Explain how your memes relate to Human-centered cybersecurity.

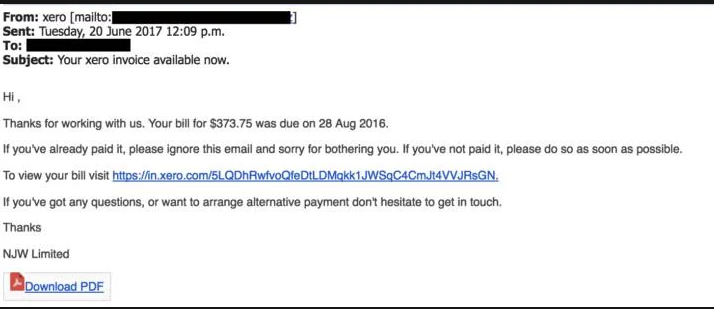
woman in white button up shirt holding silver iphone 6 (Ghen Mar Cuaño,2020)
When it comes to human-centered cybersecurity, promoting awareness when interacting with the internet is important in preventing common human errors when faced with deception. In this meme, I am depicting the excitement one may feel if one truly believed that a Nigerian prince’s scam email asking for money in return for their kingdom was true. It is important to be knowledgeable of these too-good-to-be-true scenarios when online.

person holding silver iphone 6 (Erik Mclean, 2020)
I created this meme to bring attention to how much information we put out onto the internet. Celebrities are commonly known to be stalked online and offline and tend to post their day-to-day lives for the public to see. This behavior can be very dangerous, regardless of public status. For example, posting information about not being home for a while may give someone with poor intentions an opportunity to break into your home while you are gone. It is common for fans to mindlessly engage in stalkerish behaviors towards their favorite celebrities, especially if the information is given freely online.
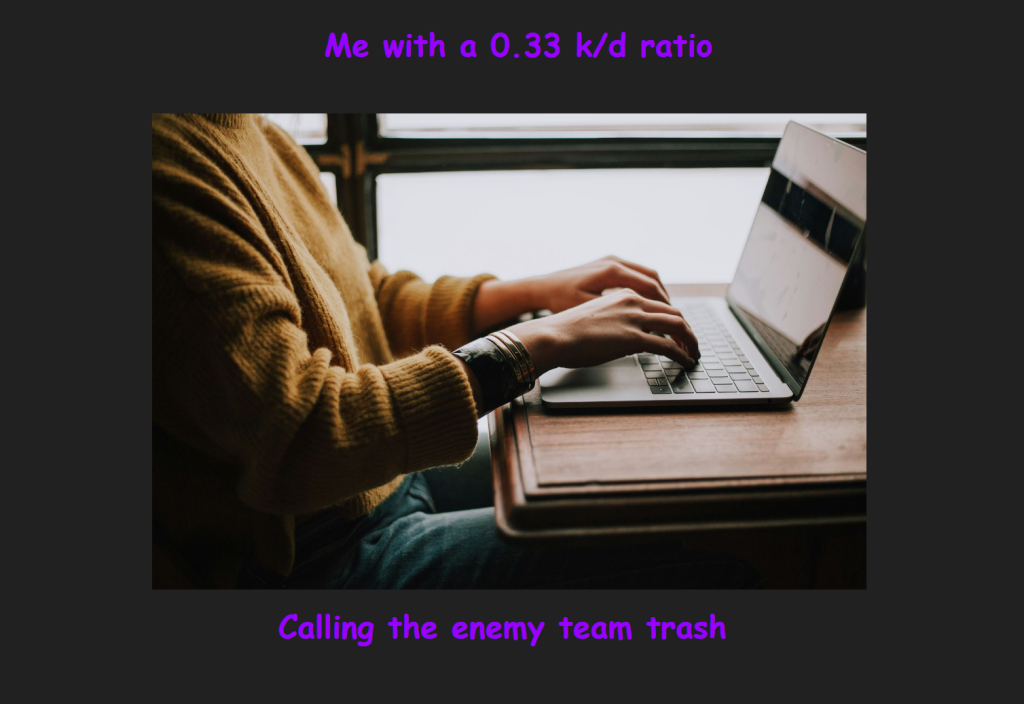
person sitting front of laptop (Christin Hume, 2018)
I created this meme to depict offensive online behaviors. It can be difficult to retain good conduct when in the heat of the moment, like in an intense video game. The internet creates a layer of anonymity that could entice someone to engage in cyber harassment as a way to cope.
citations
Mclean, E. (2020). person holding silver iphone 6. unsplash. Retrieved from https://unsplash.com/photos/person-holding-silver-iphone-6-BXiLSwwvqrY.
Hume, C. (2018). person sitting front of laptop. unsplash. Retrieved from https://unsplash.com/photos/person-sitting-front-of-laptop-mfB1B1s4sMc.
Mar Cuaño, G. (2020). woman in white button up shirt holding silver iphone 6. unsplash. Retrieved from https://unsplash.com/photos/woman-in-white-button-up-shirt-holding-silver-iphone-6-R6dSBkz32B8.