Being the CISO for a publicly traded company is a massive responsibility with the company, as well as shareholders, relying upon a well formulated security thesis in order to protect the information and availability of the corporation. If I were to be a CISO focused on protect the consistent availability of a company’s systems, I would implement a multitude of protections. The types of threats to availability are seemingly infinite in today’s cyber-run world. From DoS, browser, port, and many more types of attacks, a diverse security plan is absolutely necessary not only to protect the other aspects of the CIA triad, but namely availability.
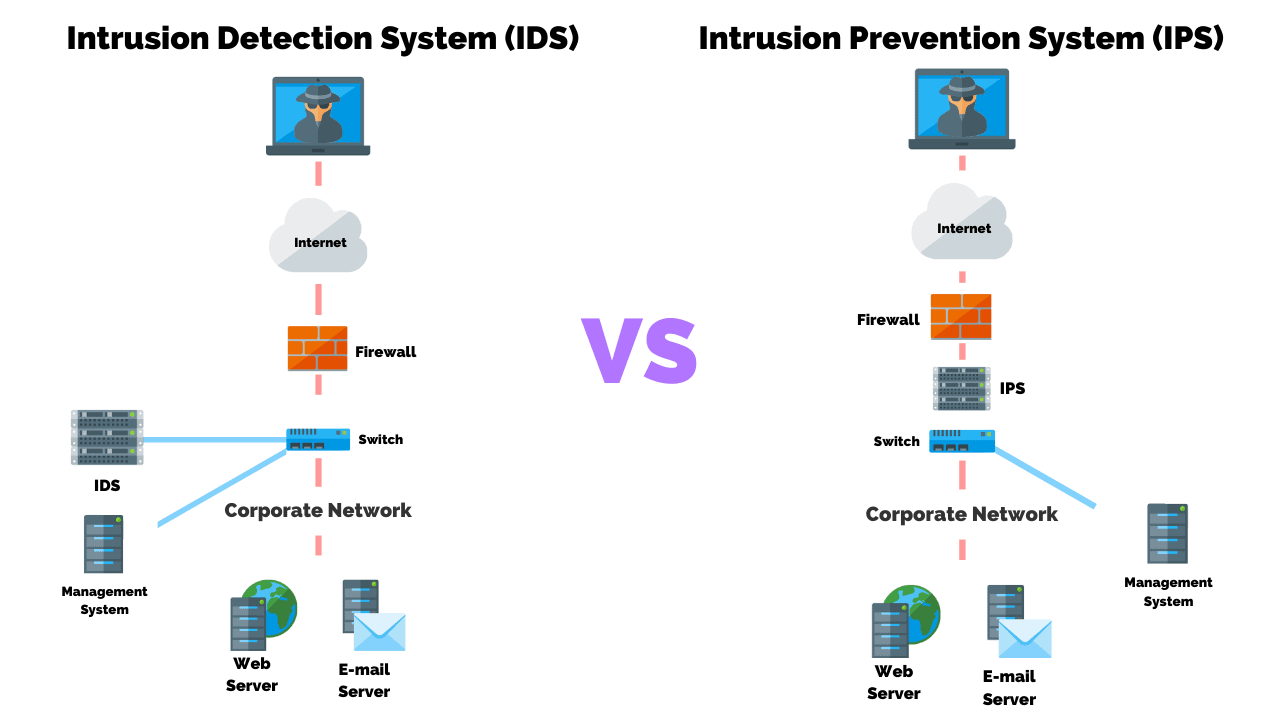
One of the first protections I would put into place would be a implementing a intrusion detection system(IDS). This software would monitor systems for malicious activities and violations of permissions, the IDS is essential to watch for attacks on the interior of the server, while the firewall protects the exterior and stops threats before they can enter a system. Implementing a strong firewall to filter and monitor traffic coming through the server is another essential protection, with firewalls being generally the first layer of protection stopping threat agents from causing damage. The firewall in place is a multi-aspect tool used to stop a number of different types of attacks, meaning any firewall put in place would have to be top-of-the-line in terms of security and diversity in order to protect the system from known types of attacks, as well as to be prepared for new ones.
Apart from hardware and software security implementations, I would also perform training programs intended to educate my employees on the many types of exploitations and cyber-attacks eligible to harm the company. Employees with access to systems would be put through mandatory training in regards to browser, e-mail, phishing attacks, and many more. The purpose being to attempt to lower the number of employees with access to company data and systems falling for something such as a browser attack which could let malware or other threat agents into the companies systems.
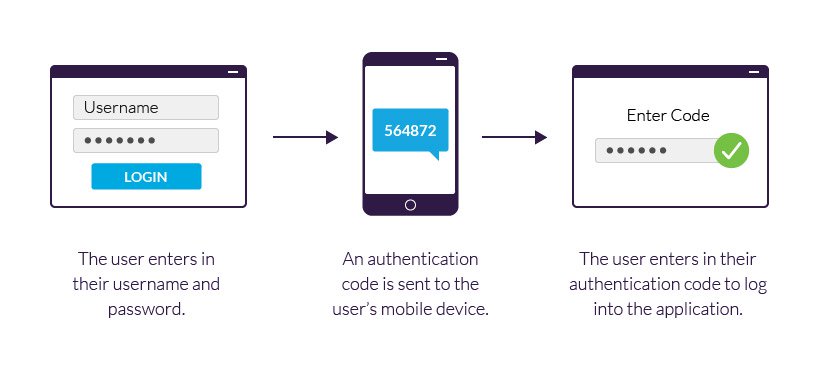
Lastly I would implement two-factor authentication for all work logins as well as a strict access control mechanism for all work personnel. This being to ensure that only persons with permission to be in and working on the systems are able to access and edit company data.