Journals
Week 15 – Journal Entry 15
Digital Forensics | Davin Teo | TEDxHongKongSalon
I find the pathway to Mr. Teo’s career interesting. He started off as an accountant in a small firm. He states he had no formal education in IT or digital forensics. At some point during his tenure as an accountant in the small firm, he found that they needed IT help, so he pivoted into working IT along with accounting at that firm. It led to him working at a “Big Four” accounting firm. He left that firm to work in the first national digital forensic practice in Australia.
Week 12 – Journal Entry 13
A later module addresses cybersecurity policy through a social science framework. At this point, attention can be drawn to one type of policy, known as bug bounty policies. These policies pay individuals for identifying vulnerabilities in a company’s cyber infrastructure. To identify the vulnerabilities, ethical hackers are invited to try explore the cyber infrastructure using their penetration testing skills. The policies relate to economics in that they are based on cost/benefits principles. Read this article https://academic.oup.com/cybersecurity/article/7/1/tyab007/6168453?login=trueLinks to an external site. and write a summary reaction to the use of the policies in your journal. Focus primarily on the literature review and the discussion of the findings.
The journal emphasized the reluctance of firms to adopt VDPs (Vulnerability Disclosure Policies) and Bug Bounties leading to underreporting of vulnerabilities due to fears of repercussions among researchers. Bug Bounty programs are based on cost-benefit principles, offering financially beneficial alternatives to having their own cybersecurity teams. Bug Bounty programs leverage the gig economy to deal with the cybersecurity talent gap. The journal provided a thorough empirical analysis using data from HackerOne. The findings highlighted several issues: Hackers exhibit price inelasticity suggesting that monetary rewards are not their sole motivator. Company size and brand have minimal impact on the number of reports received, which supports the value of bug bounty programs across differing business models. Finance, retail and healthcare receive fewer reports possibly because of the potential for monetization of vulnerabilities in these sectors. The paper acknowledges the limitations of the current understanding of bug bounty programs pointing out the significant unexplained variance in the data and the potential impact of omitted variables such as report severity and scope of the threat. The literature and findings provide good insight into the efficacy of bug bounty programs, showing their importance in modern cybersecurity strategies as well as the need for continuous research.
Week 12 – Journal Entry 12
Read this https://dojmt.gov/wp-content/uploads/Glasswasherparts.com_.pdf sample breach letter “SAMPLE DATA BREACH NOTIFICATION” and describe how two different economics theories and two different social sciences theories relate to the letter.
Risk Management Theory looks at how organizations manage uncertainty and the potential for undesirable outcomes. This theory applies to this paper because it relates to how the company and its provider manage risk associated with cyber threats. The break indicates a break in their risk management process and the response is an attempt the manage the aftermath of the risk happening. Another economic theory that applies is Transaction Cost Economics; it examines the cost associated with making transactions in the market. In this case, there are increased transaction costs for everyone involved. The company needs to spend resources to handle the fallout, the customers will be at the minimum inconvenienced as well as the possibility of having their identities stolen as well as the broader implications of trust in online transactions.
The Social Contract Theory applies to this because it explores the implied understanding between individuals and institutions. The breach could cause consumers to question the social contract between them and the company; a consumer provided personal information with the expectation that the information would be secure. The breach could cause customers to reevaluate if using this company is worth it. Symbolic Interactionism is a theory that focuses on meanings attached to human interaction. In the case of this breach, the notification letter isn’t just a communication alerting customers of the breach but it is also an act that depending how the letter is written and delivered, could impact the customer’s interpretation of the reliability and trustworthiness of the company.
Week 12 – Journal Entry 11
Write a paragraph describing social themes that arise in the presentation.
https://www.youtube.com/watch?v=iYtmuHbhmS0Links to an external site.
In the video the most obvious tie to to social themes is the importance of networking. You may need to call upon your social network for various reasons in life whether it’s getting a job or getting help with a job or personal issues.
Week 11 – Journal Entry 10
I found the article at https://www.armyupress.army.mil/Journals/Military-Review/English-Edition-Archives/Mar-Apr-2019/117-Cybersecurity/b/ about social cybersecurity enlightening. Social cybersecurity crosses technology, psychology, and national security. Unlike tradition cybersecurity which focuses on safeguarding information systems from technological breaches and attacks, social cybersecurity goes into the realm of human behavior. It looks at how digital platforms can be weaponized to manipulate societal beliefs, behaviors, and political outcomes. The cyber domain is a battlefield where information is both a tool and a target.
The article highlighted the belief that we are not just in a digital way against code and other machines but also in a struggle over the control of human cognition and societal norms. The term “Social Cybersecurity” describes efforts to understand and mitigate threats that exploit social, cultural, and political vulnerabilities through cyber means. The article highlighted a shift from hacking just machines to hacking human minds, a process described as “cognitive hacking”.
Overall an interesting article that serves as a reminder of the shift in national security and warfare. It emphasized the need for innovation to protect against various threats posted by adversaries in the cyber domain.
Week 10 – Journal Entry 9
Complete the Social Media Disorder scaleLinks to an external site.. How did you score? What do you think about the items in the scale? Why do you think that different patterns are found across the world?
Social Media Disorder Scale (SMD Scale)
Please answer the question by thinking of your experience with
using social media (e.g., WhatsApp, SnapChat, Instagram,
Twitter, Facebook, Google+, Pintrist, forums, weblogs) in past
year. Answer the questions as honestly as possible. According
to DSM, at least five (out of the nine) criteria must be met for a
formal diagnosis of “disordered social media user”.
During the past year have you…
- Regularly found that you can’t think of anything else but
the moment you will be able to use social media again?
Yes/No (Preoccupation). - Regularly felt dissatisfied because you want to spend more
time on social media? Yes/No (Tolerance). - Often felt bad when you could not use social media?
Yes/No (Withdrawal). - Tried to spend less time on social media, but failed?
Yes/No (Persistence). - Regularly neglected other activities (i.e. hobbies, sports,
homework) because you wanted to use social media?
Yes/No (Displacement). - Regularly had arguments with others because of your
social media use? Yes/No (Problems). - Regularly led to your parents or friends about the amount
of time you spend on social media? Yes/No (Deception). - Often used social media to escape from negative feelings?
Yes/No (Escape). - Had serious conflict with parents, brother, sister (friends,
relationships etc.) because of your social media use?
Yes/No (Conflict).
9-item scale measures adolescents degress of addiction to
social media. Based on scale from Internet Gaming Disorder
found in the DSM-V, for preoccupation, tolerance, escape,
persistence, withdrawal, conflict, problems, deception, and
displacement. (n= 724), reliability good.
Van den Erjnden, RJ.J.M., Lemmons, J.S., & Valkensburg P.M.
(2016). The Social Media Disorder Scale. Computers in Human
Behavior, 61, 478-487.
I scored a zero. I do use minimal social media…I have a facebook account to keep in touch with friends and family for example. That’s just to use messenger, I almost never post on facebook, and certainly dont look forward to using it. My go to is instagram reels, but I never go out of my way to watch social media. Generally I’ll only use it in the bathroom and waiting on something else to happen. The items on the scale are concerning if people are actually experiencing these things due to social media. I know there are some people out there who take it very seriously, but I definitely cannot relate. Different patterns are found around the world because of different cultures and influences.
Week 7 – Journal Entry 7
Review the following ten photos through a human-centered cybersecurity framework. Create a meme for your favorite three, explaining what is going on in the individual or individual’s mind(s).
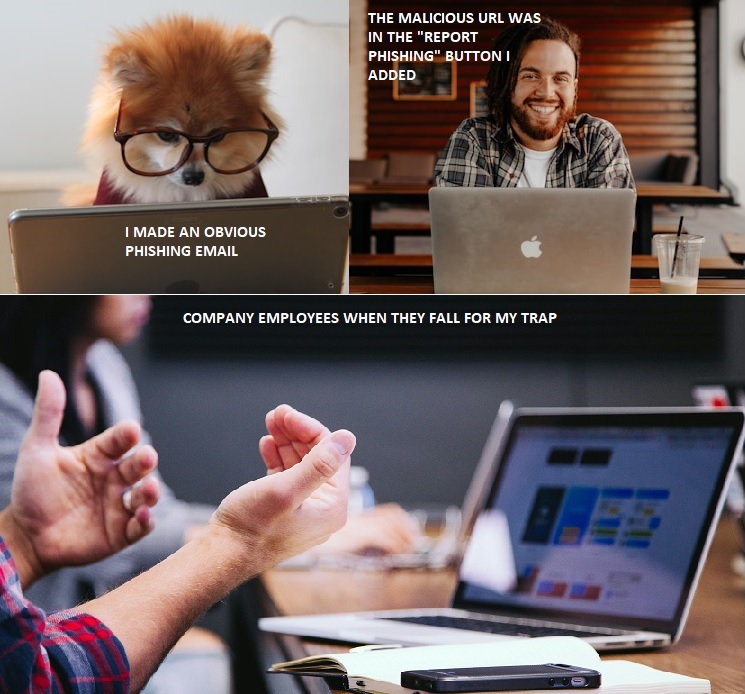
It relates to cybersecurity because some cybersecurity professionals create fake phishing emails for their company on a regular basis, and some people want to watch the world burn.
Week 6 – Journal Entry 6
Can you spot three fake websites and compare the three fake websites
to three real websites, plus showcase what makes the fake websites
fake?
The first fake website I found was “tiffanycoshop.com”. This site aims to deceive people into believing they are shopping from Tiffany. On the legitimate tiffany website, tiffany.com, under their FAQ section, they list all legitimate tiffany sites and retailers; tiffanycoshop isn’t on the list. The next indicator is price. Anyone looking to buy Tiffany jewelry should know they arent getting a piece for $30. Under the contacts section of the website, we can look up the address and find that it’s an Under Armour outlet in Texas.
The next fake site I found is “sheingivesback.com” attempting to fool victims into believing they are signing up to receive a $750 gift card by completing various tasks. When you click sign up, it’ll ask a few simple questions then ask for an email. When I entered a fake email, it asked for more personal information. I then provided the site a fake name, address, and phone number and it directed me to take a bunch of surveys. This is a classic phishing website.
Lastly we have “brookshoeoutlet.com”. This website is misrepresenting itself as an official Brooks retailer. One immediate warning is that the shoes are cheaper than anywhere else on the internet. The other is that on the official Brooks website, they say that brooksrunning.com is the only Brooks website. Next we notice that the selection on the fake site is severely limited. Lastly their contact us section is lacking in any information.
Week 5 – Journal Entry 5
Ranking motives in the order of the most to least sensical. First of all, I believe they all make sense. I don’t agree with most, but they make sense.
- Money – The mother of all motivations. Money is why I’m in this class, both because I paid for it, and because I aim to make more money at the conclusion of my degree. Money is one of my biggest motivating factors.
- Boredom – In middle school boredom is what led me to explore hacking and playing with my school’s telnet via dos.
- Entertainment – If I need something to do, hopefully it’s something I find entertaining. Kind of goes hand-in-hand with boredom. Bordem can lead one to find entertainment in cybercrime.
- Revenge – What better way to motivate yourself than getting even with someone or some entity that wronged you!
- Recognition – The first one that doesnt make much sense to me. Well, it makes sense in that if you’re a person that enjoys being the center of attention, and you can commit some type of crime to get massive amounts of attention, I guess I get it. It just goes against my more introverted perspective.
- Political – Again, not something that motivates me, but if you’re someone that seeks political gain, to each their own.
- Multiple reasons – I would assume that is the category that fits most people who commit crime. Usually there’s more than one reason that got them there.
Week 4 – Journal Entry 4
Technology is intertwined with Maslow’s Hierarchy of Needs at every level. Our Physiological needs; food, water, warmth, and rest, are all controlled with digital technology. Crops are harvested with self driving machines, water is controlled by industrial technology, my thermostat is digital, and my bed and house materials were all manufactured in factories with digital controls. Our safety and security from a societal standpoint are all controlled digitally. Police, fire, and medical use radios, vehicles, and equipment with microprocessors. As for belongingness and love needs, our primary means of communication with our loved ones is through a smart phone. Many people are able to achieve their esteem needs by posting their accomplishments or their day to day lives on social media and gain praise from friends, followers, and loved ones. Sometimes they can receive the opposite as well; a double edged sword. For self-actualization, I don’t know if technology is a requirement, but undoubtedly, technology helps in every aspect of life.
Week 3 – Journal Entry 3
Privacyrights.org is a website containing a detailed list of data breaches, providing a great resource for researchers. The information contained in privacyrights.org can use used to study trends in data breaches. It can also be utilized to see which vulnerabilities are being exploited, understand what is being targeted and from there assess the effectiveness of organization’s cybersecurity policy. If a place is never attacked, perhaps they’re doing something right.
Week 2 – Journal Entry 2
The principles of science such as relativism, determinism, parsimony, skepticism, and objectivity have a significant role in cybersecurity. Relativism implies that cybersecurity risk assessments can be subjective based on the perspectives and the priorities of the stakeholders. Risk that seems minor to a technical person may be major from a business or legal perspective. Determinism in cybersecurity implies that cyber attacks are determined by indentifiable factors. If one had complete knowledge, one would see a cyber attack coming basically. However, deterministic principles can be applied in cybersecurity; one example would be logging and databasing analysis of cybersecurity breaches, collecting big data and using machine learning to identify commonalities to help identify patterns to predict cyberattacks in the future. Parsimony, or Occam’s Razor, suggests that we should keep things as simple as possible. This applies in cybersecurity. We should keep systems and simple as possible for efficiency. A simple system is an easier system to secure. Cybersecurity professionals should be skeptical about the security of their networks and systems, testing for vulnerabilities. In cybersecurity objectivity is critical for assessing risks and incident response.
Week 1 – Journal Entry 1
Reviewing the NICE framework, the most appealing area that I’d like to focus my career on is the collect and operate category which is difficult because they all seem interesting. The specialty areas of Collection Operations, Cyber Operational Planning, and Cyber Operations all seem like careers that would suit me. On the other hand, the area that looks like it would appeal to me the least (at least based on the overview on cisa.gov) is the Securely Provision area. I have zero interest in Software Development, Systems Architecture, or Systems Development; these all seem more like Software Engineering or Programming jobs.
