Look at NICE Workforce Framework. What areas do you want to focus on? Talk about the areas that would interest you.
I want to focus on two areas: Exploitation Analyst and Software Development. The areas differ considerably, but they appeal to my interests. Becoming an Exploitation Analyst is attractive because it requires an understanding of networks. Analysts can work in various fields, such as cybersecurity, law enforcement, or data analysis. I also find the position of Software Developer interesting because it requires coding skills. The function of Software is to design, create, test, and maintain software applications, systems, and programs.
Explain how the principles of science relate to cybersecurity.

Cybersecurity: A Scientific Discipline
Cybersecurity protects systems, networks, and data from unauthorized access, use, disclosure, disruption, modification, or destruction. It is a complex and ever-evolving field, but cybersecurity is a scientific discipline at its core.
The principles of science are deeply intertwined with cybersecurity, both in methodology and philosophy. For example, the scientific method is a fundamental tool used by cybersecurity professionals to identify, detect, and respond to threats. The scientific method involves observing, hypothesizing, experimenting, and drawing conclusions. Cybersecurity professionals use a similar approach to investigate security incidents and develop countermeasures.
Another important scientific principle that is essential to cybersecurity is empiricism. Empiricism is the reliance on observable and measurable evidence to support claims. In cybersecurity, evidence-based decision-making is crucial. Security analysts rely on logs, data traffic patterns, and other empirical data to detect and analyze breaches.
Falsifiability is another fundamental scientific principle that is relevant to cybersecurity. Falsifiability means that a theory or hypothesis must be capable of being proven false to be considered valid. Cybersecurity systems and protocols are continually tested to find potential vulnerabilities. Security experts are trying to “falsify” the assumption that a system is secure.
Reproducibility is also an important scientific principle. In science, experiments must be reproducible to verify their validity. In cybersecurity, when a vulnerability is discovered, it is essential to reproduce the issue to understand it fully and verify that the implemented solutions work.
Continuous revision is another hallmark of science. Scientists revise their theories and models as they learn more about the world. Similarly, cybersecurity is never static. Security measures must be continuously revised and updated as new threats emerge and technology evolves.
Peer review is another important scientific principle. Scientists often submit their research to peers for review to ensure its validity. In cybersecurity, peer reviews are standard for code (code reviews) to identify potential vulnerabilities or logic errors.
Systematic skepticism is another crucial scientific principle. Science encourages a skeptical mindset, where claims are not accepted without evidence. Cybersecurity professionals also practice skepticism, especially when analyzing network traffic, code, or systems’ security posture.
Finally, both science and cybersecurity rely on theoretical frameworks. In science, theories provide a structured understanding of phenomena. In cybersecurity, frameworks (like the OSI model) structure complex systems and guide how security protocols are applied.
In conclusion, cybersecurity is a scientific discipline in its own right. The rigorous, systematic, evidence-based, and skeptical approach required in science is mirrored in the best practices of cybersecurity, making the two deeply interconnected in philosophy and practice.
Here are some specific examples of how the principles of science are applied in cybersecurity:
Security researchers use the scientific method to develop new security tools and techniques. For example, researchers may observe a new type of malware and then hypothesize how it works. They may then create a test environment to experiment with the malware and verify their hypothesis. Once they understand how the malware works, they can develop a countermeasure.
Security analysts use empiricism to detect and investigate security incidents. For example, an analyst may review security logs to identify suspicious activity. Once the analyst has identified suspicious activity, they may collect additional data to investigate the incident further.
Security engineers use falsifiability to test the security of systems and networks. For example, security engineers may conduct penetration tests to try to exploit vulnerabilities in a system. If the engineers can exploit a vulnerability, they can then report it to the system’s owner to fix it.
Security professionals use reproducibility to verify that security solutions are effective. For example, suppose a security researcher develops a new patch to fix a vulnerability. In that case, they may publish the patch so that other security professionals can test it and verify it works.
Security professionals use continuous revision to keep their skills and knowledge current. For example, security professionals may attend conferences, read security blogs and articles, and participate in online training courses to stay informed about the latest security threats and trends.
Security professionals use peer review to ensure the quality of their work. For example, security professionals may submit their code for review by other security professionals before deploying it in production.
Security professionals use systematic skepticism to evaluate the security of systems and networks. For example, security professionals may not trust the default security settings on a system. They may manually configure the security settings to meet the organization’s specific security needs.
Review Maslow’s Hierarchy of Needs and explain how each level relates to your experiences with technology. Give specific examples of how your digital experiences relate to each level of need.
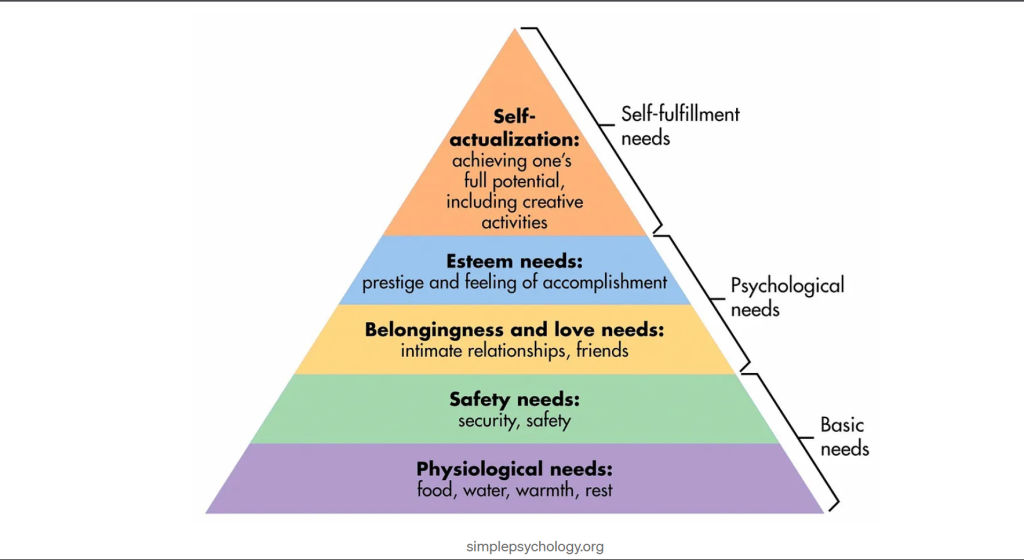
Maslow’s Hierarchy of Needs is a theory in psychology proposed by Abraham Maslow in his 1943 paper “A Theory of Human Motivation” in the journal Psychological Review. Maslow subsequently extended the idea to include his observations of humans’ innate curiosity.
The theory posits that human needs are arranged in a hierarchy, with the most basic needs at the bottom of the pyramid and the most complex at the top. Maslow believed that people are motivated to satisfy their needs in a specific order and that only once the lower-level needs are met can people focus on helping the higher-level needs.
The five levels of Maslow’s Hierarchy of Needs are:
Physiological needs: These are the most basic needs, such as food, water, shelter, sleep, and clothing.
Safety needs: These needs include security and stability, such as protection from harm, employment, and financial security.
Love and belonging needs: These needs include intimacy, affection, and acceptance.
Esteem needs: These needs include self-respect, confidence, and achievement.
Self-actualization needs: These are the highest level of needs, including reaching one’s full potential and living a meaningful life.
How each level of Maslow’s Hierarchy of Needs motivates behavior:
Physiological needs: When people are hungry, thirsty, or tired, they will be motivated to find food, water, or shelter. They will also be encouraged to avoid danger and protect themselves from harm.
Safety needs: People are motivated to find a safe place to live and work and to have a stable income. They also want to feel safe and secure in their relationships.
Love and belonging needs: People are motivated to connect with others and to feel loved and accepted. They want close relationships with friends, family, and romantic partners.
Esteem needs: People are motivated to achieve their goals and to feel good about themselves. They want to be respected and admired by others.
Self-actualization needs: People are motivated to reach their full potential and live meaningfully. They want to use their talents and abilities to make a difference.
Maslow’s Hierarchy of Needs is a helpful framework for understanding human motivation. It can explain why people behave the way they do and help people identify and satisfy their needs.
For example, a person struggling to meet their basic needs for food and shelter may need help to focus on their higher-level needs, such as education or career development. Similarly, a person feeling unsafe or insecure may be unable to form close relationships or pursue their goals.
Maslow’s Hierarchy of Needs can also create more effective workplaces and schools. When people’s basic needs are met, and they feel safe and supported, they are more likely to be motivated to perform well and reach their full potential.
Can you spot three fake websites and compare the three fake websites to three real websites, plus showcase what makes the fake websites fake?

Spotting fake websites is crucial in today’s digital age, as the internet is replete with fraudulent platforms designed to deceive unsuspecting users.
To safeguard oneself from these scams, individuals must understand the telltale signs that differentiate fake websites from legitimate ones. This essay will delve into the characteristics that make fake websites discernible, compare fake and honest websites, and emphasize the importance of vigilance in online interactions.
To begin with, recognizing fake websites starts by examining their domain names. Fake websites frequently employ misspelled variations or unconventional domain extensions to mimic legitimate sites. Fake PayPal website “paypal-login.com” deviates from the genuine “paypal.com.” Such discrepancies should raise immediate suspicion. The absence of trusted site seals is a red flag. Trusted organizations usually endorse legitimate websites with site seals, which authenticate their credibility. Fake websites either lack these seals entirely or employ counterfeit versions, further undermining their trustworthiness.
Another crucial indicator of a fake website is the lock icon in the address bar. Legitimate websites display a lock icon, signifying a secure connection, whereas fake websites omit this icon or use a counterfeit one. Content on fake websites often shows poor grammar, spelling errors, or factually incorrect information. These inaccuracies should be present in genuine websites, which prioritize well-written and informative content.
Examining auxiliary pages is also instrumental in distinguishing between real and fake websites. The “About Us” page on fake websites is typically missing or contains vague and incomplete information, whereas genuine websites provide comprehensive details about themselves and their owners. Similarly, counterfeit websites’ “Contact Us” page is non-existent or contains inaccurate and outdated contact information. In contrast, legitimate websites offer complete and accurate contact details, enabling users to reach out through multiple channels.
In conclusion, identifying fake websites is essential for internet users to protect themselves from scams and fraudulent activities. By scrutinizing the domain name, site seal, lock icon, content quality, “About Us” page, and “Contact Us” page, individuals can significantly reduce their vulnerability to online deception. Vigilance is the key to ensuring a safe and secure online experience.
Create a meme explaining what is going on in the individual’s or individuals’ mind(s).

Write a journal entry about how you think the media influences our understanding about cybersecurity.

The media, in its various forms, holds a pivotal role in shaping the public’s understanding of cybersecurity. It serves as a double-edged sword, capable of both enlightening and misleading us regarding the complex world of digital security.
To address the issue, media outlets can increase awareness concerning cybersecurity risks. News articles spotlighting significant data breaches can elucidate the potential aftermath of cyberattacks, motivating individuals to adopt protective measures like password changes and two-factor authentication. Viewers can gain a more comprehensive understanding of the various cyber threats and defense methods through accurate depictions of hacking and cybersecurity in movies and TV shows.
However, the media’s influence isn’t always benign. Yellow journalism, characterized by its sensationalism, exaggeration, and predilection for eye-catching headlines, can significantly impede our comprehension of cybersecurity risks. It often sacrifices factual accuracy to boost readership or online clicks, giving rise to several detrimental consequences.
One concerning outcome is the exaggeration of cyber threats. Yellow journalism tends to amplify the quantity and severity of cyberattacks, fueling unwarranted fear and prompting irrational responses, such as overspending on unnecessary cybersecurity products and services.
Another issue lies in the perpetuation of cybersecurity myths and stereotypes. Hackers are frequently portrayed as heroic figures or malevolent criminals, obscuring the ethical complexities of cybersecurity and making it challenging for the public to grasp the risks and ethical considerations involved.
Even in modern times, we find ourselves afflicted by yellow journalism, which can lead to inaccurate or misleading reporting on cybersecurity. Information may be presented distorted, whether deliberately or inadvertently, thereby fostering a misguided understanding of the risks and preventive measures.
To navigate this landscape, it is paramount to adopt a critical mindset when consuming information about cybersecurity, particularly from sources prone to yellow journalism. The discerning consumer should seek information from reputable outlets and exercise caution in the face of sensationalism, exaggeration, and headline-driven reporting.
Identifying yellow journalism can be facilitated by several critical indicators. Sensationalized language and exaggerated claims are standard features of such reporting. Articles that spotlight the most sensational aspects of a story, such as the scale of impact or the amount of money involved, without offering adequate context or analysis, should raise red flags. Sweeping generalizations and the promotion of stereotypes are also telltale signs. Assessing the author’s credentials and the source’s reputation is another crucial step in gauging the credibility of an article. Is the author a respected journalist, and does the source hail from a reputable news organization? When in doubt, cross-referencing with other sources can help establish a more balanced and informative perspective.
By adopting a discerning approach to information consumption, individuals can shield themselves from the pernicious influence of misinformation, fostering a more accurate understanding of cybersecurity threats and best practices. Furthermore, supporting muckraking journalism can aid in uncovering cybersecurity wrongdoing and ensuring accountability within influential organizations. This, in turn, can contribute to a more informed and secure digital landscape for everyone.
Card Magic Pedagogy: A Creative Way to Teach Cybersecurity

The article “Cybersecurity Shuffle” by Moore and Cappos proposes a novel teaching approach to cybersecurity using card magic for high school students. This innovative method transforms card tricks into cybersecurity attack simulations, bridging the gap between abstract cybersecurity concepts and concrete card manipulation. By leveraging scaffolding as a pedagogical strategy, the authors provide students with a familiar framework to demystify intricate cybersecurity topics such as social engineering and side-channel attacks.
A 90-minute online workshop employing this methodology yielded promising results, with students’ test scores improving by 15% to 30%. Feedback underscored its enjoyability and educational efficacy, demonstrating that card magic is a viable and engaging approach to cybersecurity education.
The authors demonstrate card tricks to teach cybersecurity concepts with two specific examples: the “Rising Cards” trick and the “Card Counting” trick. The Rising Cards trick demonstrates how social engineers exploit trust and manipulate people’s desire to believe in magic, mirroring the manipulation tactics used in social engineering attacks. Conversely, the Card Counting trick parallels side-channel attacks, wherein a magician exploits human error to deduce the number of cards a participant holds.
The authors’ innovative teaching strategy is supported by mixed-method research, combining quantitative and qualitative data, confirming that it not only bolsters understanding but also enhances student engagement. This strategy’s potential reach is extensive, potentially raising cybersecurity awareness in underserved communities lacking technical education.
Additionally, the card magic pedagogy integrates social science principles such as trust and decision-making, extending learning beyond technicalities to include human factors crucial in cybersecurity. This contribution to educational resources suggests that such creative teaching methods could apply to other complex fields.
Despite its promising results, the study acknowledges limitations such as its small sample size and the brief duration of the method’s impact assessment. Consequently, further research is needed to evaluate long-term effectiveness and broader demographic applicability.
Incorporating the examples given, the “Rising Cards” and “Card Counting” tricks both demonstrate essential cybersecurity threats: manipulation through trust and exploiting human error, respectively. These tricks symbolize how social engineering and side-channel attacks function, emphasizing the importance of awareness and protection against such sophisticated exploits.
Overall, the work of Moore and Cappos represents a notable innovation in education, with implications extending beyond cybersecurity. It presents a unique, relatable, and interactive way to comprehend complex topics, calling for further exploration of such methods across varied educational fields.
This innovative teaching approach has several potential benefits:
- It can make complex cybersecurity concepts more accessible and engaging for students. By using familiar and visually appealing card tricks, the authors can help students understand and remember these concepts more quickly.
- This approach can help students to develop critical thinking skills. By analyzing the card tricks and discussing how they relate to cybersecurity, students can learn to identify and mitigate potential threats.
- This approach can help students to develop a deeper understanding of the human factors involved in cybersecurity.
By learning how social engineers and attackers exploit human error, students can become more aware of their vulnerabilities and take steps to protect themselves.
While the study by Moore and Cappos has some limitations, its findings are promising and suggest that card magic could be a valuable tool for teaching cybersecurity. Further research is needed to evaluate the long-term effectiveness of this approach and to assess its applicability to broader demographics. However, the work of Moore and Cappos represents a significant step forward in developing innovative and engaging teaching methods for cybersecurity education.
References
Moore, P., & Cappos, J. (2022). Cybersecurity Shuffle: Using Card Magic to Introduce Cybersecurity Concepts. Journal of Computing Sciences in Colleges, 37(8), 52-61. https://doi.org/10.1145/3478432.3499081
Roy, S. (2023, March 25). Social Engineering: The greatest Magic Trick to Hack Your Everything. Medium. Retrieved October 1, 2023, from https://medium.com/@shantoroy/social-engineering-the-greatest-magic-trick-to-hack-your-everything-e0dfaa3786a9
Gasiewski, J. A., Eagan, M. K., Garcia, G. A., Hurtado, S., & Chang, M. J. (2023, March 25). From Gatekeeping to Engagement: A Multicontextual, Mixed Method Study of Student Academic Engagement in Introductory STEM Courses. Medium. Retrieved October 3, 2023, from https://www.ncbi.nlm.nih.gov/pmc/articles/PMC3596160/
Carrington, G. (2023, January 30). 6 Examples of Student-Centered Learning. Sora Schools. Retrieved October 3, 2023, from https://soraschools.com/6-examples-of-student-centered-learning/
New Cybersecurity Awareness Assessment Metrics Consider the Needs of Marginalized Groups

In “The Development of Metrics to Assess the Effectiveness of Cybersecurity Awareness Programs,” authored by Sunil Chaudhary, Vasileios Gkioulos, and Sokratis Katsikas and published in the Journal of Cybersecurity on August 12, 2022, we will explore how the study aligns with the principles of the social sciences, the central research questions or hypotheses it poses, the research methods employed, the data collection and analysis techniques, its connection to class concepts, its consideration of marginalized groups’ challenges, concerns, and contributions, and ultimately, the societal impact it delivers.
Relation to the Principles of the Social Sciences
The social sciences study human society and social behavior. Cybersecurity awareness programs aimed at altering human behavior fall within the purview of social sciences. This article is relevant to the social sciences because it delves into the human element of cybersecurity, an overlooked aspect.
In the social sciences, one fundamental principle asserts that human behavior is intricate and influenced by various factors, including individual, social, and cultural elements. Effective cybersecurity awareness programs must consider these factors to bring about meaningful change. Another core principle maintains that human behavior is modifiable through education and training. Cybersecurity awareness programs, as a form of education and training, play a pivotal role in disseminating cybersecurity best practices, aligning with this principle.
Research Questions or Hypotheses
The central research question of this study is: “How can we develop metrics to assess the effectiveness of cybersecurity awareness programs?”The authors posit that existing metrics need to be more comprehensive and inclusivity, rendering them inadequate for gauging the effectiveness of cybersecurity awareness programs. Consequently, they propose a novel set of metrics that not only encompass a broader range of factors but also consider the unique requirements of marginalized groups.
Types of Research Methods Used
In this study, the authors employ qualitative research methods to interview cybersecurity experts regarding their perspectives on evaluating cybersecurity awareness programs. Additionally, they conduct a thorough literature review to identify existing evaluation methods. Qualitative research, characterized by its focus on understanding the meaning of human experiences, is particularly apt for studying complex cocial phenomena like the effectiveness of cybersecurity awareness programs.
Types of Data and Analysis Done
The dataset collected for this study consists of interview transcripts and scholarly articles. To make sense of this data, the authors employ thematic analysis, a qualitative data analysis method that identifies recurring themes and patterns within textual data. Thematic analysis is a valuable tool for unpacking the nuances in interview transcripts and scholarly articles, allowing for a deeper understanding of the subject matter.
Concepts Discussed in Class That Are Relevant to the Article
Several concepts discussed in our class directly relate to this article, including:
- The significance of evaluating cybersecurity awareness programs.
- The complexities and challenges associated with assessing these programs.
- More comprehensive and inclusive evaluation metrics are necessary to address evolving
cybersecurity needs.
Relation to the Challenges, Concerns, and Contributions of Marginalized Groups
This article is pertinent to cybersecurity and addresses marginalized groups’ challenges, concerns, and contributions. Often, cybersecurity awareness programs do not cater to the specific needs of these groups, making them more susceptible to cyber threats. For instance, older adults may face difficulties due to their limited familiarity with new technologies, rendering them more susceptible to phishing scams. Similarly, people with disabilities may encounter barriers in using cybersecurity software and adhering to best practices. The study’s novel set of evaluation metrics is more comprehensive and inclusive than existing ones, ensuring that they encompass the needs of marginalized groups. For example, one metric focuses on the percentage of employees correctly identifying phishing emails, a metric relevant to all employees, including older adults and people with disabilities.
Overall Contributions of the Study to Society
This study makes a significant contribution to society by proposing a comprehensive set of
metrics for evaluating the effectiveness of cybersecurity awareness programs. These metrics
address the limitations of existing approaches and consider marginalized groups’ requirements.
Policymakers and practitioners can leverage these findings to develop and assess more effective
cybersecurity awareness programs, ultimately enhancing internet safety for all.
Conclusion
The Development of Metrics to Assess the Effectiveness of Cybersecurity Awareness Programs” by Kyung-Shick Choi is a valuable addition to cybersecurity. It underscores the importance of evaluating cybersecurity awareness programs and the associated challenges. Moreover, it introduces a novel set of evaluation metrics that are more encompassing and considerate of the diverse needs of society.
The study’s findings benefit policymakers, practitioners, and marginalized groups benefiting from improved cybersecurity awareness programs. Additionally, these findings emphasize the importance of continuous learning in cybersecurity and the need for a holistic approach to cybersecurity.
References
Chaudhary, S., Gkioulos, V., & Katsikas, S. (2022, August 12). The development of metrics to
assess the effectiveness of cybersecurity awareness programs. Journal of Cybersecurity, 12(3), 1-doi: 10.1093/cybsec/tyw028
Simply Psychology. (n.d.). Maslow’s hierarchy of needs. Retrieved from
https://www.simplypsychology.org/maslow.html
Scribbr. (n.d.). Qualitative research methodology. Retrieved from
https://www.scribbr.com/methodology/qualitative-research/
Thematic analysis. (n.d.). In Wikipedia, The Free Encyclopedia. Retrieved October 1, 2023, from
https://en.wikipedia.org/wiki/Thematic_analysis
Complete the Social Media Disorder scale. How did you score? What
do you think about the items in the scale? Why do you think that
different patterns are found across the world?

My score on the Social Media Disorder Scale (SMDS) is 1. This indicates that I have a low risk of problematic social media use (PSMU). I find the items in the scale to be comprehensive and well-written. They cover a wide range of behaviors that can be associated with PSMU, including preoccupation, persistence, escape, problems, deception, displacement, and conflict.
I believe that different patterns of social media use are found across the world due to a variety of factors, including cultural norms, access to technology, and mental health resources. For example, in some cultures, social media is seen as a more acceptable way to connect with others, which may lead to higher rates of PSMU. Additionally, people in countries with less access to technology may be more likely to use social media to escape from their daily lives, which could also contribute to PSMU. Finally, the availability of mental health resources can vary widely from country to country. People in countries with limited mental health resources may not have access to the help they need to address PSMU, which could lead to more severe problems.
Overall, I believe that the SMDS is a valuable tool for screening for PSMU. It is a reliable and valid measure that can be used to identify individuals who may be at risk of developing this condition.
As for my own social media use, I am aware of the potential for it to become problematic, so I make an effort to use it in a healthy way. I do not use it excessively, and I do not neglect other activities because of it. I also do not use it to escape from negative feelings. I am mindful of my social media use and make sure that it does not have a negative impact on my life.
While I have a low risk of PSMU, I believe that it is important to be aware of the signs and symptoms of this condition, so that I can seek help if I need it. I also believe that it is important to use social media in a healthy way, so that it does not have a negative impact on my life.
Read the article Social Cybersecurity: An Emerging National Security Requirement write a journal entry summarizing your response to the article.

The article “Social Cybersecurity: An Emerging National Security Requirement,” discusses the growing importance of social cybersecurity and its implications for national security. The authors argue that social cybersecurity is an emerging national security requirement that must be addressed by the Department of Defense (DoD) and other government agencies. They define social cybersecurity as “the ability to protect the DoD and its personnel from the harmful effects of social media and other online social networking platforms.” The authors identify several challenges to social cybersecurity, including the increasing use of social media by adversaries, the difficulty of detecting and mitigating social media attacks, and the need for clear guidance and policies on social media use. They also discuss several recommendations for improving social cybersecurity, such as developing a comprehensive social media strategy, educating personnel about social media risks, and investing in social media monitoring tools and technologies.
Social media resilience is essential for protecting individuals, organizations, and societies from the negative impacts of cyberattacks on social platforms. This resilience includes strategies to improve the ability to endure and recover from such attacks. For individuals, it means increasing cybersecurity awareness to recognize and avoid cyber threats, fostering critical thinking to discern misinformation, practicing digital hygiene like using solid passwords, being cautious with personal information, and maintaining emotional well-being in the face of online negativity. Societal resilience, on the other hand, requires a broad approach that includes establishing policies for social media use, protecting infrastructure, encouraging collaboration between various entities like government, tech companies, and academia, raising public awareness about social media threats, and supporting research in social cybersecurity. These efforts aim to enhance society’s collective defense against social media attacks and adapt to evolving technologies and emerging threats.
Read the sample breach letter “Sample Data Breach Notification”, and describe how two different economics theories and two different social sciences theories relate to the letter.
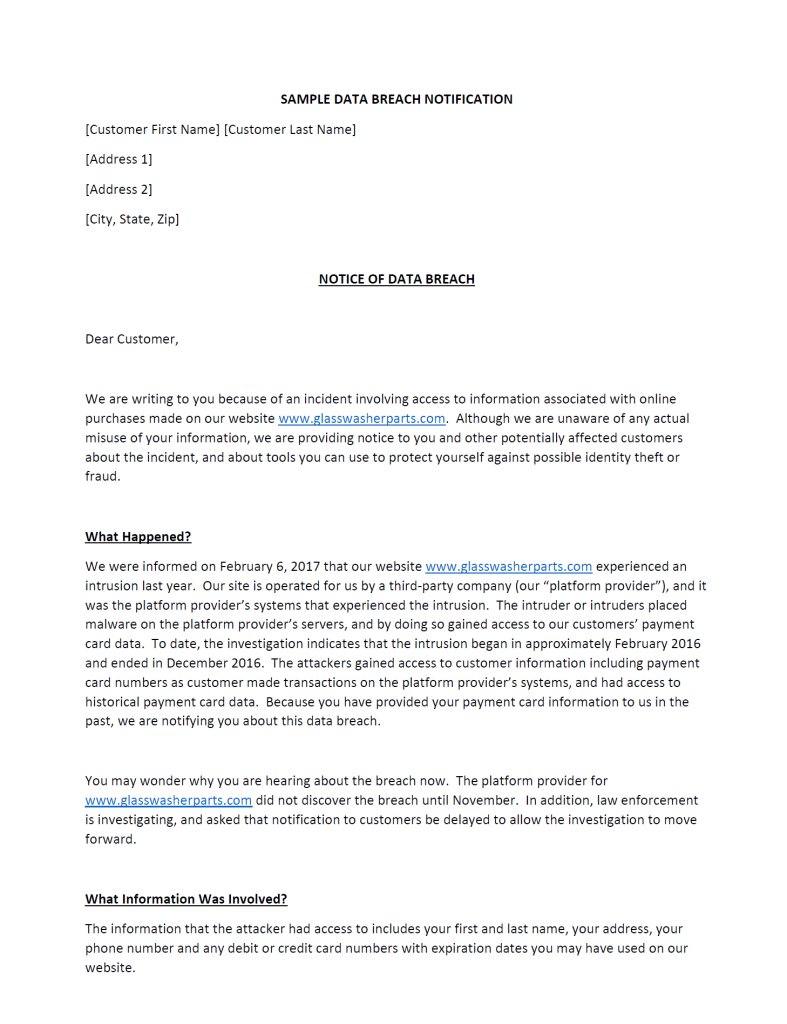
On February 6, 2017, Glasswasherparts.com, an online retailer, experienced a data breach, compromising customer payment card data. The breach, affecting transactions from February to December 2016, exposed customers’ names, addresses, phone numbers, and card details. The company has since bolstered its security and is collaborating with law enforcement, advising customers to monitor their card statements for suspicious activity.
From an economics perspective, transaction cost economics suggests the breach will escalate transaction costs for Glasswasherparts.com, necessitating investments in security and increased customer service and legal expenses. The principal-agent theory indicates a breakdown in the relationship between Glasswasherparts.com and its platform provider, whose failure to secure data led to customer harm. Socially, the social contract theory posits that Glasswasherparts.com breached its duty to protect customer data, failing in its social obligation. Social norms theory views the breach as a violation of societal norms against stealing personal information, where the company’s inability to safeguard data contravened these norms.
These theories together provide a multifaceted understanding of the breach’s implications. Economically, it reflects increased operational costs and a breakdown in trust between business entities. Socially, it represents a failure in fulfilling societal obligations and adhering to norms, highlighting the broader ethical and social responsibilities businesses hold in protecting customer data.
Review Andriy Slynchuk article and write a paragraph describing the five most serious violations and why you think those offenses are
serious.

The document outlines the five gravest violations, highlighting the severe nature of these offenses:
- Using copyrighted images without permission is a notable infringement, as it can lead to legal repercussions like lawsuits.
- Sharing personal information such as passwords, addresses, or photos of others is a significant breach, posing risks of identity theft or stalking.
- The act of bullying and trolling is included, which can cause emotional distress to the victims.
- Recording a Voice over Internet Protocol (VoIP) call without the consent of the involved parties is a violation of privacy rights.
- Audio extraction from YouTube videos is mentioned, a practice that can infringe upon copyright laws.
The severity of these offenses stems from their potential to cause harm to both the victim and the perpetrator. Infringing copyright laws, such as using unauthorized images or extracting audio from YouTube, can result in legal actions against the perpetrator. Sharing personal information like passwords and addresses can lead to serious crimes like identity theft or stalking, posing a threat to the victim’s safety and security. Bullying and trolling, although seemingly less tangible, can inflict long-lasting emotional trauma. Recording VoIP calls without consent breaches privacy, which is a fundamental right; thus, this act is taken seriously.
From a personal standpoint, sharing personal information, such as passwords, addresses, or photos of others, is the most egregious offense. This act not only violates privacy but also directly threatens individuals’ safety and security. The consequences of such a breach can be far-reaching, leading to crimes like identity theft, stalking, and, in extreme cases, physical harm. The perpetrators of such offenses must face stringent penalties to deter such behavior and safeguard the well-being of potential victims.
Why do you think individuals don’t report cybercrime victimization? Describe your views and respond to one other student’s entry.
Individuals often refrain from reporting cybercrime victimization due to various personal reasons. A primary factor is the fear of embarrassment or shame, particularly in cases of identity theft or online fraud, where victims might blame themselves. Some victims underestimate the impact of the crime, thinking it too insignificant to report, as seen in minor malware infections or phishing scams. Others doubt the effectiveness of reporting, skeptical about law enforcement’s ability to apprehend the perpetrators or assist in recovering losses. Practical challenges also play a role, as reporting can be time-consuming and complex, especially for those unfamiliar with the process or lacking necessary evidence like screenshots. Additionally, a lack of awareness about being a victim, particularly in identity theft cases, contributes to underreporting.
Systemic issues further exacerbate the underreporting of cybercrime. Cybercrime often receives low prioritization from law enforcement agencies, leading to concerns among victims about the seriousness with which their cases will be handled. The complex nature of cybercrime, involving sophisticated tactics and potentially international perpetrators, makes investigations challenging. Moreover, the absence of standardized reporting procedures complicates the process for victims, potentially resulting in reports being filed with multiple agencies and causing further investigative complications. Consequently, cybercrime remains significantly underreported, hindering the accurate assessment of its scope and the development of effective prevention and enforcement strategies. Raising awareness and simplifying the reporting process are crucial for encouraging victims to come forward and enabling law enforcement to combat cybercriminals effectively.
Write a journal entry describing what you think about the speaker’s pathway to his career.
I recently watched a TEDx talk by Davin Teo, a digital forensic expert, and I was very impressed by his career path. Teo started out as an accountant, but he always had an interest in computers. When his company was looking for someone to help out with their IT, he jumped at the opportunity. As he worked on the company’s IT systems, he became more and more interested in digital forensics. He eventually left accounting and started working as a digital forensic investigator. He has worked on a number of high-profile cases, and his testimony has helped to convict criminals.
I was particularly impressed by Teo’s willingness to take a chance on a new career. He wasn’t afraid to leave his stable job as an accountant to pursue his passion for digital forensics. I think this is a valuable lesson for anyone who is considering a career change. It’s never too late to follow your dreams.
I was also impressed by Teo’s dedication to his work. He is clearly passionate about digital forensics, and he is always looking for new ways to improve his skills. I think this is important for anyone who wants to be successful in their career. You need to be passionate about what you do, and you need to be willing to put in the hard work.
Overall, I was very inspired by Davin Teo’s story. He is a successful digital forensic expert who has made a significant contribution to the field. I am grateful for his work, and I encourage others to learn more about digital forensics.
In addition to the above, I also found it interesting that Teo was able to transition from accounting to digital forensics. This shows that there are many different paths to success, and that you don’t have to be an expert in a particular field to start working in it.
I was also impressed by Teo’s ability to adapt to new technologies. Digital forensics is a constantly evolving field, and Teo has been able to stay up-to-date on the latest trends. This is an important skill for anyone who wants to have a long and successful career.
Overall, I think Davin Teo is a role model for anyone who is considering a career in digital forensics. He is a talented and dedicated professional who has made a significant contribution to the field.