Journal Entry 1
When you think about framework picture a guide of structured sets of guidelines, practices, and processes that are meant to support organizations and improve their cybersecurity. Frameworks are very useful because they offer a structured and comprehensive way for organizations to assess, protect, detect, respond to, and recover their valuable information. The systematic approach that frameworks take is what makes them so powerful. There are 5 core activities of the NIST’s Cybersecurity framework and they are Identify, protect, detect, respond, and recover. Identifying is understanding and knowing what needs to be protected in the Cybersecurity framework. For example, this happens when a framework can Identify the assets, data, and systems critical to your organization’s cybersecurity. Identifying is also one of my favorite activities, For example in a job like a threat analyst. You gain the ability to Identify and assess the capabilities and activities of cybersecurity criminals or foreign intelligence entities to produce findings to help initialize or support law enforcement and counterintelligence investigations or activities. This is the area of work or practice that appeals to me most. There aren’t any cybersecurity practices that I wouldn’t mind doing mainly because the field of cybersecurity is very vast with many opportunities and new things to learn every day.
_________________________________________________
Journal Entry 2
The principles of science and cybersecurity are closely related.This is because similarly to the scientific method, cybersecurity takes a systematic and data-backed approach to Identify, protect, detect, respond, and recover valuable information. One example of this is how observation works in science in contrast to cyber security in science observations help us identify patterns, in cybersecurity observation helps us identify unusual patterns. In relation to security a scientific mindset can be very vital for developing strategies to combat the constant threat of cyber crime. This means that when we apply the principles of science to cybersecurity we are using method-based thinking to address the digital realm.
_________________________________________________
Journal Entry 3
The PrivacyRights organization collects information about data breaches. The main of their website PrivacyRights.org is to help people identify any time their personal information has been breeched. Researchers can use the information found in the PrivacyRights.org study and formulate plans around data breaches. They can observe the pattern, and tendencies associated with data breaches to stop more from happening. The information found on PrivacyRights.org can also help researchers learn what kind of tactics and methods cyber criminals use for their attempts. This with the combination of the many other aspects of PrivacyRights.org can be beneficial in aiding researchers.
______________________________________________
Journal Entry 4
Abraham Maslow is an American psychologist who came up with the theory of Maslow’s Hierarchy of Needs. His theory proposes the idea that we all have different levels of needs and we execute them in a precise order. In relation to my digital experiences I have used Google Maps when I was lost is an example of Maslow’s physiological need in action. I have changed my password to make it stronger this is an example of Maslow’s safety needs. I use apps like Instagram and Snapchat to connect with my friends this is an example of Maslow’s love and belonging need. I have a platform on Twitter where I share my ideas on many topics this is another example of Maslow’s esteem need. Lastly, I am currently pursuing a degree in cybersecurity which in is one of Maslow’s self-actualization needs.
____________________________________________________
Journal Entry 5
Individual motives for cyber crimes
1.Money
2. Political
3. Entertainment
4. Revenge
5. Recognition
6. Multiple reasons
7. Boredom
I ranked money as the number one motive for cybercrimes because it made the most sense. The article stated that 15% of all cybercriminals use the money they gain for necessities. These are things they will likely need again and will probably commit cybercrime to get them. That is why money is number one. Political motives were ranked second because it has many practices. Cybercriminals can gain a lot politically by using their hacking to attack political organizations. Entertainment was ranked third because we all need it. Every human on the face of this earth needs a form of entertainment. In relation to cyber criminals and their motives for entertainment. By looking at data scraping, for example, we can see how cyber criminals sometimes attack for their entertainment. Revenge was ranked fourth because of the article on revenge porn. It discussed how revenge porn is a problem and how it affects the victims. Recognition was ranked fifth because it makes sense as a motive for cybercriminals. One of the best examples of this is the hacking organizations that commit their crimes for internet fame. Multiple Reasons was ranked sixth because of the article that was associated with the motive. It highlighted the various other reasons that cyber criminals commit cybercrimes such as socioeconomic and psychological reasons. Lastly, boredom was ranked last as one of the motives for cybercriminals to commit crimes because it made the least sense. Although there are cyber criminals that commit crimes because of their boredom there is no real gain in them doing so.
_______________________________________
Journal Entry 6
For this journal entry, I have been tasked with finding three fake websites and comparing them with three real websites. After looking at the three fake websites, I have noticed that they all share a common theme of unsecure URLs, poor design, and no contact information. In contrast after looking at the three real websites, I have noticed that they all shared a common theme of a secure URL, nice design, and clear and reachable contact. By comparing fake websites with real websites I was able to learn the common traits each fake website and real websites hold. This assignment has also helped me learn the importance of being able to recognize a fake website.
________________________________________
Journal Entry 7


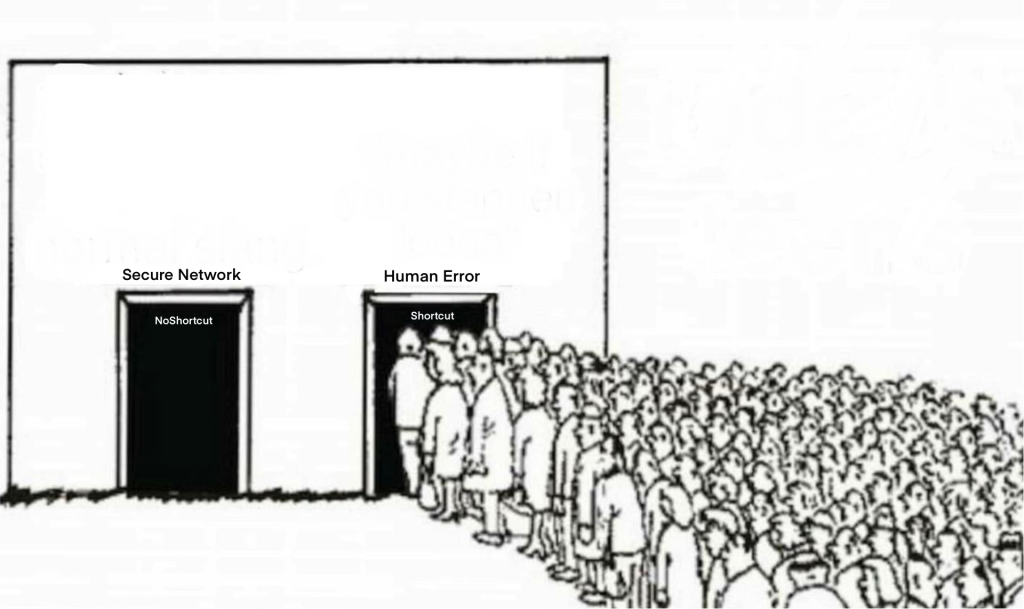
The first meme displays a man looking at his screen with an error pop-up on his laptop. The image is also accompanied by a joke about his mistake of not integrating a human firewall. This meme represents human error and how it can be avoided with a human firewall. The next meme displays a lady mistakenly clicking on a link she wasn’t supposed to. This meme represents human firewalls, human behaviors, and human errors because mistakes like these are what compromise a company’s and organization’s security. The last meme uses metaphorical imagery to display how we constantly take shortcuts as individuals and their detrimental results on our security. This is done with the help of the image of people on one line looking for a shortcut that leads them to human error.
___________________________________________
Journal Entry 8
After watching the video on how movies distort hackers it is very clear how the media influences our interpretation of the cybersecurity realm. Malcolm X once said, “The media’s the most powerful entity on earth. They have the power to make the innocent guilty and to make the guilty innocent, and that’s power. Because they control the minds of the masses”. In the same way in our world today the media plays a prominent role in our perception of the world around us. Our understanding of cybersecurity is heavily influenced by the media. One example of this is the portrayal of hackers. They are often entirely inaccurate. Portraying the abilities and role of cyber attackers and hackers in exaggerated and unrealistic tones.
_________________________________________________
Journal Entry 9
After completing the social media disorder scale, I scored 0 / all no’s. According to the tests I have had no signs of addiction to social media during the past year. I liked the questions in the test because they spoke directly to this era of young people. Asking questions like “During the past year have you regularly found that you can’t think of anything else but the moment you will be able to use social media again?”. Different patterns are found across the world are found across the world because the power of social media has tremendous power over our world today.
_________________________________________________
Journal Entry 10
The central theme of the article was centered around the evolving world of social cybersecurity. The article explored how cybersecurity plays a critical role in our modern warfare and national security. It sheds light on how technology has transformed information warfare into a powerful tool for manipulating nations, shaping our narratives, and influencing our geopolitical outcomes. The article also delved into a discussion on Russia’s information. Overall, though the article served as a reminder of the ongoing contributions that cybersecurity makes to our every day. The interconnectedness of technological advancements, societal vulnerabilities, and geopolitical strategies in our world are shaping the future of warfare and national security in our country today.
___________________________________________________
Journal Entry 11
The video I watched today delved into the role of a cybersecurity analyst. Nicole Enesse talked about the key aspects of a cybersecurity analyst as the title, responsibilities, salaries, and job outlook of a cybersecurity analyst. The most significant social theme discussed in the video involves the changing nature of work and career paths in our digital age. Nicole Enesse talked about how job titles vary from company to company reflecting how technology has transformed our traditional job roles and created new ones. Additionally, she also talked about entry-level positions and the demand for cybersecurity professionals. This shows how we as a society are shifting towards prioritizing digital security in our world today.
_________________________________________________
Journal Entry 12
After reading “SAMPLE DATA BREACH NOTIFICATION” I found two different economics theories and two different social sciences theories that relate to the letter. From an economic standpoint, the data breach notification letter relates to both information asymmetry and cost-benefit analysis theories. Information asymmetry theory is seen in how the company reacts, upon discovering the breach, and has chosen to notify customers about potential risks despite not having evidence of actual misuse of their information. The letter also touches on cost-benefit analysis, as it tells the customers they can protect themselves against identity theft or fraud, by highlighting the potential costs financial losses, or inconvenience that might come as a result of the possible breach. From a social sciences lens, the breach notification letter closely relates to social contract theory and risk communication theory. Social contract theory is displayed by the way the company acknowledges its responsibility to inform customers about the breach and offers guidance on protective measures. The risk communication theory is seen when the letter tries to communicate complex information about the breach, and potential risks.
___________________________________________________________________
Journal Entry 13
The bug bounty policy discussed in the literature review shows it’s a good way to boost cybersecurity. The research points out that hackers are driven by more than money they also value experience, reputation, and the desire to help others. I believe encouraging ethical hacking helps find weaknesses and builds a group of experts committed to bettering cyber defenses. Bug bounty programs adjust well for both novice and experienced hackers, according to HackerOne program managers. This flexibility makes them useful for businesses big and small.
___________________________________________________________________
Journal Entry 14
From Andriy Slynchuk’s eleven points. I feel that there are five that are that are the most serious violations. The first serious violation is using unlicensed streaming services. This involves accessing copyrighted content without authorization, which supports piracy and causes financial losses for creators. The second serious violation is revealing someone else’s details like passwords or addresses without their permission. This invades privacy and could cause identity theft or harassment. The third serious violation is engaging in cyberbullying or trolling. These actions can lead to emotional harm and might result in criminal charges in extreme situations. The fourth serious violation unauthorized recording of VoIP calls. This infringes on privacy rights and may bring about legal repercussions. The last serious violation is illegally extracting audio from YouTube videos or prohibited searches.
____________________________________________________________________
Journal Entry 15
Davin Teo’s path to becoming a digital forensics is very interesting. He started his career in accounting. As his interest and proficiency in IT grew it led him to specialize in digital forensics. Davin Teo is very passionate about solving intricate puzzles and uncovering digital evidence. This is very evident from his detailed case studies. His shift from old-fashioned data-gathering methods to the latest technological advancements shows how quickly technology can transform forensic investigations. Mr. Davin’s journey shows us the principles of interdisciplinary work by combining his IT skills and digital forensics. Overall, his career path highlights the multidisciplinary nature of digital forensics. Many bridging aspects of IT expertise interconnect investigative skills. I liked his story. It resonates with me because this intersection of technology and social sciences is very cool.
