– CYSE 200T –
In our CYSE 200T course, we dived into the critical relationship between technology and cybersecurity through different hands-on activities and projects. One of the most impactful experiences was a group project focused on analyzing vulnerabilities in SCADA systems, which are vital for managing infrastructure like power grids and water treatment facilities. Throughout the semester, we studied significant cyberattacks, including the Stuxnet worm, and examined the NIST Cybersecurity Framework to understand how organizations can enhance their security measures. We also learned about the CIA Triad (Confidentiality, Integrity, Availability) as a foundational model in cybersecurity. This emphasizes how these principles guide the protection of sensitive information. This learning experience was vital for applying our theoretical knowledge to real-world scenarios and recognizing the importance of safeguarding critical services against cyber threats.
From this course, I developed several key skills and values that align with the traits I identified as essential at the start of the semester, such as critical thinking, teamwork, and ethical responsibility. Engaging in discussions about vulnerabilities and risk management improved my analytical abilities. Collaborating with classmates during group activities enhanced my communication skills, which allows us to present complex ideas effectively. This experience aligns perfectly with my goal of becoming a Cybersecurity Engineer, where I aim to apply these kills to help secure systems and data.

What is the CIA Triad?
The CIA Triad is an information security model that helps organizations keep their data responsible and secure. The CIA Triad has no relation to the Central Intelligence Agency, but it stands for confidentiality, integrity, and availability. These three principles are always at the top of the mind of an information security professional. The CIA has no track of a creator or when it was created because they said it emerged over time as an article of wisdom with security pros.
The CIA Triad is needed to understand the basics of security software, services, and techniques that are being used in the market. Confidentiality is making sure that data is credible and secure. For example, before being able to access any information, a person must have two factor authentication to see any private information. Integrity is making sure that all information is processed and correct, not modified or tampered with. Availability is when data is accessible at any time so other people do not have to be involved in allowing another person to access information. All in all, it is important to have all these three principles in the CIA Triad because if one principle is corrupted, then the whole triad is messed up.
Authentication vs. Authorization
There is a big difference between knowing what Authentication is and what Authorization is. Authentication is when the system determines if a person is who they say they are supposed to be. An example of authentication is using a username and password to login to a website. This will also include biometrics, such as finger scans, eye scans, and more, but also security tokens and cryptographic keys. Authorization determines who has access to the specific data they need to look at. This can relate to confidentiality because it limits the files that are accessible to the creators and admins. An example of authorization is having full house ownership but also being able to grant other people access to it.
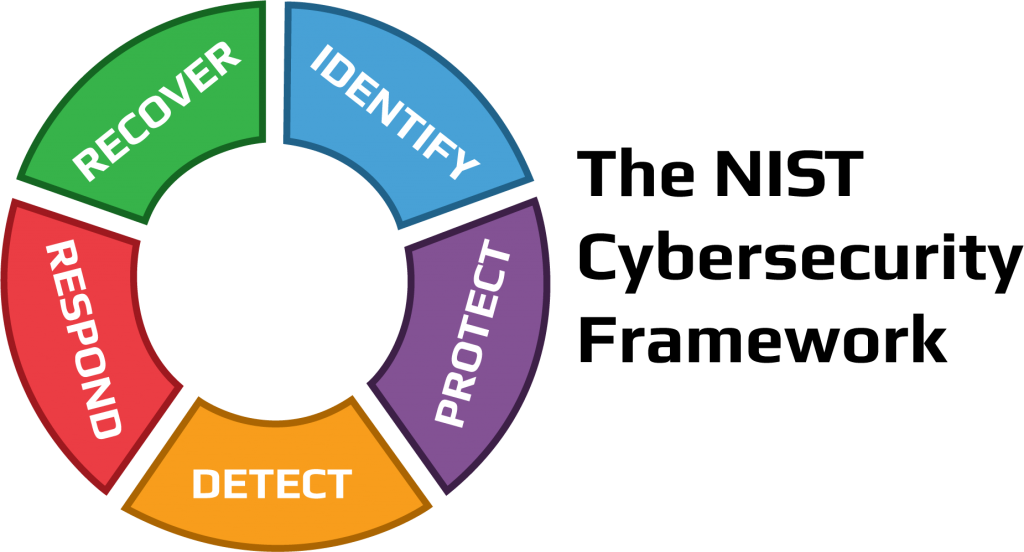
What benefit can organizations gain from the NIST Cybersecurity Framework?
NIST Cybersecurity Framework helps execute processes to detect and identify risks so organizations can be prepared or responsive to attacks. It also helps them learn ways they can be attacked and how they can recover from an attack. Another way that NIST Cybersecurity framework can benefit organizations is that it can help strengthen their cybersecurity programs. This will make the organization stronger and more protected and will also create a more comfortable secure workplace. In a future workplace, this will be very important to keep everything secure and prevention from attacks. NIST will be able to detect, protect, respond, and recover, and knowing everything is online in today’s world, cybersecurity is essential in workplaces now and in the future.
Online Safety
There are many ways to protect your Personal Information, but there are some problems when it comes to the mindset of a human being. There are many scams such as phishing, vishing, link manipulation, and fake websites. These can all be prevented if people can detect it before taking the bait. People have to learn when to look at a link, to see if it is not safe. They also need to not answer calls that seem like a scam or unsafe. Email phishing is very popular in this world to steal information, scammers will send emails to people saying that you have won a certain amount of money or you have ten minutes to redeem this gift card. Never click on any links that are not trusted or answer any calls that could be a scam.
Oversharing personal information over social media is one of the biggest ways that people’s identities are stolen. Having your nickname in your biography is okay, but adding your full government name, email, and phone number is very unsafe. All thefts need is your social security number and they will be able to become you and create credit cards under your name. Cybersecurity will be in everyone’s lives and the business is growing everyday to make sure to protect us from the thefts who steal our Personal Identifiable Information.
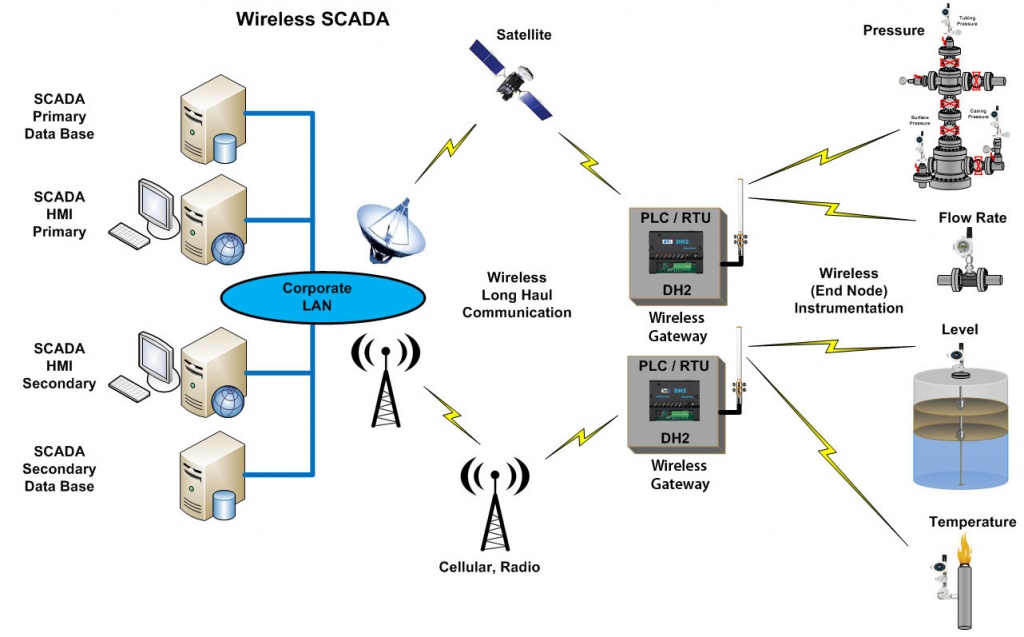
SCADA Systems
There are many vulnerabilities that are associated with critical infrastructure systems within SCADA. SCADA Systems supervise many devices, sensors, and software which opens up more attacks and easier targets. There are many bugs that occur like stack and buffer overflows and information disclosure. This can allow hackers to DoS and steal private information. Cyberattacks that occur could “paralyze” the internal processes which could lead to financial losses but most importantly, the loss of human lives. Even though these attacks can occur on the internet, it still puts risks on humans and threatens their lives. There are two major threats to SCADA which are unauthorized access to software and packet access to network segments that host SCADA devices. Their users suggest that a VPN is a way of protecting these devices. Attacks on these systems have caused major damage to industrial facilities. One of the well-known attacks that have occurred was the Stuxnet worm in 2010 where the computer worm infected computers and spread throughout to find if they are connected to PLCs. There are many ways SCADA systems can improve on their security and they learn from the mistakes they have made in the past.
Mitigation
There are lists of ways that SCADA systems mitigate the risks from the vulnerabilities of critical infrastructure systems. SCADA vendors are working on a specialized industrial VPN and firewall solutions based on TCP/IP to make their security stronger. HMI is a device that humans can interact with the SCADA systems database and sometimes they can catch threats and make changes to mitigate the potential attacks. There is a technique called “honeypots” where it is used to trap, detect, deflect, and defend from unauthorized access to the network. This can help solve the network vulnerabilities that are associated on SCADA systems. Regularly monitoring the users who have authorization to certain SCADA systems reduces inside threats and cyber threats.
How has Cyber Technology Created Opportunities for Workplace Deviance?
Since the technology world has advanced over the decade, the internet is being used for almost everything in businesses and companies. Employees who are not satisfied or are fired, can commit dangerous acts before leaving the workplace such as downloading important files and selling it to other companies for money. Since everything is over the internet, it is harder to catch employees who are being deviant because it is behind the screen. Data breaches can occur and this can be done by an insider such as an unsatisfied employee. There are many more worse forms of workplace deviance and all of this can be done with cyber technology.