This page contains my Cybersecurity as a Social Science journal entries.
NICE Framework Journal Entry
After reviewing the NICE Framework, I want to focus my career on Cyber Defense Infrastructure Support. This area has the best selection of skills used in day-to-day operations. Along with being able to create software and constantly update software, this job also provides the opportunity to work with hardware as you work across the entire computer network. This leads me to believe this job would have the most interesting daily operations, also allowing me to strengthen my knowledge in various skills. Beyond that, I also found myself interested in Digital Forensics. I was always fascinated by forensics science, so being able to use my computer skills effectively in the forensics field sounds incredibly interesting. I like the idea of analyzing past incidents to strengthen computer systems against future security threats. On the reverse of that, one area that I have no interest in is Strategic Planning and Policy. While I would have no problem doing this as part of a different job, I don’t think I could do it full-time as I much prefer hands-on programming work to writing out policies.
Principles of Science Journal Entry
With cybersecurity being a science, it makes sense that science principles apply to most aspects of the field. The scientific principles of determinism, ethical neutrality, empiricism, parsimony, objectivity, and relativism help us understand cybersecurity when viewing it through the lens of social science. Determinism, the idea that preceding events determine behavior, is used in cybersecurity to explain why malicious actors perform hacks. If you can determine the events that lead up to a cyberattack, you will be able to understand why the attack took place. Ethical Neutrality refers to the standards and unbiased moral standpoint required for scientific research. In cybersecurity, ethical neutrality needs to be taken into consideration when testing attack methods and conducting research. Empiricism, only studying behavior that is real to the senses, specifically focuses on the idea that we should not use opinions when trying to understand cybersecurity. If defensive measures in cybersecurity were simply placed based on hunches, then systems would have large gaps simply based on the opinions of whoever designed the system. Parsimony is the idea that explanations should be as simple as possible. Human behavior is a much harder thing to describe simply. However, the goal remains to describe why cybercriminals do what they do as simply as possible for the explanation to make sense to as many people as possible. Objectivity, studying in a value-free manner in which no specific opinion is promoted over another, is critical to cybersecurity. In cybersecurity, the most effective research is that which remains objective and can be used by most people to improve their systems. And lastly, relativism is the interconnectedness of all things. It is important to understand that all of cybersecurity is tied together, and improvements in any part of the field impact the entirety of the field, from hardware all the way to how people working in the field act.
PrivacyRights.org Journal Entry
The website PrivacyRights.org presents its users with a large amount of information about data breaches. Included in this information, you can find news, reports, advocacy articles, and guides all about different types of data breaches, laws surrounding them, their impacts, and how they work. This is a valuable tool for researchers as they can use items such as the “On-The-Ground Look at Consumer Impacts of Data Breaches” to get statistics about what commonly leads to a consumer data breach and what they deal with in the aftermath. Information like this can help researchers discover both the signs to look out for in a data breach while also determining the fallout of a breach so it can be determined what areas need better security to lessen or prevent the negative aftermath. Similarly, more specific articles, such as “Thousands of Disney+ Accounts Hacked Within Hours of Launch,” give more specific insight into specific data breaches while linking to trustworthy articles. Using this, researchers have reliable statistics about not only those affected by the breach but also what happened to the information afterward. This information allows researchers to identify a timeline of what happens to data in a breach, and using this, they can better track breaches in the future. The information provided by PrivacyRights.org is invaluable in understanding the impacts of a data breach, allowing researchers to determine what information needs better security.
Maslow’s Hierarchy of Needs Journal Entry
Maslow’s Hierarchy of Needs is the five types of human needs that humans strive to achieve. The first level, physiological needs, refers to what people need to survive. While some people feel that technology has grown to be a part of this level, I personally do not feel this way. Technology and internet access are not necessary for survival, and having experienced long periods of time without access to them, I feel I do not feel any different when I can’t use them. The second level, safety needs, is when I begin to feel technology interacts with my life. With so much of our information saved in a digital state, I worry about the large impacts a data breach would have on my life. I feel that my safety needs would not be met if I did not take extensive digital security measures to protect my data. The third level of belongingness and love needs refers to social relationships, the fulfillment we get from family, friendship, and intimate relationships. I believe this is the level most impacted by technology for me. My family and most of the people I grew up with are in Pennsylvania. Going to school in Virginia, I rarely see them in person. However, that hasn’t impacted these relationships, as I can still talk to them daily thanks to technology. I can see their faces or text them anytime, giving an incredible benefit that past generations did not have. The fourth level, esteem needs, refers to feelings of prestige and accomplishment. This is where I feel technology has hurt the hierarchy. Many people allow their self-worth to be heavily impacted by the views of others and, to that extent, social media. I have seen the negative effects it can have on people where they obsess over what they put online because they personally feel impacted by what everyone thinks of them. This is the main reason that I rarely use social media. Finally, the top of Maslow’s hierarchy of needs is self-actualization. Being at the highest level because it is so difficult to achieve this level refers to reaching our full potential and being our ideal selves. This level is harder to define as it differs for everyone. However, personally, I believe that technology is incredibly engrained in my self-actualization. As cybersecurity is the field I have wanted to pursue for a long time, my ideal self would include a deep knowledge of many different aspects of technology to defend them most effectively. It makes sense that technology would play a large role in our lives, given we live in a digital era. However, viewing how it relates to the hierarchy of needs reveals just how critical technology is to nearly every aspect of our lives.
Individual Motives Journal Entry
Below are the links to seven articles, each containing a different motive behind a major cyber attack. I have ranked them from one to seven, with one being the most logical and seven the least. Seventh, I believe the least logical reason for hacking is entertainment. In the article, the criminal said he simply did it for fun, even though he would later profiteer from it. In many other cases, doing a crime “for fun” is the most depraved reason to do it. There are a million other things to do to have fun, even online systems that encourage trying to be hacked if you want to challenge yourself, so having fun by committing a crime makes no sense to me. The sixth is boredom. The article addresses that it is not the boredom of the hacker but rather kids being bored and posting pictures of themselves online, which draws the attention of hackers and pedophiles. This would instead suggest that the motive is that the children are easy targets, which, as horrible as that is, would make sense for low-skill hackers to target. The fifth motive is revenge. While revenge itself is always a nasty, hateful thing, it is a strong motive. Many people who seek revenge do it because they have been hurt and find themself in a headspace where they believe the revenge will make them feel better. The article discusses the posting of revenge porn, one of the darkest and most disgusting acts one can do for revenge. Ultimately, this reason is as nonsensical as the others before it. The 4th most logical motive is recognition. For many, hacking is a job or a way to get validation. If they can pull off a large-scale attack that gets media coverage, then their name will be out there, and everyone will know how high of a skill level they have. They are also led on by one-in-a-million stories where people are offered very lucrative jobs because of the large impact of a hack they committed. For number three, I have politically motivated attacks. This article addresses the concept of hacktivism, hacking as a means of contributing to activist causes. I believe this to be one of the more sensible motives as when people contribute to activist ideas, they want to do the most they can, and if the most is working from a computer rather than rioting, it will make the most sense for them to commit these cybercrimes. The motive behind hacking in the number 2 place is money. While not all of them do, 1 in 5 hackers who hack for money do it in order to buy necessities. While still not right, I have always felt that committing a crime in order to survive is the most logical reason to do so. Number one, the most logical reason for hacking is having multiple motives for doing so. Having multiple motives encapsulates the logical reasons for committing a hack, money, recognition, politics, and beyond that, it takes into account the idea that it may be psychologically motivated, and the offender may not think of the crime in the same way other people would. Ultimately, in nearly any case, I feel like committing a crime is illogical. However, if the crime is to be carried out either way, the motive may at least explain why one would feel they had to commit said crime.
2: Money
3: Political
4: Recognition
5:Revenge
6: Boredom
Fake Websites Journal Entry
Can fake websites be discerned from Websites? This is a simple but important question for the everyday internet user. In this journal, I’ve been asked to find three fake websites and differentiate them from their real counterparts. I have chosen varying fake websites to demonstrate different things to be on the lookout for when identifying fake websites.
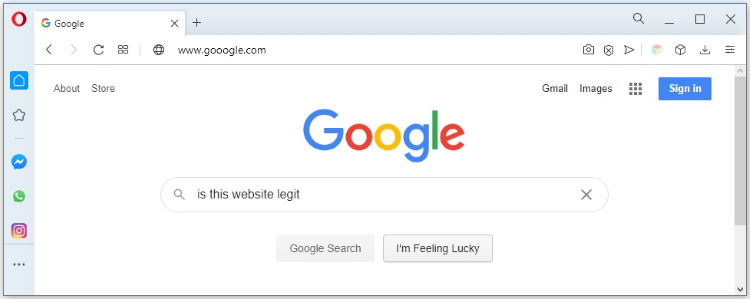
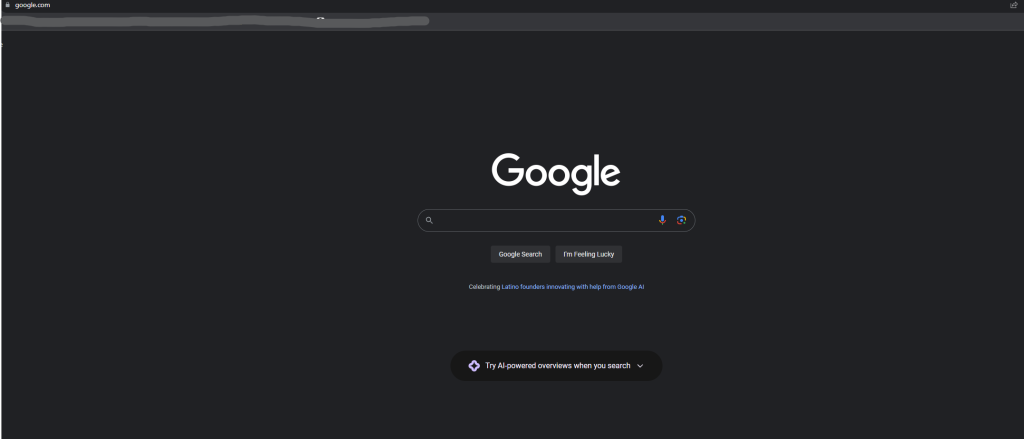
Above are two different Google sites, with this first site being one of the easier changes to notice. At first, the sites appear identical, including all of the contents of the page itself. The difference comes for those who look closely at the address bar, where the URL is actually spelled wrong with the inclusion of a third “o.” Another important detail to look for is the lack of the padlock in the address bar. This signifies that the website does not have a certificate, which all major websites need.
2. Amazon
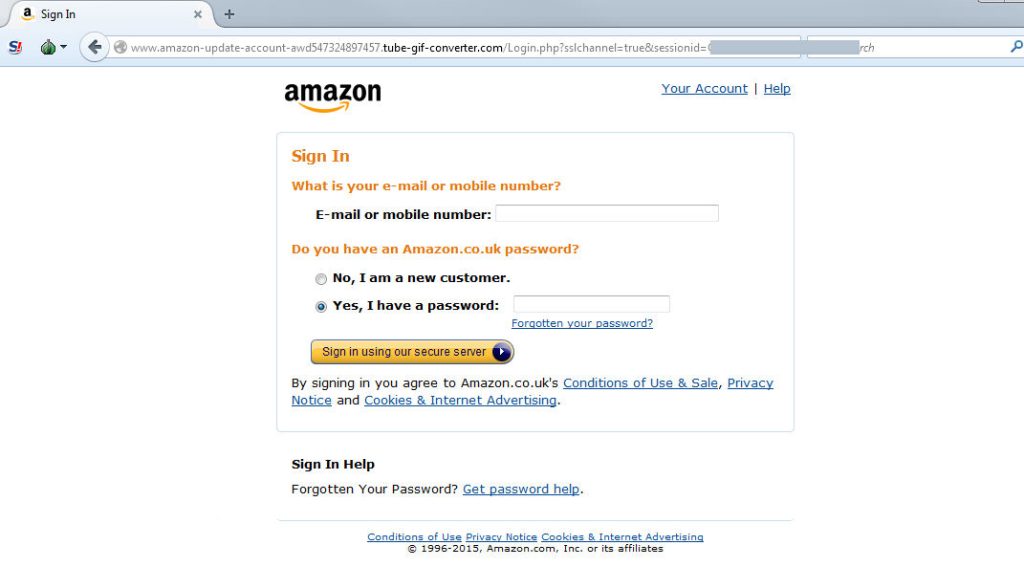
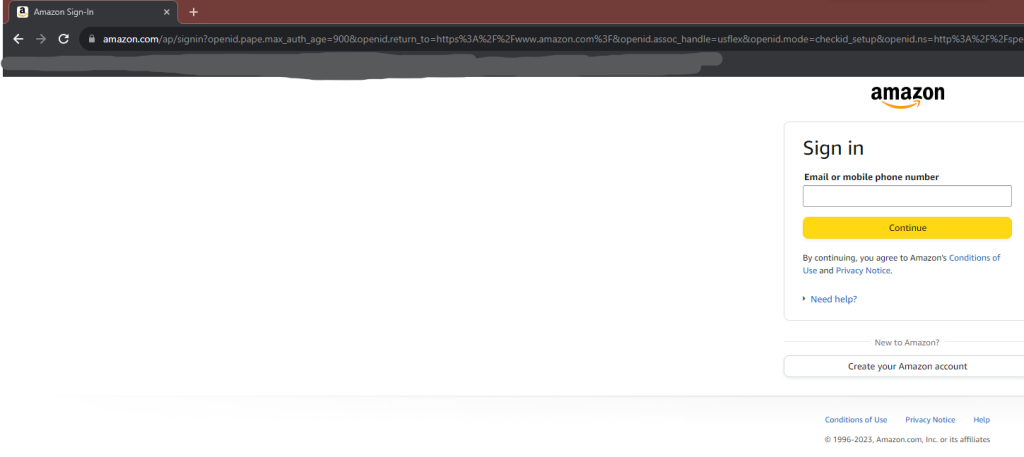
At first glance, the contents of this page are just as convincing as the Google site. The URL starts with “www.amazon,” it has a button for if you forgot your password, has Amazon’s copyright information correctly displayed on the bottom, and everything is spelled right. It even uses language to suggest that it is a safe website running on secure servers. However, there are two glaring errors with this site. Again, when closely examining the URL, we find that the actual domain name is not Amazon. Browsers even help with this by bolding the site’s domain, which in this case is actually “tube-gif-converter.com.” Secondly, when looking at the page’s contents, the biggest difference is that it asks for your username and password on the same screen. This is something that many companies will never do for the sake of security. Once the visitor to the site notices that the contents are not as convincing as they first appeared with questions like “Do you have an Amazon password?” instead of the traditional log-in or sign-up separate pages.
3. Paypal
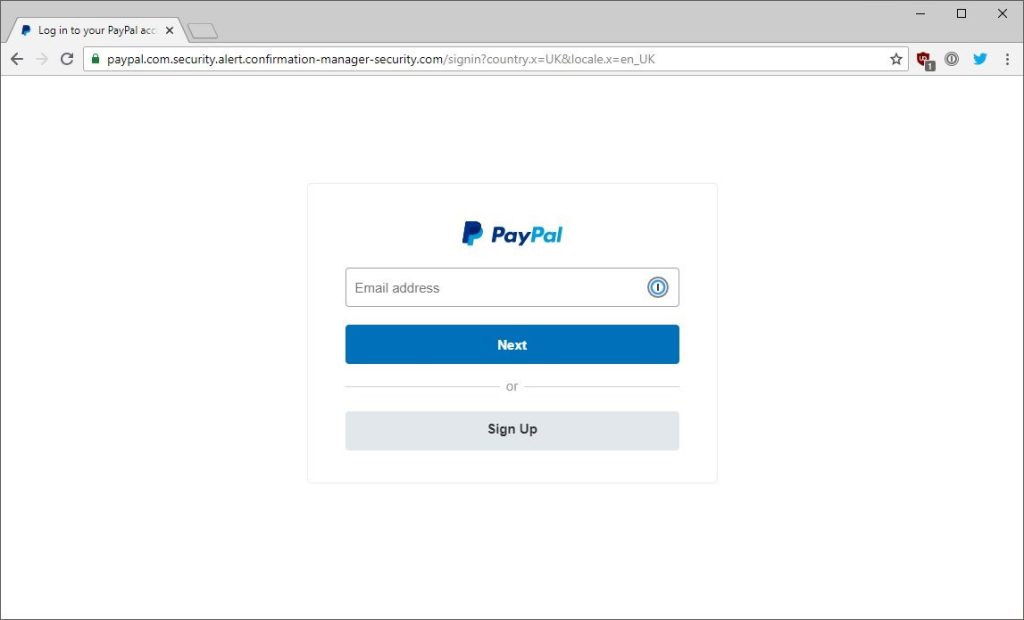
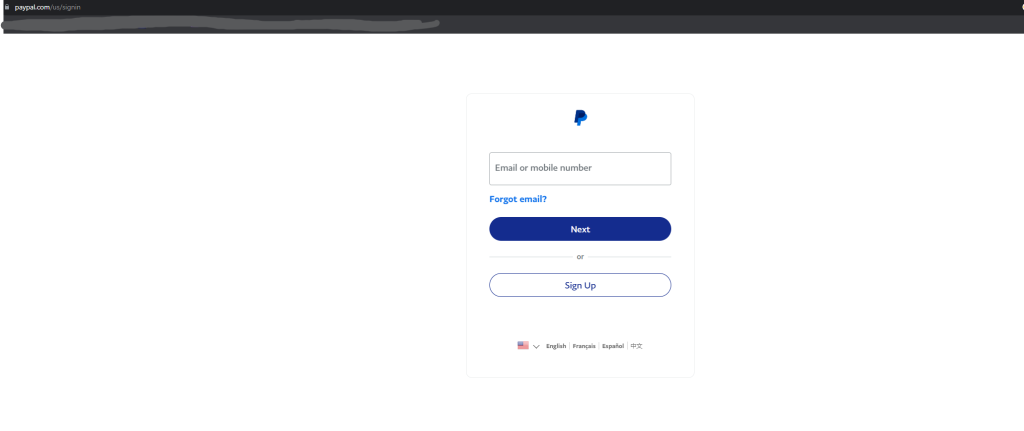
Above are two examples of PayPal login pages. This is the most difficult of the false pages to distinguish. The tab looks correct, the page’s contents look legitimate, the email and password are entered on separate pages, the URL contains PayPal.com, and most notably, the URL has the green lock, suggesting the site has a site certificate, which many spoof sites do not. The page still has three notable errors. The first is the URL. Specifically, the glaring problem is that it contains “.com” twice. This signifies to site visitors that the first “.com” is fake and everything before the second “.com” is the actual domain name. The second and third noticeable errors are issues that users of PayPal may disregard if they never use the features. That is the fact that the “Forgot email?” and switch language buttons are missing. Nearly all large sites include an email recovery option, which is missing here. Furthermore, some large companies like PayPal include the option to change the language of the whole site on the login page, and there is a noticeable emptiness at the bottom of the fake page without it.
While these are just examples of how to distinguish between fake sites visually. If there is ever a reason to believe a site is fake. You cannot distinguish visually if it is or not; there are resources that go beyond simply viewing the site, such as checking the certificate of the website to be sure it is an official site or even entering the website into a site checker, which would return a report on the authenticity of the page.
Cybersecurity Meme Journal Entry
This week, we were tasked with creating a meme related to the Human Systems Integrations Framework.

The Point of Human Systems Integration is to create systems and interfaces while optimizing every human-related aspect to create the best interaction between humans and the systems that they will be using. This is done to preserve the longevity of the systems and create more effective employees by considering their limitations. This meme shows why it is important to consider the human systems integration framework because this employee is unhappy with the interface he has to use. Although it may be effective, they have clearly missed an aspect of the framework as it is either too complicated or he has not been properly trained in how to use the program.
Media Influence on Cybersecurity Journal Entry
Linked below is an interesting How Real Is It? video by Insider in which Keren Elazari reviews some clips depicting hacking in popular media. To my surprise, the video subverted my expectations when Elazari gave numerous shows and movies high points for their depictions of realism in this hacking scene. Before this, I was under the impression that very few shows accurately portrayed hacking save for the few in which it was the sole focus of that media. I believe that in many pieces of media where hacking is not the focus, the concept is glossed over by using very technical words and showing lots of random letters on a screen. It gives the idea that all of hacking is this incredibly complex concept in which people need to be able to think as if they themselves are supercomputers. After watching the video, it is clear that many shows do put care into portraying accurate depictions of computer code and concepts taken from real-world hacks. Still, seeing as it is media, it needs to have some sort of appeal, so there is still a degree of sensationalization in many of these. This takes place in the form of many fancy visuals these hacker programs give or wildly changing certain elements such as capabilities or timeframes. I believe that it varies from film to film or show to show, but popular media, for the most part, can give real elements of hacking, although heavily sensationalized. Still, this will give people the wrong impression of hacking and cybersecurity, thinking it is either more or less difficult depending on what they watched or much more intense than in reality. It is incredibly similar to the CSI effect in which these exaggerated portrayals completely stagger how people perceive a line of work and misinform them of reality.
Social Media Disorder Journal Entry
I scored a 1.0 on the social media disorder scale, constituting normative social media usage. This made sense to me as I feel that I don’t really use social media. The nine items on the scale are great measures to see if someone has an addiction problem. Most notably, I feel that withdrawal and persistence are essential items to measure in the case of social media usage, as I feel that these are the most common items that we hear about: people who find themselves uncomfortable when they don’t have access to social media and people that spend too much of their day on social media. Interestingly, with 210 people worldwide suffering from social media disorder and 10% of Social Media Users in the US suffering from it, there is clearly a large percentage coming from the states, which is concerning. These different patterns appear worldwide because different countries approach social media usage differently. Some of it is policy, with specific age groups not allowed to be online for more than a certain amount daily. At the same time, in some countries, social media simply isn’t popular, drastically reducing the number that suffer from this problem. The big issue is it is clear that the number of people suffering from Social Media Disorder is only increasing. If we want to stop this, we will need to put restrictions in place, which would interfere with the popularity of the platforms, leading to pushback from those companies.
Cyber Security Analyst Journal Entry
Linked below is a video that describes working in a cybersecurity job analyst position. After watching the video, some social themes stood out in the role. One of the first things I noticed was that one of the key parts of the job is providing guidance and user awareness training. To effectively do this, one would need a good understanding of the social science to know what people need to be trained on and how to train them properly. Another role of a Cybersecurity Analyst is responding to phishing attacks. Again as phishing attacks are designed to target social aspects, then the Analyst will need an understanding of social themes to understand what the attack was targeting or how it could trick people. It is apparent that being a cybersecurity Analyst requires a good comprehension of social themes, and this is just the surface level of the job. Depending on the position, there may be much more.
Military Review Journal Entry
The article linked below is an examination of social cybersecurity and the predominance of information warfare across the world. Social cybersecurity is a unique form of cybersecurity that attacks the weakest part of most cybersecurity systems: humans. While it uses similar approaches to regular hacking, the goal is not to breach any information systems. Still, it is instead to gather and disperse the information they want to control the narrative. This is done both to improve security and improve influence in foreign countries. As the article discusses, it is a form of new weaponized propaganda that can more precisely target individuals for more effective results. Social cyber threats have become more prominent recently for two main factors: technology removing the need to be located close to someone to influence them and the decentralization of information flow, making it easier for groups besides a country’s government to influence people. The article presents a concerning thought in its closing as it discusses how social cyber threats can be used to create a divide between a country’s military and its people. For this reason, I think more effort should be put into educating people on social cybersecurity. It does not have to be a complex system. I agree with the author in the belief that we can significantly improve our social cybersecurity by teaching people to more effectively confirm the legitimacy of facts we read online before we fully believe them and let them sway our belief of the people we trust to lead and protect us.
Bug Bounty Policies Journal Entry
Linked below is an article discussing creating an economic model for bug bounties. One of the first things that I found interesting was how they used hackers’ pursuit of non-monetary goals to their advantage and to save money. As said in the article, many of these companies don’t have the massive budgets required to pay out large amounts of high-priced bounties. However, many hackers are driven by non-monetary gains, so by offering both experience and improvement of reputation, these companies were able to have their bounties completed while not spending any money, which is genius. I was also surprised to learn that how much money a company makes had little impact on how many reports from bu bounty hunters they received, which provides a very even playing field for companies considering implementing bug bounty hunting policies. It made sense that hackers driven by monetary gains were less likely to make reports of bugs in financial and medical industries as these bugs have a greater potential to be weaponized to make more money. It entirely depends on the moral compass of the hacker who discovers the bug, which is what leads me to believe it may be more of a risk for these types of companies to implement these policies. This article proved the effectiveness of implementing bug bounty-hunting policies. However, I feel that it should be a case-by-case decision based on the industry the company is in and what types of sensitive data they may have. Beyond that, conveniently, other factors have only a minor impact on the amount of reports a company receives, making it a viable option for many businesses.
https://academic.oup.com/cybersecurity/article/7/1/tyab007/6168453?login=true
Sample Data Breach Journal Entry
Below is a link to an example of a sample data breach letter. In it, we can see how the economic theories of rational choice theory and classical economic theory relating to the letter. The company that published this letter used rational choice theory when deciding to publish it, seeing that it would be more beneficial for them to warn people about the potential credit card compromise so that people could take action on their end. This was beneficial as it protected them if anything were to go wrong and didn’t cost them anything in needing to pay to replace their customers’ credit cards, as there seemed to be no use of the stolen data. Even if the data were used, the actions of the company and how much they would pay to appease their customers would also result from rational choice theory. Classical economic theory works with a supply and demand formula and the belief that the government should not impact the economy. This is seen in this letter as the company suggests that anyone concerned with their data being stolen should handle it themselves, as the company has no responsibility to correct any trouble with the stolen data as it is part of that supply and demand equation. As this theory also works with the notion that the government should not interfere with the economy, the government has no say in handling that data. It can’t force the company to do anything about it. We can also see how the social science theories of information behavior theory and social exchange theory relate as well. Information behavior theory states that threats to our identity are considered more urgent and gain more attention. This is exactly the case in the credit card breach, as the information stolen was the company’s customers’ names, addresses, phone numbers, and credit card information, all critical parts of their identity. Seeing as the stolen data was related to identities, the company chose to act, even though that data had not been used, just to be safe. One way to view social exchange theory is that we will terminate any more troublesome than beneficial relationships. This response letter can be seen utilizing this theory as they go out of their way to warn that it is unnecessary to build a good relationship with their customers and show that they have their best interests in mind. This way, what could be seen as a negative situation becomes a positive one that strengthens the company’s customer relationship instead of damaging it.
https://dojmt.gov/wp-content/uploads/Glasswasherparts.com_.pdf
Illegal Internet Usage Journal Entry
Linked below is an article reviewing some aspects of internet usage that many users do not realize is illegal. Of the eleven illegal acts, I felt the most serious were sharing addresses and passwords, using other people’s internet networks, collecting information about people younger than 13, illegal internet searches, and recording a VoIP call without consent. The sharing of addresses can directly result in harm and put the residents of the address in a dangerous situation. The address can be seen by criminals, stalkers, and malicious pranksters who may try to swat the home. Using other people’s internet networks without permission is no different than stealing any other utility the owner pays for, and it becomes more impactful for people without unlimited home data as you are stealing a finite resource. Collecting information on children is a direct violation of the Children’s Online Protection Act, making it completely illegal. Beyond that, collecting children’s data may later be used to take advantage of them, only adding to the crime. While there are functions in place to stop people from finding the results of illegal searches, with enough digging, people can see the results. These searches are unlawful because they result in either outlawed content or assist people in carrying out criminal activities, such as creating objects to harm others or learning how to produce drugs. Recording an online call without consent directly violates someone’s privacy, making it a crime. Now more than ever, in an age of audio manipulation and AI mimicry, audio recordings can be manipulated to create false recordings to make it sound like someone said something they did not. While everything written about in the blog is illegal, I believe these offenses come with the most significant risks. Nonetheless, I urge internet users to be cautious and think twice before carrying out these actions.
https://clario.co/blog/illegal-things-you-do-online/
Pathway to Digital Forensics Career Journal Entry
Linked above is a video by speaker Davin Teo, in which he details his pathway to getting into digital forensics. Teo started out as an account, but when the company he worked for found themselves needing help in IT he decided to help them with that as well. This led him to the opportunity to work in the First National Digital Forensic Practice in Australia. I found this to be really interesting, as it is amazing to see how much the field has developed since then. While cybersecurity is a multibillion-dollar industry with many professionals, back then, companies would even hire internally for IT and security needs so long as the applicant knew their way around a computer. I think Teo’s story is also an excellent counterargument to something that many cybersecurity professionals struggle with, that being imposter syndrome. People today feel that they may not be the best with cybersecurity, or they may not be proficient enough to continue working the job they have. Still, in Davin’s case, he entered the field with no cybersecurity background and grew into an excellent professional with an extensive list of skills and experiences to back him up. Davin’s story is an example that the only requirement to enter the field of cybersecurity is curiosity and a willingness to learn. Past that, it also provides a level of comfort for those currently studying cybersecurity who do not know the specific career they wish to pursue. Davin never set out to enter cybersecurity, instead, his experiences and his choice to accept the opportunities presented to him slowly moved him towards his career, a career which he has happily been working for 17 years. Overall, there are many aspects of Davin Teo’s story of approaching his career in digital forensics that show why cybersecurity is such an interesting and unique field to work in while also providing comfort for those trying to determine what they should do in cybersecurity.