After watching the video, write a journal entry about how you think the media influences our understanding about cybersecurity I appreciate the media such as movies and television shows for bringing the importance of securing our private data to the public view. The unfortunate side effect is that most of the time processes and strategies …
Category: CYSE201S
Feb 25
Week 7 Journal
Explain how your memes relate to Human-centered cybersecurity. woman in white button up shirt holding silver iphone 6 (Ghen Mar Cuaño,2020) When it comes to human-centered cybersecurity, promoting awareness when interacting with the internet is important in preventing common human errors when faced with deception. In this meme, I am depicting the excitement one may …
Feb 19
Week 6 Journal
Spotting Fake Websites Oftentimes when navigating the internet, we are left with only our best judgment to mitigate malicious users from harming our systems and accessing our data unauthorized. One way that malicious users gain access to our systems is through the websites we connect to over the internet. What are some telltale signs that …
Feb 09
Week 5 Journal
Review the articles linked with each individual motive in the presentation page or Slide #4. Rank the motives from 1 to 7 as the motives that you think make the most sense (being 1) to the least sense (being 7). Explain why you rank each motive the way you rank it. Boredom 7 Ranking the …
Feb 04
Week 4 Journal
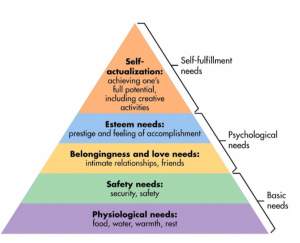
Review Maslow’s Hierarchy of Needs and explain how each level relates to your experiences with technology. Give specific examples of how your digital experiences relate to each level of need. Maslow, A. (n.d.). Hierarchy of Needs. Peakframeworks. https://www.peakframeworks.com/post/maslows-hierarchy Over the years the internet has expanded into fulfilling many human needs. From ordering food, connecting with …
Jan 29
Week 3 Journal
Visit PrivacyRights.org to see the types of publicly available information about data breaches. How might researchers use this information to study breaches? Enter a paragraph in your journal. PrivacyRights.org provides numerous options to receive and share information on privacy and data breaches. The site sorts itself and necessary information into differing sectors of cybersecurity: Personal, Education, Health etc. Those …
Jan 19
Week 2 Journal
Explain how the principles of the Social sciences relate to Cybersecurity. There are numerous parallels between the disciplines of science and Cybersecurity. Cyberspace has offered a new landscape in which humanity conducts business and socialize; all from behind their computer screens. These great advances however require professional strategies to protect its users from cyber threats. …
Jan 12
Week 1 Journal
Review the NICE Workforce Framework. Are there certain areas that you would want to focus your career on? Explain which areas would appeal the most to you and which would appeal the least. When it comes to cybersecurity, I find data collection and analysis appealing. I naturally want to look into law enforcement and other investigative positions. …