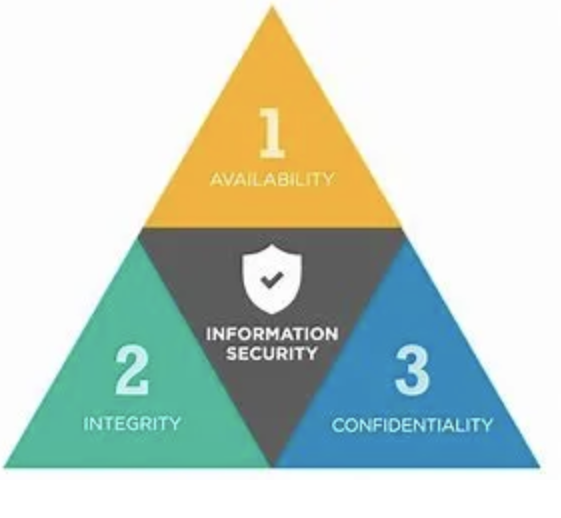
Confidentiality, integrity, and authentication are the cornerstones of a sound cybersecurity foundation. While each pillar carries its own weight and definition, each should be looked at as part of the whole, and not individually. The National Institute of Standards and Technology (NIST) defines confidentiality as preserving authorized restrictions on information access and disclosure, including means for protecting personal privacy and proprietary information. One of the most challenging aspects of cybersecurity is ensuring that the right people have access to the right information, and with that, ensuring that unauthorized personnel do not gain access to sensitive information. Perhaps one of the most widely available tools used by the industry today is two-factor authentication (2FA) which operates on a principle of securely proving that you are who you say you are. The 2FA technology is certainly not a new concept, and in fact, has origins dating back in 1986.
The NIST defines integrity as guarding against improper information modification or destruction, and includes ensuring information non-repudiation and authenticity. In any information system structure, one of the most important functions is to ensure that data has been uncompromised, and true to the nature from which it originates from. These objectives can be achieved by conducting routine security audits, security baseline scans, data backups, and ensuring that authorized users only have the permissions in which they need to conduct their job. Integrity is a vital principle that can be achieved by being proactive and not reactive.
Last but certainly not least, is availability. This was defined by the NIST as ensuring timely and reliable access to and use of information. The fact is, availability is something that is accomplished without the end user even realizing. Ensuring that an authorized user can log in and access the information they require, is exactly what the third pillar of the CIA is all about. When you consider the first two pillars, you begin to understand why availability is included. Each part of the CIA triad is intricately intertwined into one another, and with its’ interconnectivity, the end goal is to create a secure infrastructure of authorized users, and to ensure that access to information is readily available when needed. In order to bolster availability, we must investigate two critical pieces of the puzzle, authentication and authorization.
Authentication is the process of proving who we say we are. Consider the following example: Jane, a new employee at a tech start-up has requested an account from IT. She has provided the required paperwork and photo identification required to get an account. Given that she has proven she is who she says she is, IT has given her a username and password, which is required for her to be authenticated on the local network.
Authorization on the other hand, is similar, but quite different. As part of Jane’s new hire process, her supervisor has been requested to provide a list of folders and files to IT, in order to permission her account. By doing this, Jane has been given authorization to access specified data, with the lowest required permissions in order to conduct business. These two practices play a vital role in securing access to data and information systems, and an important distinction must be made between the two in order to understand how to implement best practices.
Although the concept of the CIA Triad has been around for quite some time, it continues to move into tomorrow. As our technologies and security practices evolve, so too does the capabilities of those who would seek to exploit vulnerable networks and data. The importance of the CIA Triad cannot be understated, and it is up to the security professionals of today to refine and evolve these basic security principles and ensure they do not get left behind.