CYSE201S
Journal Entry 1
Review the NICE Workforce Framework. Are there certain areas that you would want to focus your career on? Explain which areas would appeal the most to you and which would appeal the least.
I would definitely want to focus on the areas of Investigation (IN) or Protection and Defense (PD). In the Investigation (IN) work role category, both Cybercrime Investigation and Digital Evidence Analysis are both in the area of investigating, which is my main area of interest, and both give the accomplishment of solving a puzzle. The next work role category of interest would be Protection and Defense (PD), which areas of interest include Digital Forensics and Insider Threat Analysis. The work role categories that appeal to me the least would be Design and Development (DD) and Implementation and Operation (IO).
Journal Entry 2
• Explain how the principles of science relate to cybersecurity.
Relativism- The principle that all things are related to or affected by each other. Relativism could relate to Cybersecurity by helping to correlate the legal complexities that vary in cybercrime investigations.
Objectivity- The principle that scientists research topics without opinion, in an unbiased manner, with facts. Objectivity could relate to Cybersecurity when responding to and analyzing a cyber incident without preconceived stereotypes of attacker’s motives.
Parsimony- Keeping the levels of explanation as simple as possible, prioritizing simplicity. Parsimony could relate to Cybersecurity when choosing a single, well known and effective security solution to a threat, rather than layering tools that could cause redundancy.
Empiricism- The concept that only behavior that is real to the senses, and what can be experienced should be studied, and to not rely on opinions, theories, or assumptions. Empiricism could relate to Cybersecurity in the reconnaissance phase of a cyber attack by finding and collecting information on a system.
Skepticism- The principle that all claims should be questioned and examined before validation. Skepticism could relate to Cybersecurity by training employees to look for misspellings and odd language, which are signs of phishing, when clicking links and downloading files, and being cautious of out of the ordinary requests.
Ethical Neutrality- Scientist must adhere to ethical standards when conducting research. Ethical Neutrality can relate to Cybersecurity by maintaining privacy and confidentiality of people and their information by following ethical data collection procedures.
Determinism- Behavior is caused, determined, or influenced by preceding events. Determinism could relate to Cybersecurity by the soon to be ex-employee that is disgruntled by pay discrepancies, and favoritism by managers and directors.
Journal Entry 3
Visit PrivacyRights.org to see the types of publicly available information about data breaches. How might researchers use this information to study breaches? Enter a paragraph in your journal.
PrivacyRights.org collects data from government-maintained data sources that are available publicly, which include U.S. Department of Health and Human Services along with states Attorney Generals that publish data breaches notices according to their notification laws. The data collected is from 2005 to current. There are current laws and tips on how to avoid breaches of your personal information. You can filter the breaches by timeline, which is an infographic overview of the total breaches, by State, by category, and a chronological table listing all breaches by organization name. They also categorize the type of breach, along with classification of the type of organization or business. Researchers can use this data to study which types of organizations are most susceptible to specific breaches. Also, to study the pattern of previous breaches and to gather and compile data, to further draw conclusions and educate in order to prevent future breaches.
Journal Entry 4
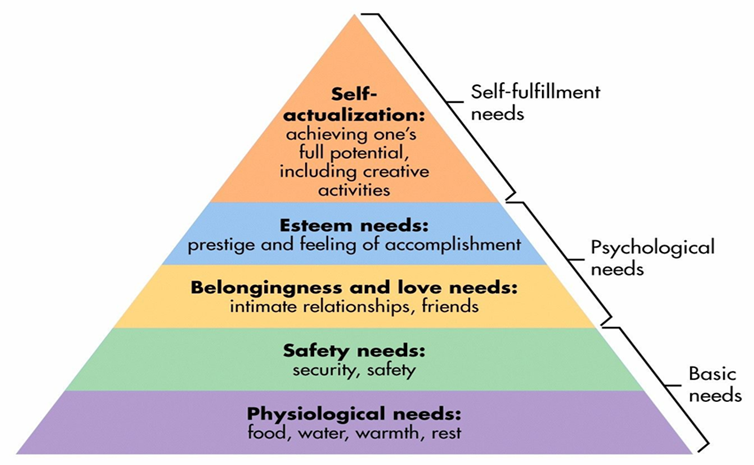
Physiological needs (Basic needs) – I would say internet. The internet is a basic need at this point. In order to do school work, I need the internet to view, submit assignments, and be able to take quizzes and tests. Although watching television and paying bills are not an absolute nessessity, I do also use the internet to do these things.
Safety needs (Basic needs)- A phone. Since few people have a “house phone” in this day, including myself, I would have to say my cell phone. It provides the safety and security of being able to call 911 or someone for help.
Belongingness and love needs (Psychological needs)- Social media. Although I’m not over the top involved in it, I do use social media to communicate with family and friends that may not live close to me.
Esteem needs (Psychological needs)- My computer. Not only for my school work, but to handle personal tasks, keep track of important documents, which all give me the feeling of accomplishment and productivity.
Self-actualization (Self-fulfillment needs)- I am hoping that I have not yet reached my full potential yet, but that period of time is coming.
Journal Entry 5
Review the articles linked with each individual motive. Rank the motives from 1 to 7 as the motives that you think make the most sense (being 1) to the least sense (being 7). Explain why you rank each motive the way you rank it.
- Boredom- I think that boredom as a reason makes the least sense. There are millions of options on things to do to combat boredom, rather than cyber offending.
- Entertainment- I see entertainment as an extension to boredom. Other than being someone who takes pleasure in seeing unknown people harmed, which is just some form of mental illness that help should be sought for, I do not understand why offending would be a form of entertainment.
- Recognition- I somewhat get this logic, however there are multiple more productive, meaningful ways to be recognized for your skills rather than compromise other people’s personal information.
- Political- In a time where it seems like almost everyone has a political opinion, or some motivation that is affected by political affiliation, there are a lot of people that would go to extremes to make their point politically, and hacking would be no different.
- Revenge- When there is a personal motivation, like getting revenge on someone a person feels harmed them or did them wrong in some way, there seems to be a lot of satisfaction in getting revenge in this way.
- Money- The number one reason (besides multiple reasons) I feel makes the most sense as why people offend. Money makes the world go round. Whether it is to makes end meet, or to just selfishly want money to spend on things someone may not otherwise afford, some people see profiting from offending as justifiable.
- Multiple reasons- Well it stands to reason that the more reasons a person has to offend, the more likely they would. It is the only motive other than money that I feel makes the most sense.
Journal Entry 6
Fake websites can use multiple ways to mislead users, to ultimately the end goal, which is to get you to provide your personal and or financial information. Some of these websites are made to look legitimate, although some are not well created, and if you pay close attention, a lot of times you can spot things that indicate that these are fake sites. The most used socially engineered aspect in fake websites, is emotion. This tactic will only work if you can relate to it, or it is something relevant to you. Using emotional manipulation allows attackers to bypass your natural skeptical instincts and use urgency, excitement, or fear.
DMV Phishing Scam Sites. Because almost anything can be done online now, and DMV is used in most every state in the US. The acronym and any version of “DMV” and can be used and made into a website that mimics the legitimate Dept. of Motor Vehicles site and confuse people into clicking on site, and possibly take payment for services like registration renewal or accessing driving records. For example, instead of www.dmv.virginia.gov, the legitimate website in Virginia for Dept. of Motor Vehicles, there fake sites like.DMVNow.
Fake websites that look very similar to legitimate sites login page, that trick customers into entering account details. The attacks purposefully made the URLs similar to legitimate sites, for example instead of PayPal’s login page, the URLs are like paypaysecurity.com, using the word “pay” twice instead of “PayPal” or paypa1.com, using the number “1” instead of the letter “l” which look similar to each other.
Things that can indicate that you are possibly on a fake website include: Unheard of online stores offering too good to be true deals or sales, Poor design quality or layout, if your attempting to access a well-known large company, is the website design and layout what you would expect or typically see when accessing a legitimate site. Is the grammar correct, can you spot spelling mistakes? Most any legitimate business website, will have things like an “About Us” and ‘Contact Us” page, and a legitimate phone number to contact business.
Journal Entry 7
Journal 8
Q: After watching the video, write a journal entry about how you think the media influences our understanding about cybersecurity
A: Well as with any real-world scenario that is depicted on a show, movie, or even by the media, the main objective is to get the point of the situation across, to make it understandable, which means a lot of dramatizations, and time lapses to make the situation look like it’s possible in a small amount of time. Because explaining cybersecurity in a lot of detail would not be completely understood by a lot of people, they “make a long story short” and summarize the processes and procedures, to make it look a lot faster and simpler than it actually is.
Journal 9
Social Media Disorder Scale (SMD Scale)
Please answer the question by thinking of your experience with using social media (e.g., WhatsApp, SnapChat, Instagram, Twitter, Facebook, Google+, Pintrist, forums, weblogs) in past year. Answer the questions as honestly as possible. According to DSM, at least five (out of the nine) criteria must be met for a formal diagnosis of “disordered social media user”.
During the past year have you…
- Regularly found that you can’t think of anything else but the moment you will be able to use social media again? Yes/No (Preoccupation). NO
- Regularly felt dissatisfied because you want to spend more time on social media? Yes/No (Tolerance). NO
- Often felt bad when you could not use social media? Yes/No (Withdrawal). NO
- Tried to spend less time on social media, but failed? Yes/No (Persistence). NO
- Regularly neglected other activities (i.e. hobbies, sports, homework) because you wanted to use social media? Yes/No (Displacement). YES
- Regularly had arguments with others because of your social media use? Yes/No (Problems). NO
- Regularly led to your parents or friends about the amount of time you spend on social media? Yes/No (Deception). NO
- Often used social media to escape from negative feelings?
Yes/No (Escape). YES - Had serious conflict with parents, brother, sister (friends, relationships etc.) because of your social media use? Yes/No (Conflict). NO
Q: How did you score? What do you think about the items in the scale? Why do you think that different patterns are found across the world?
I scored 2 out of 9. I don’t know if the questions equate to each of the catagories specifically, maybe because in order for a “formal diagnosis” you would need to answer “yes” to at least 5 of the 9 questions. I do think that some of the questions are relative to personality traits and individuals. For instance, sometimes if I am procrastinating on doing something I am not that excited to do, like chores or homework, I will procrastinate in a lot of different ways, not just social media. I think different patterns are found accross the world based on the differences in culture, family roles and connections, and schedules.
Journal Entry 10
To summarize the article, Social Cybersecurity An Emerging National Security Requirement, a new aspect of warfare is the information and psychological aspect that will most likely be the key aspect to victory. The biggest weakness to prepare for is not the external attack, but to understand the aspect of social cybersecurity in order to prepare to defend the external attack.
Journal Entry 11
Basically, as an entry level cybersecurity analyst you are monitoring the network, working the help desk responding to phishing attacks, assisting higher level analysts in mitigation of vulnerabilities, training for users, paperwork, and research for patches on vulnerabilities. The social behavior in entry level analysts is that you would most likely be shadowing a more experienced analyst for the first few years, depending on the company you work for.
Journal Entry 12
The economic theory of Rational choice applies because the business chose a third party to oversee the website, and clearly, they did not have strong policies in place to prevent malware and did not become aware of it until after a year the attacks first gained access. The Classical economic theory also applies, based on the information about us that we willingly provide to companies as part of supply and demand.
The social science theories that apply to the letter are Agency Theory, because the two-party relationship between buyers and sellers, whose goals do not coincide, and Rational Choice theory based on people calculating the cost and benefits of actions, and act accordingly.
Journal Entry 13
First, I think the bug bounty programs is genius. It allows small and medium size businesses to improve their cyber structure and vulnerabilities, without having to spend a lot of money that they may not have by hiring outside companies to do the same thing. Large businesses and corporations have the means to employ a large number of the best cyber security professionals, and that leaves small to medium size companies not able to compete. It also shows and emphasizes the general rule that having diversity in people with different strengths helps find the greatest number of issues in the code. It isn’t surprising that most security researchers are able to work part time, and at the convenience of their schedule, including 27% that are students.
Surprisingly to me, the study found a price elasticity of between .1 and .2 at the median for hackers, indicating that hackers main motivation is not money. This is also good news for smaller businesses, because it means they still can have resources available to them, even when they do not have an endless source of money to offer for bounties.
The findings from the study are that bug bounties are effective, no matter the industry, size, or resources, even though certain industries received fewer reports. Other findings from the study include the drop in valid reports over time, and that amount of new programs did not significantly impact the number of reports companies receive on the HackerOne platform in the same month. Lastly, the study found that there is still little is known about the bug bounty markets and the pertinent variables that exist with it.
Journal Entry 14
Q: Andriy Slynchuck has described eleven things Internet users do that may be illegal. Review what the author says and write a paragraph describing the five most serious violations and why you think those offenses are serious.
A:1-Collecting Information about Children-With human trafficking having become such an issue, there should never be information collected or displayed that would make the most innocent of all humans, more at risk.
2-Cyberbulling and Trolling- Cyberbullying can have a detrimental effects on someone’s mental, physical, and emotional health, especially children.
3- Using Unofficial Streaming Services- Not only is this act illegal, but you never know when companies are cracking down and attempting to catch people, which you can be charged with a crime or sued. Not only that but depending on where you are getting the content from, your personal information could be compromised or stolen.
4- Using Torrent Services- Basically the same reason as in #3
5- Sharing Passwords, Addresses, or Photos of Others- Personally, I feel this one stands out for the reason that posting someone’s address online is a scary possibility, and apparently illegal, however, taking someone’s picture (as long as you are not on private property) and posting it is not.
Journal Entry 15
Watch this video and think about how the career of digital forensics investigators relate to the social sciences. Write a journal entry describing what you think about the speaker’s pathway to his career.
I personally think that is the way a lot of people in Cybersecurity and most IT related positions got into the field, more especially back before colleges had classes specifically in the computer field. I also think that those people are most likely more knowledgeable in the field, because everything was hands on. You did not learn by tests and quizzes, you learned by poking around on computers and programs, giving you a firsthand look at what you’re doing, and what happens when you do a specific action. I also think when you have a background in another science, whether it be accounting or law enforcement, you start with the foundation, and then learn the technical part of cyber, by trial and error. I also think it is easier to learn things that way. You learn the heart of the career, and then you can take classes and be taught the process and procedures.
Article Review #1, Increasing Cybercrime Since the Pandemic: Concerns for Psychiatry https://www.ncbi.nlm.nih.gov/pmc/articles/PMC7927777/ The topic of how the increase in cybercrime since the pandemic, and the concerns for psychiatry relate to a few principles of social science. It relates to Relativism by showing how the influx of use of the internet, has increased cybercrime. It relates to Determinism because the human element is the common denominator in cybersecurity, with the human element, based on individual behaviors and personality traits. And lastly, it relates to Objectivity because there were no opinion-based information in relation to the article, all conclusions were based on research and statistics. The study’s research questions address the changing use of technology, societal impacts of the pandemic, cybercrime evolution, individuals with vulnerabilities to cybercrime, with emphasis on those with mental illness. The research method used was quantitative research using numerical data and statistical analysis. The analysis based on all the data provided, summarize that a mental illness could increase the chance to become a victim of cybercrime and that psychiatrists need to be aware of the impact of cybercrime on mental health, to include online mental health services. Although it is not the responsibility of mental health providers to teach cybersecurity, nor will it prevent a patient from potentially experiencing internet fraud, distributing information will increase awareness of cybercrimes and hopefully incite people to educate themselves. The concepts that relate to this article from the presentations include behavior and risk (Module 5) and how that behavior contributes to the specific risk regarding cyber-attacks, the psychological consequences of victimization (Module 5) outlines the some of the emotions associated with being a victim of a cybercrime, the psychological factors increasing the risk of victimization (Module 4), and the use of technology and psychology (Module 4) that concludes that technological changes influence virtually all aspects of society and that technology and psychology are closely connected. The impact of the Pandemic was especially high in minority, low income and education households, and households with a child or children under eighteen. Not to mention, the majority of people in the age group of 18–29-year-olds are living with parents for the first time since the Great Depression.1
Article Review #2, The Challenges of Identifying Dangers Online and Predictors of Victimization
https://vc.bridgew.edu/ijcic/vol7/iss2/1/?utm_source=vc.bridgew.edu%2Fijcic%2Fvol7%2Fiss2%2F1&utm_medium=PDF&utm_campaign=PDFCoverPages
The topic of how real the dangers are online, and specifically the behaviors of cyber-offenders that other online users should be aware of relate to a few principles in social science, including Relativism because now that the internet is the backbone of our daily routine, the more chance you have to becoming a victim of the dangers online, Determinism by taking the results of the research, to provide policies, programs, and laws for every internet user to benefit from, and Parsimony by using Routine Activity Theory (RAT) which is a simple theory to understand and explain many complex ideas.
The research questions include whether people providing information in online articles can be considered credible, the effectiveness of treatments to recover from social and psychological suffrage of cyberbullying, and online related activities that increase victimization risk.
In the online credibility, cyberbullying, and unauthorized access of information examinations, archival research was the research method used in all three.
The analysis based on all the data provided, summarize a suggested model including “examining information” and “user interaction characteristics” to best inform a user for online credibility, success regarding treatments to reduce social and psychological harm from cyberbullying, and that online target exposure and accessibility increased victimization risk, yet physical methods were “weakly protective.”
The concepts from the class presentations that relate to this article are the psychological consequences of victimization (Module 5) outlines the some of the emotions associated with being a victim of a cybercrime, the use of technology and psychology (Module 4) that concludes that technological changes influence virtually all aspects of society, perceptions and safety (Module 6) explains that online disinhibition refers to the way that we feel less inhibitions online than we do when were with others in the same physical setting, and misinformation (Module 8) which refers to false or out-of-context information that is presented as fact.
The topic relates to the marginalized “peer” victims of cyberbullying and the social and psychological harm “among schoolers.”
The overall contributions to society from the studies are stated above in that taking the results of the research helps to provide needed information to construct policies, programs, and laws that every internet user will benefit from.
Career Paper: Navigating the Digital Maze: Digital Evidence of Data Recovery
Courtney Swink
Cybersecurity and Social Science
Professor Yalpi
November 21, 2024
Digital Forensic Investigators or analysts are professionals who help law enforcement gather, collect, preserve, examine, and analyze digital evidence for legal proceedings. They recover and extract digital evidence from computers, mobile devices, digital media, tablets, servers, cloud storage, network traffic, wearable devices, and navigation devices. These investigators are trained in tools and techniques to recover and analyze data including, but not limited to deleted files, text messages, call logs, internet history, emails, databases, meta data, images, videos, system logs, and location data. After analyzing the evidence, Digital Forensic Investigators write a report and testify in court as to their findings. According to IBM, “over 90% of all crime is recognized as having a digital element” making Digital Forensic Investigators at the playing a crucial role in investigating crimes, illegal activity, and fraud through digital devices.
Digital Forensic Investigators can use digital footprints such as social media activity (Module 9) and browsing history to infer habits, interests, and potential motivations as to understanding behavior, along with analyzing digital communications to provide insights into a psychological profile (Module 4) and identifying a potential suspect. Using digital artifacts, timestamps, and location data can eliminate or narrow down suspect lists and authenticate or disprove alibis.
Social Science principles (Module 2) are extremely relevant regarding Digital Forensics. Digital Forensic Investigators apply the principle of relativism through interpretation and variance of digital evidence based on circumstances of a case, context, and jurisdiction. Objectivity is a principle a Digital Forensic Investigator must possess in order to analyze without assumptions or bias, and deliver findings impartially solely based on the data collected. When testifying in court, Digital Forensic Investigators engage in parsimony when presenting evidence and testifying in relation to the findings, so that members of a jury, attorneys, and judges understand and are not lost or overwhelmed in the complexities of digital forensics. Ethical neutrality is another key principle that Digital Forensic Investigators should heavily maintain. By following established policies and procedures, and only accessing digital evidence that is legally applicable to the relevant investigation. Determinism directly relates to profiling and determining how criminal behavior is caused or influenced by events in a person’s life that made them amenable to a particular crime. Whenever a crime is committed, the sentiment that there is no such thing as coincidence is regularly expressed. However obvious it looks that a person may be guilty of a crime, Digital Forensic Investigators should always maintain a level of skepticism until it is proven by science, of a person’s guilt. Digital forensic techniques, tools, methodologies, and algorithms are all used to empirical research to test hypotheses and evaluate the effectiveness of such.
According to demographics from Zippia the Career Expert, only “27.2% of Forensic computer examiners are female, and 44.1% are minorities.” With such underrepresented demographics, (Module3) there are bound to be challenges that arise. Among the challenges, language barriers when evaluating evidence in a different language, accurate interpretation of cultural digital artifacts, and unconscious biases based on personal experiences and stereotypes. Practically everyone uses digital tools on a daily basis, the demand for Digital Forensic Investigators has and will continue to evolve. Digital Forensic Investigators use various techniques to gather, collect, preserve, examine, and analyze data from a multitude of digital devices to detect criminal activity in today’s society.
“Forensic Computer Examiner Demographics and Statistics [2022]: Number of Forensic Computer Examiners in the US.” Www.zippia.com, 29 Jan. 2021, https://www.zippia.com/forensic-computer-examiner-jobs/demographics/.
“Meeting the Future of Digital Forensics and Evidence Management.” IBM, www.ibm.com/downloads/documents/us-en/107a02e953c8ff6b.
Munday, Rebecca. “Day to Day of a Computer Forensics Investigator | Main Responsibilities.” Www.computerscience.org, 17 Apr. 2023, www.computerscience.org/careers/computer-forensics-investigator/day-in-the-life/.
