Part I
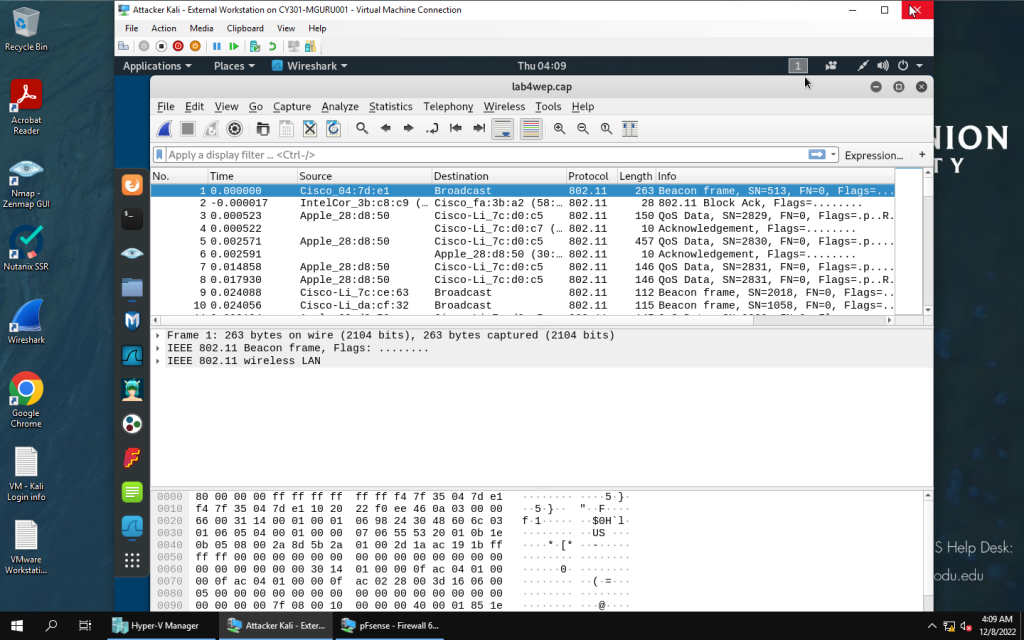
Wireshark before cracking
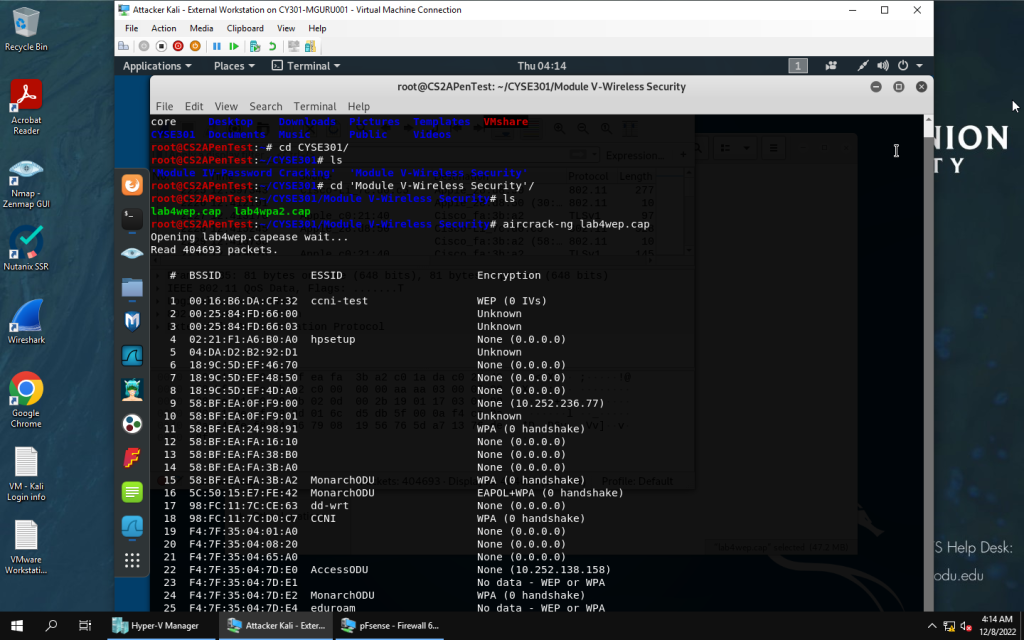
aircrack-ng use on first .cap file
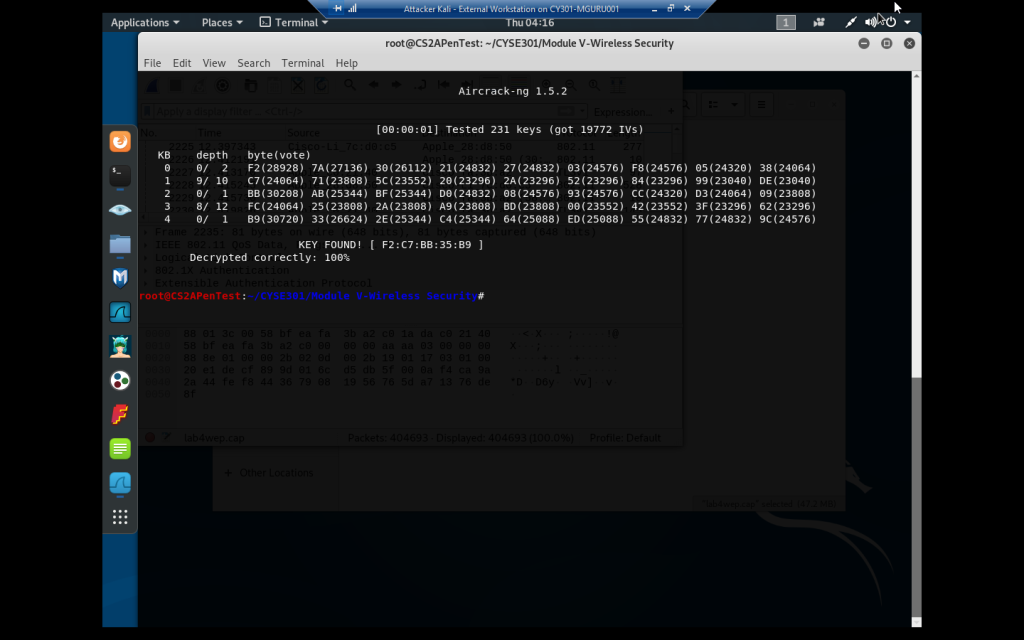
aircrack-ng on the WEP option
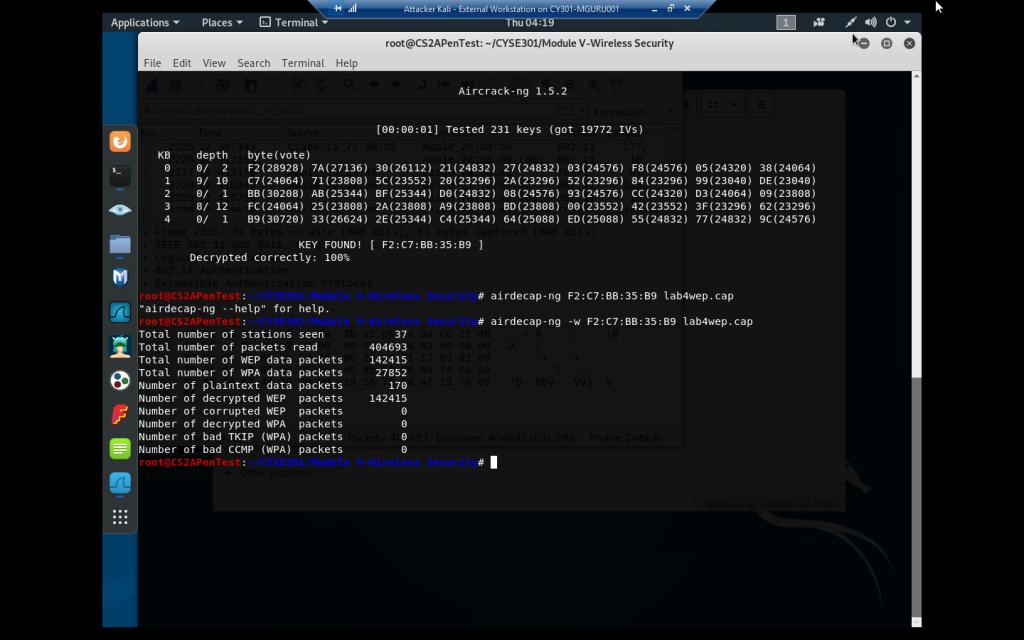
Decryption using airdecap-ng
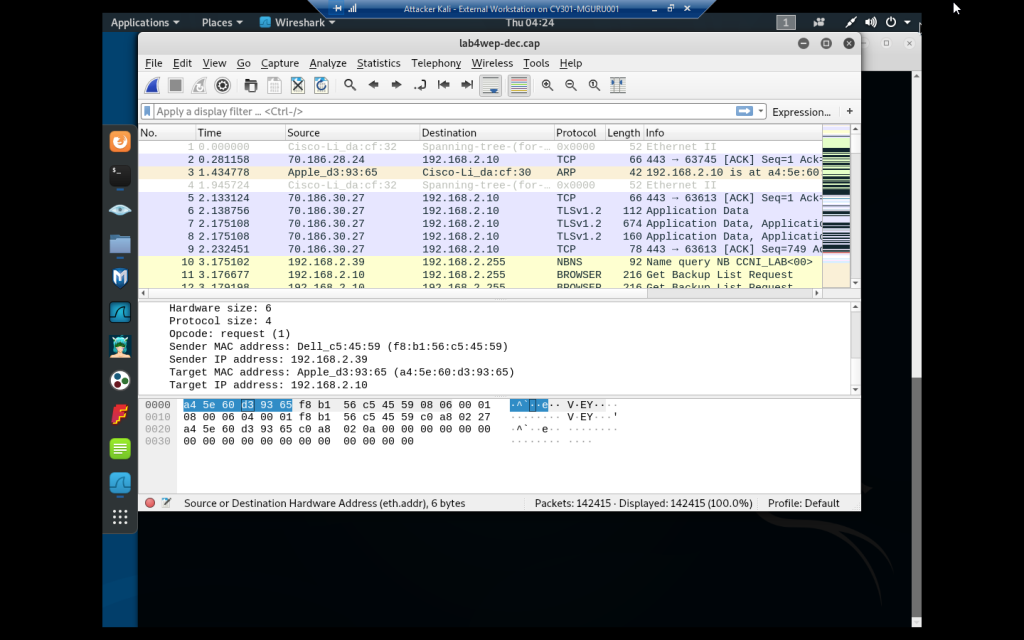
Initial decrypted Wireshark file

Wireshark of file with “arp” display filter
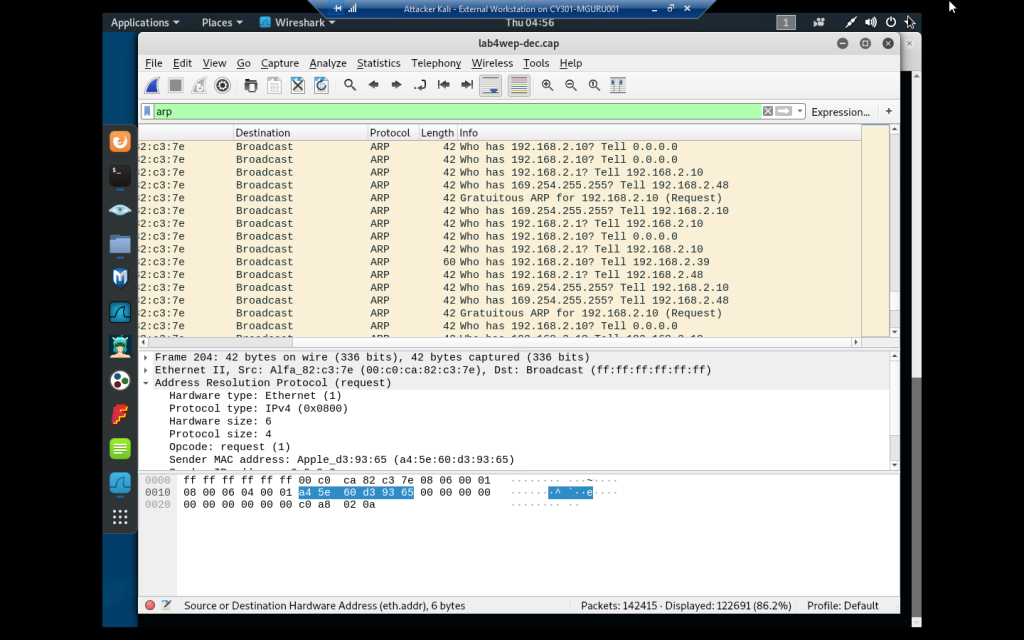
More ARP requests and gratuitous ARP requests
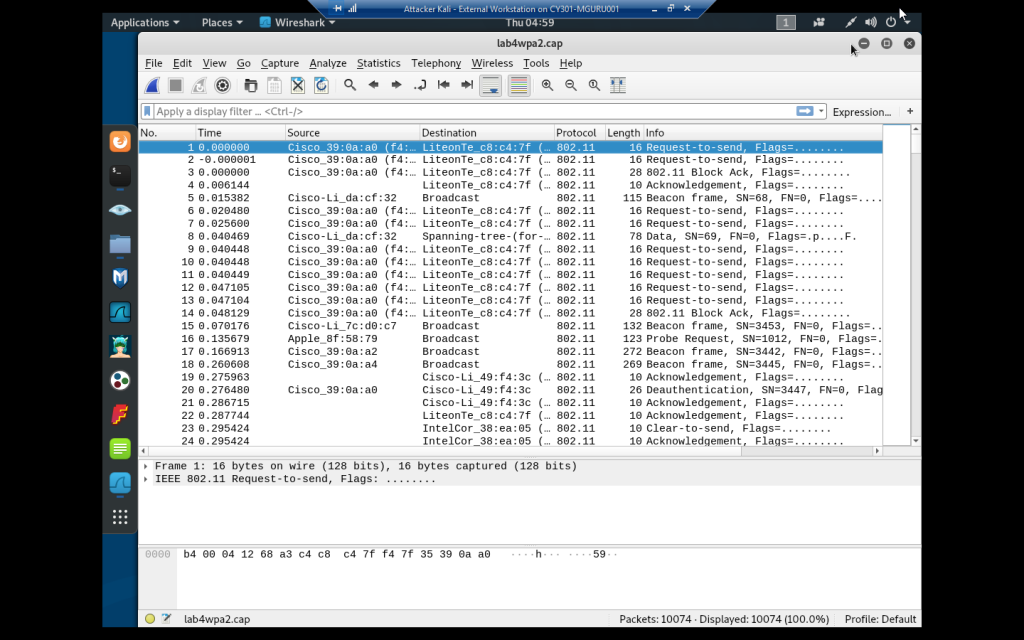
Wireshark of second .cap file
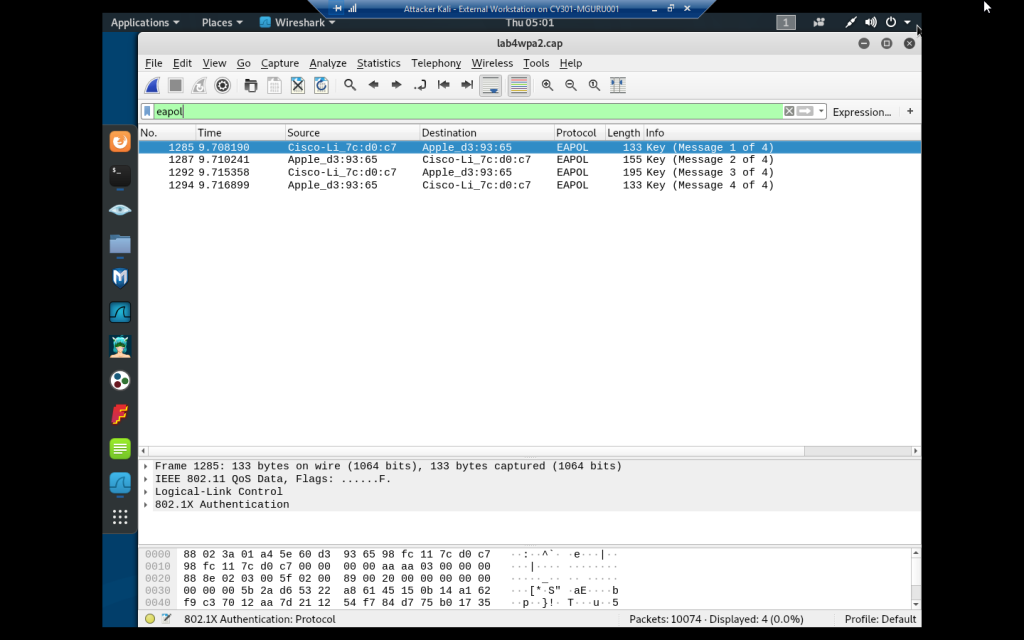
Finding a 4-way handshake in the capture
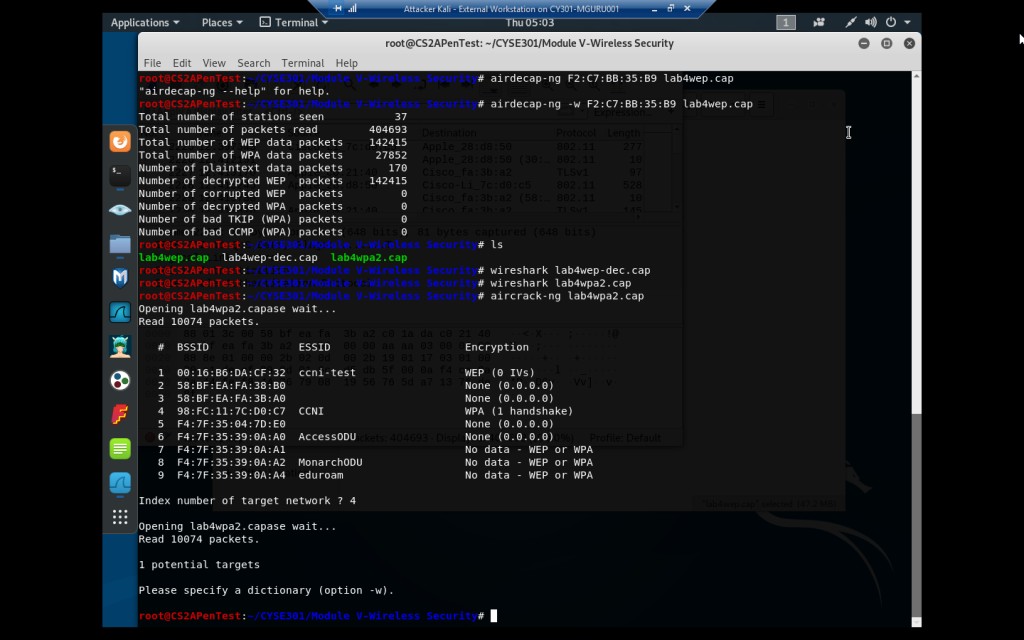
aircrack-ng command to find a WPA encryption with the handshake
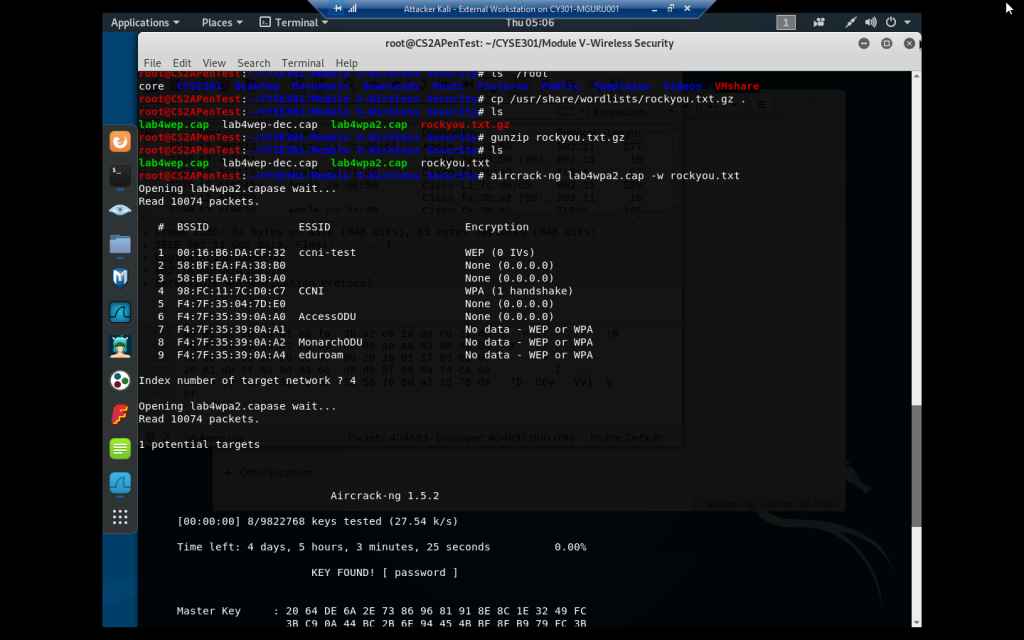
aircrack-ng command with -w option to add the wordlist rockyou.txt on WPA encryption with ESSID: CCNI

Decryption
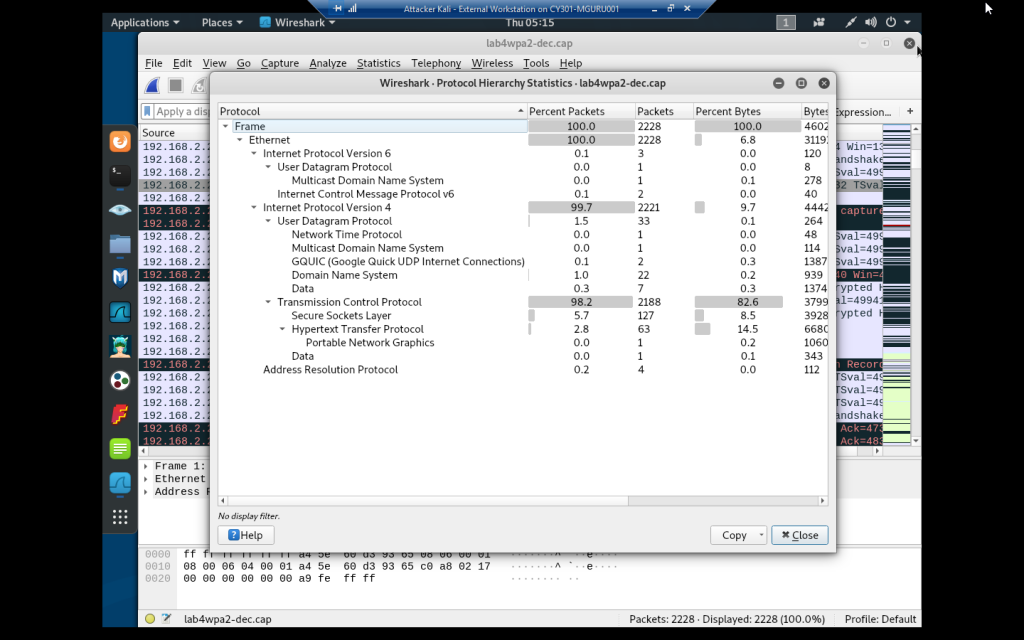
Protocol statistics
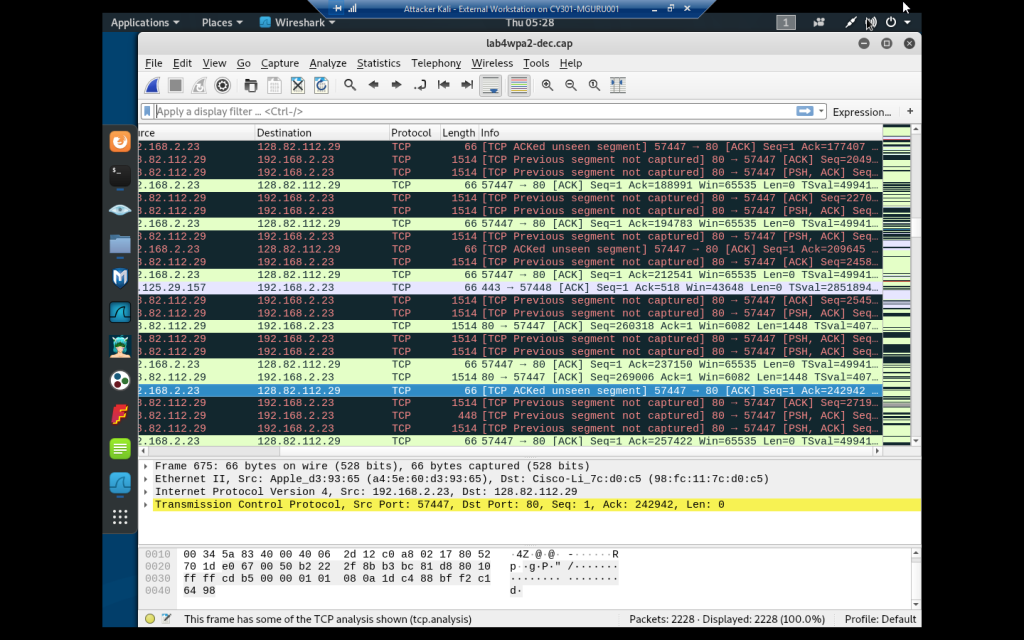
Wireshark of decrypted file
Part II
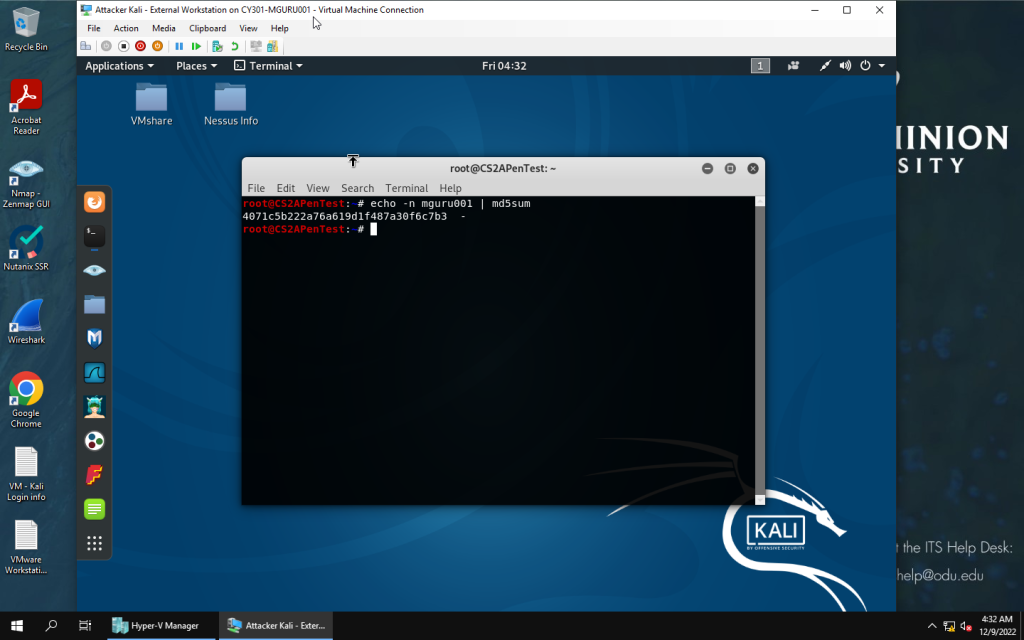
Getting MD5 hash for my Midas ID
Saving my .cap file into the VMshare folder on the virtual machine host
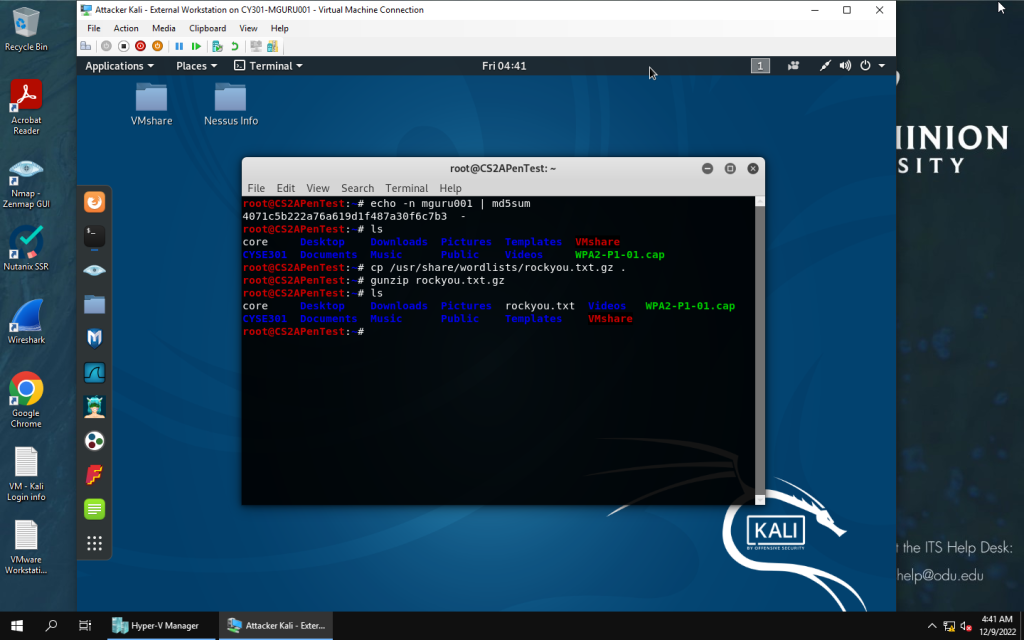
Moving wordlist to working directory
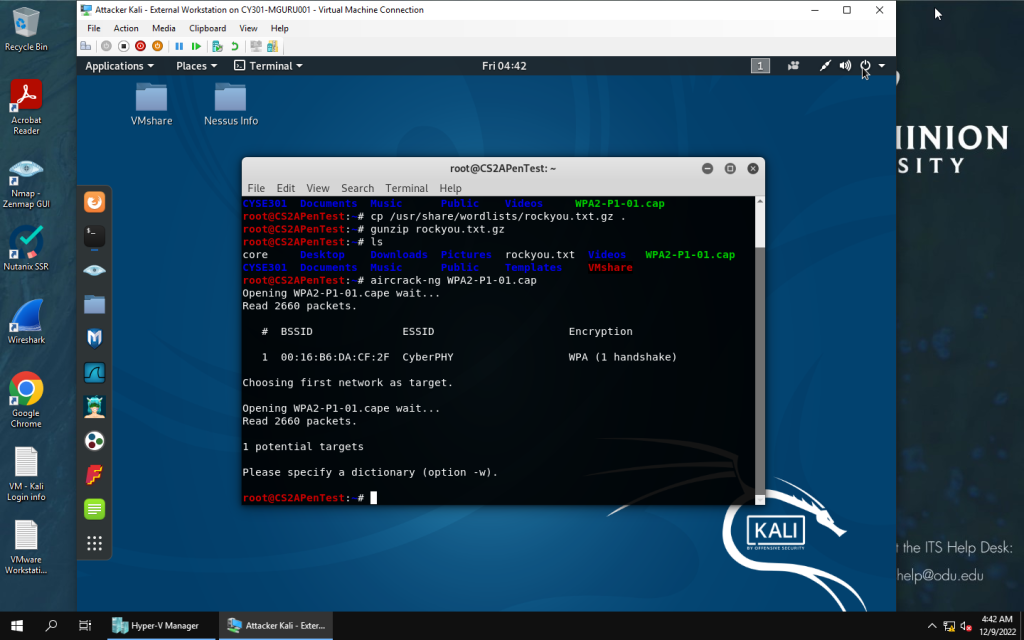
aircrack-ng on file to find encryption
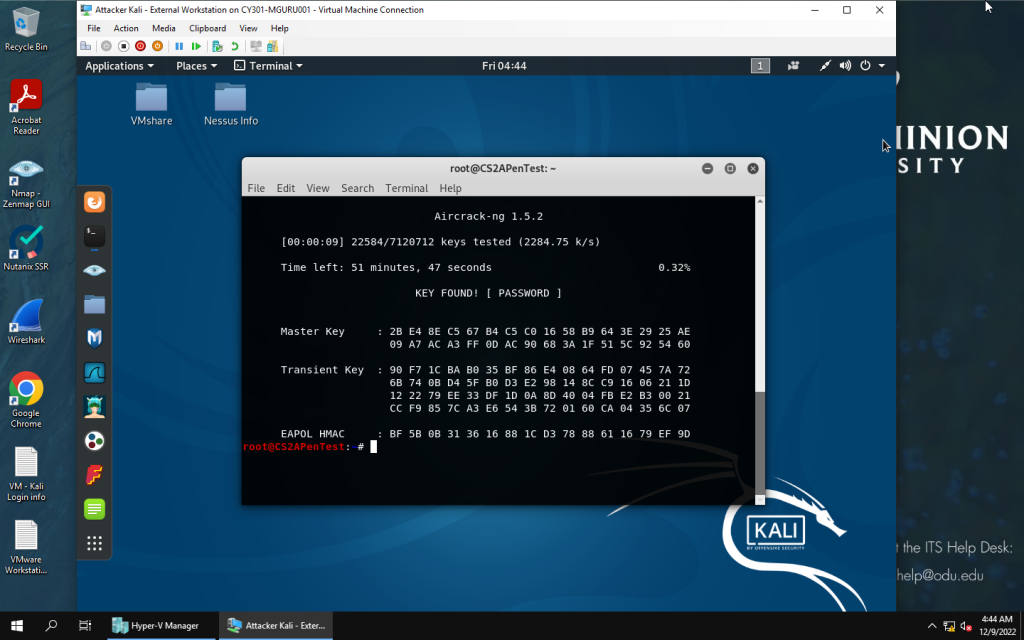
aircrack-ng with option -w used with rockyou.txt to find KEY
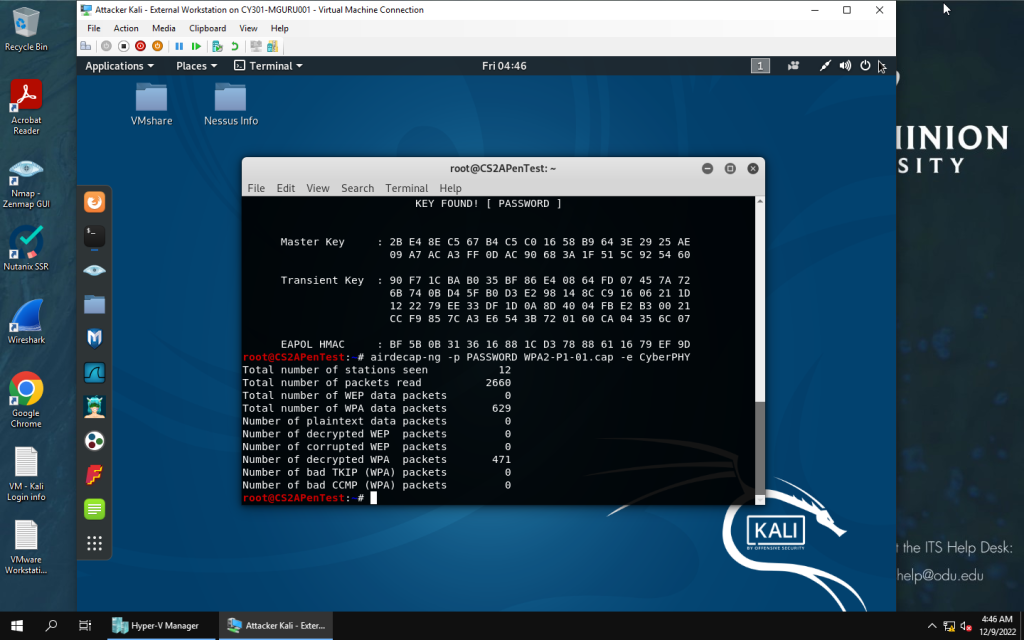
airdecap-ng with options -p to input password KEY and -e for ESSID: CyberPHY