Old Dominion University
CYSE 301 Cybersecurity Techniques and Operations
Assignment 3: Sword vs. Shield
Edwin C Wells IV
Task A: Sword – Network Scanning
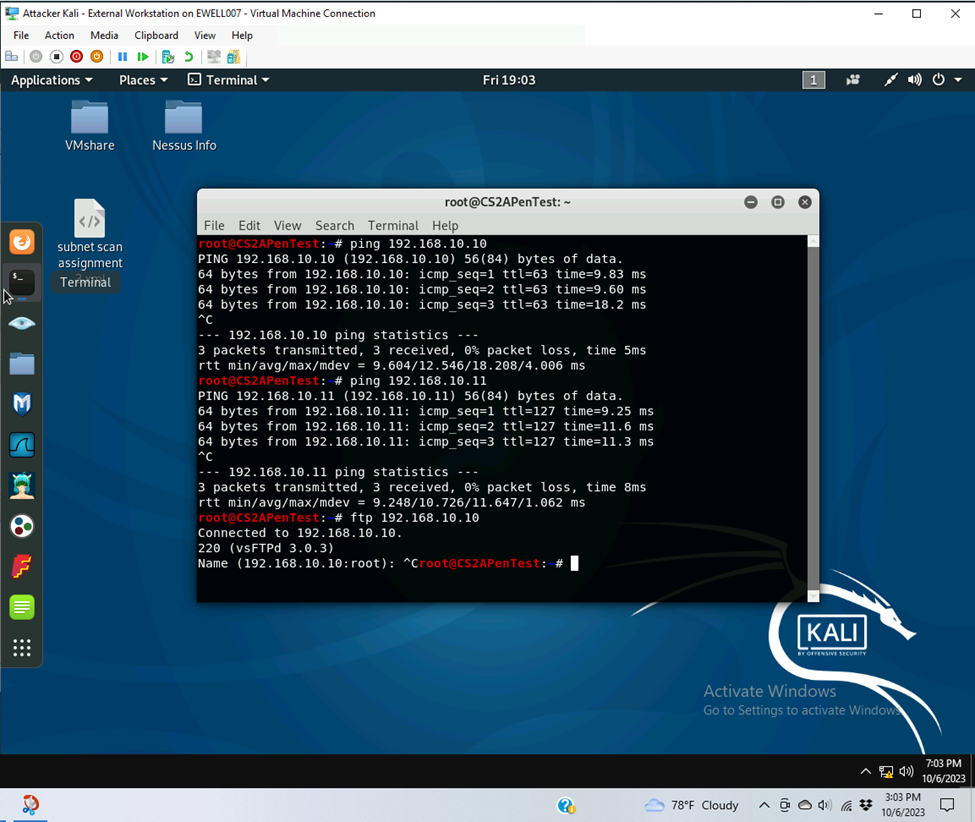
- Use Nmap to profile the basic information about the subnet topology (including open ports information, operation systems, etc.) You need to get the service and backend software information associated with each opening port in each VM.
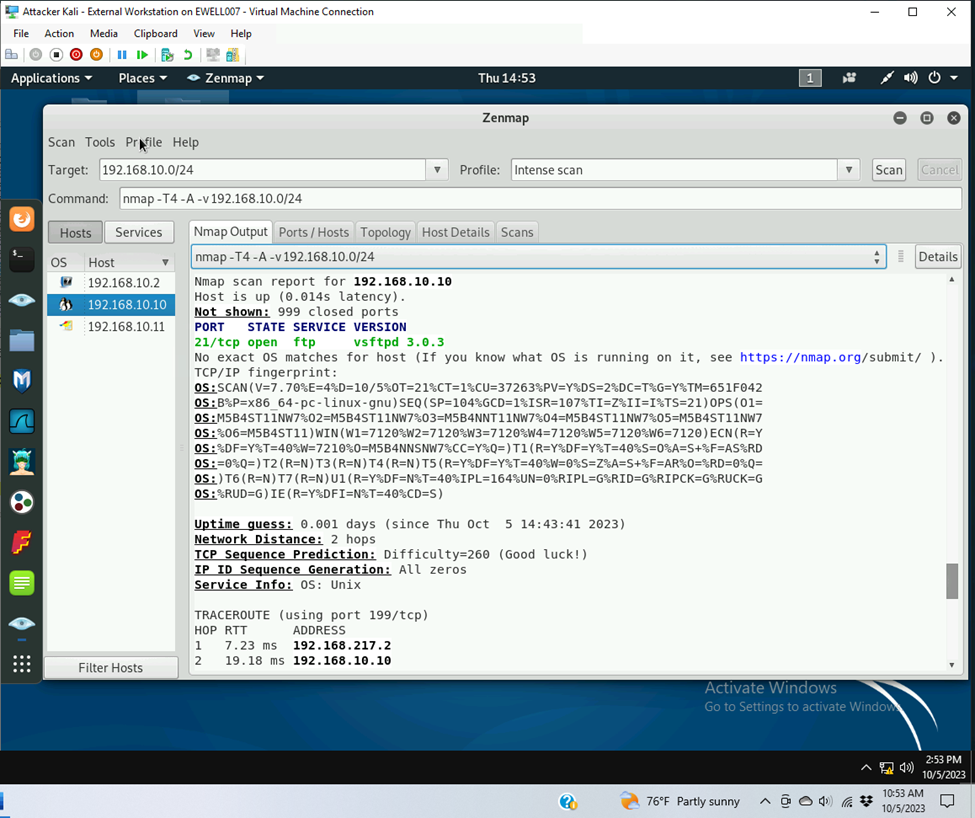
- 192.168.10.10 Ubuntu
- Open Ports
- Port 21
- Service: ftp
- Version: vsftpd 3.0.3
- Service: ftp
- Port 21
- Open Ports
- 192.168.10.10 Ubuntu
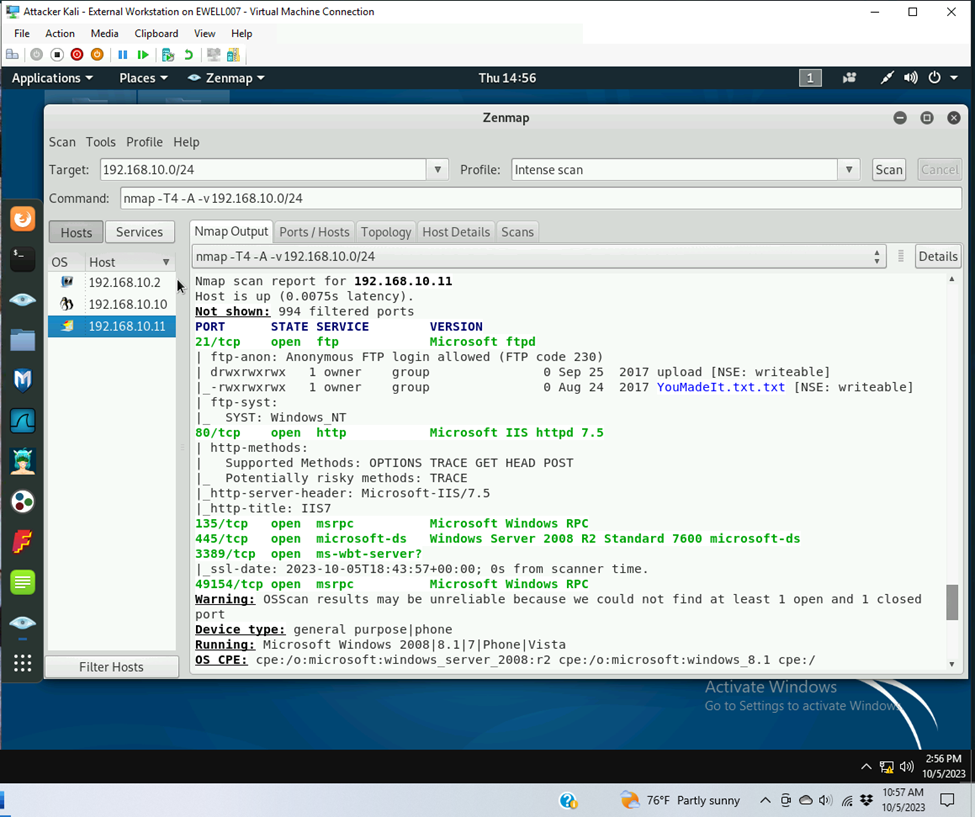
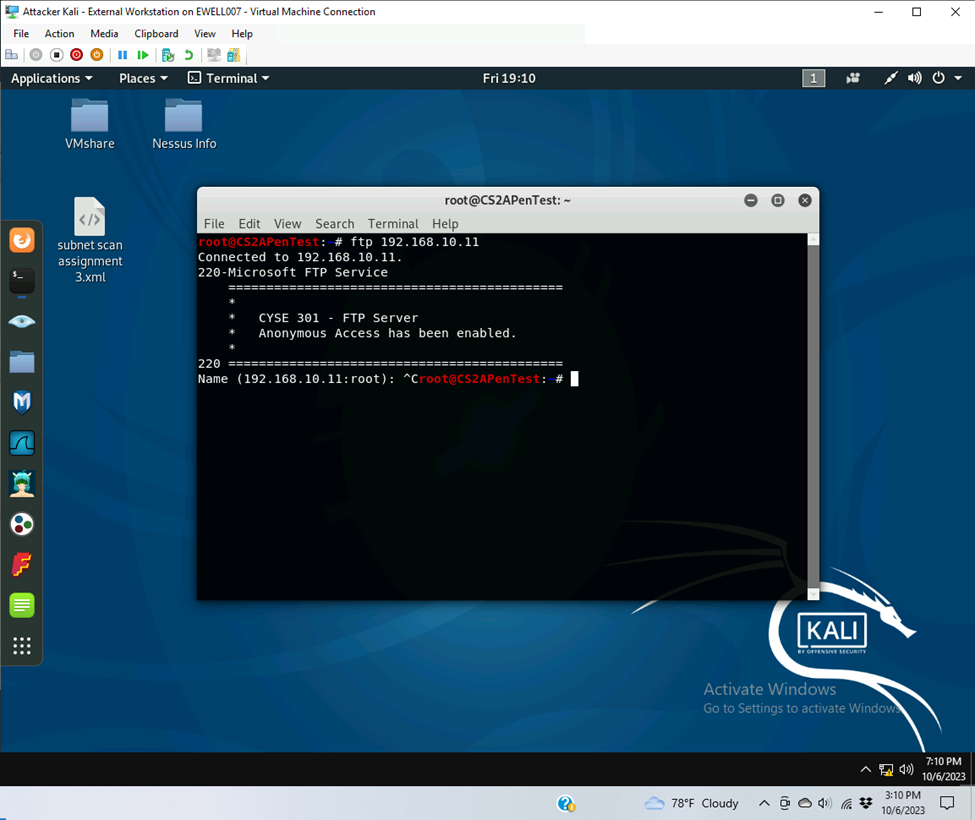
- 192.168.10.11 windows server 2008
- Open ports
- Port: 21
- Service: FTP
- Version: Microsoft ftpd
- Service: FTP
- Port: 80
- Service: http
- Version: Microsoft ITS httpd 7.5
- Service: http
- Port 135
- Service: msrpc
- Version: Microsoft Windows RPC
- Service: msrpc
- Port 445
- Service: Microsoft-ds
- Version: Windows Server 2008 R2 Standard 7600 microsoft-ds
- Service: Microsoft-ds
- Port 3389
- Service: ms-wbtserver
- Version: not listed
- Service: ms-wbtserver
- Port 49154
- Service: msrpc
- Version: Microsoft windows RPC
- Service: msrpc
- Port: 21
- Open ports
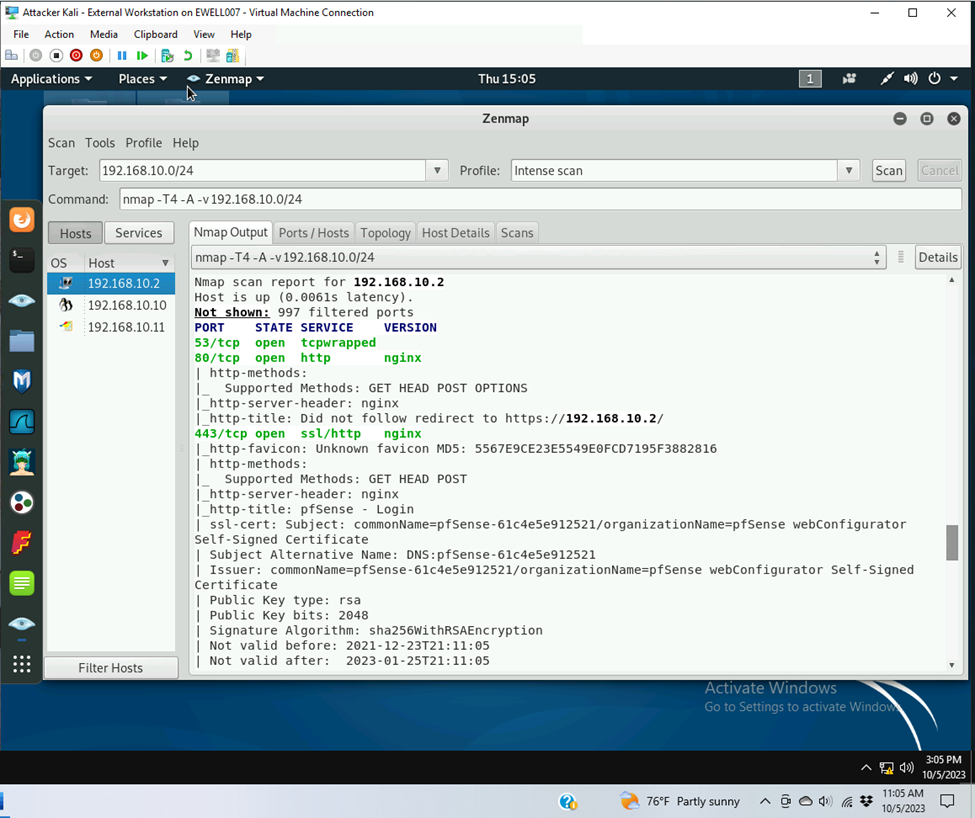
- 192.168.10.2 pfsense
- Open Ports
- Port 53
- Service: tcpwrapped
- Version: not listed
- Service: tcpwrapped
- Ports 80
- Service: http
- Version: nginx
- Service: http
- Port: 443
- Service: ssl/http
- Version: nginx
- Service: ssl/http
- Port 53
- Open Ports
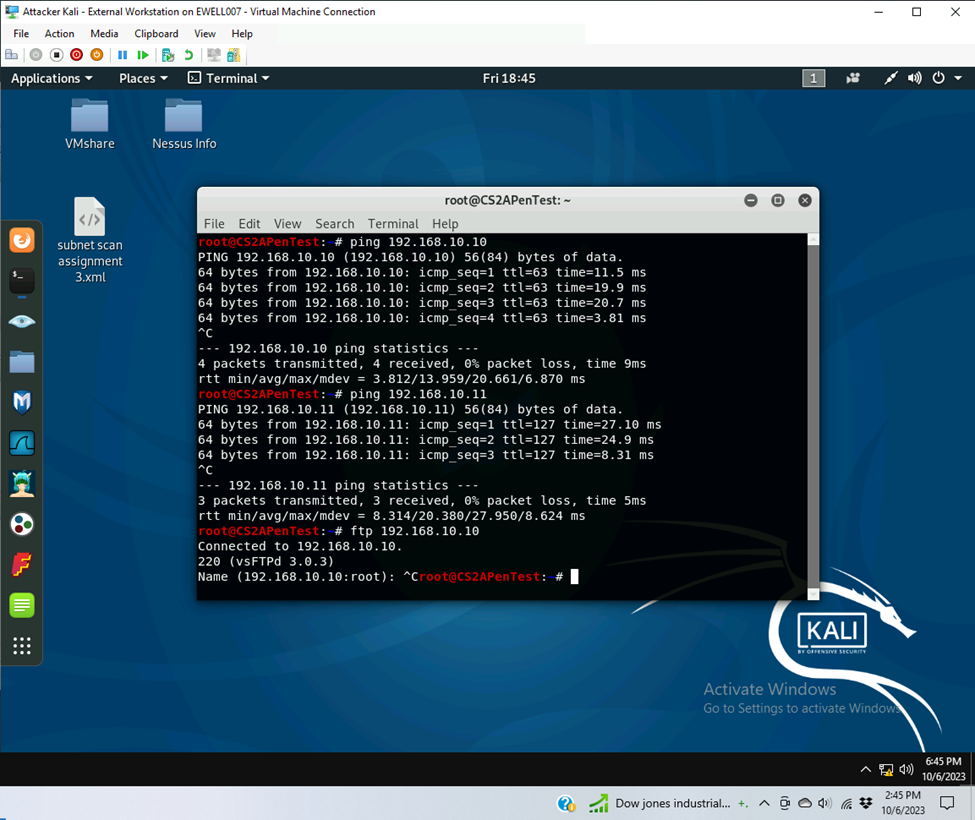
- Run Wireshark in Ubuntu VM while External Kali is scanning the network. Discuss the traffic pattern you observed. What do you find? Please write a 200-word essay to discuss your findings.
At the beginning of the Wireshark capture there is the normal TCP and DNS traffic between Ubuntu and Pfsense. Then as Zenmap started its intense scan a flood of broadcast ARP happened for 192.168.10.0/24 subnet. Two pings were successfully made from ubuntu to external kali during the ARP broadcast. After the broadcast then came external kali trying to establish a connection on all ports. The only port that ubuntu was responding for was TCP port 21. External Kali then verified the software and service for port 21 which was FTP service with vsFTPd 3.0.3. Then the stream went back to the standard TCP and DNS request from ubuntu for ntp.ubuntu.com. This probably happened while zenmap was testing the other endpoint for open ports. Once Zenmap came back to ubuntu it retested the connection to port 21 and pinged the ubuntu system as well, several more times. The TCP recconection to port 21 also was coming from different source port sequentially. Zenmap also tried to connect to port 37263 via UDP but was unreachable. Responses were in ICMP. Zenmap tried to login to the FTP server on Ubuntu several times with the username anonymos and the password IEUser@. It also tried to connect to the FTP server with the Transport Layer Security however quit afterwards. Zenmap also utilized the SYST and STAT commands to attempt to gather system information about the FTP server. Then it returned to the normal TCP and DNS stream indicating that Zenmap was finished with its scan.
Task B: Shield – Protect your network with firewall
- Configure the pfSense firewall rule to block the ICMP traffic from External Kali to Ubuntu VM.
| Rule # | Interface | Action | Source IP | Destination IP | Protocol (port # if appliable) |
| 1 | WAN | Block | 192.168.217.3 | 192.168.10.10 | ICMP |
- Initial test
- Ping ubuntu and WS 2008
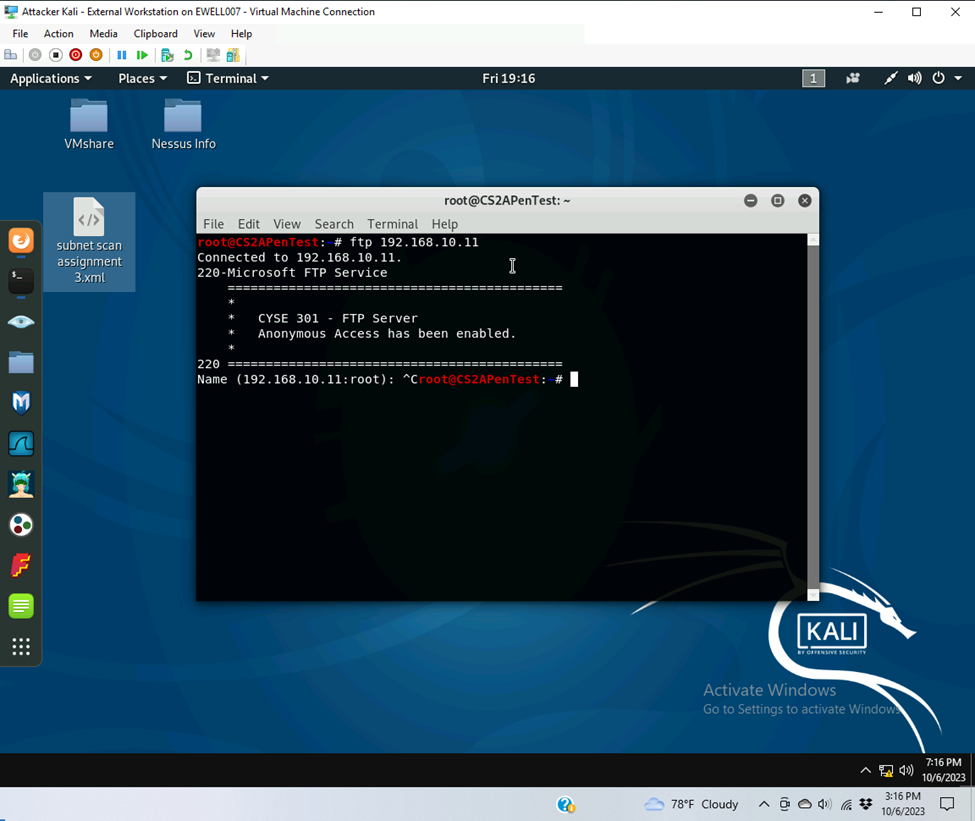
- Connect FTP on Ubuntu
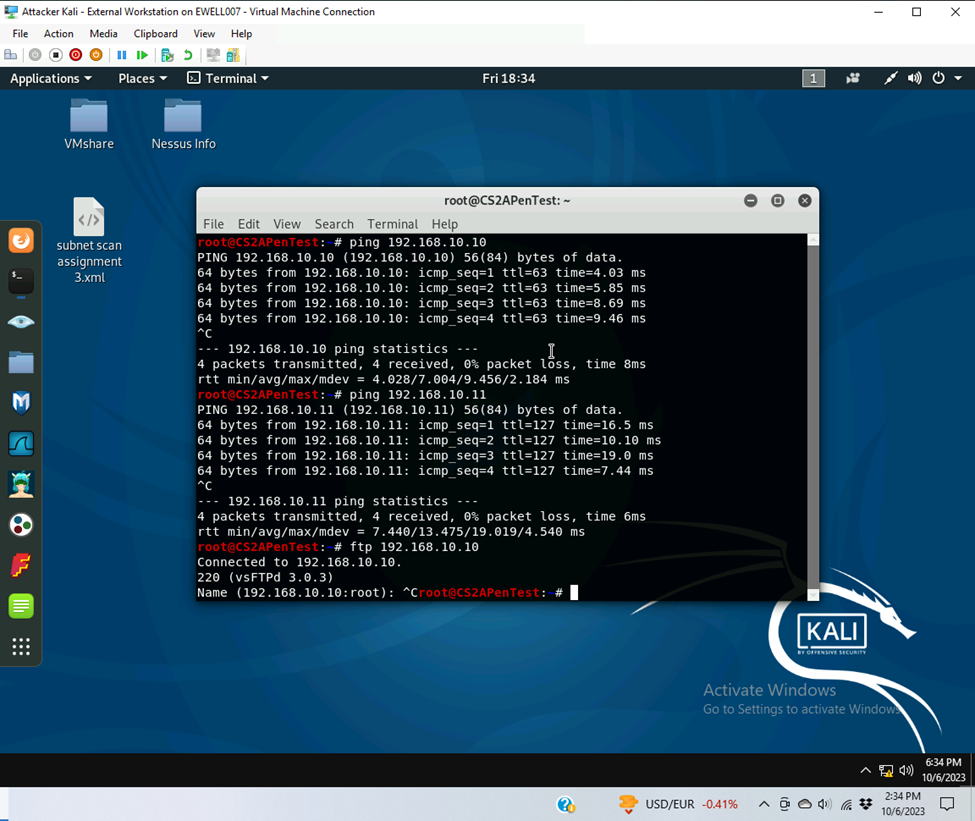
- Rule
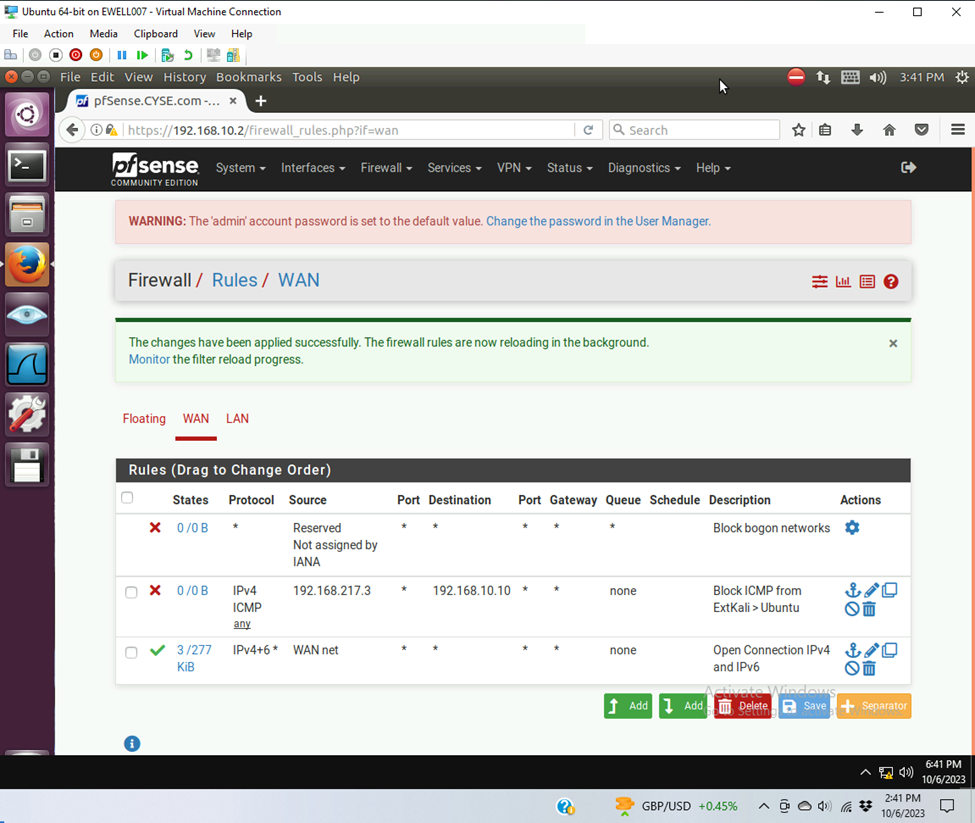
- Validation of rule
- Affected parameters
- Block ping from external kali to ubuntu
- Affected parameters
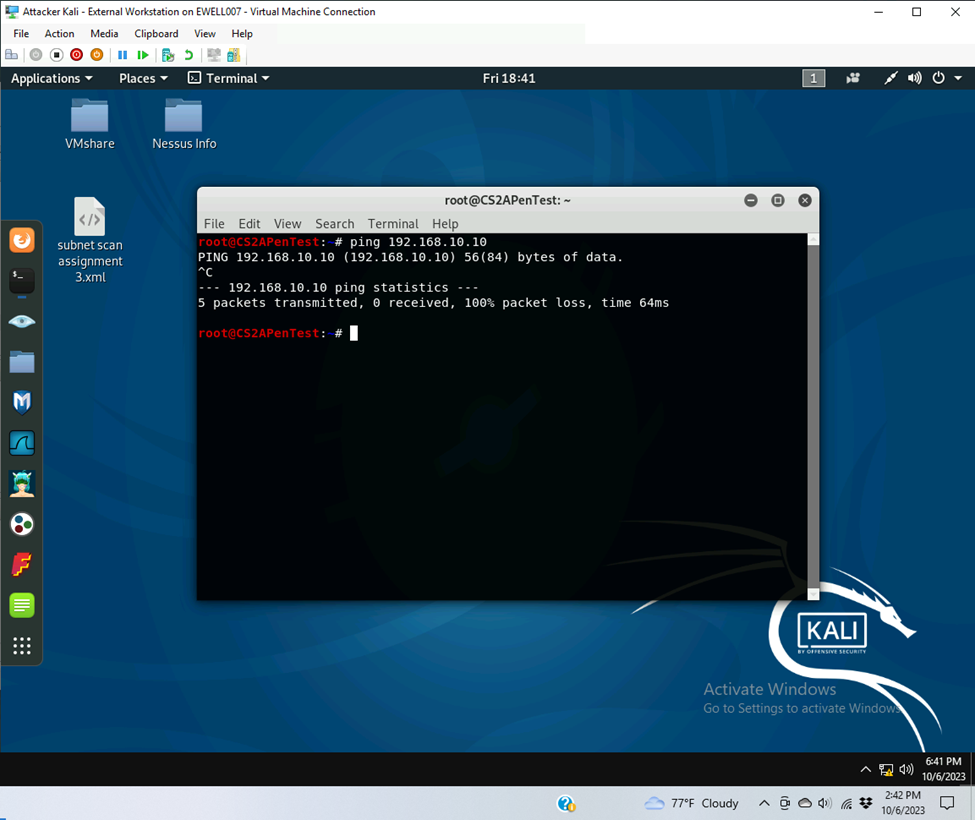
- Unaffected parameters
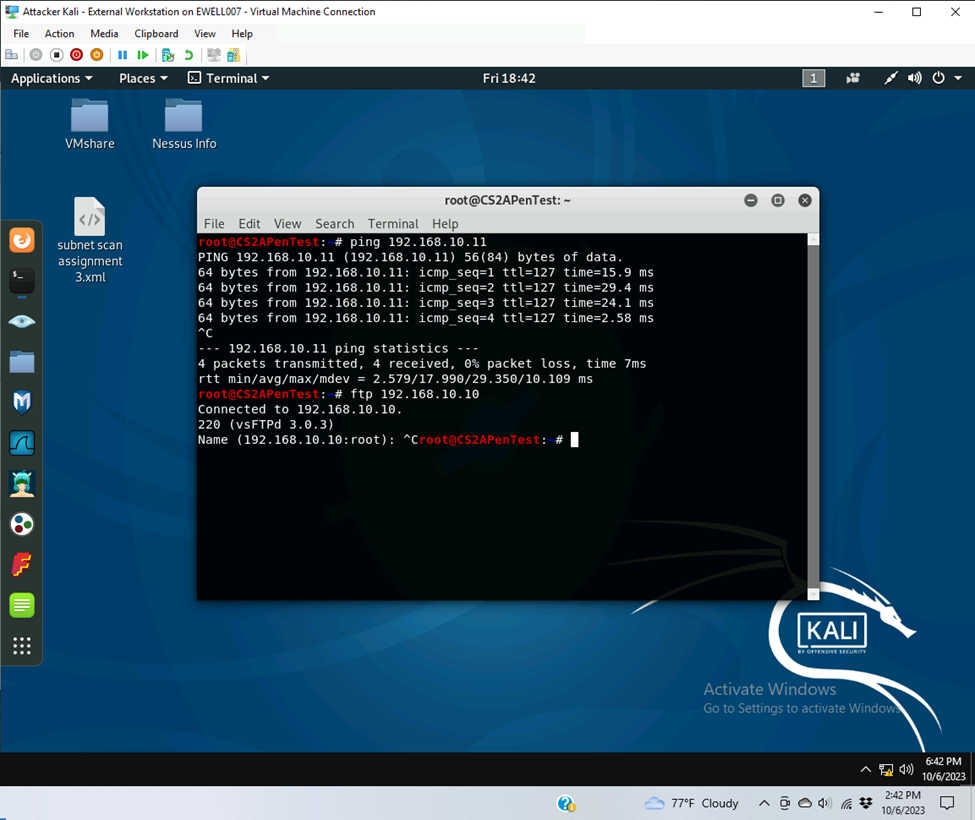
- Ping WS 2008 and FTP to ubuntu successfully
- Clear the previous firewall policies and configure the pfSense firewall to block all ICMP traffic from External Kali to the LAN side.
| Rule # | Interface | Action | Source IP | Destination IP | Protocol (port # if appliable) |
| 1 | WAN | Block | 192.168.217.3 | * | ICMP |
- Initial test
- Ping ubuntu and WS 2008
- Connect FTP on Ubuntu
- Rule
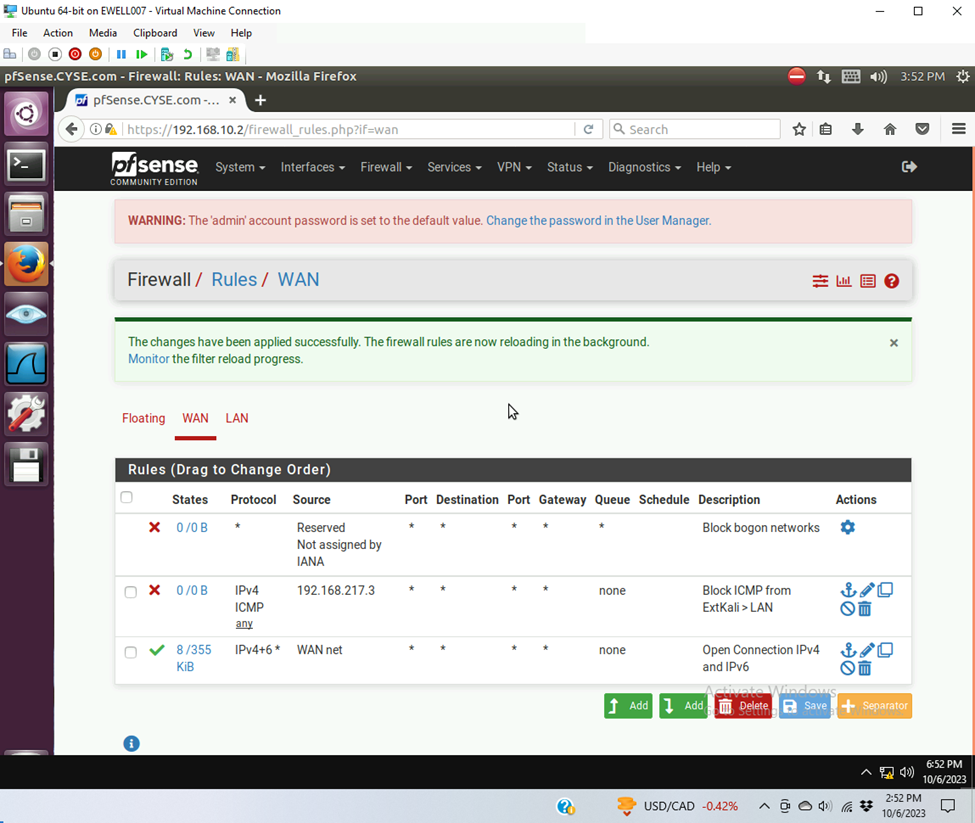
- Validation of rule
- Affected parameters
- Blocked pings to both ubuntu and WS 2008
- Affected parameters
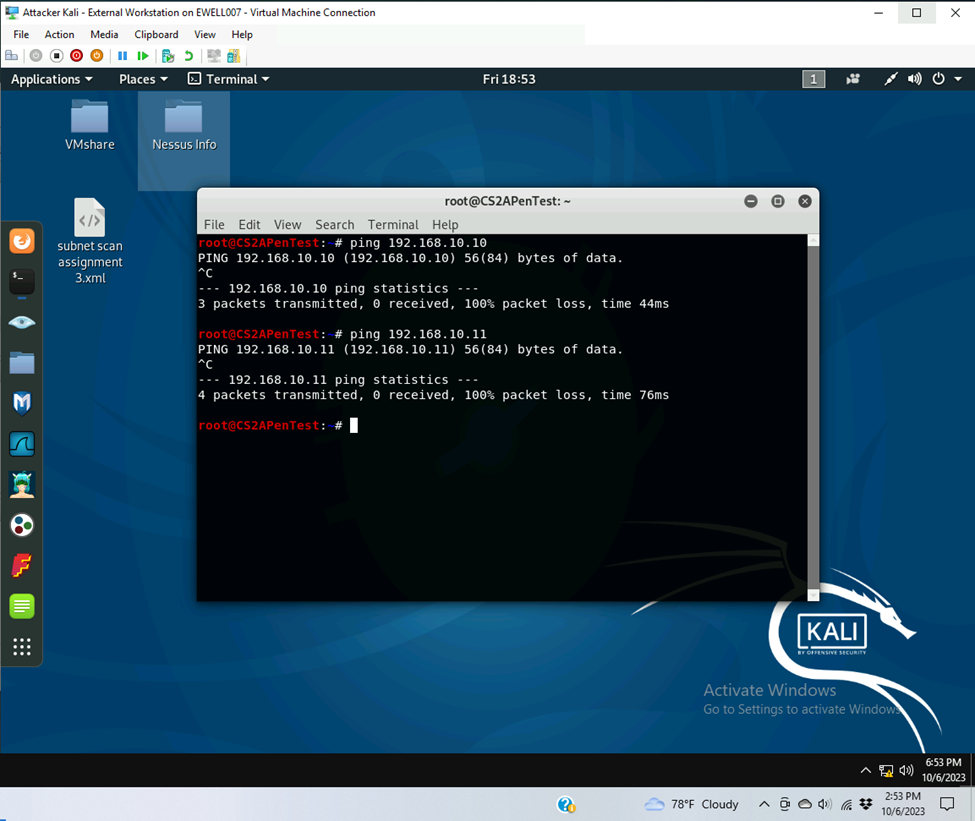
- Unaffected parameters
- FTP connection to ubuntu sucess
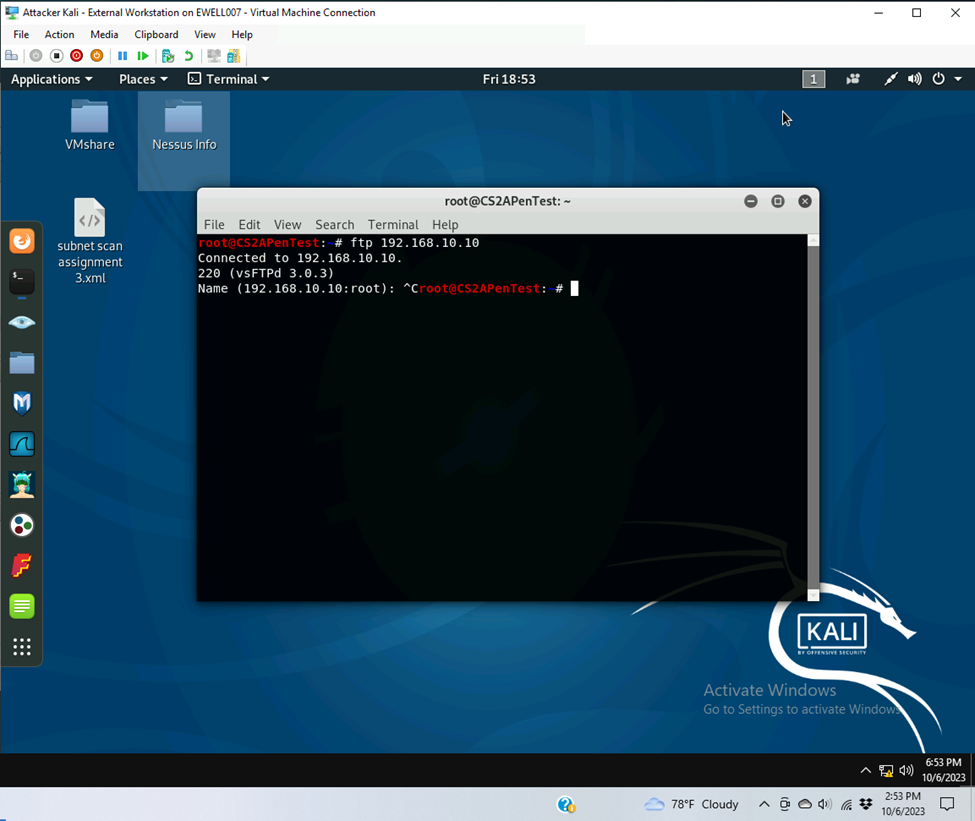
- Clear the previous firewall policies and configure the pfSense firewall to block ALL traffic from External Kali to the LAN side, except for the FTP protocol towards Windows Server 2008.
| Rule # | Interface | Action | Source IP | Destination IP | Protocol (port # if appliable) |
| 1 | WAN | Pass | 192.168.217.3 | 192.168.10.11 | FTP Port 21 |
| 2 | WAN | Block | 192.168.217.3 | * | * |
- Initial test
- Ping ubuntu and WS 2008
- Connect FTP on Ubuntu
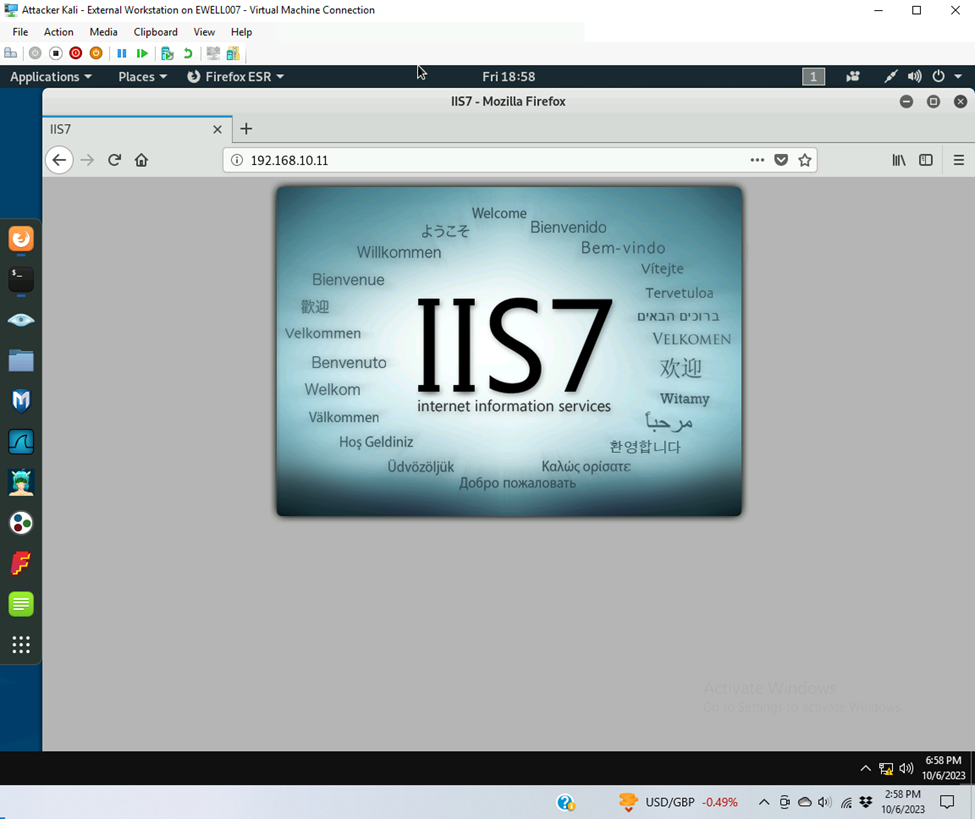
- HTTP to WS 2008
- FTP to WS 2008
- Rule
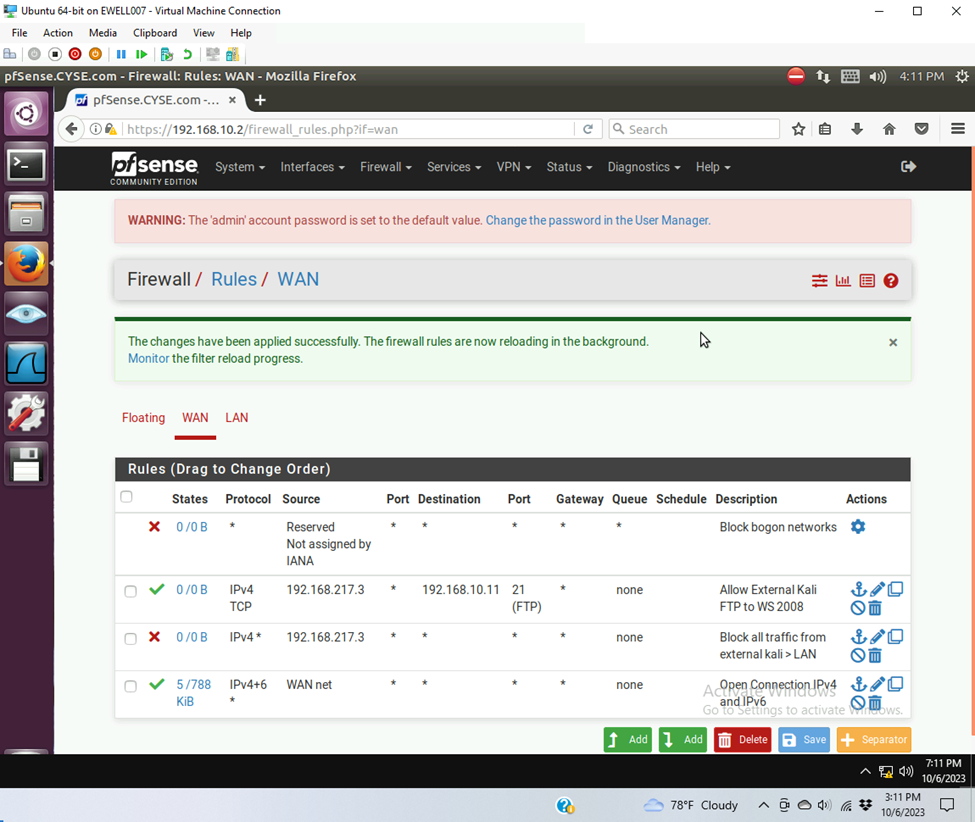
- Validation of rule
- Affected parameters
- Blocked pings to ubuntu and WS 2008
- Blocked FTP to ubuntu
- Affected parameters
- Blocked http to WS 2008
- Unaffected parameters
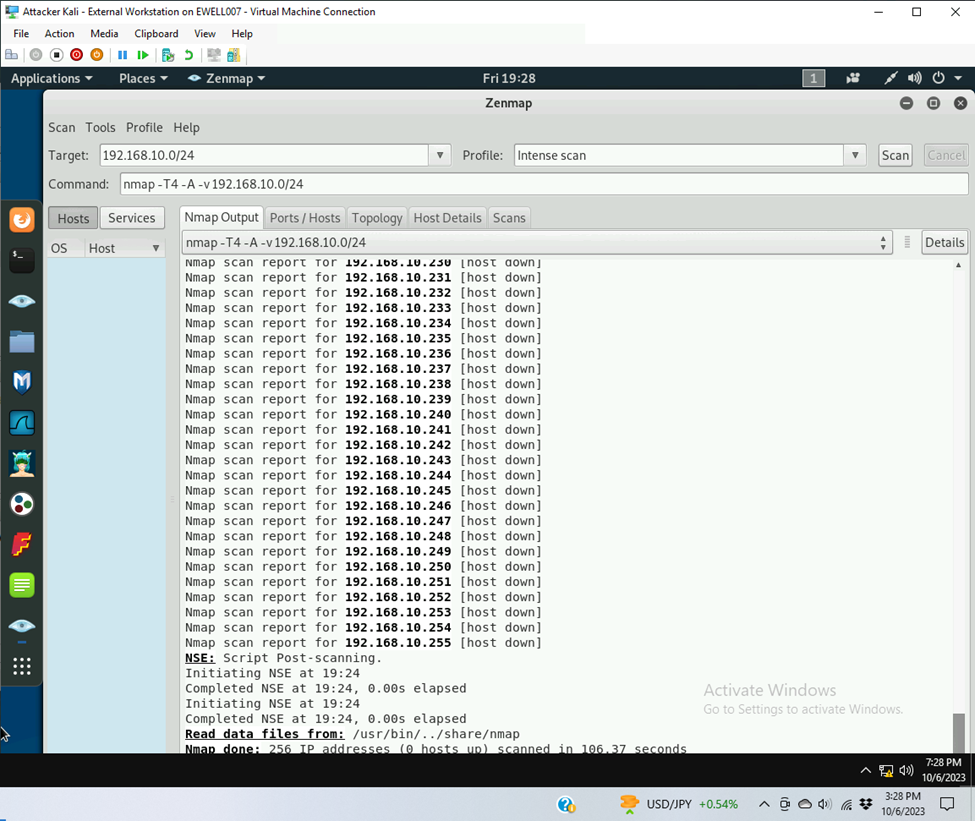
- Keep the firewall policies you created in Task B.3 and repeat Task A.1. What’s the difference?
- All of the host were down/blocked during the ping broadcast from zenmap. This then prevented zenmap from further scanning the subnet. Wireshark on the ubuntu side only saw the normal TCP/DNS stream from ubuntu to pfsense.
Extra credit (15 points): Use NESSUS to enumerate the security vulnerabilities of Microsoft Windows Server 2008 VM in the CCIA network.
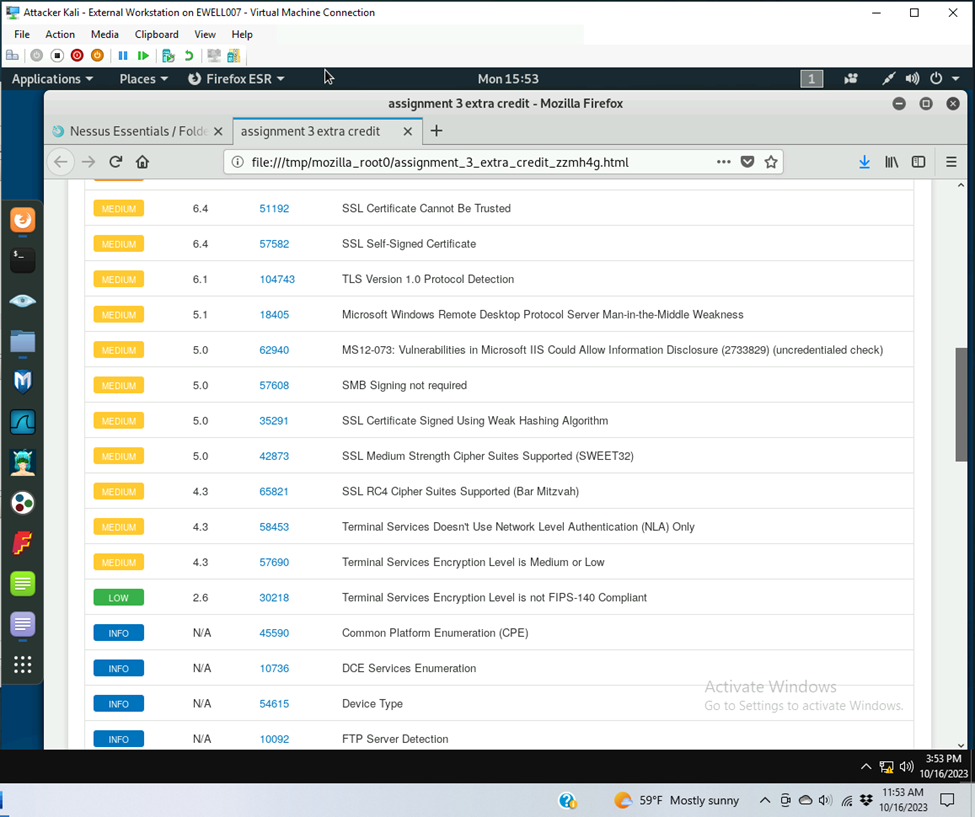
There are 18 listed vulnerabilities and 36 informations
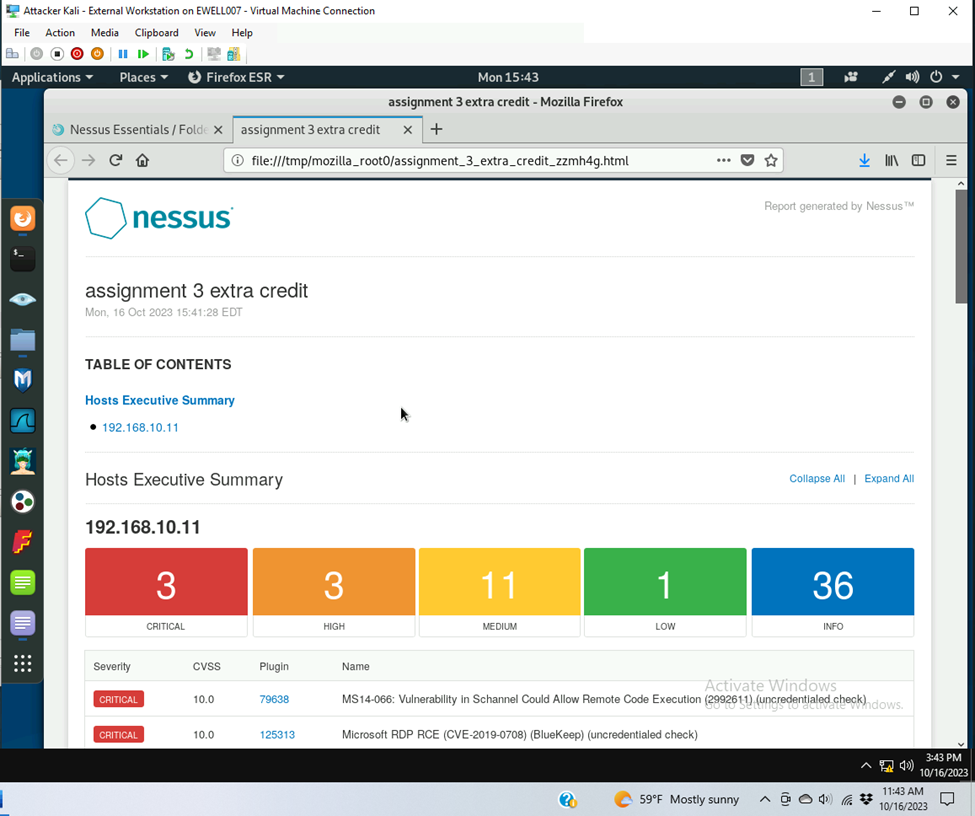
There are 3 critical vulnerabilities and 3 high vulnerabilities
- Critical
- Microsoft RPD RCE CVE 2019-0708
- MS 14-066 Vulnerability in Schannel cloud allow remote code execution 2992511
- Unsupported windows OS
- High
- MS12-020 vulnerabilities in remote desktop cloud all remote code execution 2671387
- MS17-010 secuiryt update for Microsoft windows SMB server 4013389
- Unsupported web server detection
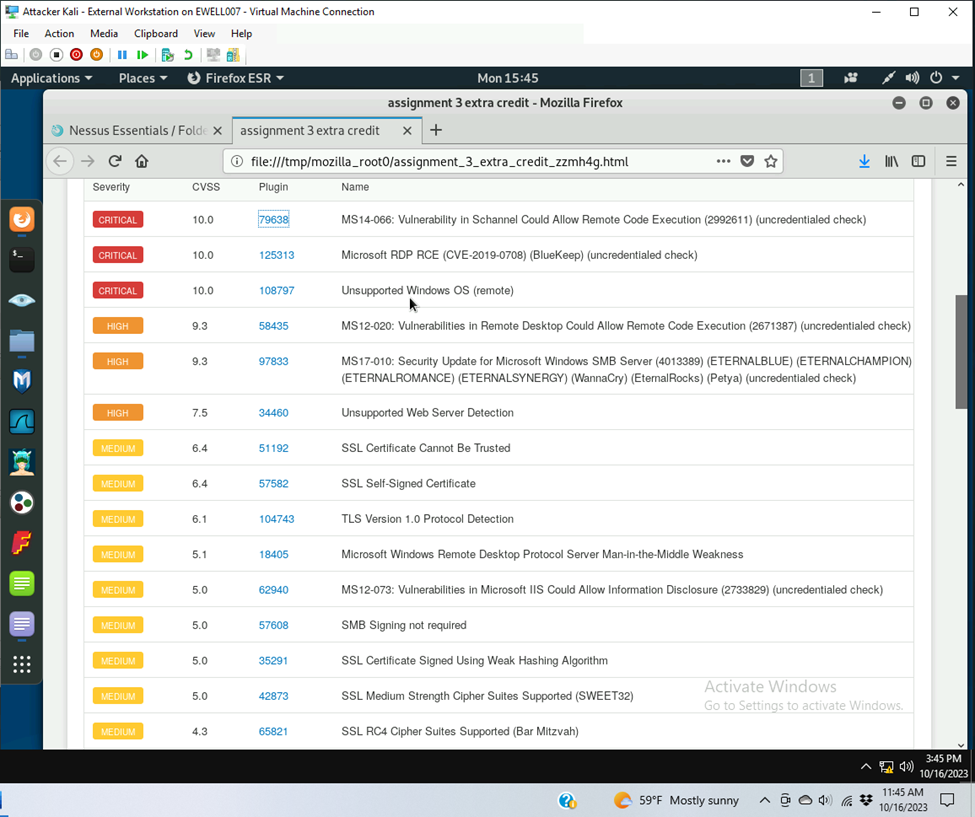
There are 11 medium security vulnerabilities and 1 low security vulnerability
- Medium
- SSL certificate cannot be trusted
- SSL self-signed certificate
- TLS version 1.0 protocol detection
- Microsoft Windows Remote desktop protocol server man-in-the-middle weakness
- Ms 12-073 vulnerabilities in Microsoft IIS cloud allow information disclosure 1733829
- SMB singing not required
- SSL certificate signed using weak hashing algorithm
- SSL medium strength cipher suites supported
- SSL RC4 cipher suites supported
- Terminal Services Encryption level is medium or low
- Terminal serviced doesn’t use network level authentication only
- Low
- Terminal Services encryption level is not FIPS-140 Compliant