Journal Entry 1
1/21/25
I am currently interested in cyber intelligence, blue teamer, or purple teamer job. These are all dream jobs to me and the parts of the NICE Framework that focus on these careers are protection and defense, investigation, cyberspace intelligence, and cyberspace effects. I want to work more with the actual crimes, but I also want to know how to defend against them so all of these parts are crucial to these types of jobs. The least beneficial, I believe would be oversight and governance, design and development, and implementation and operation. While these would all be useful pieces of knowledge and experience, they don’t match to my current job goals.
Journal Entry 2
1/29/25
The principles of science relate to cybersecurity because cybersecurity is a very interwoven field into every discipline. These principles are used to understand and study the behaviors of people and the environment according to how they are interacting and using technology, specifically relating to cyber attacks in cybersecurity. By understanding the human side or social science part of attacks, cybersecurity professionals can better understand how to secure systems by coming up with ways to prevent certain dangerous behaviors. The principles of science in social science and cybersecurity work together to better understand how and why people make decisions about attacks and think critically to develop research that is simple and efficient in solving a problem.
Journal Entry 3
2/4/25
This information from privacyrights.org can help researchers understand where the main targets are for attacks. This can also help security analysts focus on the most targeted places in order to see where their vulnerabilities are. This information, because it is public, is easy to access as well which means that any researcher can study patterns that have formed over time in certain states or industries. This information also gives researchers a glance at where the majority of attacks come from and target, which can help narrow their search to find an attacker. Smaller numbers of affected individuals can be studied by seeing if they were specific targeted attacks for companies or just random victims, this may help researchers see what the attacker’s motives were.
Journal Entry 4
2/11/25
Maslow’s hierarchy of needs can be related to the behaviors created when technology is used and needs are met or hindered. On the physiological level, my sleep was affected when I was not able to use my computer at home for over two days because it was not working. For the safety needs level, I felt unsafe one time using an app I had when a family member with the same app got a virus while using it. Both of these affected how I was sleeping and made me worrisome and upset. At the belongingness and love needs level, I was able to connect with others on a social media site called LinkedIn, including a friend of my parents, who has helped me in my career goals. For the esteem needs level, I was able to create digital flashcards and use an online program that helped me prepare for a big test I was taking. I was proud of myself for completing the online program and passing the exam which then raised my self-esteem. The highest level of Maslow’s hierarchy of needs in which I can connect with my experiences with technology is the self-actualization level. My strive to achieve my full potential in computer training is where I can connect with this level through technology. I plan on achieving self-actualization through the achievement of certain certifications provided online, training on computer programs, practice using programming languages, the completion of a bachelors and masters in cybersecurity, and the achievement of completing an internship and then earning a job.
Journal Entry 5
2/19/25
If I had to rank the individual motives behind cybercrimes between 1 and 7, my top rank would be entertainment. I feel like in a way, hacking can be really fun and the risks or harm factors can be forgotten about in the act. This is why an entertainment motive makes the most sense to me for cybercrime, and I believe it is one of the most dangerous as well. In second, I would place boredom, followed by revenge motives in third. Boredom can be related to entertainment, because if someone is bored, they are going to find some way to entertain themselves, even if it is risky behaviors online. Since it is much easier for hackers these days as well, with AI, this may be the best remedy for bored hackers. In 3rd place, I would place revenge because this reminds me of trolling which can be easy for anyone to do, because they don’t have to actually face their victims in real life, and it can be done in many ways to hurt their victim. The last 4 spots in order from 4th to 7th are multiple reasons, political, money and recognition. I placed multiple reasons in the middle because I think this is a very important motive since a regular joe is not going to commit cybercrime unless they have some impeding factors in their life that drive them the fulfill another motive. For example, someone who may have grown up in poverty might try to steal money and therefore has two motives, socioeconomic and money. Political motives specifically make sense to me during elections and campaigns, and have been used a lot. Politics is full of very strong opinions, therefore people with hacking abilities will use this to their advantage to either make their opinions heard or make others’ look unprofessional. Politics motives are lower due to the fact that they spike during elections and campaigns and are not typically an all-year motive. Money is a very strong motive because most people in the world want money, and stealing a little bit of money through the internet does not seem so risky compared to major street crimes, making it an easy motive. The reason this motive is lower on my list is because the other ones seem more credible to use as a motive if someone is going to go through with committing a cybercrime. In 7th place, I chose recognition because just like outside cyberspace, people want to fit in and feel connected with others, so being able to be recognized for a huge hack could attract attention and wanted recognition, but I feel like most cybercrime happens individually at least for smaller crimes.
Journal Entry 6
2/27/25
The first fake website I found was a fake amazon website [1]. There are several images of this fake website example and the first one has a misspelt word which is an indicator of a fake website. The other images show time limits and large discounts to get people to click on them before the time runs out. These unreasonable discounts and time limits are also indicators of a scam. The real amazon website has a lot more details, images, and headings at the top without misspelt words. The fake website is more limited on what is on the home screen and immediately asks for information compared to the real site. The second site I found was a fake paypal website [2]. This site was tricky to catch but if you look at the URL carefully, you can see that it is a spoofed URL. The creator placed paypal[.]com before the actual site name to make it look more real. The real website is right behind paypal[.]com and it is a random website, which makes this a fake website. The real site says paypal[.]com with no other website behind it. I would also say that the login box looks weird compared to the real site, because the text looks fuzzy and a little off. The last site I found was a fake Nike website [3]. This website also had a URL that revealed it was fake. Instead of the URL saying Nike[.]com, like the real site, it says some other shop. The items for sale are also listed as major discounted items. The shoes also have numbers listed in the item description lines which looks very odd, especially since the official site just lists what the shoe is, there are no weird combination of numbers. The logo in the corner is also an indicator of this being a fake website, since it says NikeFactoryStore, while the real website just says Nike. There are also other things listed for all three of these examples including complaints for customers and low-level reviews that help determine that these websites are fake. These problems with these sites help identify them as fraudulent sites because they have grammar issues, scams, and missing information on their sites. All of these sites are scams to get people to spend money on either misleading products or nothing at all.
[1] Slekyte, I. (June 24, 2024). A fake or scam website: What it is, and how to know if a website is legit. NordVPN. https://nordvpn.com/blog/fake-scam-websites/
[2] Toohil, R. (January 15, 2025). Websites: 11 warning signs. AURA. https://www.aura.com/learn/how-to-identify-fake-websites
[3] Lakovics, Z. (September 11, 2024). 5 recent examples of fake websites. MEMCYCO. https://www.memcyco.com/5-recent-examples-of-fake-websites/
Journal Entry 7
2/5/25

- This is an example of human centered cybersecurity because there is active security training taking place. They are specifically going over phishing attacks and how to prevent them. Training can be done in any sort of workplace for cybersecurity awareness, and by helping people stay alert of cyber awareness, there will be less human error.
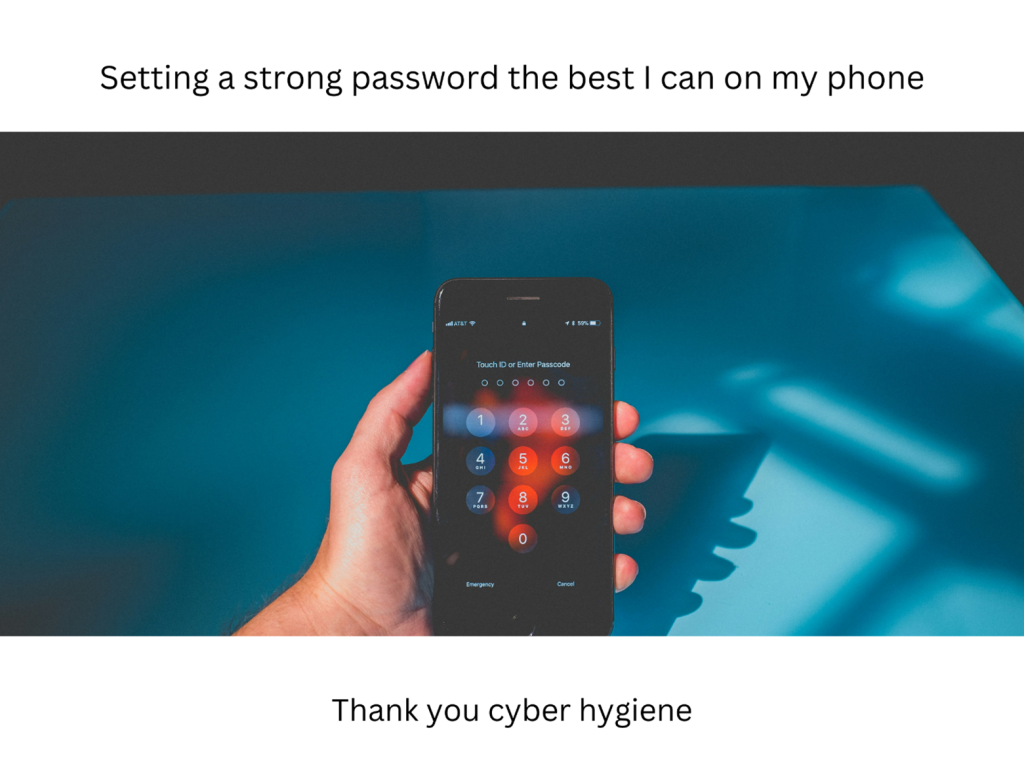
- Setting strong password is another great example of how people can learn about cyber hygiene and how they can do their part to protect data. This example is specific to creating a strong password, even thought the only options are numbers, a random combination, preferably not a birthday or significant number would work better. Something to add here is also two factor authentication, this person can possibly set this up and have the option for both to have a more secure login.

- Training on keeping software up to date is very important and can help prevent vulnerabilities in a system. This is something that anyone can do on any device and can help the device stay up to date and running smoothly.
Journal Entry 8
3/19/25
The media can manipulate our ways of thinking about cybersecurity in many different ways. Movies and shows involving hackers typically use fake jargon to make the scenario sound complicated and make the hackers look very intelligent for knowing and understanding these terms. Media can also make code look scarier than it actually is, like in several movies where is shown to be 3D and moving in some intelligent super computers. The media can also give the false idea that all hacking is done quickly and without difficulty. This is simply not true because a lot of times these things take a long time and sometimes hackers have to understand a new type of code before they can continue. The media can lastly create a false idea about cybersecurity by making it seem like we have all sorts of technology to do anything, like a box that can automatically crack passwords. All of these things take time and the assumptions against the cybersecurity field can create confusion for why things take so long.
Journal Entry 9
3/26/25
After answering the statements on the social media disorder scale, I received a score of 0, meaning that I answered no to all of the questions. This means that I have a normative usage of social media, which is good. I really don’t use social media, unless LinkedIn counts, which I am rarely on anyway. The items in the scale are very relatable to me, only because I have seen many other people act differently due to social media. I knew someone who would spend there whole day on social media and would get upset when they had to leave it for the day. I believe that different social media usage patterns are found across the world because a lot of cultures don’t revolve around social media like the U.S. does. The U.S. uses social media in almost every aspect of life: politics, news, everyday activities, food, music, etc. Other countries in the world use social media, but only use it to share memorable, conversational, or immediate information in their country or to other countries. I feel like social media is overused here in the U.S., and a lot of people have become too dependent on it for social interactions.
Journal Entry 10
3/30/25
There has been a large rush of the decentralization of information over the past decade. People now receive their information from other places other than just single news platforms. Information is distributed on the internet through social media, blogs, forums, and many other sources nowadays. There is little that prevents or restricts the creation and spread of content online across a state, country, or the world. This easy manipulation of information can be controlled by cybercriminals to create disorder and chaos among a population through the spread of disinformation that can influence a society as a whole. Bots typically spread this information through fake social media accounts to manipulate opinions. Some preventions for this problem could be the censorship of the information that is fake, but then this leads into the problem of interfering with the freedom of speech in some nations. The BEND model can help cyber professionals organize and distinguish between different intentions behind disinformation spread. Distrust in a nation is an enemy in itself and is therefore, why social cybersecurity is important to understand and implement into defenses.
Journal Entry 11
3/31/25
Some important social behaviors that can be required for a job as a cybersecurity analyst would be technical and communication skills. To get this entry level job, you would need to have some sort of technical experience such as an internship, volunteer work, or even certification knowledge in that field. Communication skills are also very important for the interview process, working with others, and even just being able to network with others to get the job. As the video stated, a cybersecurity analyst will have to review a lot of data and is the first line of defense, therefore having a social behavior such as being a systematic thinker is important as well. It will be crucial that a security analyst looks at all of the interconnected parts to understand attacks. Finally, the field of cybersecurity is all about the continued learning social behavior. The more people train themselves on other subjects in the field, the more they will be able to either ask for a pay raise or move up to a higher position.
Journal Entry 12
4/7/25
The company letter demonstrates an economic theory known as the rational choice theory. In the best interest of the company’s future profits, the company decides to send out a notification to possibly affected customers and how they are going to fix the information leak issue. This represents this theory because the company decided to make the rational choice to tell the affected customers instead of avoiding the issue and receiving complaints or losses in profits; therefore, this is pleasure over pain. Another economic theory that relates to this letter would be the Laissez-faire economic theory. This theory states that government should not be involved with the economy unless people’s inalienable rights are tampered with. Since the pursuit of happiness and another, not listed but assumed, right of privacy, are listed, these would be affected in this scenario. Therefore, the inclusion of federal law enforcement for the investigation is understandable. One social science theory that relates to this letter would be the structural functionalism theory. This theory explains that everything in a society is connected and that everything and everyone rely on each other. The company in the letter relies on the cybersecurity professional and the law enforcement to protect and investigate the system. The customer relies on the company for news and products but also relies on the bank to reset compromised information. Symbolic interactionism is the last social science theory that connects to this letter. This theory states that society functions due to the connections between people. In this letter, the company is connecting with the customer and describes other connections it has made with law enforcement and cyber professionals to correct the issue. If there wasn’t a connection with the customer, then the customer may have had information stolen and did not even know about it. This company probably would have lost more customers if they did not address the issue either.
Journal Entry 13
4/7/25
Due to the lack of bug bounty submissions because of fears about liability issues, between 2017 and 2019, the implementation of VDPs (vulnerability disclosure policies) has been instated. The use of bug bounties can help companies easily detect vulnerabilities by hiring these skilled researchers to be paid per bounty. This research highlights the questions of whether bug bounties help just larger companies or if they are beneficial to smaller ones as well, and how HackerOne is helpful to specific companies they choose. The results showed that these hackers were often driven by other factors such as competitiveness and accomplishment rather than monetary gain from these bug bounties. This factor is crucial for smaller companies who may be have the funds to pay them very much. This is seen the most in inexperienced hackers who want the experience more than the money, while more experienced hackers do still care about the bounty price. The number of bug bounty reports have been inconsistent across programs. Bug bounties are useful across all companies, however, because there are hackers like lower level for smaller companies and higher level for larger ones.
Journal Entry 14
4/14/25
Out of the 11 illegal things that internet users unknowingly do online, my top five would be, from the worst to the 5th worst, sharing passwords, addresses, or photos of others, bullying and trolling, using unofficial streaming services, illegal searches on the internet, and collecting information about children. I put sharing passwords, addresses, and photos of others as first because this can be very dangerous to the person who owns the password, address, and photo. An attacker may target them either online using their password and demographics for a social engineering attack, or just in person, since they know their address and what they look like. Bullying and trolling is in second because not only is this emotionally destructive to the victims, but the attacker could be charged for this type of behavior. Their actions could also be used against them in court if anything happens to their victim, due to their actions. Using unofficial streaming services is in third because it happens all the time. People download and watch pirated content all the time and it is unfair to the people who spent time on the content, and then didn’t receive anything from the viewers who just watched it illegally for free. This can also be dangerous because pirated sites are not secure, which could be the source of a cyberattack. In fourth place, I put illegal searches online because these searches can be subject to supervision by authorities once you have searched a supervised search term. Even if someone was just searching something as a joke, it is very important for people to watch what they search because the internet is not just free anyone to do whatever they want. I chose collecting information about children to be the fifth spot because to me, this is just wrong. It is also against the law to collect data about children under 13 in surveys or any other data collection, online.
Journal Entry 15
4/25/25
Digital forensics relates to the social sciences because the investigators have to be able to understand the social aspects of how people communicate and why different attacks were done. Searching social media interactions can be used by digital forensic investigators to collect information on suspects to be used in court. They can also learn about the different social interactions and aspects of a company or business that can help them understand why an attack may have occurred, like maybe having all of the emails for a company stored on the same servers with other data, unencrypted. The speaker’s pathway to his career is interesting but also shows that really any person can start in a cyber related job just with some experience or interest in the field. He started in the account field and just gained some experience in the IT department when they needed help. This opened many doors for him and his interest only made him more open to learning new things and continuing his learning through digital forensics.