Analysis
- The AWS environment that I am specifically evaluating is the most common, which is the Elastic Cloud Computing (EC2) Web Service.
AWS Infrastructure
Amazon Web Services uses a Shared-Responsibility Model for the Security Infrastructure of their virtual environments, which works tremendously well due to its cloud-based nature. As you can see on AWS’ own model below, AWS secures the background infrastructure that allows your virtual environment to run, the storage, the database accessed and the networking side, while the Client is responsible for the security of their platform, its applications, and general security configurations that you would have on any other network. Leaving the upper layer security of the environment up to the Client allows them to manage and tweak the security based on the clients needs efficiently and effectively.
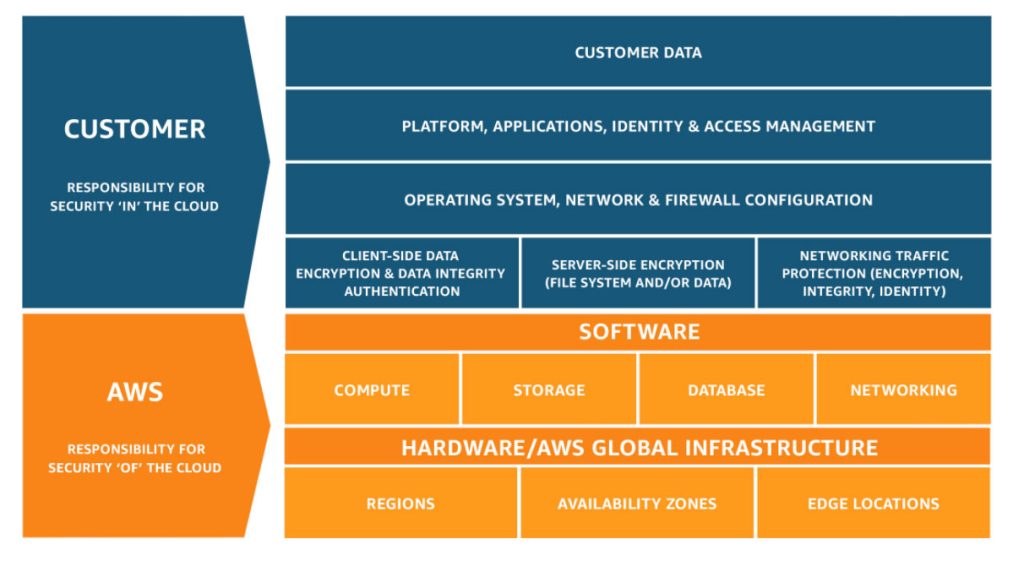
AWS Security Controls
- AWS provides heavy security within its networks, as each virtual environment has built-in Firewalls and automatically all traffic for its data storage facilities.
- AWS CloudTrail – Cloud Deployment Management Software
- AWS CloudWatch – Built-In and Scalable Network Monitoring Software
- AWS GuardDuty – Threat Detection Service that can even mitigate several threats without user intervention
- AWS IAM – Multi-Factor Authentication Service and Federated Access For virtual environments
- AWS HSM and Key Management – Amazon Proprietary Hardware Security Module and Cryptographic key Management
Possible Vulnerabilities
No Operator Access
The AWS Nitro System is the virtualization platform that the EC2 Instance uses to build its applications from. It comes with the previously mentioned security features, with one of them being a lack of AWS Operator Access because of the Shared Responsibility Model. AWS Operators are heavily limited in their access and abilities within a Client’s EC2 environment. This is not a high-level vulnerability, however this stops an AWS Operator from helping secure the environment with debugging the system. In fact, if the Client needed assistance with an issue within the environment, the AWS Operator would have to host a separate environment and try to recreate the issue on their side. Now if there was an issue such as a malicious code in the Operating System that the user didn’t know how to debug, the issue would be hard to recreate for the AWS operator.
User Misconfigurations
AWS’ Shared Responsibility Model leaves the responsibility of configuring the environment’s policies and security up to the user. This can lead to major vulnerabilities within the environment due to human error in every part of the user’s configurations. Simple issues such as not using secured ports and lacking enough authentication levels on their endpoints can create significant room for threats.