Protecting Small Businesses from Cyber Threats
Michael Figliotti
OLD DOMINION UNIVERSITY
CYSE 595 ENTREPRENEURSHIP IN CYBERSECURITY
Dr. Brian K. Payne
June 20, 2022
Table of Contents
1. Introduction
2. The Problems
2.1 Business Email Compromise (BEC)
2.2 Spear phishing That Could Lead to BEC
2.3 Ransomware
2.4 SIM Swapping
2.5 Other Vulnerability Vectors
2.6 Passwords
3 The Solution
3.1 Services Offered and Sales Methodology
4 Possible Barriers
5 The Assessment
5.1 Items Needed
6 Next Steps
7 Works Cited
8 Reflection Letter
Protecting Small Businesses from Cyber Threats
Introduction
Small businesses lack cybersecurity awareness and protections. Cybercrime such as ransomware, email compromise and an increase in tech support scams are the biggest vulnerabilities for companies and are on the rise. These attacks and scams can be devastating to a small business that cannot afford the costs associated with complete data loss or in the case of email compromise, loss of money due to it being transferred out under a false pretense.
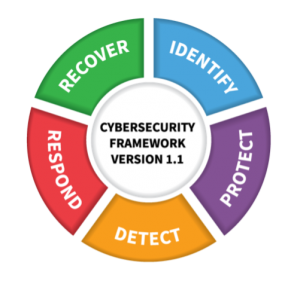
The US government has made significant progress in cyber defense, however it is mainly focused on protecting large corporations and critical infrastructure providers. The documents, best practices and checklists created by the National Institute of Standards and Technology (NIST) highlight this fact. The Cybersecurity Framework (CSF) is a complex and thorough checklist containing recommended actions to protect against the majority of threats that can cause financial and data loss or compromise, but it does not help small businesses with only a few computer systems and minimal computer servers, if any.
This innovation is a service company tailored towards the cybersecurity needs of small businesses. Small business proprietors need a trusted support agent and consultant to evaluate their systems, make recommendations and execute complex changes. Internet facing websites, service portals and online presence in search engines is a requirement in the modern business landscape, regardless of how nontechnical the business is. The Small Business Administration has stated that 99% of businesses in the US are small businesses, this equated to 32.5 million small businesses in the US in 2021.
The flagship service of this new company will be assessing the small businesses IT infrastructure and auding cybersecurity practices to verify that both electronic devices and online accounts are secure. This assessment will be based on the NIST CSF but adapted to fit the needs of small businesses. Once the assessment is completed, we will offer additional services to remedy or mitigate threats and vulnerabilities.
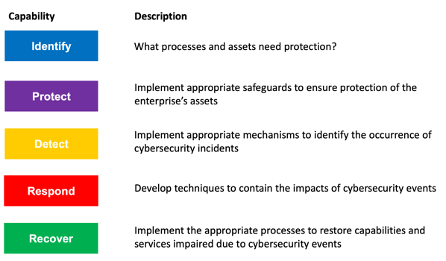
The NIST CSF is based on the idea that you constantly follow the Identify, Protect, Detect, Respond, Recover cycle. This cyclical process indicates that cybersecurity is not a “one and done” event, it is a process and a culture that goes hand in hand with modern business operations.
The Problems
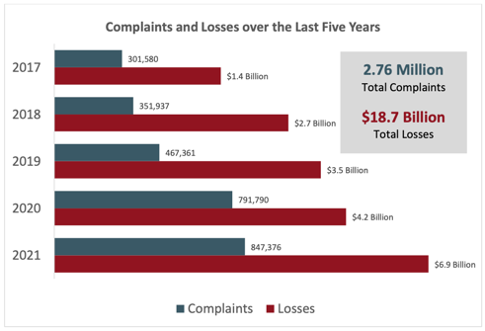
The FBI’s Internet Crime Complaint Center (IC3) releases an annual internet crime report that has shown a steady increase in the number of reported cybercrimes and the monetary value of the losses. According to an article by Alexander Cuiafi at TechTarget, It is also widely believed that the astronomical figures of complaints and losses are underreported due to ignorance of the reporting process, or the feeling of shame associated with falling victim to a crime or scam. Of the nearly $7 Billion lost in 2021, $2.39B were business email compromise and email account compromise (BEC/EAC) losses, $517M were Personal data breach losses and $347.6M was due to tech support scams. (IC3) As a student of cybersecurity, and the family tech support, I consistently read news and field questions related to preventing identity theft and data loss at an increasing rate. These statistics are the most complete and accurate data available for the United States and are a basis of which areas to focus on to provide the most significant impact.
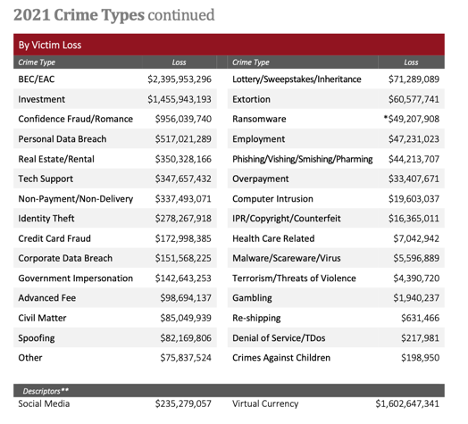
When looking at the victim loss chart sorted by loss value, it provides a clear guide of where to focus efforts and how to tailor the small business audit checklist. Many of the crime types listed below, such as “investment, Romance, Lottery” are more focused on individuals and will not receive much attention despite the high loss amounts. My company will focus primarily on “BEC/EAC, Tech Support, Data Breach, and Ransomware”. Many of the other categories can be mitigated by providing general training to employees.
Business Email Compromise
Business Email Compromise (BEC) is a broad term used to describe the use of leveraging an assumed authoritative position by a person for fraudulent purposes. This most often occurs when a hacker gains access to a CEOs, Owner, or other powerful decision makers email credentials. The hacker/scammer will lurk for months sometimes to learn the pattern of emails and look for an opportune time to leverage that knowledge. (Cidon, Asaf, et al) For instance if large bank transfers normally happen quarterly, the hacker could send an email posing to be the CEO to the employee who normally completes the transaction but include a new account number with a plausible explanation. By the time the CEO and employee figure out what happened, the money is gone and often time not recoverable.
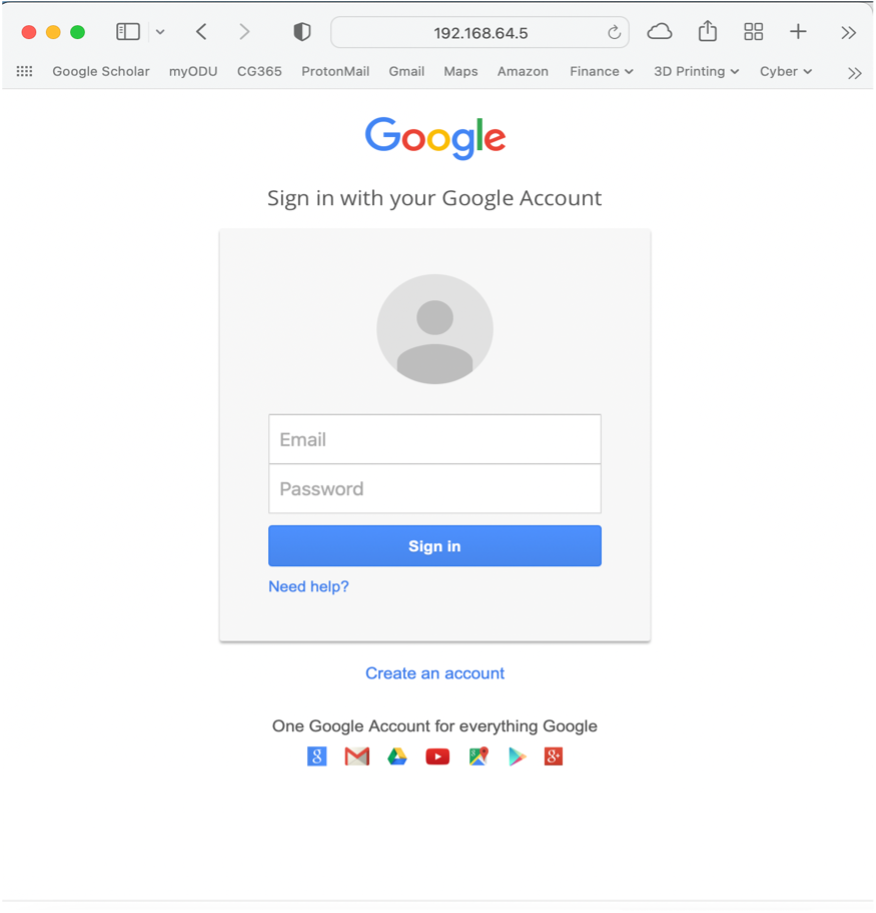
How does BEC actually happen? It is often accomplished by a simple phishing email sent to high value targets. (Buo, Shadrack Awah) The technique of identifying a high value target using open-source intelligence (OSINT) methods and then sending a phishing email to hijack their account credentials is known as Spear Phishing. These phishing emails can look identical to a real email from Google, Microsoft, or can clone any website login page if needed. Below is a example spoofed login page that I created using the Social Engineering Toolkit (SET) application included with Kali Linux, a popular Linux Distribution used by both security researchers and malicious hackers. These tools are freely available online and are fairly easy to use.
BEC is actually even more nefarious that it seems. In addition to sending emails that instruct others to transfer funds on your behalf, an attacker can change the password to your email account. Once they have exclusive access, they can use that email to reset passwords for other valuable sites, such as banking. Remember, whenever you forget your password to a site, it is usually able to be reset by sending you an email to the account on file, and since the attacker has spent weeks sifting through your old emails in your account, they have a list of targets and will take over all of them in rapid succession. They will then use this access to high value accounts to extract money if it’s a banking account or use access as leverage to extort funds directly from their victims. This type of attack is best defended against by not clicking on suspicious links and enabling two factor authentication (2FA). If 2FA had been enabled, the attacker would not be able to gain access to the email account without the authentication code.
Spear phishing That Could Lead to BEC
Above: Malicious page that will steal your username and password.
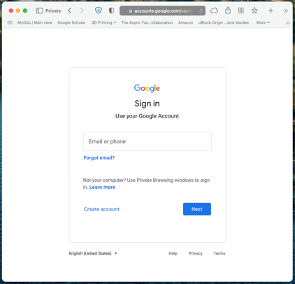
Above: Authentic Google sign in page.
The main differences here are that the malicious cloned site has an IP address in the address bar whereas the legitimate site has an accounts.gooogle.com address.
Additionally, Google has updated their site to only prompt for a password after receiving the email address username. This specifically prevents against this kind of attack, but only if the user recognizes it as being inconsistent.
Additionally, if an attacker wanted to make their site less conspicuous to the target, they could register a domain name that looks legit, such as accountgooglesignin.com and redirect that site to their IP that is standing by ready to capture credentials.
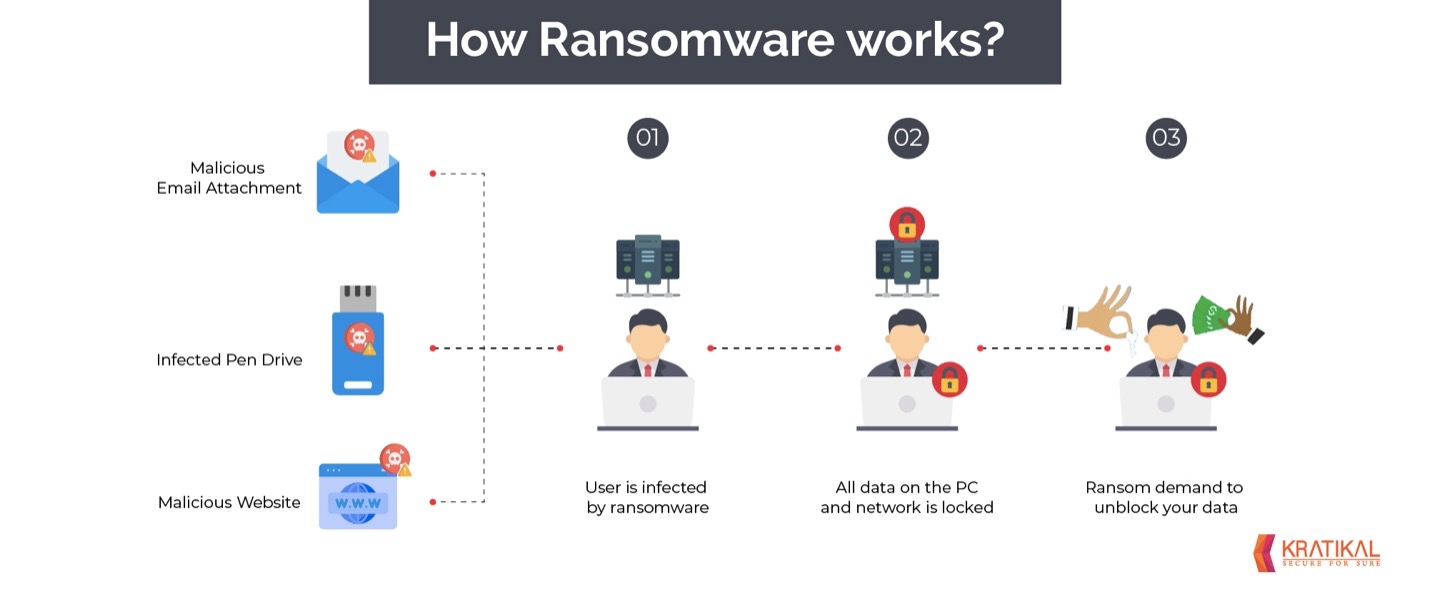
Ransomware
Ransomware was not at the top of the FBI’s list for most losses, but this is because it did of how the figure was calculated. According to the FBI’s report, “Regarding ransomware adjusted losses, this number does not include estimates of lost business, time, wages, files, or equipment, or any third-party remediation services acquired by a victim.” The main threat from ransomware is the loss of data, hardware, productivity and ultimately sales. Actual losses from ransomware can be far worse once these factors are considered.
NotPetya is the name of the costliest cyberattack in history and the prime example for demonstrating the dangers and impact of ransomware. “The result was more than $10 Billion Dollars, according to White House assessment confirmed to WIRED by former Homeland Security adviser Tom Bossert…” (Greenberg) The NotPetya virus ended up being a data wiper in disguise as ransomware, even if victims paid the Bitcoin ransom, it was impossible to recover their data. The best protection against ransomware is having a recovery plan. This plan should include making and then testing your backups. Many people now turn to cloud backups to handle their backup needs. This method reduces the friction associated with hard media backups, but can be tricky to configure for multiple devices in a business setting.
SIM Swapping
A sim swapping attack is when an attacker attempts to take over your phone number onto their device so that when a text is sent with a verification code, they will receive the code instead of you. (Russo) Additionally, it is best to protect against sim swapping attacks by using an authenticator app such as Google Authy, Microsoft Authenticator or DUO instead of relying on text messages. Again, it’s a keys to the kingdom scenario, but it is more secure than SMS based authentication codes.
Scammers often target individuals with high value bank, brokerage, or crypto accounts to target for these attacks and have a 39 out of 50 success rate. (SNB) These individuals are targeted by their activity on social media, however, in person targeting can also occur if someone sees a company doing lots of business. Currently Verizon is the most secure against sim swapping attacks due to their account security measures. A study done by Recorded Future found that how-to guides for sim swapping can be purchased for a little as $40-$200 on dark marketplaces. (Recorded Future) SIM swapping services can run as high as several thousand dollars depending on the wireless carrier.
Other Vulnerability Vectors
It is difficult to list all of the possible cyber related risks in the wild today. The line between traditional scam and cyber scam can often be blurry and classified as cybercrime if the attacker used any technology to enable their crimes. One category of cyber scam that has grown significantly recently is tech support fraud. (FBI) These scams have more than doubled their losses every year for the past five years, culminating at $347M in losses in 2021. These scams rely on traditional social engineering to trick their victims into thinking the caller is a legitimate employee calling them to “fix” an issue. According to the FBI, “Tech support scammers continue to impersonate well-known tech companies, offering to fix non-existent technology issues or renew fraudulent software or security subscriptions. However, in 2021, the IC3 observed an increase in complaints reporting the impersonation of customer support, which has taken on a variety of forms, such as financial and banking institutions, utility companies, or virtual currency exchanges.”
Online presence is required for all companies regardless of size or scope. Even the most non-technical company should at least have a website or Facebook page to list their services and contact information. Amazon has done a great job of training everyone to always look at how many review stars something has before purchasing. I just had my carpets cleaned and they were extra adamant to tell me to leave a review if it was pleased with their service. Rightly so, I found them by Googling “carpet cleaners” and called the top two for quotes. Maintaining a business listing also requires an account to be created and therefore secured against account takeover and extortion.
Passwords
Unfortunately, weak passwords is the most trite of security concerns, but is still one of the most relevant. Even if a user creates an unguessable complex password, they could still be at risk if their data is leaked online by hackers. According to new research analyzing leaked passwords and how passwords fragments leaked online can be used to crack other passwords by the same user (Kanta, Coray, Coisel, & Scanlon, 2021). For example, you diligently updated your password from “Fluffy10” to “Fluffy11” when prompted or use unique passwords such as “JaxNETFLIX” and “JaxSPOTIFY” across different sites, but the research shows that this data can be used against you if one of your accounts leaks.
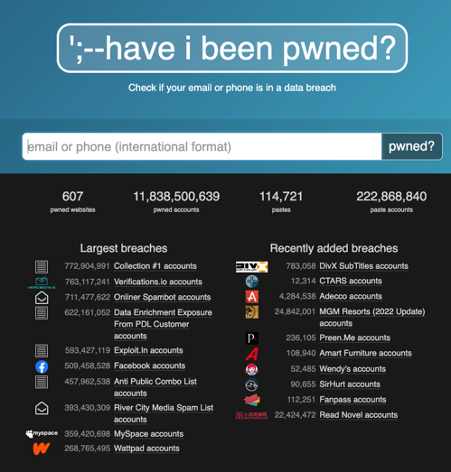
In 2019 researchers discovered that over 82% of Americans had their accounts breached. (Cor & Sood, 2019) The website https://haveibeenpwned.com is a project by the security researcher Troy Hunt and it catalogs data breaches and aggerates their datasets. If you provide your email address, they will alert you if your credentials appear in an online data dump. On the main page, there is a tally for the number of pwned accounts, which is hacker speak for “owned”. As of June 2022, 11.8 billion accounts have been breached. The question is not if but when you will fall victim to a cybercrime. With the proper safeguards in place, exposure and risk can be mitigated. I always recommended that everyone sign up for free alerts at haveibeenpwned?, if any accounts associated with the email address provided show up in a hack or data breach, you will receive an email alert. I have received one of these alerts for Netflix, and it notified me weeks before Netflix did.
The solution
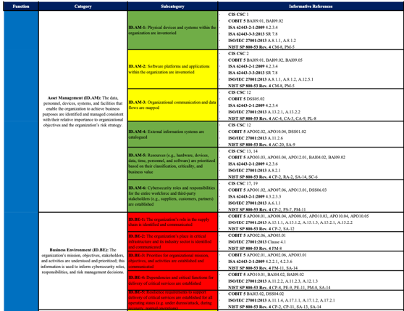
My innovation is a company that is dedicated to the cybersecurity needs of small businesses. Small businesses with less that 25 employees fall into a gap not addressed by consumer or professional cybersecurity productsor services. This small business specific cybersecurity consulting company will offer many services, but the market differentiator will be that we have the small business tailored checklist to assess customers security safeguards against. This checklist will be similar to the NIST CSF based on the security controls recommended by NIST, ISO and COBIT. The CSF controls are industry best practices but are aimed at large enterprises and too complicated to be applied to or by a small business customer. Our tailored checklist will provide adequate security for small business owners without breaking the bank for overkill services targeted at corporations.
Above is an example of from the first of 6 pages that make up the actual NIST CSF checklist. Each section has been color coded to show applicability to small business needs.
Services offered and sales methodology
| Email and account lockdown | Backup configurations and as a service |
| Multifactor Authentication configuration (MFA) | Ransomware prevention and consultation |
| Patching | New computer/device configuration |
| Antivirus setup | Network & Wi-Fi configuration |
| Security auditing | Password Manager configuration |
| Cyber awareness training for employees | Product consulting |
Focus on the basics but leave no stone unturned. Computers are complicated, but cybersecurity doesn’t have to be. I was previously an Electrician’s Mate in the Coast Guard. When troubleshooting electrical issues, it was always an “open, short, or ground” referring to the three types of electrical faults, regardless of how confounding the problem was. Cybersecurity isn’t much different, if you focus on the basics and ensure you cover all of your bases, the risk diminished dramatically.
After the initial consultation and checklist assessment is completed, a formal report will be issued to the customer, similar to what a home inspector delivers to a new home buyer. This report will reference each item on the checklist along with my findings. I will then categorize each discrepancy with a severity score (Green, Amber and Red), and describe what could happen if left uncorrected. This list of recommended actions along with pricing for each service will be part of the official report. In addition to the checklist, all business and finance accounts will be enumerated and audited for password, 2FA and other security measures. Finally, a business transaction assessment will be performed to follow the flow of funds in each transaction to check for risk.
Possible Barriers
My Graduate degree has only included Cybersecurity classes. This entrepreneurship class has taught the most principles not directly related to my major. This section is going to focus on how business problems, planning and marketing apply to this innovation.
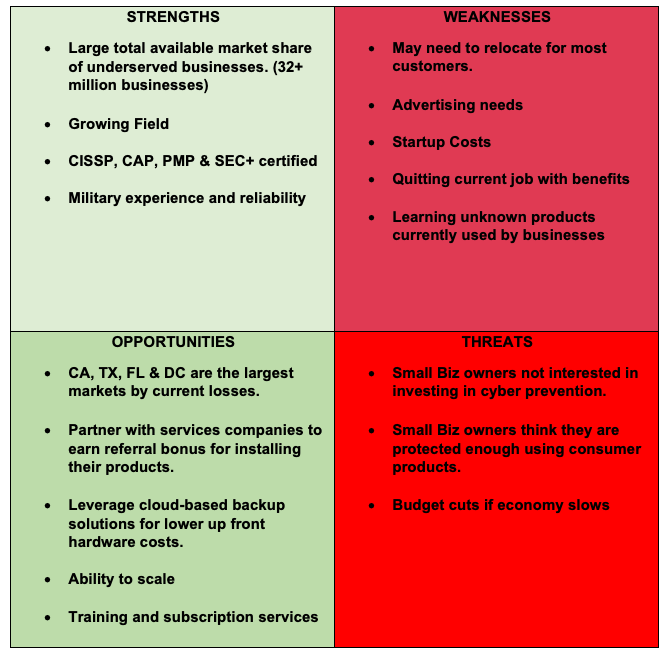
The primary barrier is most likely marketing and advertising. It may be a time-consuming process to become known as the go-to company for small business cybersecurity needs and gain the initial trust of customers and grow the consumer base. This should become less of a problem over time as word-of-mouth spreads and goodwill grows. Online marketing campaigns and targeted Google ads will also help jumpstart the business. Research estimates that Google ads keyword advertising should cost $1-2 per click. (Tri) The marketing budget will have to be flexible at first until we are able to target potential customers more accurately.
There will also be some technical barriers. customers will already be using or invested in an application or system that I am not familiar with. In these cases, I will either need to get up to speed on the topic to provide support which could result in a reduced hourly profit, or I will be unable to support certain systems that I am unfamiliar with. Reality will most likely be a mix of the two. Upon encountering certain products multiple times, I will invest the time into learning how to support it. I will also be cataloging and recommending products that I have had positive experience supporting to customers. This could also lead to a referral-based income stream.
Another barrier could be pricing. It will require a lot of research and modeling to determine how to price complex services. We will also consider subscription-based services, that provide quarterly assessments and priority response in the event of an incident, similar to having a lawyer on retainer.
Additionally, as a small business proprietor, I would be responsible to pay for a medical plan out of pocket for myself and my family. This is a major drawback to leaving a job with good benefits. Another option would be to start this venture as a side business, and then transition out of my existing full-time employment once this venture is successful enough to become my primary source of income. This option is the most secure, but it is also the easiest to get sidetracked and not put in the effort required to nurture a new business into a profitable venture.
SWOT Analysis
As the above SWOT analysis shows, there is a significant opportunity in this marketplace. Aside from the logistics around quitting a regular career and becoming an entrepreneur, most challenges stem from marketing, pricing, and advertising. Based on this discovery, I may need to hire a consultant to ensure I successfully launch the business. Knowing myself, I am very capable of handling technical details and performing complex tasks, however I know that I am not a professional marketer and may require some guidance to get started.
All of the potential treats are similar in that small business owners may not immediately see the value in our services. This is most likely to happen if I am early in addressing market needs. As cybersecurity threats grow and continue to plague businesses as they have over the past five years, the market will naturally begin to look for solutions. Using another cybersecurity product for comparison, antivirus software did not gain in market share until broadband and always on connectivity was the norm. File sharing services proliferated virus propagation to the masses. If cybercrime continues to become more automated, it’s reach will steadily include smaller targets. Research shows that ransomware criminals have set up “call centers” with customer service agents to guide victims through the process of purchasing cryptocurrency, then transferring the payment, and eventually decrypting the files. (Nadir, & Bakhshi, 2018) As long as it continues to be profitable, cybercrime will continue to grow. Due to the distributed global architecture of the internet, criminals are able to remain anonymous and are largely unprosecuted when operating outside of the United States. In the case of most ransomware and cybercrime, once the damage is done, it is often too late for the victim to recover their data or mitigate losses. Proactive prevention and resiliency are the best counter for cybercrime.
An in-depth government study shows that formal education, experience, and industry certifications are all equally weighted in finding qualified employees. I currently hold three industry certifications, including “Certified Information Systems Security Professional (CISSP) which was the most popular certification and required for 5% of the listed jobs. (Marquardson & Elnoshokaty, 2020) This certification is also most often required for top level management positions such as Chief Information Security Officer (CISO). My Military training and experience means I will consistently perform reliable and thorough services for my customers.
The Assessment
If the losses continue to compound as they have for the past five years, small business owners will start looking for solutions to reduce their risk of losing money to these crimes. My goal for this business to be successful will be if the net profit is greater than $250k per year at a 60-hour work week. I plan to reach this figure by averaging over $21k monthly within one year of startup. I chose the $250k figure because, the areas with the highest cyber losses and therefore the most opportunity are also high cost of living areas, and I will need to personally purchase an expensive health insurance policy for my family.
Customer feedback will be an important part of the service sales cycle. In addition to requesting favorable reviews on Google and social media, I will have frequent and open communications with a designated point of contact at each client business. I will inquire as to how their operations are working and if any changes have been made. This will give me an opportunity to market new products and services, especially training opportunities. Feedback from clients will be incorporated into my business. The strength of small businesses is their ability to be incredibly agile. If multiple clients are looking for something other than what I am offering, I can pivot to meet their needs.
If I am unable to reach $250k per year in net profit, I will reanalyze the business to determine if a more drastic pivot is required than being done based on the constant feedback. Hopefully, I will have the opposite problem and need to scale employees to meet business demands. Hiring employees will either reduce my ability to be hands on with clients or I will need to hire an operations manager to handle the day-to-day tasks associated with employing a team. This is where I will have the greatest risk, however. Hiring employees to represent yourself is costly and may not show immediate benefit.
Another gauge of success would be if I could sell the company after 3 years for $3.75 million which would be 15x P/E on $250k in revenue. (The Hartford) If business sale is possible, I could move to another market and restart the business.
Items Needed
Launching this business venture successfully will require significant planning, capital, and expertise that I may need to outsource. First, I plan to register my company as an LLC to limit liability and personal asset exposure. This will require a lawyer and some fees associated with filing the paperwork for the state I’m living in.
Website
A website is estimated to cost me roughly $5000 for a clean design and some Search Engine Optimization (SEO) targeting. I have some experience with web design but would prefer to maintain a website rather than create one from scratch. One tactic many modern businesses use is to have a blog accompany your website. I plan to do this and incorporate tips and intelligence gathered from consulting with small businesses to drive more customers to my website organically rather than paying per click using Google Ads. Traffic to the website can also be driven by starting a social media presence on Twitter and Pinterest using my comments to drive traffic to my website.
Advertising
As previously mentioned, advertising is one of my weaknesses and I could benefit from an analysis on how to best reach potential customers. Assuming that Google Ads will be the primary driver of business, I will need an estimated initial monthly ad budget of $1000 per month for the first 12 months. Once business picks up, I can reduce the amount of advertising I do. I think I could also greatly benefit from attending some local business owners meet ups. It would be a great way to network with potential customers. For these events, I will need to have my elevator and 5-minute pitch perfected as well as have literature and business cards available to hand out. This would also be a good way to find a professional advertising agency to represent me.
Location
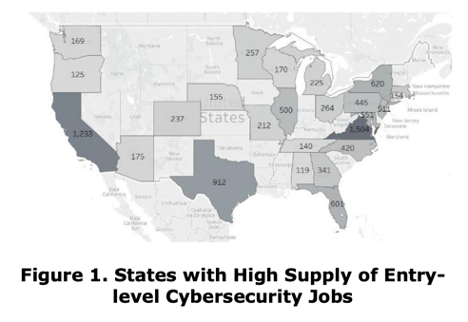
Data shows that staggering amounts of money is being lost due to these scams, specifically in CA, FL, TX, and NY. One of these locations should be the headquarters for the business. A secondary analysis confirms that these states had the most cybersecurity jobs as well, indicating a correlation between cybercrime and cybersecurity demand. (Marquardson & Elnoshokaty, 2020)
This research added Virginia to the list of high demand areas for cyber security. This must be because of the high concentration of government jobs and contractors concentrated in the Northern Virginia area. It is unclear still if the high demand for cybersecurity jobs in the area would mean it would be a good place to launch a small business catering to small business cybersecurity.
The Bottom Line
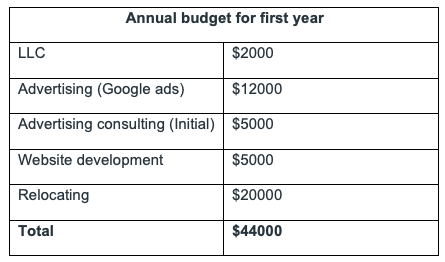
I will need approximately $44,000 dollars plus living expenses to safely start this company if relocation is required. I am about to relocate with the Coast Guard at the end of the year and may end up in a local with a high demand for cybersecurity. The living expenses required to leave my full-time job would vary based on location but is my primary reasoning for transitioning over time from active duty to entrepreneur instead of quitting/retiring then starting up a business. My options are to either take out a small business loan, start saving or try to incrementally build my business while employed otherwise. With interest rates rising, I would like to avoid borrowing money to start this venture.
The Next Steps
Many things need to happen next before launching my company. To keep myself organized I will create a work breakdown structure, which is essentially a project managers to-do list that includes subitems. Most of the items below have already been thoroughly discussed in the previous sections. I have determined through my research that this is a venture that I intend to pursue. I believe the best way to make it work for me is to start small while I finish the last six years of my Coast Guard career and time my transition over to full time business owner with my retirement from active duty.
Work Breakdown Structure
- Create savings account for startup costs
- Research potential markets
- Determine next Coast Guard duty station
- Perform market research for:
- Direct Competition
- Rates for services
- Cost of living expenses
- Perform market research for:
- Find and join an entrepreneur or small business owners’ group
- Network, perform more market research.
- Determine need for advertising agency
- Fine tune services offered based on market research
- Set pricing for website and marketing materials
- Register business as LLC
- Determine business name
- Create EIN for taxes
- Create business bank account
- Create marketing materials
- Business cards
- Create brochure of services
- Create website
- Start blogging
- Have 10 articles prewritten before website launch
- Register Social media accounts
- Register domain name
- Setup business Email and accounts
- Launch website
- Start blogging
- Purchase advertising
- Google Ads
- Local ads ie. Coffee News
- Get clients!!!
- Look for partnerships and referral business opportunities
- Reevaluate business
- Pivot products and services as needed
References
Advocacy Releases 2021 Small Business Profiles for the States. SBA’s Office of Advocacy, https://advocacy.sba.gov/2021/08/31/advocacy-releases-2021-small-business-profiles-for-the-states.
Buo, Shadrack Awah. An application of cyberpsychology in business email compromise. arXiv preprint arXiv:2011.11112(2020).
Kanta, A., Coray, S., Coisel, I., & Scanlon, M. (2021). How viable is password cracking in digital forensic investigation? Analyzing the guessability of over 3.9 billion real-world accounts. Forensic Science International: Digital Investigation, 37, 301186.
Cidon, Asaf, et al. High precision detection of business email compromise. 28th USENIX Security Symposium (USENIX Security 19). 2019.
Cor, K., & Sood, G. (2019). Pwned: How Often Are Americans’ Online Accounts Breached?. arXiv preprint arXiv:1808.01883
Culafi, Alexander. FBI IC3 Report’s Ransomware Numbers Are Low, Experts Say. SearchSecurity, 18 Mar. 2021, www.techtarget.com/searchsecurity/news/252498133/FBI-IC3-reports-ransomware-numbers-are-low-experts-say.
Cybersecurity for Small Businesses. Federal Communications Commission, 30 Mar. 2022, www.fcc.gov/communications-business-opportunities/cybersecurity-small-businesses.
Greenberg, A. (2018). The untold story of NotPetya, the most devastating cyberattack in history. Wired, August, 22.
FBI Internet Crime Report 2021. Internet Crime Complaint Center (IC3), www.ic3.gov/Media/PDF/AnnualReport/2021_IC3Report.pdf. Accessed 23 May 2022.
Determining Your Business’s Market Value. (n.d.). The Hartford. Retrieved June 20, 2022, from https://www.thehartford.com/business-insurance/strategy/selling-a-business/determining-market-value
How Ransomware Works. (n.d.). [Illustration]. https://www.kratikal.com/blog/wp-content/uploads/2021/03/How-Ransomware-Works-1.jpg
Hunt, T. (2022.). ’;–have i been pwned? Have i Been Pwned? https://haveibeenpwned.com
INSIKT GROUP. (2021, August 25). The Business of Fraud: SIM Swapping. Recorded Future. Retrieved June 18, 2022, from https://www.recordedfuture.com/business-fraud-sim-swapping
Marquardson, J., & Elnoshokaty, A. (2020). Skills, Certifications, or Degrees: What Companies Demand for Entry-Level Cybersecurity Jobs. Information Systems Education Journal, 18(1), 22-28.
Nadir, I., & Bakhshi, T. (2018, March). Contemporary cybercrime: A taxonomy of ransomware threats & mitigation techniques. In 2018 International Conference on Computing, Mathematics and Engineering Technologies (iCoMET) (pp. 1-7). IEEE.
Russo, T. SIMulated Trust: How Malicious Actors Take Advantage of Cellular Carriers to Perform SIM Swapping Attacks.
Security National Bank. (2021, April 21). Could a Thief Steal Your Phone Number? How SIM Swap Scams Happen: Blue Compass, Des Moines, Iowa, Www.Bluecompass.Com. Retrieved June 18, 2022, from https://www.snbonline.com/about/news/how-to-prevent-sim-swap-fraud
Stay Safe from Cybersecurity Threats. Small Business Administration, www.sba.gov/business-guide/manage-your-business/stay-safe-cybersecurity-threats.
Reflection Letter
Dear Director of the Advanced Technology Center,
I recently completed a research project for the class Entrepreneurship in Cybersecurity. The class taught many business principles and my project was to write a research paper discussing how I could apply these principles to creating a cybersecurity innovation. I discovered through previous cybersecurity experience those small businesses are a largely underserved sector of the market. I believe this is because large companies have a much larger budget to apply to hiring pricy cyber consulting firms, but that doesn’t mean there isn’t money in the small business sector.
I have learned through my research that there is a market gap for services that apply national cybersecurity standards and best practices to small businesses. The number that stood out to me the most was that the Small Business Administration estimates that there are over 32 million small businesses nationwide. Modern business norms indicate that cybersecurity is a growing field and required for almost every business. If anyone would like to create a similar venture and narrow their focus further, the states that had the most cybercrime measured in dollars lost and should therefore have the greatest need for cyber professionals are California, Florida, New York, and Texas.
In retrospect I would have been able to narrow my focus and create a more detailed plan if I wasn’t in the military and could actually consider relocating to one of these hot spot locations. If I had a location selected, I could have done more in-depth market research and determined my pricing and services offered. Instead, I left that part to do under the “Next Steps” section. I also believe the best way to conduct market demand research is to actively interact with potential customers. Once I determine the location I want to pursue, my top priority will be to network and discuss demand with actual business owners.
Sincerely,
Michael Figliotti