Experience
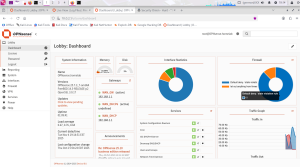
Home Lab Architecture & Operations
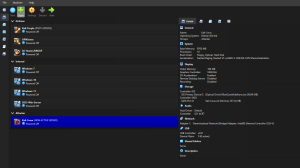
Designed and configured a multi-network virtualized cybersecurity lab using Oracle VirtualBox to simulate real-world attack and defense scenarios. The environment includes multiple operating systems—such as Kali Linux, Kali Purple, Parrot OS, and several Windows versions—segmented into dedicated offensive, defensive, and vulnerable networks.
Key Skills & Accomplishments
-
Built and maintained isolated subnets to emulate enterprise-grade network segmentation.
-
Deployed virtual machines for penetration testing, network monitoring, blue-team analysis, and incident response.
-
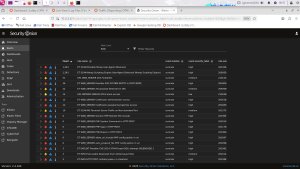
Implemented log monitoring, firewall controls, and baseline hardening for realistic risk management.
-
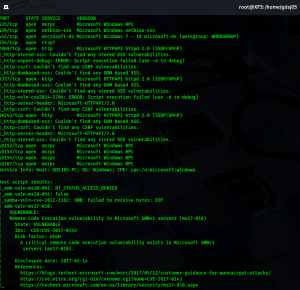
Conducted controlled vulnerability assessments and exploitation using tools such as Metasploit, Nmap, and Burp Suite.
Outcome
Created a safe, fully functional environment for hands-on training in penetration testing, SIEM operations, network defense strategies, and adversarial simulation—all without risking production systems.
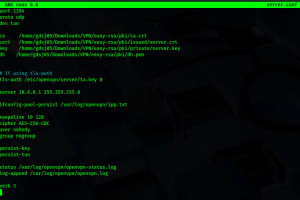
Secure VPN Tunnel & SSH Server Configuration
Project: Built and troubleshot a multi-client OpenVPN environment (Windows Client ↔ Kali Linux Server).
Configured a certification-based VPN using Easy-RSA with custom encryption (AES-256-CBC) and authentication (SHA-256). Tuned server and client parameters to ensure successful tunnel negotiation and prevent TLS handshake failures.
Skills & Lessons Learned
-
VPN Configuration & PKI Management: Generated certificates, keys, and revocation lists using Easy-RSA; configured OpenVPN server and client profiles.
-
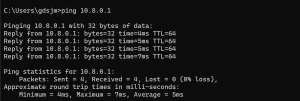
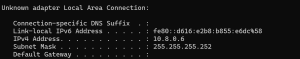
Network Troubleshooting: Diagnosed routing, DNS, VM networking (Bridged/NAT), and firewall issues causing connection failures.
-
Security Best Practices: Implemented strong ciphers, TLS-auth keys, proper key lifecycles, and hardened server configurations.
-
Systematic Debugging: Analyzed logs to resolve cryptographic mismatches, authentication failures, and configuration errors.