Skill # 1
Introduction
Network Security & Threat Prevention is at the heart of keeping information safe. Data constantly moves between devices and systems. Without the right protections, it can be stolen, changed, or blocked. In my studies, I have learned how to protect information as it travels across networks, identify weaknesses before they are exploited, and apply security measures to stop attacks before they start.
This skill combines technical knowledge with strategic thinking. You must understand how networks are built and how attackers try to break into them. You also need to know which defenses will work best in different situations. The artifacts on this page show my ability to design secure network structures, analyze risks, and create defenses that respond to the changing threat landscape.
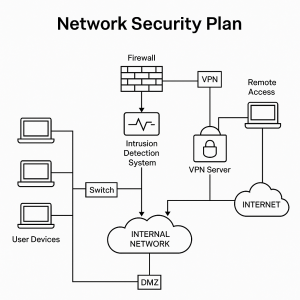
Artifact 1: Network Security Plan
Description:
This project involved creating a detailed security plan for a medium-sized organization’s internal network. I included firewall rules, intrusion detection systems, and access control policies. The plan explained how each security measure protected the network from specific threats such as malware, phishing, and unauthorized access.
Reflection:
This artifact shows my ability to think about security from the ground up. I had to consider both the technical setup and the human factors. For example, even the best firewall will fail if users are tricked into giving away passwords. I learned to balance hardware, software, and training as part of a complete defense strategy. This experience will help me in real-world jobs where I need to protect networks of different sizes and purposes.
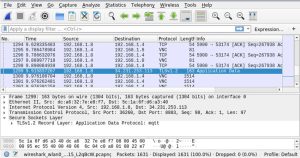
Artifact 2: Packet Analysis Report
Description:
In this lab assignment, I used Wireshark to capture and analyze network traffic. I identified normal patterns as well as suspicious activity that suggested possible attacks. The report explained what the captured data meant and how it could be used to detect and stop threats.
Reflection:
This artifact shows my skill in monitoring and analyzing network traffic in real time. Packet analysis is a core skill for detecting attacks early. I learned how to filter through large amounts of data to find the pieces that matter. This skill is directly relevant to jobs in Security Operations Centers where quick detection and response can prevent major damage.
Snippet from the report:
Intro blurb:
This report shows how I captured and analyzed live network traffic to detect suspicious behavior. I used Wireshark to identify normal patterns and then filtered for anomalies such as unusual ports, malformed packets, and repeated authentication failures. The findings show how to separate noise from signal and turn raw packet data into clear security insights.
At-a-glance:
- Tools: Wireshark, PCAP filters, protocol dissectors
- Focus: HTTP/S, DNS, TCP handshakes, ARP, and TLS negotiation
- Detections: Repeated SYN packets without ACK, DNS queries to known bad domains, and plaintext credentials in misconfigured test traffic
- Outcome: Alert rules proposed for SOC playbooks and a set of tuned display filters for faster triage
“Filtering suspicious DNS traffic. Queries to a sinkholed domain clustered within a 2-minute window suggested automated beaconing.”
“Packet captures revealed a burst of DNS queries using randomized subdomains. The pattern and timing aligned with typical C2 beaconing. Blocking the egress domain and adding a detection rule for high-frequency NXDOMAIN responses reduced false negatives in follow-up tests.”
For accessibility:
“Wireshark capture showing DNS requests to a suspicious domain with time-sequence spikes and filter bar highlighting ‘dns and frame.time_delta > 0.5’.”
Filter Cheatsheet box:
tcp.flags.syn == 1 and tcp.flags.ack == 0
dns.flags.rcode == 3
http.request.method
tls.handshake.extensions_server_name contains “example.com”
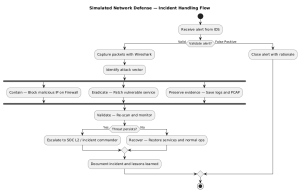
Artifact 3: Simulated Network Defense Project
Description:
This hands-on exercise was part of a cybersecurity lab simulation. I was given a virtual network that was under attack. My task was to identify the vulnerabilities, apply security patches, and strengthen the defenses. The simulation measured how quickly and effectively I could secure the network.
Reflection:
This artifact highlights my ability to respond under pressure. The simulation required quick thinking and knowledge of multiple security tools. I had to patch systems, configure defenses, and test the results while attacks were still happening. This mirrors the real-world situations where time is critical. It showed me that preparation and practice are key to successful threat prevention.
Closing Reflection
Network Security & Threat Prevention is a skill that combines planning, analysis, and quick response. The three artifacts on this page each show a different part of that skill. The Network Security Plan focuses on building strong defenses from the start. The Packet Analysis Report shows the value of constant monitoring. The Simulated Network Defense Project proves the need for rapid action during an attack.
These experiences have prepared me to take on real-world challenges in cybersecurity. They have taught me that protecting a network is never a one-time task. It is an ongoing process that requires constant learning and adaptation. This is why I am committed to keeping my skills current and ready for whatever threats may come next.