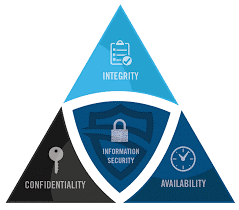
The CIA triad isn’t just an information security model that organizations use to help maintain data secure, but as Josh Fruhlinger states in his article, “…the triad is a way of thinking, planning, and perhaps most importantly, setting priorities” (Fruhlinger, 2020) for an organization to best protect its data. The CIA triad consists of three different concepts that need to be considered and addressed when implementing information security. A reason the CIA triad is so important is that when it comes to creating effective security policies is because the three concepts are interconnected and when one is removed, security vulnerabilities appear (Chai, 2021).
The first concept of the CIA triad is confidentiality which can be described as “only authorized users and processes should be able to access or modify data” (Fruhlinger, 2020). This concept simply means that data should only be seen by those authorized, need-to-know concepts. This helps prevent security vulnerability by attempting to prevent unauthorized users from accessing secured data. Confidentiality can be seen by using a badge to enter a classified area or using two-factor authentication to log on. The second concept of the CIA triad is integrity which can be described as “data should be maintained in a corrective state, and nobody should be able to improperly modify it, either accidentally or maliciously” (Fruhlinger, 2020). This concept simply means that the data should remain as intended and only be modified by authorized users to do so. Integrity can be seen by using Read-Only rules to prevent unauthorized users from altering information accidentally or intentionally. The third concept of the CIA triad is availability which can be described as only “authorized users should be able to access data whenever they need to do so” (Fruhlinger, 2020). Availability can be seen as ATMs for usage after hours or being able to access a network without it crashing.
Authentication and authorization are similar in that they fall under the concept of confidentiality but are different in that they do. Simply, “authentication means confirming your own identity, whereas authorization means being allowed access to the system” (Siddiqui, 2020). One example that illustrates the difference is when you log on to an account and what you are able to do. By logging in and possibly using two-factor authentication, you are authenticating that you are who you say you are and log in. Once you have logged on, you will only be able to do things you have permission to, which would be the authorization. One helps determine who you are and if you are allowed access and the other helps with determining what you can and cannot do once you have been allowed access. Just because you have access to read information doesn’t mean you have permission to edit it.
Resources
Chai, W. (2021, January 29). What is the CIA triad? definition, explanation and examples. WhatIs.com. Retrieved March 14, 2022, from https://whatis.techtarget.com/definition/Confidentiality-integrity-and-availability-CIA#:~:text=Why%20the%20CIA%20triad%20is%20important&text=Confidentiality%2C%20integrity%20and%20availability%20together,of%20security%20policies%20for%20organizations.
Fruhlinger, J. (2020, February 10). The CIA triad: Definition, components and examples. CSO Online. Retrieved March 14, 2022, from https://www.csoonline.com/article/3519908/the-cia-triad-definition-components-and-examples.html
Siddiqui, A. (2019, February 20). Authentication vs authorization. Medium. Retrieved March 14, 2022, from https://medium.datadriveninvestor.com/authentication-vs-authorization-716fea914d55