About Me
My name is Seraina Dailey. I’m a Cyber security student at ODU. I work full time at Resolute Building Co as head of IT which includes a lot of help desk, data harvesting, creating policy, and managing the digital security of the company. I serve part time in the Army Reserves as an Information Technology Specialist and Signal Support Systems Specialist.
My goals are that I graduate with a bachelors in Cyber Security and keep having adventures through the army, pursue character development, and keep a nice steady office job in the civilian world.
I like the army, outdoor activities, traveling, art, reading, lunches with friends, my dog, and the gym
My Thoughts on cybersecurity and the social sciences
People are why we have cyber security. They want everything connected and easily managed. The intranet of things is a network of every day devices on the network. This futuristic lifestyle though comes with a downfall. it can be hacked. This is why we need Cyber security.

Cyber security works on teaching you correct digital hygiene and making sure you have the right balance of connection with the world, social media, and cyber security. Our digital footprint gets larger the more we share and are connected and this information can be used for social engineering.

Social engineering is how the hackers gather and manipulate the information that you have out in the world. That Facebook post about your new job and position can lead to someone targeting you. The earlier post about looking for puppies could be their leverage.

Hackers use the data you release to find out more data. They can send links about a puppy they have for sale and corrupt your computer that you bring to work. They can infect your computer with any type of Malware.
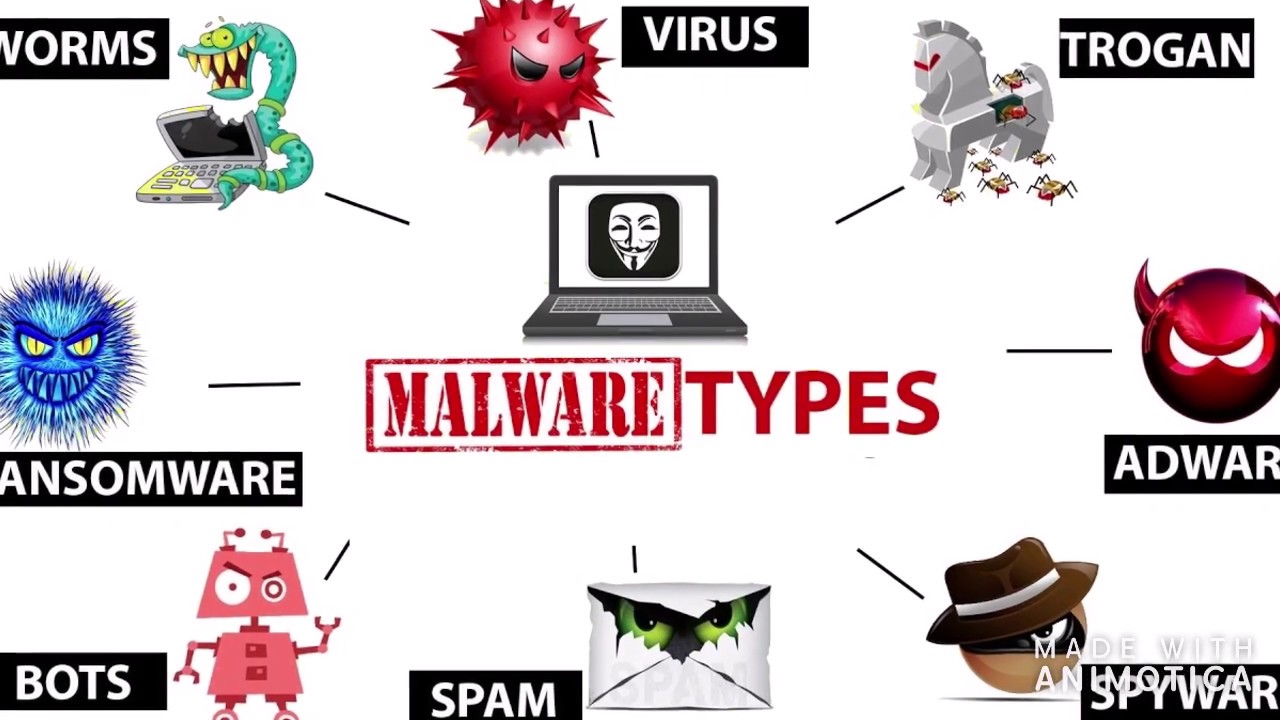
Once you are compromised hackers can create a data breach at your work or spread it to others at your company. They even can take over your identity and use that to compromise other people.
The connection between cyber security and social science is deep. Hackers use it to take advantage of us, and Cyber Security Specialists use it to comprehend, defend, and deter these compromises.