Week 1 – Journal Entry
NICE Workforce Framework Review
Posted on January 14, 2024
Of the various cybersecurity career paths in the NICE framework, I am most drawn to hands-on technical roles like Cyber Defense Analysis and Cyber Defense Infrastructure Support. With my passion for protecting systems from cyber threats, Cyber Defense Analysis appeals to me because I would get to study adversaries, monitor networks, and identify attacks. I also find appeal in Cyber Defense Infrastructure Support since I am interested in building and optimizing secure IT systems and devices like firewalls and servers. While management roles like Cybersecurity Program and Project Management are important, they focus less on the technical work I hope to do day-to-day. I am eager to leverage my skills in research, infrastructure design, and technology optimization to secure organizations from cyber risks through technical cybersecurity roles.
Week 2 – Journal Entry
Principles of Science Related to Cybersecurity
Posted on January 21, 2024
The principles of science such, as relativism, objectivity, parsimony, empiricism, ethical neutrality and determinism offer a framework for examining cybersecurity from a social science perspective. Relativism highlights that various societal systems are interconnected; so changes in one system – like technology – can impact other systems like education, healthcare, and criminal justice. To ensure accurate and credible threat assessments, and maintain public trust, objectivity and ethical neutrality must to be referred to, as they emphasize the importance to study cybersecurity topics in an unbiased and factual manner. Parsimony suggests keeping explanations as simple as possible; this can be explained in cybersecurity, by theories that are developed – like the self-control theory in cybercrime – must be straightforward and testable, even though human behavior is complex and often influenced by multiple factors. Empiricism means relying on observable evidence from research rather than opinions or hunches. Determinism recognizes that human behaviors have causes, even if not completely predetermined. All these principles serve as foundation for developing understanding of the dynamics, and behaviors surrounding cybersecurity.
Week 3 – Journal Entry
Information on Privacy Rights Website (https://privacyrights.org)
Posted on January 28, 2024
The Privacy Rights website is a resource for researchers looking to gain insights from data breaches. By examining the types, sources ,and causes of breaches over time, cybersecurity professionals and researchers can identify trends and patterns to determine which industries, companies or technologies are most vulnerable. Also, they can assess the effect and impacts of breaches by checking the number of people affected thereby, revealing which breach types have the most impact on individuals. Additionally, researchers can evaluate the types of information that are at the highest risk by examining what kind of data was exposed; whether it is financial, medical or personal in nature. This will will help in determining where and what resources should be put in place to stem the threats. Apart from this, information contained on the website give an opportunity to study companies’ reactions towards their own incidences like notifying clients and monitoring credit thus getting a clear overview on how they handle cyber issues around. To sum it up, the collection of breach data, by Privacy Rights enables analysis with the goal of improving data security and preventing breaches.
Week 4 – Journal Entry
Maslow’s Hierarchy of Needs Related to Technology
Posted on January 28, 2024
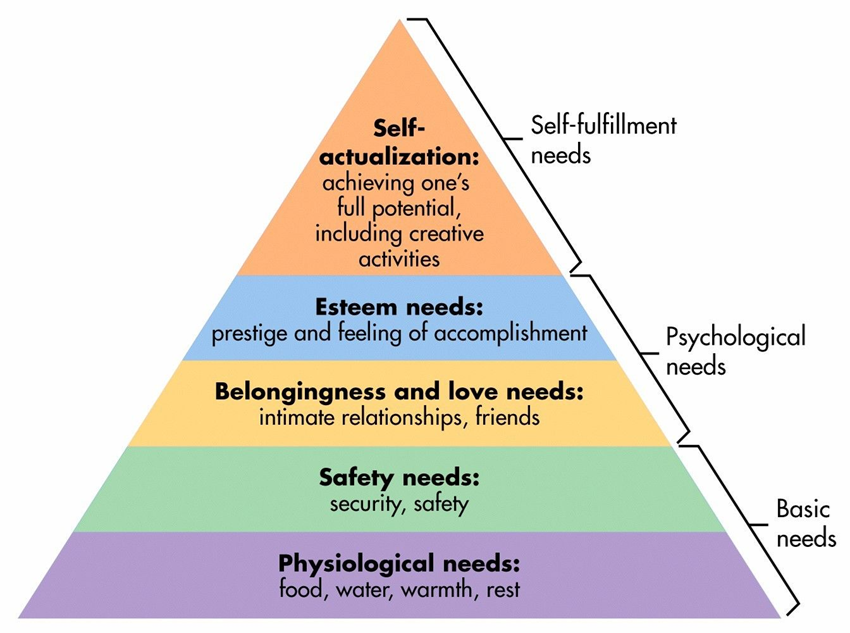
According to Maslow’s hierarchy represented by the figure above, physiological needs like food, water, shelter, and sleep are the most basic needs that must be met first. Access to technology has almost become like a basic physiological need. I feel anxious or irritable when I lose access to my phone or the internet – it’s like a vital resource being taken away. For example, I rely on my phone’s alarm to wake up in the morning and check social media while eating breakfast; losing technology access makes me feel uneasy and disrupts my daily routine.
After physiological needs are met, Maslow says safety needs become important, and cybersecurity meets this need by providing safety technology devices and users. I feel unsafe when my devices get hacked or infected with viruses. It’s like my personal space has been violated; I take precautions like using antivirus software and strong passwords to fulfill this need for safety in my digital activities.
According to Maslow, after safety comes the need for belongingness. For many people, including myself, social media provides a sense of community and belonging through interacting with friends on platforms like Facebook and Instagram where receiving likes and comments makes feel connected. The online presence fulfills my need to belong to a community.
Esteem needs come next on Maslow’s hierarchy. Staying with my example of social media, they can have both positive and negative impacts on self-esteem. I feel good when I get a lot of likes on a post, but get down on myself when I compare my life to others’. Social media experiences definitely influence my self-worth.
Finally, self-actualization is the highest need according to Maslow. I believe that technology tools give opportunities for self-fulfillment by enabling people to create art, write, and share ideas online. On a personal level, they allow me to reach my full potential. The digital world offers me chances to grow that may not exist offline.
Maslow’s hierarchy is interesting in explaining how technology meets human psychological needs, from basic survival to self-fulfillment; my digital experiences align closely with the different levels he proposed. Technology has become intertwined with fulfilling my most basic needs all the way up to achieving my highest potential as a person.
Week 5 – Journal Entry
Individual Motives for Cyber Offending
Posted on February 11, 2024
Considering factors such as prevalence, potential societal damage, and alignment with psychological theories, I ranked the individual motives for cyber offending from the one that make the most sense to me to the one that make the least sense.
- For Money – This is the most straightforward and understandable motive. The hackers who are after money are drawn to the huge potential funds that the digital world offers them. The ease at which hacking skills may be monetized through various methods like stealing of financial information to ransomware is the reason behind many of these hackers wanting to be a part of the cyber criminal world. In the article about how cybercriminals spend their money, it is clear to see how large sums of money may be made by hackers and how many different ways they spend their current. It further supports how hackers are mainly motivated by financial gain, as many hackers say they are doing it for the money.
- Political – Hacktivism, or hacking for political reasons, is ranked highly because it often stems from a desire to effect change, highlight injustices, or expose wrongdoing. Through the article about the new generation of hacktivist joining the wave, we spot some of the motivations and hints on the political promise of cybercrime, often rooted in a sense of justice or a desire to influence political outcomes.
- Revenge – Revenge is an understandable motive because it is hard not to get someone back if you are wronged by them or if you feel that you were wronged. The Wales Online article about revenge porn victims explains the deep personal nature and using cybercrime as a method of exacting your personal vengeance, which while it is illegal and morally wrong is something most humans probably want to do when they are hurt of betrayed by someone.
- Recognition – The want and the desire to prove yourself within a community can lead to individuals coming into hacking. This is common in environments where technical skill is looked at as being meaningful or highly ingenuitive. An example of this can be seen in the scenario given in the reading of the article on an individual who DDoS’d a political candidate’s website with the goal of being acknowledged as a hacker.
- Multiple Reasons – Hackers’ reasons for engaging in cybercrime are often unclear and contradicting. The complexity and multiplicity of motivations — including financial, psychological, and intellectual factors—found in many of these stories make them difficult to accurately place in a linear narrative. The diverse, sometimes almost contradictory motivations for these attacks fit poorly into neat categories.
- Boredom – While boredom is a less compelling motive, it’s understandable how individuals with technical skills might turn to hacking as a form of entertainment or challenge when under-stimulated. The article titled “Cyberbullying and Online Sexual Grooming of Children ‘on the Increase’” discusses how minors, particularly, are increasingly engaging in cyber crimes due to boredom and a lack of supervision.
- Entertainment – Ranked as the least sensible, hacking purely for entertainment, as seen in the case of the LinkedIn scraping, suggests a disconnection from the understanding of the consequences of one’s actions on others. While it might provide temporary amusement, the impact on victims and the legal repercussions make it a less justifiable motive.
Because some motives are more grave and some involve few more victims than others, my ranking takes into account the spectrum of complexity that characterizes human motivations, and consequent offending.
Week 6 – Journal Entry
Fake Websites vs Real Websites
Posted on February 18, 2024
It’s crucial to identify fake websites and differentiate them from the actual ones in an attempt to prevent from being scammed, phished or fed with misinformation. Bellow are three bogus websites compare to three real websites, and the characteristics which generally separate genuine sites from bogus ones.
Fake Websites
- Fake PayPal Site: Fake versions of PayPal use slightly altered URLs like “Paypa1.com” or “Paypal-secure.com.” These sites mimic the real PayPal to trick users into entering their login credentials or financial information.
- Fake DMV Site: Scammers create counterfeit DMV sites to collect personal information or payment for services that are either free or not provided by the DMV at all. They use URLs that are misspelled or use a misleading domain extension (http://www.dmv.virginia.xyz/).
- Fake USPS Site: Similar to the DMV, fake USPS sites aim to steal personal and financial information by offering to track packages or update address information, using URLs that closely look like the legitimate USPS website but with minor alterations (http://usps.net/go/TrackConfirmAction_input).
Real Websites
- Real PayPal Site: The legitimate PayPal website uses a secure HTTPS connection, has a clean and professional design, and its URL is correctly spelled as “https://www.paypal.com/.” It also provides extensive security information and support for users.
- Real DMV Site: The official DMV site have government-endorsed URL, often ending in “.gov,” and feature secure connections with clear contact information and services listed (https://www.dmv.virginia.gov/online-services). It does not ask for unnecessary personal information through insecure means.
- Real USPS Site: The genuine USPS site uses “https://www.usps.com/” with a secure HTTPS connection. It offers a coherent layout, accurate information about services, and secure forms for any personal or financial information required.
Characteristics of Fake Websites
- Misspelled URLs: A common tactic is slightly altering a well-known URL, such as using “paypa1.com” instead of “paypal.com”.
- Too Good to Be True Offers: Deals that seem incredibly favorable without any catch are often bait to lure people.
- Lack of Secure Connection: While not always the case, many fake sites may not use HTTPS encryption, indicated by the absence of a padlock icon in the address bar. However, some fake sites may still use HTTPS.
- Poor Design and Grammar: Fake websites often have spelling and grammatical errors, low-quality images, and an unprofessional look.
Week 7 – Journal Entry
Human-centered Cybersecurity Framework Through Memes
Posted on February 25, 2024
- 1 – Computer User Icon (https://commons.wikimedia.org/wiki/File:Computer_user_icon.svg)

Meme: “Me, after clicking ‘Forgot Password’ for the 10th time today.”
The individual’s mind: “Yet, I thought it was so easy to remember!”
Explanation: The meme deals with the difficulties and frustration that people feel as they wrestle with password administration, a fundamental principle in cybersecurity. It shows how it is important to make it simple for people to manage their authentication while considering the fact that people limited memory. Solutions include things like digitally reading your fingerprints or having one sign-on. All these ideas are part of cybersecurity that pays attention to what regular people need while they are trying to keep themselves and their information safe.
- 2 – Pomeranian Working on an iPad (https://unsplash.com/photos/gySMaocSdqs)

Meme: “When your security question is ‘Who’s a good boy?'”
The individual’s mind: “This can never be forgotten!”
Explanation: This meme humorously imagines a world where pets are part of our digital security practices. Playing on the notion of making security relatable and personal to the user—a key principle of human-centered cybersecurity—security measures can become more engaging and intuitive by utilizing recognizable and familiar personal information, which lessens the cognitive load on users.
- 3 – Person in Front of Laptop (https://unsplash.com/photos/mfB1B1s4sMc)

Meme: “That moment you realize ‘password123’ might not be the cybersecurity strategy you thought it was.”
The individual’s mind: “I would bet that this password was long enough!”
Explanation: This meme plays on the common yet risky practice of using simple, easily guessable passwords. It emphasizes the need for online security education and solutions that encourage and enforce secure passwords without overburdening users. The human-focused approach to online safety holds that it must appeal to the public’s design preferences to succeed and be adopted. Security measures should be intuitive, engaging, and minimize the burden on the user.
Each of the memes use humor to display the human element in cybersecurity. They advocate designing cybersecurity centered around ease of use, intuitiveness, and minimizing user burden – core tenets of the human-centered approach, as these memes remind us that cybersecurity ultimately serves human users and must account for their capabilities and limitations.
Week 8 – Journal Entry 8
The Portrayal of Hacking in Media
Posted on March 3, 2024
The portrayal of hacking in the media affects people’s opinion of hacking. Though the media portrays hackers in a very glamorous and positive way, hacking actually affects our lives in many negative ways, so I believe the media should take more action to inform the public about these detrimental effects.
In my opinion, one positive aspect is that some of the movies incorporates authentic cybersecurity terminology. I liked how actors use real cybersecurity terms when they talk or face a cyberattack. By this they show the audience or teach the audience what those technical jargons are and what some of the terms mean. The ways hackers go through the thought process can also be interesting, as there are numerous movies that show hackers analyzing vulnerabilities, exploiting weaknesses, or devising creative solutions to help viewers understand how much there is to the cybersecurity world. The audience can see what takes place in the coding and the security. These portrayals show that cybersecurity experts are strategic thinkers; they know well about the nuances of digital security rather than just being keyboard warriors.
However, the media often falls into the trap of dramatization and glamorization. Hollywood loves to depict hackers as mysterious geniuses, clad in hoodies, typing at lightning speed, and breaking into systems with ease. It is entertaining, but really not what is happening in the field. I think that this is made just for convenience of movies. Cybersecurity incident is a laborious work which need teamwork, analysis, and protocol. Movies perpetuate the misunderstanding that cybersecurity specialist can solve anything by just a snap on the keyboard.
Misinformation is another big issue. Movies sometimes present exaggerated situations or unrealistic scenarios. For instance, hacking into a highly secure government system in seconds may make for thrilling cinema, but it misleads viewers about the actual challenges faced by cybersecurity experts.
Media has pros and cons for good cybersecurity coverage. The fiction part of media can introduce the public to the cyber field but the public must view it with discerning eye. By doing this they are able to know the real facts about cyber and make the internet a safer place and also will give some respect to all those cyber professionals in the real world.
Week 10 – Journal Entry 9
Social Media and Cybersecurity
Posted on March 17, 2024
I scored 1/9 on the Social Media Disorder scale test. I got such a low score maybe because I am no longer an adolescent. Social media does not have a any impact on my life. I do not accept invitation from people that I do not know. I can even remember that day when one of my friends asked me: “why almost all of your Facebook friends are your family members?” I was very cautious about social media.
I think that the items in the Social Media Disorder Scale a meant to assess the relationship people have with social media and identify the potential addictive behaviors related to its use. I can notice that the items in the scale focus on aspects like the amount of time spent on social media, emotional responses to social media interactions, impact on daily life and relationships, and feelings of distress when unable to access social media. I believe that the different patterns found across the world are influenced by difference in cultures, societies, technologies, and individual places. For example, some cultures may place a higher value on face-to-face interactions, leading to less reliance on social media for communication – I am from such a society. The difference in the levels of internet access and smartphone usage can also contribute to differences in social media behavior globally.
Week 11 – Journal Entry 10
Social Cybersecurity in the National Security and Information Warfare
Posted on March 24, 2024
The article entitled “Social Cybersecurity: An Emerging National Security Requirement” by Lt. Col. David M. Beskow, and Kathleen M. Carley, PhD provides e concerning view at the emerging threats posed by social cybersecurity – the use of technology and cyber tools to manipulate human behavior, beliefs, and societies.
The rise of decentralized information flows on social media combined with the remote ability to influence societies through cyber means has enabled state and non-state actors to create powerful new vectors for shaping narratives and sowing discord by waging “information blitzkriegs” against target populations. Russia is highlighted as a pioneer in waging information warfare campaigns, aiming to weaken social cohesion, trust in institutions, and commitment to democratic values from within other nations by injecting distortions, conspiracy theories, and divisive content into their online discourse.
The authors introduce the “BEND” model for classifying different social cyber attack vectors – some target the information itself, while others target the networks spreading that information. Techniques like network bridging, community building, and automated bots/troll armies are used to saturate populations with tailored disinformation. This form of warfare represents a strategic shift, where influencing the “human terrain” may become as important as physical terrain. As societies place greater weight on the cyber information space, defending against these human-centered attacks becomes a national security priority.
Overall, the article has highlighted an alarming landscape where the marketplace of ideas is being deliberately polluted and weaponized by hostile actors. Defending truthful narratives and societal cohesion may require organizational adaptations, new policies enabling cyber activities, and a public educated on these threats.
Week 11 – Journal Entry 11
Cybersecurity Analyst Job Related to Social Behaviors
Posted on March 24, 2024
In the video “What Does a Cybersecurity Analyst Do?” by Nicole Enesse1, the description of the cybersecurity analyst job intertwines with several social themes.
Continuous Learning and Adaptation: The video implicitly talked about continuous learning through the importance of having some certifications. Validity of these certification is maintained with a regular recertification. Given the continually changing threat landscape and the ever-evolving technologies of cybersecurity, the necessity to learn continually may seem quite overwhelming. Nonetheless, it’s no different from the concept of lifelong learning. Cybersecurity professionals must heed knowledge, adapt and acquire new skills constantly to keep up and survive in this digital age – where cyberwarfare has become not just a danger but a reality.
Work location and Social Adaptation: The discussion of job locations—whether remote or in person—touches on social adaptation. The nature of remote work requires a different approach to communication and a high level of self-discipline. This can impact the way people interact socially. At the same time, the need to adapt extends to the cybersecurity field. Threats are continually changing, and cybersecurity analysts are relentless in their efforts to stay current on the most recent attack techniques. Only when they can think both like and unlike the hackers trying to breach their systems can they address new challenges creatively.
STEM in cybersecurity: The author points out the importance of STEM education (Science, Technology, Engineering and Mathematics) in arming individuals with the technical knowledge, critical thinking abilities, and problem-solving skills needed to do well in cybersecurity.
In general, the position of the cybersecurity analyst crosses paths with social dynamics, paying heed to knowledge, communication, cooperation, and adaptability. As guardians of digital safety, analysts traverse not only the technical hurdles they encounter but also the vast, complex landscape of human conduct in the virtual realm.
Week 12 – Journal Entry 12
Analysis of a Data Breach Notification: Intersections of Economic and Social Decision-Making
Posted on March 31, 2024
The document “Sample Data Breach Notification” as its title mentioned, is notification sample from Glasswasherparts.com, informing customers of a data breach involving payment card data due to malware on the platform provider’s servers. An analysis help us display how key economic theories, like rational choice, Marxian, and sciences theories relate to this letter.
The rationale choice theory can be seen in the response to the GlassWasherParts.com breach. Both the company and the customers conducted themselves in ways that sought to minimize their losses and, using economically-literate terminology, to “rationalize” their situation in such a way that post-facto rationality yields minimal impact. The Marxian lens of analysis, through which this document views the GlassWasherParts.com data breach, does a brilliant job of tying the random accident to the larger social picture in one breath with the economic construct.
Looking through a social sciences perspective, the breach can be seen through the lens of social contract theory, where the implicit agreement between the company and its customers on data protection was broken, necessitating a reassessment of mutual trust and obligations. The symbolic interactionist approach elucidates the post-violation communication intricacies, through the communication via the notification letter, functioning as a symbol of trust/responsibility, shaping consumer perceptions and behaviors vis-à-vis the violation.
These theories give a perspective on the ways in which cyber incidents involve economic and social decision-making. They underline the intricate relationship between economic decisions, societal norms, power dynamics, and individual actions in the digital domain.
Week 12 – Journal Entry 13
The Economics of Bug Bounty Policies in Cybersecurity
Posted on March 31, 2024
“Hacking for good: Leveraging HackerOne data to develop an economic model of Bug Bounties,” a Journal of Cybersecurity article, gives a realistic look into the efficacy and financial consequences of bug bounty initiatives. It uses an exclusive dataset to review the effectiveness of these programs in the cybersecurity domain, where White Hat or ethical hackers are rewarded generously for identifying and effectively reporting justifiable vulnerabilities in organizations’ software.
The research suggests that the investigators show little regard for cost sensitivity, indicating that their motives stem from something other than financial gain. It may be deduced from this that even businesses with little financial resources have the potential to enjoy financial benefits via bug bounty programs. The analysis also shows that the rate of submission of vulnerability reports does not vary significantly by company size or emplacement: this is an indication that there is an universal gain of having a bug bounty programs. It is notable that there were fewer reports in key sectors like finance, retail and healthcare, although this was not statistically significant. The report observes that as bug bounty programs age, the number of reports tends to decrease. This may be a consequence of the gradual drop of vulnerabilities that are simple to detect over time. It is impossible to exaggerate the value of the bug bounty program inside the ecosystem of cybersecurity. This is a cost-effective method which companies can utilize to boost their security posture.
The article shows how bug bounty programs can be advantageous to corporations, even if they are resource-constrained. All businesses – no matter their size – can drive meaningful cybersecurity improvements by running these types of incentive programs. The universal applicability of bug bounties is highlighted by the consistent submission rates across company sizes and locations. While the number of reports tends to decline as programs mature, likely due to the resolution of evident vulnerabilities over time, bug bounty programs remain a cost-effective strategy for organizations to enhance their cybersecurity posture.
Week 13 – Journal Entry 14
Five Serious Internet Offenses: Andriy Slynchuk’s Insight into Common Yet Illegal Online Activities
Posted on April 07, 2024
Andriy Slynchuk, in his blog “11 Illegal Things You Unknowingly Do on the Internet,” has highlighted eleven (11) potentially illegal actions that internet users might unknowingly engage in. Among these, I consider the following five offenses to be particularly serious:
- Collecting Information About Children: This infraction involves the collection of information regarding children who are less than 13 years old. It can have serious repercussions although it could appear to be harmless. The use of children’s personal information for commercial purposes is not just unethical but also against the law. The protection of their privacy is of the utmost importance, and any offense that violates this confidence is extremely upsetting.
- Using Unofficial Streaming Services: Many people use unofficial streaming platforms to watch movies, TV shows, and sports content for free. On the other hand, these platforms frequently violate copyright laws by disseminating content that has been illegally obtained; this kind of behavior is detrimental to content creators and violates their rights to intellectual property. Due to the fact that this infraction may result in legal consequences, it is a major cause for concern.
- Using Torrent Services: Torrents allow users to access copyrighted material without paying for it. By downloading movies, music, or other content through torrents, individuals contribute to piracy and undermine the hard work of creators. This offense not only violates copyright laws but also harms the entertainment industry.
- Using Copyrighted Images Without Permission: Contrary to popular belief, most images and photos on the internet have owners—photographers, corporations, or other creators. Using copyrighted images without proper authorization constitutes infringement; respect for intellectual property rights is essential, and unauthorized image usage can lead to legal consequences.
- Recording VoIP Calls Without Consent: VoIP (Voice over Internet Protocol) calls are commonly used for communication. Recording such calls without the consent of all parties involved is illegal in many jurisdictions. Violating privacy by secretly recording conversations undermines trust and can result in legal penalties.
The offenses described range from privacy violations to copyright infringement, and they all have real-world implications; it is crucial as good internet users to be aware of what we are doing and to work within legal and ethical guidelines on line.
Reference:
Slynchuk, Andriy. “11 Illegal Things You Unknowingly Do on the Internet.” Clario.co, 1 June 2021, clario.co/blog/illegal-things-you-do-online/. Accessed 6 Apr. 2024.
Week 15 – Journal Entry 15
Thoughts on a Career in Digital Forensics
Posted on April 21, 2024
The professional path of a digital forensics investigator as highlighted in the video, exemplifies the significant intersection that exists between the social sciences and cybersecurity. Davin Teo, the speaker, clarifies that, as opposed to computer science, accounting is his background. But through an opportunity at one of the big accounting firms in Australia, he was able to move into a profession in digital forensics.
What struck me most was not just his career shift but how digital forensics intertwines with various aspects of the social sciences. By definition, digital forensics involves the study of human behavior, particularly in relation to illicit or unethical online behaviors; the psychological and sociological tendencies that motivate people to commit digital crimes—which can include everything from fraud to cyberthreats—must be taken into account by investigators. In his capacity as a digital forensics investigator, Davin is responsible for analyzing digital evidence to discern the psychological and motivational underpinnings that is behind cyber-related incidents. Technical skills like data extraction and analysis as well as social science skills like comprehension of criminal behavior, human psychology, and investigation methods are needed for this profession. When it comes to tackling the human part of cybersecurity, the social sciences are extremely important, as demonstrated by Teo’s professional path. Digital forensics investigators expertise is essential as digital platforms have become ubiquitous, often enabling new forms of criminal activities; a deep comprehension of the interpersonal and technical aspects of these interactions is necessary. The core competency of the social sciences is making the connection between human intents and data trails.
Digital forensics investigators like Teo are able to respond to cyber threats in a more thorough and efficient manner by fusing their technical skills and social science understanding. As seen by Teo’s path, the cybersecurity industry values and demands a broad range of skills, including technical and social scientific knowledge.