I’ve compiled five photos on this page depicting my thoughts about cybersecurity and the social sciences. I’ve also embedded a video related to the topic directly into my ePortfolio.
Photo 1 Description – Group of people using social media with thought bubbles:

Photo 1 Caption – Our online behavior can be tracked and used to target us with cyberattacks.
Photo 2 Description – Person at the computer with a hacker looking over their shoulder:

Photo 2 Caption – We are all vulnerable to cyberattacks, regardless of our technical expertise.
Photo 3 Description – Computer screen with a virus warning message
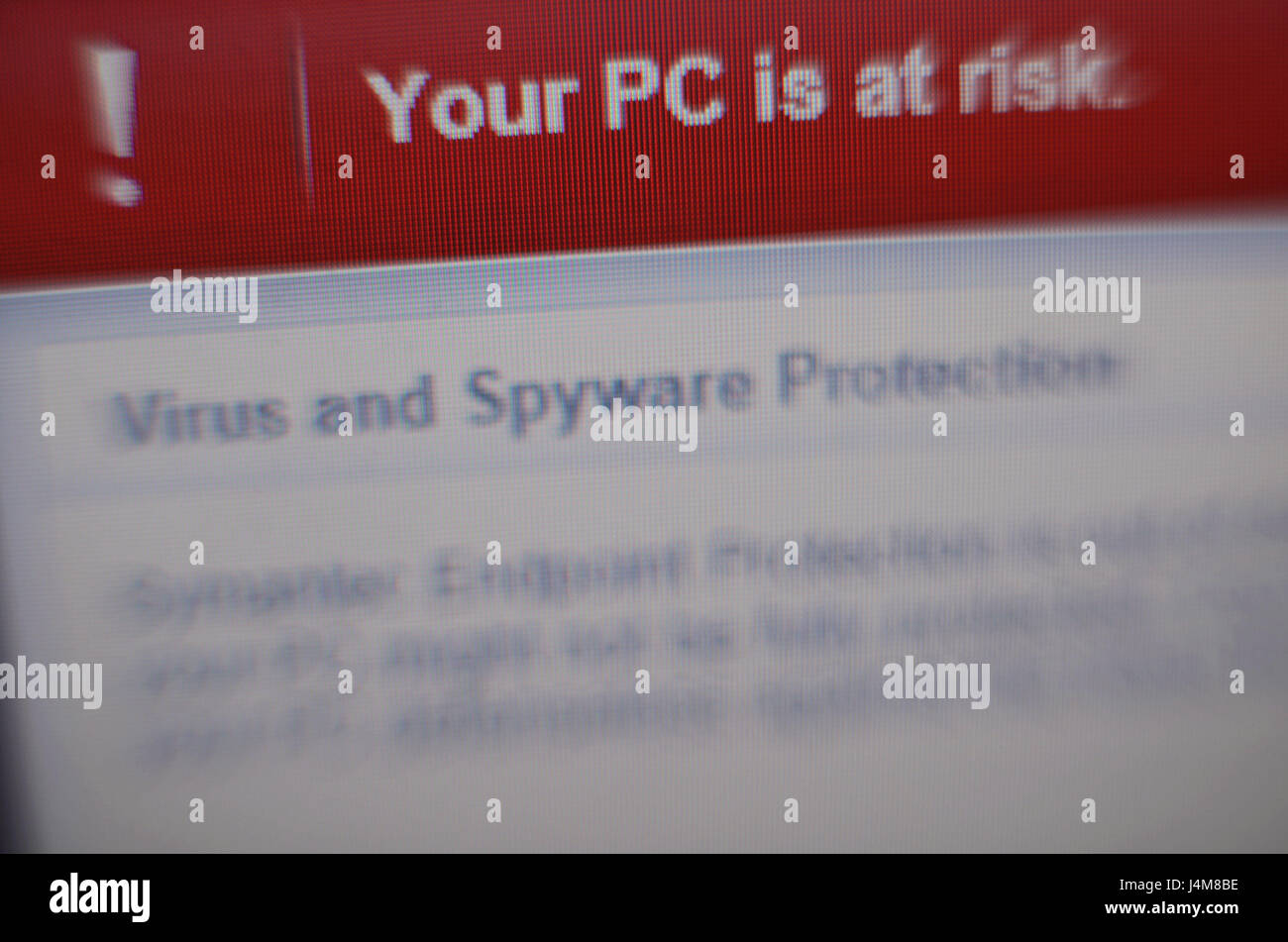
Photo 3 Caption – Cyberattacks can significantly impact our lives, both personally and professionally.
Photo 4 Description – Group of people protesting against government surveillance

Photo 4 Caption – Cybersecurity is a complex issue with social and political implications.
Photo 5 Description – Child learning about cybersecurity in school

Photo 5 Caption – Cybersecurity education empowers individuals to protect themselves online.
Video Description – What is Social Engineering? | Proofpoint Cybersecurity Education Series
References
B Christopher / Alamy Stock Photo. (2013, October 25). Washington, DC USA. 26th
Oct, 2013. : Thousands of citizens and many public advocacy organizations
gather to rally on Capitol Hill in protest, resulting from recent reports of domestic
and international surveillance by the NSA © B Christopher/Alamy Live News.
Alamy Stock Photo. https://www.alamy.com/washington-dc-usa-26th-oct-2013-
thousands-of-citizens-and-many-public-image62037536.html?imageid=
FEA92C43-8DA7-4B85-B60E-41F61813BEE8&p=67200&pn=1&
searchId=9b74d640c491a9a4a615e80885de2cab&searchtype=0
melita / Alamy Stock Vector. (2020, March 1). Group of diverse people with speech
bubble. Social network. Communication and sharing. Crowd talking. Share ideas.
Multi-ethnic people who talk.Speak. Alamy Stock Photo. https://www.alamy.com/
group-of-diverse-people-with-speech-bubble-social-network-communication-and-
sharing-crowd-talking-share-ideas-multi-ethnic-people-who-talkspeak-
image345725140.html
Milans5. (n.d.). Rear view, one young man, 20-29 years old, sitting, using computer, on
the web. looking at images at his home, in his room. Dreamstime. https://www.
dreamstime.com/rear-view-one-young-man-years-old-sitting-using-computer-
web-looking-images-his-home-his-room-desk-w-rear-view-one-image143403808
PA Images / Alamy Stock Photo. (2017, May 12). A virus and spyware warning
message on a laptop screen at a home in London, following a major cyber attack
on NHS computer systems. Alamy Stock Photo. https://www.alamy.com/stock-
photo-a-virus-and-spyware-warning-message-on-a-laptop-screen-at-a-home-in-
140587202.html
Proofpoint. (2019, August 14). What is Social Engineering? | Proofpoint Cybersecurity
Education Series . YouTube. http://www.youtube.com/watch?v=9U-JgdUkaTQ
Wallace, F. (2020, September 18). Teaching Cybersecurity to Kids. United States
Cybersecurity Magazine. https://www.uscybersecurity.net/teaching-cybersecurity-
to-kids/