Journal Entry #1: NICE Framework
After looking into the Workforce Framework for Cybersecurity (NICE Framework), I’ve realized that I’m really interested in roles related to Oversight, Governance, Investigation, and Cyberspace Effects. My military background has given me a strong interest in Oversight and Governance, and I’m also excited about management and bringing creative ideas to the table.
In particular, I find cybersecurity workforce management, policy and planning, and executive cybersecurity leadership to be super fascinating. I’m also drawn to Secure Project Management, Technology Portfolio Management, and Technology Program Auditing because they blend cybersecurity with business practices in a way that I think is really cool. Plus, these roles offer the chance to share knowledge through training, which can help employees improve their personal security.
Conversely, I find work roles within protection and defense, such as digital forensics and infrastructure support, less appealing. Additionally, I find work roles within the implementation and operations to be less engaging.
Journal Entry #2: How the Principles of Science relate to Cybersecurity
The principles of science are crucial to understanding cybersecurity and its relationship with technology. Relativism highlights how technology and cybersecurity evolve together; as tech advances, so do security measures. Objectivity emphasizes the need for unbiased approaches, focusing on the broader benefits rather than personal opinions. Parsimony ensures that cybersecurity concepts remain simple and understandable, providing a solid foundation for broader practices. Empiricism stresses that security solutions must be practical and grounded in reality, not just theoretical. Ethical neutrality ensures that cybersecurity is designed for the greater good of all users, not just specific groups. Finally, determinism shows that external events and social influences can impact how cybersecurity is implemented and adapted to best serve the common good.
Journal Entry #3: PrivacyRights.org
PrivacyRights.org offers valuable insights for researchers studying data breaches. The site’s well-organized layout categorizes breaches by type and frequency, which facilitates comprehensive analysis. Additionally, the interactive map of the United States highlights states with higher incidences of breaches and cyber crimes. Many of these areas are federally funded or have larger populations and/or a significant presence of Fortune 500 companies. This detailed information, including trends and patterns is crucial for researchers aiming to develop effective strategies to enhance system security and safeguard both individuals and corporations from potential future breaches and cyber attacks. It provides a solid foundation for improving cybersecurity measures.
Journal Entry #4: Maslow’s Hierarchy of Needs
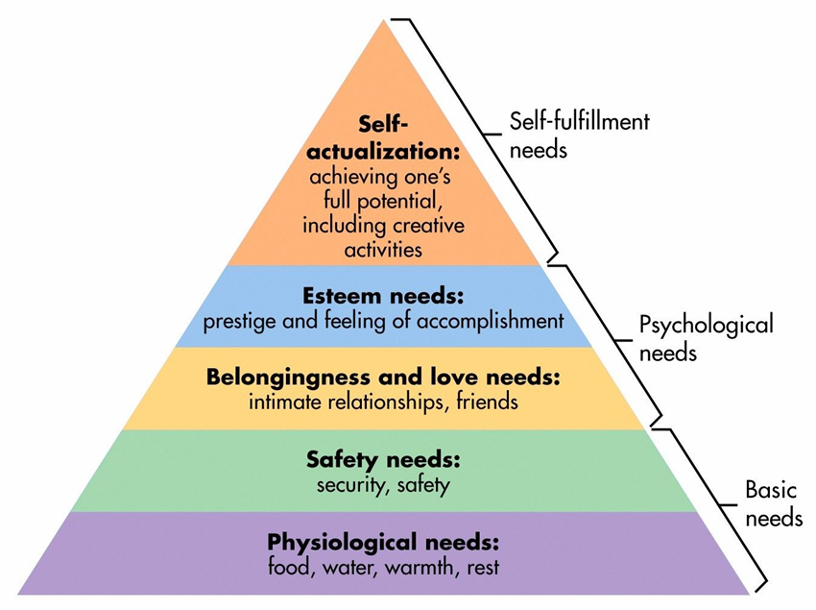
Maslow’s Hierarchy of Needs really reflects my experiences with technology in a meaningful way. I primarily use tech to manage my health, relying on devices like my Whoop and Apple Watch to keep an eye on my vitals. This not only meets my physiological need for wellness but also gives me the power to stay within optimal health parameters. At home, technology is key to my sense of security. My security system and the advanced features on my phone make me feel safe, whether I’m sleeping or just relaxing alone. Knowing that my personal data is secure as well as my home adds another layer of reassurance and peace of mind. Staying connected with loved ones is essential for me, too. Whether I’m video chatting with family in Texas or catching up with my wife and daughter, technology keeps those relationships strong, even when we’re apart.On the professional side, sharing my achievements on LinkedIn and receiving congratulations from others really boosts my self-esteem and motivates me to keep pushing forward. Plus, I love exploring the internet for topics I’m passionate about and diving into online gaming, which brings a sense of fulfillment and personal growth. Overall, technology not only meets my basic needs but also adds richness and depth to my life.
Journal Entry #5: Motives Behind Cyber Crime
- For Money – I believe for money is the biggest motive behind cyber criminals. Because without money I do not believe most criminals would participate in it, but since there’s a lot of money in doing “dirty work”. They tend to be drawn to it.
- Political – Political view is a very prominent reason cybercrime happens as well. Weather it’s the country themselves or society within political affiliations it tends to be very common. Especially in today’s day and age.
- Multiple Reasons – This is a very interesting motive because it can be a mixture of both motives ahead of it. I do believe that most cybercrimes do have multiple motives behind them majority of the time.
- Revenge – Revenge is a motive that I would like to think is common with big companies. Firing employees without a honest reason why could lead them to react in a violent way especially if it involves changing their financial status or effecting their family.
- Entertainment – most internet trolls do this out of spite just because they like to see others afraid of the possible consequences. Especially within online chat rooms and gaming communities.
- Boredom – Just having the ability to do something with nothing to keep you occupied could lead someone in committing a cybercrime just because they could be curious or not even knowing they are committing a crime. They could have no malicious intent behind it.
- Recognition – There are groups of hackers or individual out there that come to the light when needed for recognition and to show their presence. Also, individual could do cybercrime in hopes that it could give them the recognition they need to possible get a job or draw interest of other people within the cyber community.
Journal Entry #6: Fake Websites
In exploring fraudulent websites masquerading as reputable brands, I’ve come to appreciate the necessity of vigilance in the digital age. I began with Brooks Running, where the official site, brooksrunning.com, presents a polished and professional interface. In contrast, I encountered a counterfeit site: BrookShoeOutlet.com. Immediate red flags emerged, notably Brooks’ confirmation that they do not operate outlet stores, effectively nullifying the legitimacy of this site. Additionally, the misnaming of the brand spelling “Brooks” as “Brook” was a glaring indicator of unprofessionalism. A plethora of online complaints from users questioning the site’s authenticity further underscores its dubious nature. Next, I turned my attention to Hoka. The official website, hoka.com, is sleek and user-friendly, while the fraudulent counterpart, OnlineHokaSale.com, displayed numerous grammatical errors and an overall unrefined design that resembled an amateur endeavor. The site boasted significant discounts, such as offering the Women’s Bondi 8 shoes for just $39.89, a stark contrast to their retail price of $165. Such deals are often a hallmark of scams, reinforcing the adage that if something seems too good to be true, it likely is. Finally, I investigated PayPal, with its authentic site located at paypal.com. Here, I found another counterfeit: Pay-Pail.com. The misspelling alone raised immediate suspicions. Compounding this issue, the site lacked HTTPS encryption a critical feature for any financial platform. Furthermore, it offered only one language option, which is atypical for a globally recognized service.These findings have been profoundly illuminating.
The sophistication of some fraudulent sites is alarming, revealing how easily consumers can be misled. This experience serves as a vital reminder of the importance of thorough scrutiny and verification before disclosing personal information online. Awareness of the common signs of fraud can significantly mitigate the risks associated with digital transactions.
Journal Entry #7: Cybersecurity memes

This meme shows you the exact reaction I person would have if they were to use public wifi are no regard. The Wi-Fi is possibly monitored and you are an easy target for being hacked.

This meme directly relates to majority of employees in companies due to how they like to use simple passwords usually containing PII or other sensitive information due to the fact that it’s easy to remember or they have specific attached to it.

This meme demonstrates that you should watch carefully on that websites you are browsing to because not all of them could be secured, which could lead to stolen data such as credit card information or other PII.
Journal Entry #8: Hollywood Cybersecurity
Media shapes our understanding of cybersecurity in ways that often portray it as chaotic and intense. For someone who only sees it through movies or TV shows, it can seem like a world of hackers and criminals constantly stealing and breaking into infrastructure. While there’s some truth to this depiction, it overlooks the broader landscape of cybersecurity. The portrayal often suggests that hacking is both incredibly complex yet somehow accessible to those who “get it,” making it seem like a split-second infiltration can bring down major corporations. In reality, a sophisticated hack typically requires months, if not years, of meticulous planning to execute successfully not just a quick effort from a local coffee shop.
Journal Entry #9: Social Media Disorder Scale
I believe I did relatively good getting a 2/9 score. I believe the items are this scale are actually interesting and more common than people would like to think so. Social media is very addictive and can’t lead to many hours of “doomscrolling”. I believe that different patterns are found across the world depending on the country you live in and the social media restrictions that region of the world might have especially when compared to the United States.
Journal Entry #10: National Security Requirements
The article highlights the increasing importance of information and psychological warfare in modern conflicts, as emphasized in Russian military doctrine, which predicts that future wars will be shaped by efforts to control information and undermine the morale of both military forces and civilian populations. It argues that a nation’s greatest vulnerability lies in its internal weaknesses, with adversaries seeking to exploit divisions within society and erode trust in its institutions, including the military. To counter this, military leaders must understand “social cybersecurity,” which involves defending against external efforts to manipulate or destabilize the internal information environment. A central tactic of adversaries is to create distrust between military forces and civilian leadership, weakening societal cohesion and making it more susceptible to foreign influence.
The article also stresses the need for military leaders to actively promote American values both domestically and internationally, engaging in the global “marketplace of ideas” through both direct, on the ground interactions and online platforms. However, to do so effectively, current military policies surrounding information operations particularly in the use of social media tools and Application Programming Interfaces must be more flexible and better defined. The article calls for the development of agile policies that allow for rapid, ethical maneuvering within the information domain while ensuring privacy protections and adhering to the legal boundaries of the Department of Defense; it also advocates for a comprehensive educational approach to social cybersecurity, aimed at both military personnel and the broader public. It is crucial to raise awareness about the risks of misinformation and the importance of critically evaluating the information that shapes public perception. Addressing social cybersecurity requires a multidisciplinary strategy that integrates policy, technology, and public education to effectively defend against the threats posed by external manipulation. As information warfare continues to evolve, the article argues that a coordinated, proactive effort to safeguard against these threats is essential for maintaining national security and societal trust.
Journal Entry #11: Social Behaviors in Cybersecurity Analysis
What i got from the video was that as a cybersecurity analysis you are the front line defense when it comes to cyber security. Rather that is with making the company more aware of cyber threats to training, scanning the network as a daily task or implementing policies and STIGS within the company. You main job is to analyze and protect the company by knowledge and vigilance. This role requires more social skills than other technical roles due to the fact that you will be hands on with the employees of the company as well as issuing of equipment in some cases. This role also allows you to understand the culture of the company and use that to also influence the way to decide to use best practices to protect the company.
Journal Entry #12: Social and Economic Theory in Data Breach Notification
The data breach described in the letter can be understood through a few key economic and social science theories. From an economic standpoint, Principal-Agent Theory helps explain the relationship between the website operator and the third-party platform provider . In this case, the platform provider was responsible for securing customer data, but failed to do so, leading to the breach. This creates a conflict because the platform provider didn’t act in the best interest of the website operator or its customers. This theory points out the importance of making sure agents are properly monitored and incentivized to prioritize security. Another relevant economic theory is Transaction Cost Economics, which focuses on the costs involved in the breach. For the business, there are immediate costs related to fixing the problem and communicating with customers, as well as longer-term costs like damage to its reputation. For customers, the costs include things like replacing credit cards, checking accounts for fraud, and dealing with the inconvenience of the breach. This theory highlights how important it is to invest in strong security upfront, to avoid these expensive and time consuming costs later.
From a social science perspective, Social Exchange Theory helps us understand how the breach affects the relationship between the business and its customers. This theory is based on the idea that people engage in exchanges where they expect to get something in return for what they give. In this case, customers gave their personal and financial information to the website in exchange for products. The breach violates that trust, as customers now face risks like identity theft, and the company has to work to restore the balance of this exchange. This is where Trust Theory comes in, suggesting that the breach undermines customer trust in the company. When trust is lost, customers may be less likely to make future purchases, or they may hesitate to share personal information again. The company’s efforts to notify customers and offer protective measures are part of an attempt to rebuild that trust. However, whether customers feel confident again will depend on how seriously the company commits to improving its security moving forward.
In Conclusion, both economic theories and social science theories help us understand the impact of the data breach. From the economic side, the breach creates financial and operational costs, and from the social side, it damages the trust and relationships between the business and its customers. The company’s response is key to managing both the immediate fallout and restoring longer term trust.
Journal Entry #13: Effectiveness and Challenges of Bug Bounty Programs
The article provides valuable insights into bug bounty programs, focusing on factors that influence the number of valid vulnerability reports companies receive. The literature review serves as a solid foundation, reviewing previous studies on crowdsourced cybersecurity and highlighting gaps in the existing research, particularly in understanding hacker behavior and program effectiveness. The review emphasizes how past studies often fail to account for endogeneity, which the article addresses by using a comprehensive dataset to isolate key variables.
The discussion of findings brings several noteworthy points. First, the finding that hackers are relatively price-insensitive challenges the common assumption that higher rewards always drive more participation. It suggests that factors like reputation, challenge, or personal motivation may play a larger role. Additionally, the article finds that bug bounties work well for companies of all sizes, but certain industries receive fewer reports, indicating potential barriers or lack of appeal. The study also raises concerns about diminishing returns, as programs seem to get fewer valid reports over time. Overall, while the findings make significant contributions, the article acknowledges the need for further research to better understand the dynamics of hacker supply and the long-term sustainability of bug bounty programs.
Journal Entry #14: The Illegal Uses of the Internet
Among the most serious violations internet users can commit, child pornography ranks as the most reprehensible due to the severe harm it inflicts on vulnerable minors and its lasting impact on their lives. The distribution, creation, or possession of such material is not only deeply unethical but also illegal across most jurisdictions, often resulting in severe criminal penalties. Torrenting, particularly when it involves pirated content, is also a significant violation as it infringes on copyright laws, deprives creators and companies of revenue, and encourages illegal distribution of media. Online bullying, including harassment, threats, and defamation, can cause long-lasting emotional damage to individuals, leading to severe consequences like depression, anxiety, and even suicide in extreme cases, making it a serious social issue. The illegal capturing of photos, particularly in private or sensitive contexts without consent, violates privacy rights and can lead to exploitation or blackmail. Lastly, creating and using fake identities online for fraudulent purposes, including scams or identity theft, compromises the trust and security of the internet, causing significant financial and emotional harm to victims. These violations are serious because they involve ethical breaches, legal consequences, and, often, severe harm to individuals or society at large.
Sources:
https://clario.co/blog/illegal-things-you-do-online/,
https://clario.co/blog/illegal-things-you-do-online/
Journal Entry #15: Reflecting on a Digital Forensics Investigator’s Career Path
I recently watched a video about a digital forensics investigator who started his career in a totally different field. His journey was super inspiring! He started out apart of a finance team and while part of this team they needed someone tech-savy to handle the IT portion of their job , and over time he transitioned into digital forensics due to his strong interested in IT now. It was amazing to see how his curiosity and passion for technology led him to become part of Australia’s first digital forensics team. What really caught my attention was how his background in finance, combined with his IT skills, helped him bridge two important fields: technology and human behavior. Digital forensics isn’t just about technical analysis; it’s about understanding the context of digital evidence, which often ties into criminal behavior and connects to the social sciences. This story reminded me that career paths aren’t always straight lines. By following your interests and being open to new opportunities, you can find success in unexpected fields. It also shows how diverse skills like finance, IT, and social science can combine to create exciting new opportunities.