The NICE Workforce Framework provides a amazing way to explore cybersecurity careers and match them with personal interests. I’m especially drawn to Systems Security Analysis and Technology Research and Development because they focus on identifying vulnerabilities and exploring cutting-edge solutions to enhance cybersecurity. These areas excite me because they’re fast-paced, require creative problem-solving, and allow me to stay ahead of new threats. On the other hand, Database Administration doesn’t appeal as much to me. While it’s vital for securing data, it feels more routine and less engaging compared to roles that involve innovation and analysis. I appreciate how the NICE Framework helps break down the options, making it easier to see where my passion and skills fit best.
Entry 2
Entry 2- I believe when protecting systems from cyber threats, we draw on principles that have been tested in science. Empiricism reminds us to rely on data and real-world evidence, ensuring our decisions are based on facts rather than assumptions. Determinism helps design predictable systems, enabling the development of consistent security measures. Parsimony encourages simplicity, urging us to avoid unnecessary complexity that could introduce vulnerabilities or errors. Objectivity ensures that our assessments are unbiased and based on facts, allowing for clearer evaluations of risk. By applying these principles in cybersecurity, we can strengthen defenses, adapt to new challenges, and maintain resilience. This approach helps us stay one step ahead in an ever-changing and unpredictable cyber landscape.
Entry 3
I believe with cyber threats on the rise, understanding data breaches is more important than ever. Websites like PrivacyRights.org provide researchers with valuable information to analyze breach trends, uncover vulnerabilities, and assess the overall impact on businesses and consumers. By examining the types of breaches, affected industries, and the number of compromised records, researchers can identify patterns that help improve cybersecurity strategies. This data also aids policymakers in crafting stronger regulations to protect sensitive information. Additionally, studying breaches allows researchers to explore how they influence consumer trust and corporate security policies. With this knowledge, organizations and individuals can take proactive steps to strengthen data protection and minimize future risks. For instance, the 2017 Equifax data breach compromised the personal information of approximately 143 million Americans, including Social Security numbers, birth dates, and addresses. This incident underscores the critical need for robust cybersecurity measures and provides a case study for analyzing the consequences of inadequate data protection.
Entry 4 –
From Maslow’s perspective of the Hierarchy of Needs, it connects to cybersecurity in various ways. Physiological needs include reliable internet access along with secure cloud storage to facilitate online banking or remote work. Safety needs are met through firewalls, VPNs, and encrypted messaging which is kept super resilient against cyber threats to protect sensitive information. Human love and belonging are promoted through secured interactions on social media, and also private messaging ensures safe communication with friends or family members. Esteem needs are met through successfully identifying and preventing cyber threats, killing a phishing attempt, bolstering one’s confidence, and enhancing professional credibility. Self-realization is achieved through creating awareness of cybersecurity, such as teaching others about online safety or developing security measures that protect the digital sphere.
Entry 5-
The most common motive of cybercrime is money, where hackers, fraudsters, and ransomware victims use computer systems for financial gain. Political motives come next in line, with hacktivists, cyber attacks to promote ideologies in cyber invasions, and disruptions of governments. Revenge stands out as another major motive for target on others using cybercrimes, such as in the case of revenge porn. Some hackers are intent on recognition characterized by notoriety or respect within the online communities. Some have multiple motives, stacked one on the other, blending financial, political, or personal reasons. Examples of entertainment-driven cybercrime would include data scraping just for fun, which, though not justifiable, are still harmful. Boredom stands out as the least justifiable form of motivation, as a result of boredom, mainly cyberbullying, online harassment, or other destructive actions ensue. Every single cybercrime has negative impacts, however, financial, political, and personal motives predominate in their frequency, and they readily attract common understanding, unlike the indispensable aspects found in entertainment or idiocy.
Entry 6-
Comparison of fake vs real websites
3 Fake Websites:
- example-fakebank.comBackground: Mimics a well-known bank to steal login credentials and personal data.Indicators of Fraudulence: Unusual URL: Slight alterations (e.g., hyphens, different top-level domains).Poor grammar and design: Spelling errors and unprofessional layout.
- cheap-medicines-online.com Background: Poses as an online pharmacy offering prescription drugs at extremely low prices. Indicators of Fraudulence: Absence of regulatory seals: Lacks proper certifications from recognized health organizations. Unsecured website: Uses HTTP instead of HTTPS, indicating weak security.
- win-a-luxury-vacation.comBackground: Promises extravagant vacation giveaways in exchange for personal details. Indicators of Fraudulence: Vague terms and unclear deadlines: No transparent rules for participation. Overexaggerated claims: Unrealistic offers designed to lure users into sharing data.
3 Real Websites:
- truist.com (Legitimate banking website) Secure URL (HTTPS) with a padlock icon. Professional design and branding.
- roblox.com (Authentic gaming platform) Consistent branding and user-friendly navigation. Official contact details and policies.
- fortnite.com (Verified game website) Clear terms of service and privacy policies. Uses HTTPS for secure transactions.
| Feature | Fake Website | Real Website |
|---|---|---|
| URL | Slightly altered, suspicious, has fake letters | Clear, matches the official brand |
| Security | Generally HTTP, lacks SSL encryption | HTTPS, secure connection |
| Design and Usability | Poor design, inconsistent layout | Professional design, user-friendly |
| Regulatory Compliance | No legitimate seals/approvals | Displays relevant certifications |
| Information Transparency | Vague terms, lack of contact info | Clear contact details, transparent |
| Claims | Too good to be true | Realistic and verifiable offers |
key differences between fake and real websites
I believe to detect these fake websites, users can check for the right URL, secure HTTPS connection, and site design and usability. However, trusted sources such as Norton LifeLock, FTC Consumer Information, and CISA provide additional guidance on scams and ways to protect personal information.
Citations:
- Norton LifeLock. (n.d.). “How to Spot a Phishing Website”. Retrieved from Norton.
- Federal Trade Commission (FTC). (n.d.). “Shopping Online”. Retrieved from FTC.
- Cybersecurity and Infrastructure Security Agency (CISA). (n.d.). “Phishing Campaigns”. Retrieved from CISA.
Entry 7-
A developer such as this person enjoys the freedom of working remotely, soaking in the beautiful
sunset and cityscape whilst typing away on the laptop. They could be working on an urgent
project, trying to finish the assigned tasks ahead of deadline, or just tap a bit into the flexible
lifestyle that remote work offers. In their engrossed work half-aware of surroundings, they could
be ignoring the cybersecurity risks of their environment. They might be inadvertently connected
to an unsecured, public WiFi network where their data is most likely exposed to hackers. Their
login credentials, emails, and private company information might be at risk because, at this
moment, there are more pressing priorities other than security.
Connection- Human-centered cybersecurity is about the awareness raised combined with easy-
to-use security tools. One should guide the users to practices such as using VPNs, encryption,
and 2FA. The security in place should be intuitive and embedded into the work environment, so
users don’t have to choose between convenience and safety.

This person is all about writing or debugging code.
They tend to concentrate very hard on getting things right: improving security measures to fix
some vulnerabilities or to ease efficient functionality of the system. Yet sometimes, prolonged
overconcentration can practically lead to the wrong turn when there is no sustained propagation
of security best practices.
Connection- In the area of human-centered cybersecurity, secure programming is a core
principle. Developers must have security in mind from the conception point, ensuring that they
build systems to safeguard users against threats such as SQL injection, cross-site scripting, and
other forms of cyber risks.


This meme is about forgetting or not knowing the password.
Each time, trying to remember yet another, this time, a more complex password becomes an
ordeal, most of the time resulting in insecure practices such as password reuse or writing the
passwords down. Human-centered cybersecurity looks at various designs of security practices
and systems that are intended to cater to human behavior, such as the use of passphrases or
password managers and even multi factor authentication, to increase security without creating a
burden on the users.
Entry 8- https://www.youtube.com/watch?app=desktop&v=6BqpU4V0Ypk
In this video the way the media has covered cybersecurity shapes how we think about it. While news stories about major data breaches and cybercriminals create urgency, they often focus on the extremes rather than the common threats. This can lead people to view cybersecurity threats as problems for others, not personal to them. Although attention-grabbing reporting is engaging, it may sometimes cloud more valuable content about protecting personal information. Conversely, the public can be empowered to practice safer use of technology when journalists provide factual and informative content. When it comes to confronting cyberthreats, it is important to have an informed public, and responsible media engagements afford that opportunity.
Entry 9- https://www.youtube.com/watch?v=Zbqo7MGVElw
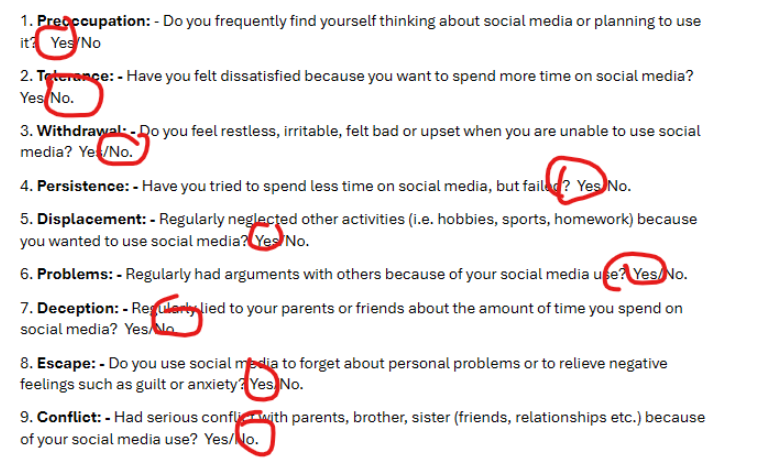
The scale helps examines a range of issues, which include, but are not limited to, preoccupation, withdrawal, deception, and social conflicts associated with risky overuse. Social media use can manifest qualitatively and quantitatively in different ways in various parts of the world because of cultural norms, accessibility of internet services, economic dependency on these services, and government laws and regulations. Some cultures promote social interaction, others promote face-to-face engagement.
I believe cybercriminals can take advantage of social media activity in many ways, including, but not limited to, phishing attacks, identity theft, social engineering and doxxing. The more personal information that is shared online, the more vulnerable someone may be to scams, fraud or harassment. I also believe that thinking about these issues can help people understand this context and critically reflect on their social media use and enhance their digital well-being and safety and security.
Entry 10- https://www.armyupress.army.mil/Journals/Military-Review/English-Edition-Archives/Mar-Apr-2019/117-Cybersecurity/b
Beskow and Carley in Social Cybersecurity point to a vital link between societal behavior and cybersecurity, arguing that technical defenses alone will not do against the contemporary onslaughts. Control of such threats requires the merger of insights from social science with technical approaches, so work against problems like misinformation and influence campaigns can be accomplished. The article pertinently makes the case that adversaries manipulate social structure and psychological vulnerabilities to sway public opinion and destabilize societies. Hence, understanding and mitigating such threats require an interdisciplinary approach that takes into account computational modeling, behavioral analysis, and policy interventions. An especially relevant point is the disproportionate effects of exploitation through cyberspace on already marginalized communities. This is also pertinent within wider conversations about systemic deprivation regarding access to information and education in digital literacy, indicating that inclusive strategies in cybersecurity are essential for addressing these inequalities. Authors using data-driven techniques such as network analysis and machine learning for threat pattern detection stress the importance of combining technological tools with knowledge of human behavior to better identify and counter cyber threats.
Beskow and Carley also suggest encouraging collaboration among social scientists, cybersecurity practitioners, and legislators to develop proactive measures; public education initiatives are also emphasized to help users develop their critical thinking and digital resilience. Overall, Social Cybersecurity is an insightful and topical article that argues for the urgent need for a comprehensive understanding of cybersecurity by examining the complex interactions between social dynamics and digital vulnerabilities. In order to continuously reduce the risks associated with social threats to cyber security, interdisciplinary research and public awareness are essential.
Entry 11- https://www.youtube.com/watch?v=iYtmuHbhmS0
I believe that cybersecurity has a significant impact on how social and economic opportunities are shaped in the connected world of today. The presentation focuses on issues like workforce accessibility, digital inequality, and the moral ramifications of cyberthreats. It emphasizes how the increasing need for cybersecurity experts brings with it both opportunities and difficulties, especially for underrepresented groups who might encounter entry barriers because of financial and educational limitations. The conversation also considers the wider social duty to preserve digital security, since cyberthreats impact not just big businesses but also people in their daily lives. A social divide is also revealed by the emphasis on certifications and ongoing education, where those with resources can progress in their careers while others may find it difficult to keep up. In the end, the presentation shows how cybersecurity is a social issue that affects digital ethics, personal safety, and economic mobility in addition to being a technical one.
Entry 12- https://dojmt.gov/wp-content/uploads/Glasswasherparts.com_.pdf
I believe that the recent data breach shows some important stuff from economics and psychology. On the economic side, it’s a case of information asymmetry. The company and its platform provider knew about the breach long before they told customers, which left people unable to protect themselves in time. Customers also face negative effects, like dealing with fraud risks and spending time replacing cards, even though they didn’t cause the breach. From a psychological angle, prospect theory helps explain why customers might freak out over the potential loss of their personal and financial data. People usually react more to losses than they do to gains. Trust theory is also a big deal here and when breaches happen and communication is slow, it can really hurt a customer’s trust in a brand. Overall, this situation really highlights the need for clear, timely communication and good data protection.
Entry 13-https://academic.oup.com/cybersecurity/article/7/1/tyab007/6168453?login=true
I believe digital threats becoming a bigger worry for our national systems, makes it crucial to understand how people feel about cybersecurity policies. The article Cyberattacks, Cyber Threats, and Attitudes Toward Cybersecurity Policies looks into how different cyberattack scenarios affect public support for government measures to keep us safe online.
The review of past research lays a solid groundwork, pulling from political psychology and security studies. It points out that people’s support for security policies isn’t just about the threats themselves, but how those threats are framed especially regarding how serious they are and the risk they pose. The study compiles previous research and identifies a lack of understanding about how people react to cyber threats compared to more traditional forms of violence. When discussing their findings, the authors share that how we perceive threats plays a big role in shaping our views on policies. When it came to non-lethal attacks, people tended to favor more balanced oversight and less intense regulations. This difference in reactions to lethal versus non-lethal threats is really interesting. It indicates that support for tough cyber policies isn’t uniform and can change based on how the threat is presented emotionally and psychologically. This has important implications for how policymakers talk about cyber threats and explain new rules. The study provides solid insights into how our perceptions of threats relate to our support for policies in today’s digital world. It raises important questions about finding the right balance between security and freedom, and how the way cyber incidents are described can influence public opinion.
Entry 14-
I believe that Andriy Slynchuk pointed out that a significant number of internet users unwittingly engage in illegal activities, despite the serious consequences they can have. Collecting personal information about children is a violation of child protection laws and can lead to potential abuse. Another major concern is the impersonation of others on the internet, which is frequently used to defraud or scam people, causing harm to victims both financially and emotionally. If you are not willing to share someone’s personal information or photos, it can result in harassment or identity theft. In addition, unlawful searches such as investigating crime can draw the public’s attention and expose individuals to legal risks. In certain jurisdictions, recording VoIP calls without the other person’s consent may be considered a violation of wiretapping laws. The actions listed are not only against the law but also pose a threat to people’s safety, trust, and privacy, making them particularly grave cyber attacks.
Entry 15- https://www.youtube.com/watch?v=Pf-JnQfAEew
In this video the path to entering digital forensics as described in Davin Teo’s TEDx talk reveals the tight links that digital forensics maintains with the social sciences domain. Openly demonstrating his financial expertise Teo started his work life as an accountant of economic and financial background. His work as an accountant gave him useful insights when he joined digital forensics which proved crucial during financial crime and fraud investigations. To practice digital forensics successfully a professional needs both advanced technological competence and comprehensive knowledge of human activities alongside social patterns together with ethical standards. The analysis of digital evidence for behavioral interpretation and motive interpretation from Teo matches the methods employed in psychology and sociology studies. The investigations require him to skillfully handle technical components together with understanding human behaviors thus demonstrating the cross-disciplinary nature of his work. The most exciting aspect of Teo’s career path demonstrates the significance of using different academic perspectives to excel in digital forensics. The example of his career shift shows that forensic investigators need skills from both accounting and social sciences to solve difficult digital crimes. This expanded understanding of digital forensics changed my perspective to view the field beyond technical computing functions because it combines analysis of human behavior beside computer forensics work. In his experience he demonstrates that professionals seeking digital forensic careers should welcome different educational paths because these diverse backgrounds offer practical methods to study human aspects of digital evidence examination