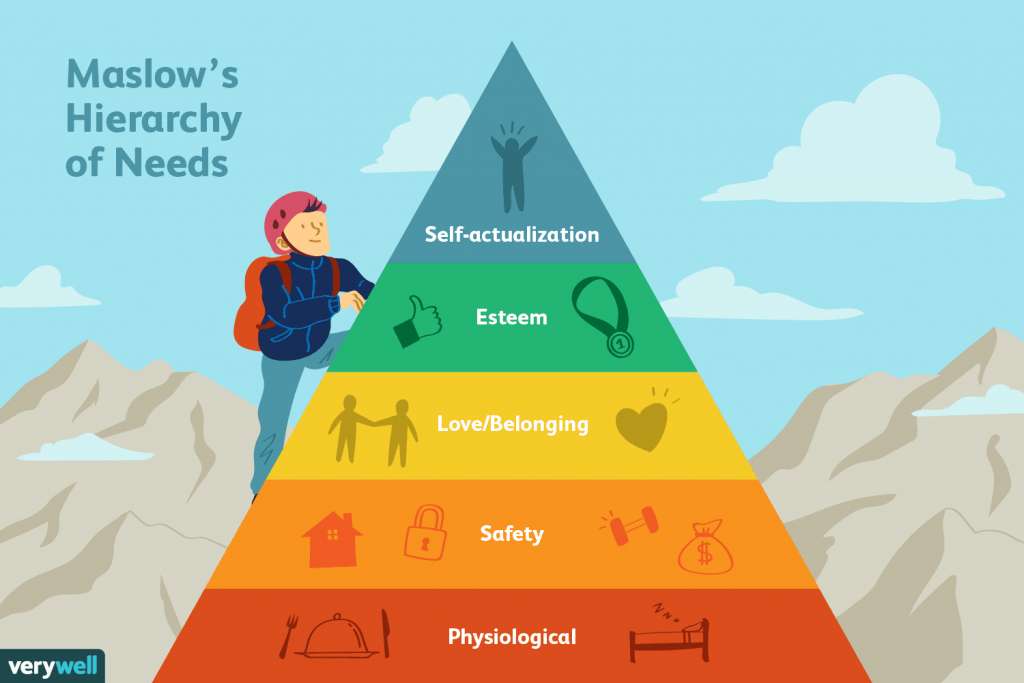
From Maslow’s Hierarchy of Needs Theory that says all humans have needs that exist on a hierarchy that can change over time. It has 5 levels viz physiological needs as level 1, safety needs as level 2, belongingness and love needs as level 3, esteem needs as level 4, and self-actualization as level 5. We can use this theory with cyber behavior to explain the digital experiences we found in the present that how people’s digital experiences relate to each level of need.
For level 1 physiological needs when we talk about digital experiences or technology, it relates to behavior that everyone sees the technology such as smartphone becomes a physiological need that people will have emotion to it or physiological reactions when something happens to that technology such as when I lose the phone, I will show some actions to find it and feel anxious or angry for that loss.
For level 2 safety needs when we talk about digital experiences or technology, it relates to behavior that everyone wants to protect the information in social media or makes their technology safety when using it such as I need a firewall to protect my computer from hackers or when people’s computer has a virus, they need to fix it as fast as possible to make their computer safety.
For level 3 belongingness and love needs when we talk about digital experiences or technology, it relates to behavior that people make their relationships with other people in the cyber world such as I am using social media to find friends, some people using dating apps to find the lover, some people subscribe to YouTube channels to make them more feels belong to that channel, etc.
For level 4 esteem needs when we talk about digital experiences or technology, it relates to behavior that people use the space in the cyber world to present their prestige or accomplishment to make other people know such as I posts on social media that I get a new job or wins some sport competitions.
For level 5 self-actualization when we talk about digital experiences or technology, it relates to behavior that people use the technology or cyberspace to make some creative things that they are interested such as I really love gaming so I decide to create a new game or web page about gaming that makes me happy and can make income from technology at the same time.
Module 5 Journal: Review the articles linked with each individual motive. Rank the motives from 1 to 7 as the motives that you think make the most sense (being 1) to the least sense (being 7). Explain why you rank each motive the way you rank it.
I believe each individual motive that makes a cyber offender commit the cybercrime in the article viz entertainment, political, revenge, boredom, recognition, money, and other reasons are really significant to affect their decision to commit the crime. If I need to rank these motives from 1 to 7 that what I think it makes the most sense to the least sense, I will rank them in this order:
- Money motive will be the first place in my rank that looks the most sense to me because we know everyone in this world wants money and even though money can’t buy happiness in your life, I guarantee you will suffer if you don’t have it. So, money is the easiest motive for cyber-criminal to commit cybercrime which makes them have a lot of money to use in their life.
- Revenge motive is the second place because I think revenge is also easy to make you commit something you know is wrong (not equal to money), but you want to do it for your justice in your opinion. So, it will be easy if you have the technical knowledge and technology to commit cybercrime against the person you have a conflict in the first place.
- Other reasons motives such as ego and power will be my third place because when you have the knowledge to do something that can affect the world even in a bad way, you will be needed in some way and may be proud of your action. So, if you can commit a cybercrime such as hacking some companies, you may be proud of yourself and be needed by illegal places such as the dark web which can be a motive for you to commit cybercrime but not enough 2 previous motives in my opinion.
- Political motive is the next one because I think when we talk about politics it always comes with different points of view in the society that always have people do some actions to show their standpoint and sometimes it is more aggressive than should it be. So, cyber offenders can be motivated by politics to make them commit cybercrime because they want to show their standpoint. It is a motive that makes sense, but I think the 3 previous motives that do just for themselves more make sense.
- Recognition motive is fifth place in this order because I think it is hard to make people commit cybercrime from the recognition experience that they realize they just can do it. However, I also believe it is possible for cyber offenders to have this motive, but it just looks not make sense to me.
- Entertainment motive is the sixth place because I think the cyber offender should not risk their life for just finding the entertainment but should have a serious motive as the 5 previous motives in my opinion.
- Boredom motive is the last place because it is a similar tier to the entertainment motive but I just think the entertainment motive more makes sense than the boredom motive because it also has cyber offenders who really like to commit cybercrime such as hacking because they see it as the entertainment to their life but for the boredom, I think people can find other ways that funnier than commit cybercrime to eliminate that boredom.

Module 6 Journal: Can spot three fake websites and compare them to three real websites, plus showcase what makes them fake?
For this question, in my opinion, my answer is yes that I can spot three fake websites and compare them to three real websites, moreover, I also can tell the difference between real websites and fake websites which makes those fake websites fake. So, first, I need to notice some of the unique characteristics of the fake website that criminals want to use in bad ways such as the website having unreliable and unsafety domains such as amaz0n.net, the information on the website offering too good to be true such as “Congratulation you have the right to get the iPhone 14 pro just give us the email and password then iPhone will be yours”, the information on the website has unorganized language and words, etc. After I found websites that have those characteristics, I will compare those websites to the three real websites such as the FBI website, the NASA website, and the Apple Company website which have opposite characteristics from the fake website such as the website having a reliable and safe domain, the information on the website doesn’t offer too good to be true, the information on the website has well-organized language and words, etc. for checking and confirming those websites are fake websites that different from the real website. So, if I do this method, I have confidence that I can spot the 3 fake websites from the 3 real websites and can identify what makes those 3 fake websites fake or have differences from the 3 real websites.

Module 7 Journal: Review the following ten photos through a cybersecurity human systems integration framework. Create a meme explaining what is going on in the individual’s or individuals’ mind. Explain how your memes relate to Human Systems Integration.
After I see all of the photos, I think it directly shows or implies about technology now in the present day such as computers, smartphones, etc. are a part of human life and have significance for almost human activities when humans want to do something in daily life such as have to conference with the company, communicate with a friend, take a photo with your partner, etc. On the other hand, we can say society now has Human Systems Integration (HIS) which we can find an interaction between human and technological processes everywhere in society.

Module 8 Journal: After watching the video, write a journal entry about how you think the media influences our understanding of cybersecurity?
From module 8, it makes me realize that many social forces can influence or shape some groups and individuals in society. One of the social forces that have an important role in the present day is the media. It is a social force that everyone is familiar with and can see throughout society such as news, television shows, movies, etc. Media is a really useful tool in people’s lives to get information or entertainment for themselves, however, media also can harm people if media provide misinformation to the people that may lead the people to get the wrong concept from some topics. After I am watching the video, it makes me see clearly how the media influences our understanding of cybersecurity. If the media such as blockbuster movies present the correct information or knowledge about cybersecurity to the people, it will make people more understanding about cybersecurity and may use the information from that media to prevent them from victimization or practice cyber hygiene in cyberspace. However, if the media presents misinformation or the wrong knowledge to people, it will make people understand cybersecurity as the wrong concept such as cyberspace is pathologically unsafe and may lead people to overemphasize scary of cyberspace or may make them easily become a cyber victims from the misinformation they get. So, I think media is a double-edged sword for cybersecurity and should be more controlled to benefit society.

Module 9 Journal: Complete the Social Media Disorder scale. How did you score? What do you think about the items on the scale? Why do you think that different patterns are found across the world?
After completing the social media disorder scale, which asked me about my behavior and emotion toward social media disorder during the past year. I found I don’t have a high social media disorder scale score (only 2) which likely proves I don’t have social media disorder. However, it also has some questions from many questions “How often used social media to escape from negative feelings?” and “How regularly I felt dissatisfied because I wanted to spend more time on social media?” that I have s strong feeling about it. I think all items or questions on the scale are effective to use for measuring social media disorder in people because it is a contemporary question that can evaluate people’s behavior and emotions toward social media disorder. And if you ask me why we found the pattern of the score from this scale different across the world. I think it happens from the different cultures or environments that every people have across the world because culture can shape people’s view, idea, and norm that could affect the behavior and emotions of people on every topic, and the use of social media or social media disorder is one of the topics in the present day. Moreover, even though people are in the same area we also can find the different score patterns of social media disorders from their different cultures. So, it doesn’t strange if we can find this scoring pattern different across the world.

Module 10 Journal 1: Think about how the description of the cybersecurity analyst job relates to social behaviors. Write a paragraph describing social themes that arise in the presentation.
After I am watching the video about the cybersecurity analyst career that the class provides, it makes me clearly see and understand how a cybersecurity career relates to or requires some social behaviors. In the video, I get knowledge of the overall cybersecurity analyst career such as what is the duty or responsibilities of a cybersecurity career, what is the best location to do this job, how much salary will get, etc. But the main concept that I focus on in this video is how social behaviors relate to a cybersecurity analyst career, and I found people who want to have this career need to have some social behaviors viz first, Continued Learning Behavior that will make you don’t miss anything in the current situation about knowledge that relates to cybersecurity analyst because people in this job need to always update themselves for preparing to cope with the problem when the incident or threat happens. However, in this career, one person can’t do anything much because this career has a lot of topics to learn. Somebody may be good at networking, but somebody may be good at the operating system. So, for the second social behavior, this career necessarily needs to have a team player and communication social behavior that make people can work efficiently in this career path. For example, in this video, the woman doesn’t like and doesn’t have good skills in networking with other people but she also tries to involve in the community at “meetup.com” which has a lot of technical meetings that benefit her work. So, we can see this career really relates to the concept of social behavior of cybersecurity professionals from the class.

Module 10 Journal 2: Read this and write a journal entry summarizing your response to the article on social cybersecurity
After I read the article about social cybersecurity provided by the class, it makes me see and agree with how significant social cybersecurity is and how warfare and cybersecurity changed from the past. In the twentieth century, the world and many nations focus on physical warfare and use some technologies to hack other technology to get information, but now in the twenty-first century the world focus on information and psychological warfare instead, on the other hand, we can say in the new generation war will relate or be dominated by the information and psychological. Because from the growth of technology in the present day, makes the decentralization of information and doesn’t require physical presence to get information which makes “high connectivity, low latency, low cost of entry, multiple distribution points without intermediaries, and a total disregard for physical distance or national borders.” (Carley, 2019) It makes other nations’ malicious groups can use that technology to make an information blitzkrieg to drive a wedge of distrust between society and government, and also between society and military which will make severe damage to the nation. Therefore, to solve this problem or to win this information warfare the leaders of both government and military must understand and have knowledge about social cybersecurity that will make them can prepare policies to cope with the information blitzkrieg when it happens. Moreover, they need to educate society about this social cybersecurity topic such as the current risk, the modern information environment, etc. which support eliminating distrust between society and government (and military). So, it is understandable why social cybersecurity is necessary for the present day and maybe in the future.

Module 11 Journal 1: Read the three case studies and identify at least one thing each company could have done to reduce the risk of experiencing cybersecurity incidents. Also, explain whether doing a risk assessment ahead of time would have helped each company.
For the 3 cybersecurity incident cases, I decide to study viz 1. Yahoo data breach 2013 case 2. LinkedIn data leak 2021 case, and 3. Facebook data breach 2019 case. So, first, in the Yahoo case, it happens when the hacker or the intruder can steal the name, birth dates, phone numbers, passwords, and also security questions and answers of the account user even though all of that information was encrypted with Yahoo security because of poor security practices (phishing). It impacts 3 billion user accounts that make high damage to Yahoo. Second, in the LinkedIn case, it found the hacker that use the username “TomLiner” declares to sell information of 700 million LinkedIn users such as email addresses, full names, phone numbers, etc. on the dark web that he got by using LinkedIn’s API (Application Programming Interface) which has a potential security risk. It makes LinkedIn lose its reputation and money. Lastly, in the Facebook case, it found the personal information of Facebook users’ 533 million accounts such as user ID, address, phone number, etc. leaked on the dark web. Facebook said the hacker uses data scraping, the process that import data from a website to a local file in the computer, to get the user’s information. It is like the 2 previous cases that make Facebook lose its reputation and money.
All 3 cases are similar and relate to a data breach or data leak if you ask me how to reduce the risk to each company. I will suggest to these 3 companies recruit more cybersecurity expertise to monitor or set up the network and system, moreover, they should have more training in cybersecurity in their company because we can see in Yahoo’s case it happens from the inner person from the company that responds to the phishing email and other 2 cases it happens from the vulnerable of the system itself. And if you ask me how risk assessments ahead of time will help these 3 companies. I think it may help these 3 companies don’t have a data breach or data leak happening or can quickly recover and mitigate the problem faster than the actual case because the risk assessment makes them prepared to cope with the cybersecurity incident that may happen in the future.
Module 11 Journal 2: Read this article https://academic.oup.com/cybersecurity/article/7/1/tyab007/6168453?login=true and write a summary reaction to the use of the policies in your journal. Focus primarily on the literature review and the discussion of the findings.
After I study and read the Bug bounty policy article, it makes me know many things about bug bounty policies that it is a policy that the organization or company pays money to the individual employee for identifying the vulnerability of the company’s network or company’s system (company’s cyber infrastructure). So, ethical hackers will be invited by the company for exploring the cyber infrastructure and find the vulnerability by using their penetration testing skills to get the money. From the article, it shows me that a bug bounty program is an efficient tool to benefit the economy which can help the company to have stronger security and it doesn’t matter to the size of the company and level of prominence. Moreover, it found that bug bounty programs also receive fewer valid reports over time because the hackers’ supply is price inelastic, and they want a high bounty. So, if the bug bounty program does not increase its bounties, the company will get fewer reports from the bug bounty program which may affect the security of the company. However, this article also tells me this is just simple information about the bug bounty policy that points out how little people know about the bug bounty markets. Anyway, it makes me think and feel we should give more attention to the bug bounty policy that is useful to the company and business.

Module 11 Journal 3: Read this https://dojmt.gov/wp-content/uploads/Glasswasherparts.com_.pdf sample breach letter “SAMPLE DATA BREACH NOTIFICATION” and describe how two different economics theories and two different social sciences theories relate to the letter.
After I read this article, I found it is an article about a data breach that www.glasswasherparts.com was hacked by a hacker. The hacker uses the malware on the platform provider’s servers, which allows hackers to get information such as the customer’s name, address, phone number, and any customer’s debit or credit card information. The situation from the article or letter makes me relate to some economics and social sciences theories. For the economics theories, I found it related to Marxian economic theory and Laissez-fare economic theory. First, the Marxian economic theory that states those with power exploit those without power for economic gain, relates to this case that we will see the hacker use their power (malware) and knowledge to exploit people that don’t have knowledge about this topic by stealing people’s personal information. Second, the Laissez-fare economic theory that states government should not intervene in the economy except to protect individuals’ inalienable rights, related to this case that we will see the Glasswasher part company also contact to the government for federal law enforcement to solve this problem. For the social science theory, I found it related to Cognitive theory and Neutralization theory. First, the cognitive theory that theory focuses on the way individuals think and process information relate to this case because the hacker must already think before hacking the website that if he/she hacks this website, he/she will get a lot of information which can make money to him/her. Second, the neutralization theory that states individuals know right from wrong and they rationalize their behavior before committing a crime, relates to this case that the hacker may hack this company because the hacker believes nobody got hurt from the action that the hacker steals the personal information on the digital platform. That are some theories which relate to the letter.

Module 12 Journal: Review what the author says and write a paragraph describing the five most serious violations and why you think those offenses are serious.
After I read and study the article about eleven things Internet users do that may be illegal by Andriy Slynchuk, it makes me recognize how some violation activities in cyberspace or the internet can significantly harm society. Then if you ask what the five most serious violations from these eleven violations are, in my opinion, I think the most five will be viz 1. Using unofficial streaming services 2. Using torrent services 3. Using copyrighted images 4. Sharing passwords, addresses, or photos of others, and 5. Collecting information about children.
First, for using unofficial streaming services which is a violation of people watching movies, TV shows, and any content that must pay to the creator for free on the illegal platform. Second, for using torrent services which is a violation of people downloading pirated copies of movies and other digital content through torrents. And third, for using copyrighted images which is a violation of people using copyrighted photos or pictures that they get from the internet for their purpose. They are serious problems because they make creators lose many millions of dollars and it will damage the entertainment kingdom that makes it doesn’t develop in the future. Fourth, for sharing passwords, addresses, or photos of others which is a violation of people sharing other information without consent to the internet or social media platforms. It is a serious problem because it may have bad people (hackers) who can use that information to benefit themselves which will directly damage the person who was posted the information on the internet and indirectly to society. Lastly, for collecting information about children which is a violation of people collecting information about people younger than 13 years old. It is a serious problem because it violates the Children’s Online Protection Act and it relates to children which is the future of the nation. That is why I think these five violations are more serious than the other 6 violations.

Module 14 Journal 1: Complete the Patchin and Hinduja’s cyber bullying survey. After completing the survey, discuss how you think criminologists might use the surveys to explore relationships between the different items.
After I complete Patchin and Hinduja’s cyberbullying survey that asks you more than 30 questions about your cyber bully experience and behavior in the last 30 days. I found I have a lower score on both Cyberbullying Victimization Scale and Cyberbullying Offending Scale which represents I have less involvement with cyberbullying. It also makes me see and understand how criminologists can use this survey to explore relationships between the different items. So, criminologists may use this survey to see the relationship if people in society who have a high chance of being a victim of cyberbullying from their experience and behavior, it will affect the chance that people can also be cyber offenders in the future or not. Because the question that asks in the survey can show the result of how people can have a high chance to be offenders and victims of cyberbullying then it makes criminologists can use that result to analyze the relationship between them. Moreover, criminologists may also find the relationship between emotions and the chance to make people become cyberbullying offenders because the survey also asks a question that relates to the feeling and emotions of people that relate to cyberbullying. That is something I think criminologists can use this survey to explore relationships about cyberbullying.

Module 14 Journal 2: Digital Forensics | Davin Teo | TEDxHongKongSalon – YouTube Watch this video and think about how the career of digital forensics investigators relates to the social sciences. Write a journal entry describing what you think about the speaker’s pathway to his career.
After I watch the TEDx talk about the digital forensics investigator career by Davin Teo, it makes me interested and know more about the digital forensics investigator career. I see that is the career that directly relates to social science principles. For the principle of relativism, it shows it is a career that affects to the justice system in the present day because digital forensics investigators help the court to keep and analyze the evidence in cyberspace. It is a career that also relates to objectivity and ethical neutrality principles because people who have a digital forensics investigator career need to work with the justice system so they should not have a bias or be unethical when they do something in this career. Moreover, this career also needs to have parsimony and empiricism principles which should present the information they found simply as possible to make people easy to use it as evidence and understand and doesn’t rely on an opinion or hunch but uses digital forensics process and tool to find the evidence which is real to sense. So, I think it is an interesting and flexible career that has many ways to become a digital forensics investigator career because the speaker before he becomes a digital forensics investigator, he also has a career as an accountant with a passion for technology. It makes me recognize that everyone can be a digital forensics investigator career if they have enough motivation or passion for technology and cyber staff.
