Using Snort was a great way to practice real world skills in network monitoring and automating alerts with an IPS.
Snort is a widely used open-source Intrusion Prevention System (IPS) that can use both custom set rules and community-set rules to find and analyze malicious traffic. Snort can be used as a packet sniffer, packet logger, and be a line of defense against network attacks. In this project, I will show how to download and install this free resource, as well as how to monitor and set rules for catching network traffic.
First, I recommend getting your snort account setup at www.snort.org so you can purchase the free product and be able to use.

Step 2. Download and run the Snort 2.9.20.exe to install snort on your end device.
Next, after successful download, Snort requires you to download npcap for packet captures dependency.
Make sure to download the correct version for your OS. I am running on Windows 10, so I downloaded the windows 10 version (x64)
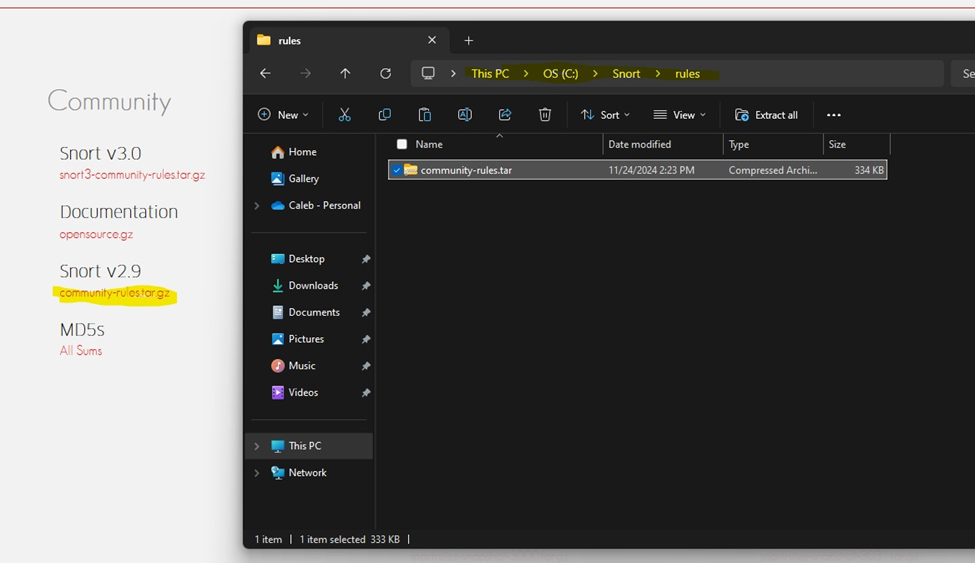
Next download the community rules from the snort website, then extract them to your snort /rules folder.
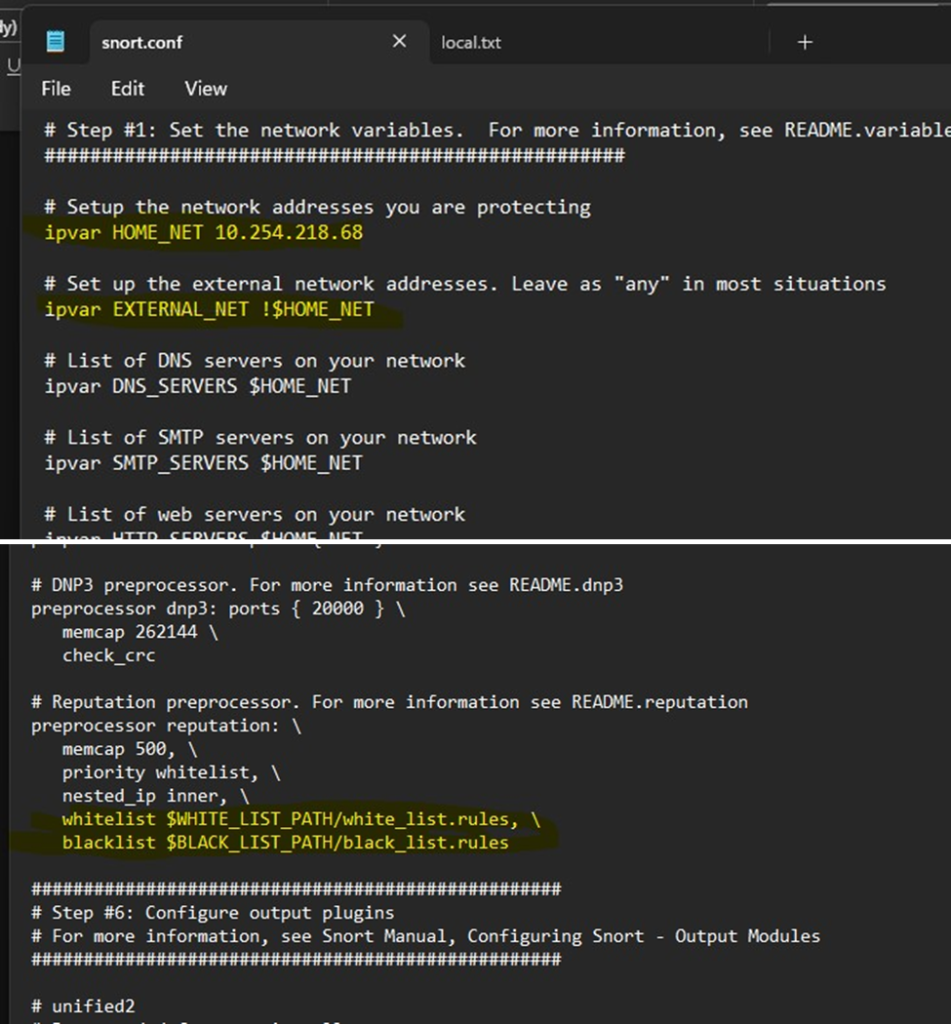
Next, open up the Snort.conf file to configure the rules for the IPS to capture traffic.
Including the host IP address, the blacklist and whitelist.
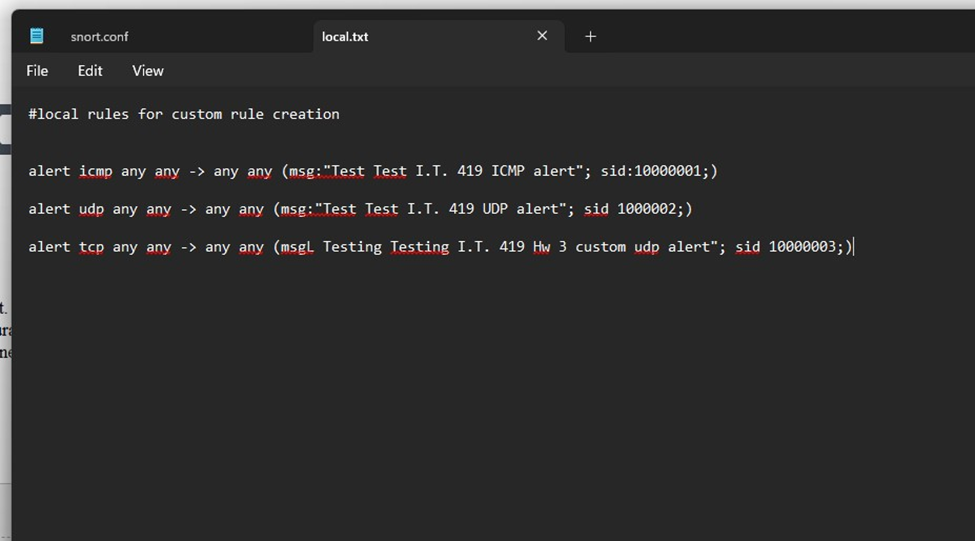
Make sure to configure the Firewall rules as well , I put them in the Snort\Rules folder.
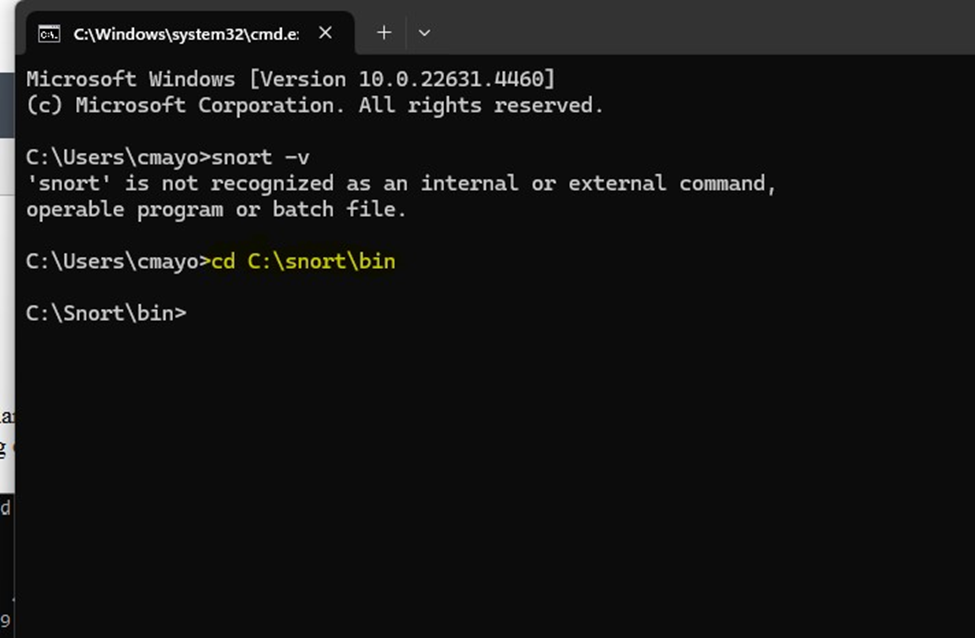
Now I am going to show you how to run snort and start analyzing traffic. First, open your command line as an Admin, and run cd C:\snort\bin to change directories to where snort is located on your host drive.
After that, use the snort –W command to verify the interfaces snort is running on. For this demonstration I will run on interface 5 as I configured it on the config file.
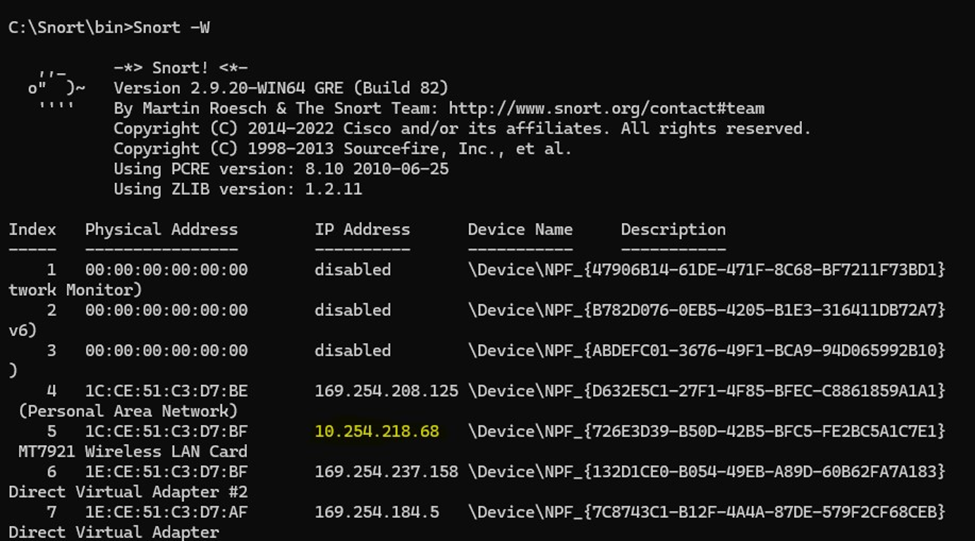
Lastly, run snort –i 4 c:/Snort/rules/bin/snort.conf -A to start monitoring the network traffic based on the config file.
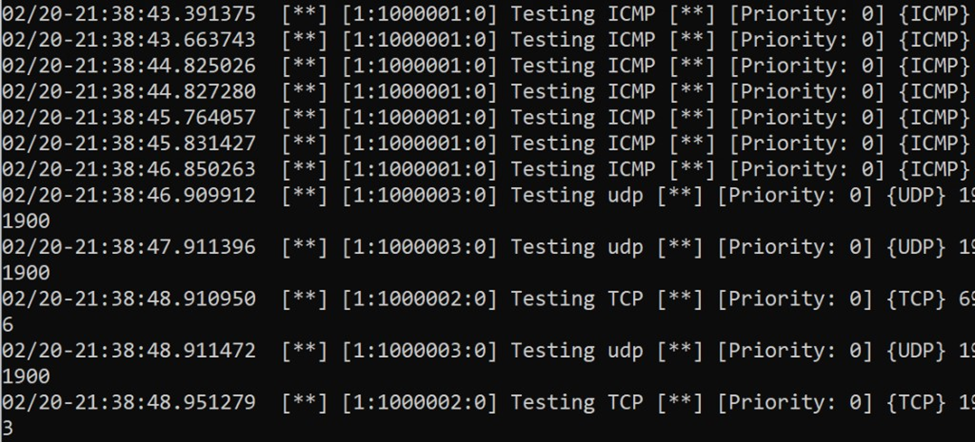
***IT should look something like this, however mine is having issues as I keep getting the same error.