System monitoring and the use of network traffic log files are extremely important for gauging baseline performance and observing events. Why does identifying abnormal behavior first require having a baseline? What can a log file show that lends insight into abnormal behavior?
System monitoring and network traffic log files play an important role in several ways. Monitoring establishes a baseline for normal system behavior, identifying anomalies indicating threats or issues. Real-time monitoring ensures haste issue detection, decreasing downtime. Network log files, vital for detecting and addressing security breaches, also aid forensic investigations after an incident. These logs, essential for regulatory compliance, provide an auditable activity trail. Administrators maintain performance by analyzing system resource utilization through informed upgrades and configurations. Long-term monitoring can reveal system usage trends, guiding future infrastructure decisions.
Identifying abnormal behavior is crucial for several reasons. First, it establishes a benchmark distinguishing between regular operational variances and actual anomalies. This ensures objective and consistent judgments on abnormalities and prevents biased or personal interpretations. By defining a baseline, one can measure the extent of deviations, thereby highlighting the seriousness of the abnormality. This understanding helps us avoid reacting unnecessarily to typical system fluctuations and ensures we direct resources optimally toward genuine concerns. Furthermore, with a clear distinction between expected behaviors and anomalies, it becomes possible to initiate swift and targeted responses, enhancing the efficiency of system management.
Log files offer invaluable insights into abnormal behavior. They track login attempts, flagging unauthorized access, monitor data transfers, identify potential breaches, report unusual error messages and system changes, hinting at vulnerabilities, observe access timings, catch suspicious off-hour activities, and record resource spikes, suggesting malware. They also pinpoint unfamiliar connection sources, alert to deviations like atypical command sequences, and track irregular in-app activities. Security logs directly highlight threats. By assessing these logs, IT professionals can promptly tackle abnormal behaviors, ensuring system security.
What are the benefits and risks of the use of SSO? Specify measures that can be taken to better secure an SSO system.
Single Sign-On (SSO) epitomizes an authentication standard that allows users to access numerous applications and websites through a single set of credentials. While it does simplify management of accessing numerous resources, this approach also creates assorted security concerns. An exploration of the Risks and Benefits of SSO is warranted to elucidate the best course of action to secure such a system better.
Single Sign-On (SSO) offers several benefits, including improved convenience and efficiency, as users only need to remember one set of credentials, leading to increased productivity and reduced IT costs by simplifying user account and password administration. Moreover, SSO can enhance security by reducing the likelihood of password reuse or writing down passwords, thus mitigating the risk of breaches. However, it also entails certain risks, such as serving as a single point of failure if compromised, necessitating robust security measures for the SSO system. Additionally, phishing and man-in-the-middle attacks pose threats, emphasizing the importance of user education on avoiding phishing attempts and using cryptographic protocols like HTTPS and TLS for all SSO communications.
To fortify the security of a Single Sign-On (SSO) system, it’s essential to recognize the importance of each measure in mitigating specific security risks. Employ cryptographic communication protocols, such as HTTPS encryption, to shield user credentials from interception during transmission. Regular security audits are crucial for identifying and proactively addressing vulnerabilities within an SSO system, minimizing the risk of data breaches and unauthorized access. Strengthen authentication with multi-factor authentication (MFA), requiring users to provide multiple verification elements like solid passwords and one-time mobile device codes to enhance security. Ensure software and security patches are regularly updated to prevent exploitation of known vulnerabilities, as outdated software can expose organizations to significant risks. Lastly, prioritize user education in SSO security best practices, including strong passwords and awareness of phishing threats. Through these measures, organizations can bolster the security of their SSO systems, safeguard sensitive data, and mitigate the potential risks associated with unauthorized access and cyberattacks, leveraging resources from reputable cybersecurity experts for more in-depth guidance.
The decision to escalate incidents to law enforcement is an area fraught with conflict. In your opinion, what are the pros and cons of law enforcement involvement? What resources and references can you cite to back up your assertions?
Maintaining sensitive data and responding to security incidents is overseen by intricate legal and regulatory frameworks that mandate organizations safeguard data, report breaches, and preserve privacy. Despite this, the involvement of law enforcement presents some challenges, including jurisdiction and privacy concerns.
Cybercrimes often transcend international borders, making it difficult to determine which jurisdiction holds responsibility for investigating and prosecuting an incident, leading to response delays and hindering efforts to bring perpetrators to justice. In addition, law enforcement investigations often require extensive data collection, which raises important questions about balancing security and privacy.
Due to this, organizations must weigh the potential risks and benefits before involving law enforcement in a cybersecurity incident. Law enforcement can be crucial in responding to cyber incidents, offering expertise and resources to investigate intricate crimes and trace culprits. In some cases, they may facilitate data recovery and mitigate the impact of breaches, making their involvement indispensable.
Despite this, organizations must make well-informed decisions by considering the severity of the incident, consequences, resources, and legal obligations and by having an indepth understanding of law enforcement’s role and limitation.
Further Reading:
https://www.fairinstitute.org/Links to an external site.
https://www.nist.gov/cyberframeworkLinks to an external site.
https://www.policechiefmagazine.org/cybersecurity-an-emerging-challenge-for-all-law-enforcement
https://www.csoonline.com/article/575329/law-enforcement-crackdowns-and-new-techniques-are-forcing-cybercriminals-to-pivot.html
What is the best value that should be assessed when evaluating the worth of an information asset to the organization – replacement cost or lost income while repairing or replacing? What is the likelihood value of a vulnerability that no longer requires consideration?
The total cost of ownership (TCO) is the best value to assess when evaluating the worth of an information asset to an organization. TCO includes both the replacement cost and the lost income while repairing or replacing the asset.
The replacement cost may be more relevant for non-critical systems that can be easily replaced. However, for critical systems essential for operations, the lost income associated with downtime may be far greater than the replacement cost.
The likelihood value of a vulnerability that no longer requires consideration is zero. However, the likelihood of a vulnerability can change over time. Therefore, it is important to regularly reassess the likelihood of vulnerabilities in the organization’s risk management strategy.
Further Reading
https://www.investopedia.com/terms/t/totalcostofownership.aspLinks to an external site.
https://nvlpubs.nist.gov/nistpubs/legacy/sp/nistspecialpublication800-30r1.pdfLinks to an external site.
https://www.hhs.gov/sites/default/files/ocr/privacy/hipaa/administrative/securityrule/nist800-30.pdfLinks to an external site.
https://www.techtarget.com/searchdatacenter/definition/TCO
Describe some actions or techniques that can be used to mitigate or stop the impacts of malicious applications. Are some of these methods more effective than others? Provide an example of a cyber attack that resulted from the execution of malicious code. There are plenty of examples that can be queried from the Internet.
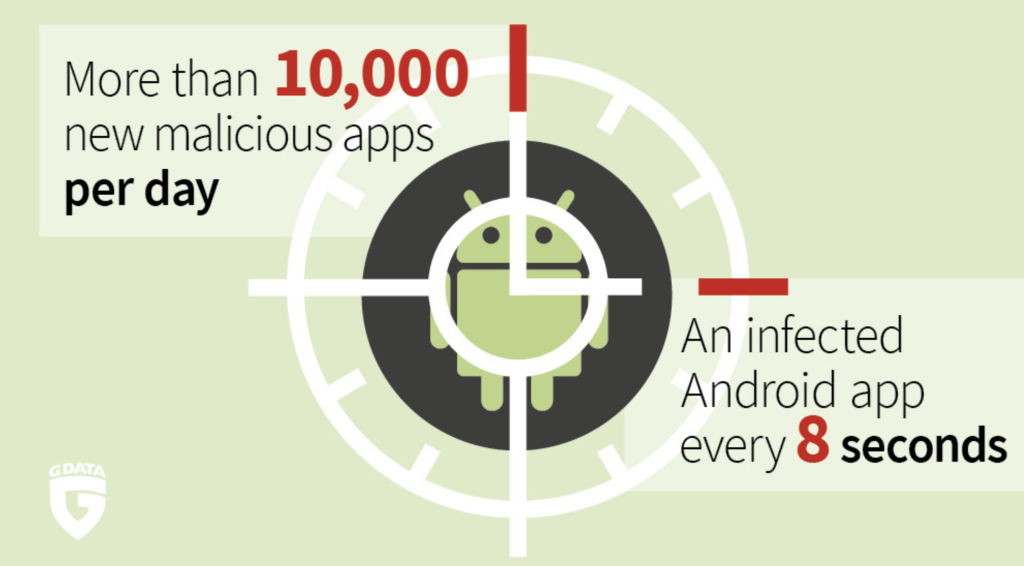
Malicious applications can have a devastating impact on organizations of all sizes. To mitigate these risks, a layered approach encompassing prevention, detection, and response is essential. Prevention is the most effective means of protection, involving measures such as installing updated antivirus and anti-malware software, applying security patches, using strong passwords with multi-factor authentication, and exercising caution with links and downloads.
Despite best efforts, no system is entirely impervious to threats. Therefore, detection and response strategies are critical. Detection mechanisms such as SIEM systems, regular audits, and IDS/IPS can identify breaches when they occur. Without these mechanisms, breaches can go undetected for extended periods, magnifying their impact.
Once a breach is detected, an actionable response plan is paramount to contain and recover from the attack. The WannaCry ransomware incident, which exploited unpatched systems to devastating effect, highlights the importance of proactive measures such as system updates and backups, as well as responsive actions such as disconnecting infected systems and scanning for malware.
While prevention offers the first line of defense, a comprehensive security posture demands robust detection and swift response capabilities to manage and recover from incidents that may bypass preventative measures.
https://www.cisecurity.org/controlsLinks to an external site.