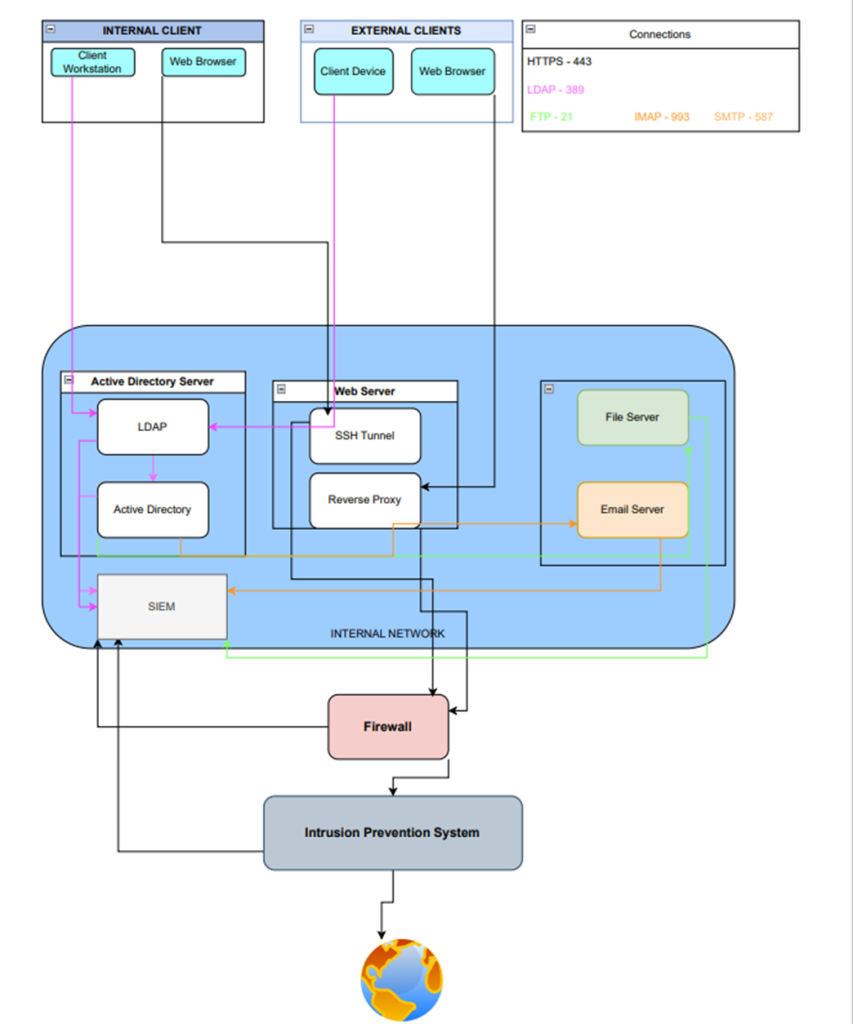
Network Diagram Risk Management Standard
Network Design
Client Devices
- Company workstations are to access the network resources through the Active Directory Server, first being authenticated by Lightweight Directory Access Protocol (LDAP), and directed to resources using Active Directory on the server.
- All web traffic is communicated through SSH encryption connecting to the SSH tunnel in the Web Server.
- External Client devices use the reverse proxy to reach file and email resources on the internal network.
Network Monitoring
- All traffic running through the network is monitored by the SIEM through information and alerts including the Email Server, File Server, Active Directory Server, Firewall, and Intrusion Prevention System
Roles and Responsibilities
Information Security Officer
- Establish and Implement Network Security Standards and Policies for the Organization
- Verify System Functionality Periodically along with consistent updates and upgrades to maintain system functionality.
- Development of Guidelines and Incident Response Plans as well as Policies for User and Device Privileges communicated to the System Administrator to be enforced.
System Administrator
- In charge of Network Monitoring, Auditing, Security Event Management
- Enforce Security Awareness Training for Employees, direct if needed.
- User Account Management including setting permissions based on Principle of Least Privilege, Group Policy Management, and Access Management
Wi-Fi and Routing
Routers
- Routers can only be configured by the System Administrator or Information Security Officer Accounts, password protected.
- Router discovery should be disabled.
- All Routers are to be configured with WPA2 Encryption and be password protected, and all login attempts are to be logged on the SIEM.
- SSID Broadcast should be disabled.
Firewalls
- Should be configured to deny all Inbound Connections and allow all Outbound Connections on all firewalls.
- The Access Control List should be updated regularly allowing only the applications needed for the network and business to function.
Switches
- Layer 2 Management Access is restricted to only the ISO and System Admin.
- All connections are to be hosted through SSH.
Workstations and Personal Devices
Workstations
- All user accounts must be Password Protected with a Complexity Policy of at least 15 characters consisting of letters, 1 number, and 1 special character.
- When a user vacates their workstation, it must be turned off, and automatically log them out after 10 minutes of inactivity.
- All workstation events and activities will be logged and monitored using the SIEM.
- Each user will have a specific set of permissions and privileges based on their Group Policy set by the System Administrator, and additional permissions must be requested to the System Administrator and verified by the ISO.
- Account Log-in on workstations are to be authenticated with Dual-Factor Authentication using both a password and secondary authentication using the Duo Mobile App.
BYOD Policy
- All User Mobile Devices must be authenticated on the network through the Dual Factor Authentication, and each Device’s IP address manually allowed on the network by the system Administrator.
- While on the network, each device will have restricted access to the same level of access on their workstation.
- While on the network, all of the User’s device traffic and use will be monitored through the SIEM.
- Each User can only have up to 1 device IP address associated with their account added to the network at a time along with their workstation.
Security Awareness Training
- All users will have a monthly Security Awareness Training Seminar to better understand Social Engineering Techniques and best practices for handling suspicious emails, websites and software with assistance from the System Administrator, and a yearly training exercise.