Internet of things and Networking sounds synonymous subjects along the complementary discipline of Cybersecurity. They principally exist in the same line of structure. Internet of things refers to a communication of collected network enabled devices; networking is what enables all electronic devices to connect each other; Cybersecurity is there to secure the system which has a need to always be connected. The relationship among these three technological apparatuses , range and scope of technological importance, the dynamic they play on each other, promises they often deliver and the challenges they present and the tools they offers for a solution, are some of the mechanisms which enable our technologically aided day to day life possible. The chemistry between these three apparatus can briefly understood in a way that internet of things connect systems of smart appliance, systems of application, computer peripherals, home security systems, cameras, printers etc. These technically are enabled, by networking- in the network structure by means of different network systems like Wi-Fi, blue tooth, and near-field communication (NFC). Then these advantages gained through correlations on the other hand create a gateway for vulnerability, potentially of creating a communication flaw to the point of cyber-attack. Cybersecurity provides measures to protect, prevent and secure internet connected devices, network and data from unauthorized access.
Key Words: 1- Internet of things 2-Network 3-Cybersecurity 4- cyber-attack 5- Security
Introduction:
In this era of technology, the interconnectivity of things is ubiquitous. Internet of things is almost in every device. On 19 November 2020, the number of internet of things connections was about 12 billion exceeded the number of connections without internet of things and by 2025 it is expected to be more than 30 billion internet of things connections (Amir Djenna). The success of this interconnectedness is undeniably noticeable. It’s the fastest growing technology, with the ability to offer different connectivity services. It fills almost every aspect of the so called our modern life. Its connectedness covers area of business, healthcare, education, finance and marketing. At the core of every internet of things is network of devices which are in a model of sharing information and data. Internet of things meet the network of networks also called the internet here. This vast interconnectedness of devices has in contrary served as a gateway for many threats and cyber-attacks. When devices are always open to receive information or data from other devices (internet of things), the chances of these devices being connected to be hacked or criminally attacked is a possibility. This raises an enormous security challenges and threats to the increasingly connecting number of devices. Cybersecurity as a subject is in the frontline to challenge the security weaknesses and vulnerabilities arises with in networks and internet of things. It protects a system, information and data from unauthorized access through methods of maintaining high confidentiality, integrity and availability of information.
Internet of Things:
Internet of things is the interconnection of physical moving objects “Things” through internet embedded with an electronic chip, sensors, and other forms of hardware (Farhan Ullah). It also refers to a name for the aggregate collection of network-enabled devices, excluding traditional computers like laptops and servers (Kenton). In the current state of technology, Machine-to-Machine (M2M) is the most popular application form of connecting things. These remote-monitor enabled machines, which consist of a unique Radio frequency identifier tag (RFID), are communicating on node connections. IP, TCP, SMPT, protocols which identifies a computer in World Wide Web are the protocols used here in Internet of things for communication. Internet of things offers connectivity to a broad range of objects from security systems, smart appliances, smart speaker, routers, service industries, cloud computing and applications. This connectivity brought countless advantages in many area of our daily life. Internet of things centered technologies has advance in developing urban planning, smart education systems, businesses, banking, health, medicine, industries, and entertainment which essentially aid the over wellbeing of human. For example an advantage of internet of things we all familiar with, a sensor with an IP address placed in a busy city street alert us with the upcoming message regarding a road condition, traffic or an accident, plays a vital role in creating convenience. Similarly in medicine and health the promise of internet of things is enormous. A patient can be monitored inside and outside hospital settings with the help of Internet of things-convenience through sharing data and information. Smart devices of internet of things are also used as a means of competitive advantages in a business strategy. Data tracking advantages from internet of things can for example notify a business an inventory level of its products which can help the business to make smart decision accordingly.
Networking:
Network simply refers to things connected. In the context of computing, networking represent the same version of idea, connected devices. In a network, two or more devices are connected in such a manner that enables them to share data and information with each other. Network as a whole composed of mainly four basic components, network devices, network media, network interfaces and network protocols. Devices can be phones, TV, printers, security camera, computer chips, sensors, servers etc. These devices can be connected in a different environment of network media. It can be wired or wireless. Wired network environment may use copper wire, electrical signals, fiber optics, light pulse, while wireless medium uses wireless connection and radio waves. For the proper network functionality devices should be equipped with appropriate network interface to convert the digital signals to a signal suitable to be transmitted through the network and eventually create a connection through the network. Network adapter integrated in to a devices mother board for example is the interface which enable wired network possible. Network protocol is an agreed set of rules on how information is received, organized, handled, formatted and sent in a network. Computers having different operating systems are configured to communicate each other through the same the rules of protocols. TCP, SMTP, HTTP, FTP are some of the known protocols used in a networked devices. Structurally, based on the levels of area coverage, networks can be designed in to three main major types LAN, MAN, and WAN. LAN connects a computer to workstation through switches for the purpose of sharing data, resources and programs in a house or office setting. MAN covers larger geographical area than LAN, with more computers and devices in it. WAN covers the largest geographical area, with in a country or out of country connections. VPN, EPN, PAN and SAN are also networks settings with in their own specific accord. In this technological era a vast progress in device networking has significantly changed how we live our life and accordingly we find networking deeply integrated in to our everyday life, such as determining the right way in a road, hourly weather report (satellite), electricity delivery and video streaming services. Honestly these times, no network means no-thing getting done.
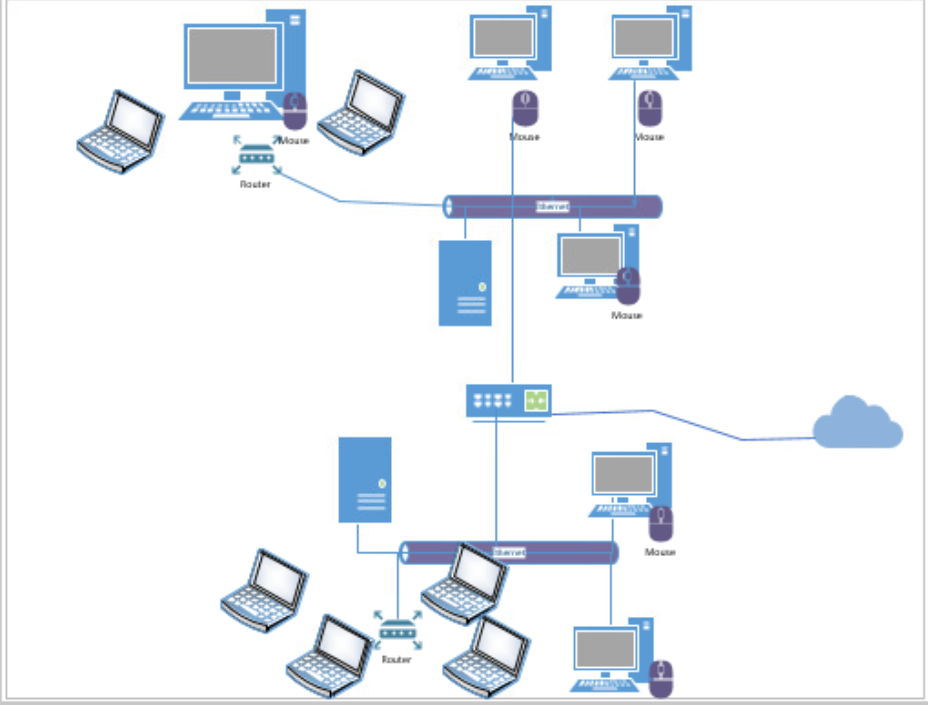
Cybersecurity
In simple terms, Cybersecurity refers to a set of practices used to protect computers, servers, mobile devices, various electronic systems, communications, networks, data and information from unauthorized access, malicious attacks and threats (Investopedia). Cybersecurity protects system and everything in it mainly from cyber-attack, information privacy extortion, information disclosure, data theft, information damage, system disruption and denial of services. With the world continuous reliance on technology and increasing creation of data and information ecosystem, Cybersecurity solutions has become the key for the CIA triad, confidentiality, integrity and availability of data and systems in the cyber world. Cybersecurty techniques and methods attempt to give privacy and security solution for individuals, businesses, governments and organizations. According to McAfee report, with the ten common attacked sectors of the critical infrastructure being government, manufacturing, transportation, oil and gas, energy and utility, health, financial services, legal, education, media and entertainment, until 2020 the total loose of Cyber-incidents are accounted to staggering one trillion dollars. These incidents are increasingly becoming complicated and sophisticated in nature which is talking a lot of resource and money. Hackers and criminals are using malware, phishing, man in the middle attack, denial of service attack, password attack etc. to disrupt, deny network systems or steal data and information. Malware use downloaded Trojan, spyware or adware viruses to get in to a system. Phishing attacks get to a computer by tricking a user to click in a fraudulent email which appears to have been sent from a legitimate person. Man in the middle attack occurs when a hacker intercepts the information path between two ends. Denial-of-service is an attack targeting devices, information systems, and other network resources to prevent legitimate users from accessing services and resources by means of flooding the two end devices to the point of system blackout or crash. Password attack is simply an authentication escape method by guessing a commonly used password or trying all possible alphabetical combinations. Cybersecurity tackles to provide solutions for strengthening system-networks through installing and creating system firewalls, using antivirus soft wares, applying safe practices to avoid fraudulent emails and enforcing stronger password policies.
Conclusion:
The role internet of things and networking plays in the interconnectedness of devices is inevitable. For the purpose of creating convenience communication and sharing data among devices will continue to increase. The security challenges arise with this constant interconnectedness will continue to be complex and sophisticated. Cybersecurity should understand the overall structure of networking and internet of things and modify and develop adequate solutions to tackle the system and network vulnerability and weakness which are currently a challenge. The amount of dollars wasted in short of these solutions is huge. Wired and wireless network are without a doubt the pathway with in the network in the communication of internet of things. Any resolution to secure this line of connection will for-example removes the frequently used attacks, man in the middle attack and denial of service attack and this eventually can be a huge success. Finally Cybersecurity hand in hand with the fortune internet of things and networking will create a sound and manageable world of interconnected devices and systems.
Reference:
• Farhan Ullah;Hamad Naeem; Sohail Jabbar; Shehzad Khalid; Muhammad Ahsan Latif; ‘’ Cyber Security Threats Detection in Internet of Things Using Deep Learning Approach’’ IEEE, 26 August,2019.
https://ieeexplore.ieee.org/abstract/document/8812669
• W.Kenton, “The Internet of Things’’, Investopedia, May, 28,2021
https://www.investopedia.com/terms/i/internet-things.asp
• Brian Russell, Drew van Duren, ‘’Practical Internet of Things Security’’, Packt publishing, June, 2016.
• Mohamed Abomhara and Geir M. Køien,’’ Cyber Security and the Internet of Things:Vulnerabilities,Threats, Intrudersand Attacks’’, Rivers Publishers, 22 May,2015.
https://journals.riverpublishers.com/index.php/JCSANDM/article/view/6087
• Radanliev, P.; Mantilla Montalvo, R.; Cannady, S.; Nicolescu, R.; De Roure, D.; Nurse, J.R.; Huth, M. Cyber Security Framework for the Internet-of-Things in Industry 4.0. Preprints 2019, 2019030111 (doi: 10.20944/preprints201903.0111.v1).
file:///C:/Users/END%20USER/Downloads/preprints201903.0111.v1.pdf
• Amir Djenna ,Saad Harous , Djamel Eddine Saidouni, ‘’ Internet of Things Meet Internet of Threats: New Concern Cyber Security Issues of Critical Cyber Infrastructure’’ , Misc Laboratory, College of New Technologies of Information and Communication, University of Constantine 2, Constantine 25000, Algeria, 7 May,2021.
https://www.mdpi.com/2076-3417/11/10/4580/htm
- Zhanna, Smith; Eugenia, Lostri; ‘’The hidden costs of cybercrime’’; 20, Dec, 2020
https://www.mcafee.com/enterprise/en-us/assets/reports/rp-hidden-costs-of-cybercrime.pdf
Robert J. Walls, Patrick McDaniel;’’ Building an Ontology of Cyber Security’’
http://citeseerx.ist.psu.edu/viewdoc/download?doi=10.1.1.664.3593&rep=rep1&type=pdf
Birhane: compiled and researched for project