Week 1 Journal Entry –
When I looked into the Cybersecurity NICE framework, I saw some things I am strong in
and some that I lack. With the career I’m striving to achieve, I want to be stronger in a few things
to have a better chance of getting it. The roles that I will be good in are protection and defense.
The roles like incident response, Infrastructure support, and Insider threat analysis will be in my
better categories because I prefer to work with the defense, and my skills would be perfect there.
I would be the least helpful in oversight and governance because of the company’s management
and product, and I would not be a good help in that role.
Week 2 – Journal Entry 2 –
Today, I will discuss the different science principles and how they relate to cybersecurity. As we went
through the modules, I realized that they all can deal with cybersecurity in their way. Parsimony can
relate to cybersecurity because it can simplify how humans approach cybersecurity attacks and create a
theory from it. Empiricism related to cybersecurity is that we can study previous attacks and then use the
experience in our next defense when another attack emerges. Determinism can relate to cybersecurity,
which is when we figure out the cause of the behavior or attack and determine our following action
toward it.
Week 3 – Journal Entry 3 –
While going through these websites and looking under the headings, I found out they can use
this information about data breaches to study the findings and when the breach happened or
was born. There are also many different reports up here from many different breach attacks,
and you can find a pattern or a way the breaches are coming from to have a precautionary
measure or be proactive about the situation. Researchers can also use this information to study
the effects or impacts of the breach on organizations, companies, and individuals. Overall, this
can help keep information safe when a breach happens or when our security is at risk of getting
broken from the inside or out.
Week 4 – Journal Entry 4 –
While reading Maslow’s hierarchy of needs, I was given thoughts on how it can relate to my
experience with technology. Self-fulfillment can connect with my level with technology by
reminding me of my struggle with using computers and achieving my experience with them.
Safety needs with my technology include putting on ad blockers and adding firewalls to my
laptop to keep files and information safe. Esteem needs, when it comes to my experience with
technology, is when I’m stressed while on the computer, I try to either take a walk or take time
away from the computer for Psychological needs.
Week 5 – Journal Entry 5
After reading the articles, the most reasonable reason why people commit cyber crimes and for
individual reasons is for Money. Everything revolves around money, and the world craves it. The
second one is for recognition; if you get enough recognition, you can be much more helpful to
other criminals and chip in on the crime they are trying to commit. The third reason is revenge;
maybe someone or a company has a grudge against it and wants to start a crime from it. The
final reason is entertainment, and nobody commits a crime for entertainment because there is
always a motive behind a crime, or it wouldn’t be caused in the first place.
Week 6 – Journal Entry 6
After looking and comparing these six websites, I separated these into two categories and using
my sources and my knowledge I was able to put them in their correct spots because all of them
are real ones and the fake ones have very different features behind them. For example, The
real websites have “https://” which means Hypertext Transfer Protocol Secure and it makes sure
you and the website you connected to is encrypted and secure with privacy, the fake ones do
not. The second thing I found was that the domain source name is not really telling us where it’s
going to take us when we click on it like the real ones do, and it’s important that we look closely
at that.
Fake websites
● NBCNews.com.com
● LiberalSociety.com
● Channel18News.com
Real websites
● https://www.microsoft.com
● NBC News – Breaking News & Top Stories – Latest World, US & Local News |
NBC News
● Norfolk News & Weather | Norfolk, VA | WAVY.com
Week 7 Journal Entry 7
This meme is about when you are in a cybersecurity position and you can travel anywhere, but all you do is sit there on your laptop. This relates to cybersecurity because we can be anywhere and still do our jobs, no matter where we are. We can be across the world and still be able to do our jobs.
This is a meme of 2 people looking at a laptop while an attack is happening. This relates to cybersecurity and the principles because we use the principles to not only figure out ways to prevent the attack from happening but we can use the scientific principles to keep these attacks from getting breached.
This is someone staring at their screen and there is codes up there. I chose this meme because it relates to how cybersecurity people in their positions are up there and sometimes they may be confused with certain codes they do and it may not work in the terminal. Reason why cybersecurity people need to be good at their job
Week 8 Journal Entry 8 –
After watching this video it tells me that social media plays a huge role in shaping the way we
look at the cyberworld. As we go through different clips of people hacking through, For example,
the “Ocean 8” uses a spearfishing attack to target individuals to something he is passionate
about which was the dog that was on his social media page. Another example of how they use it
is the analysis, Lisbeth hangs around people’s apartment places sees the codes puts them in to
get in and find specific hardware, and then uses a Nokia to take information and store it on it.
Week 10 – Journal Entry 9
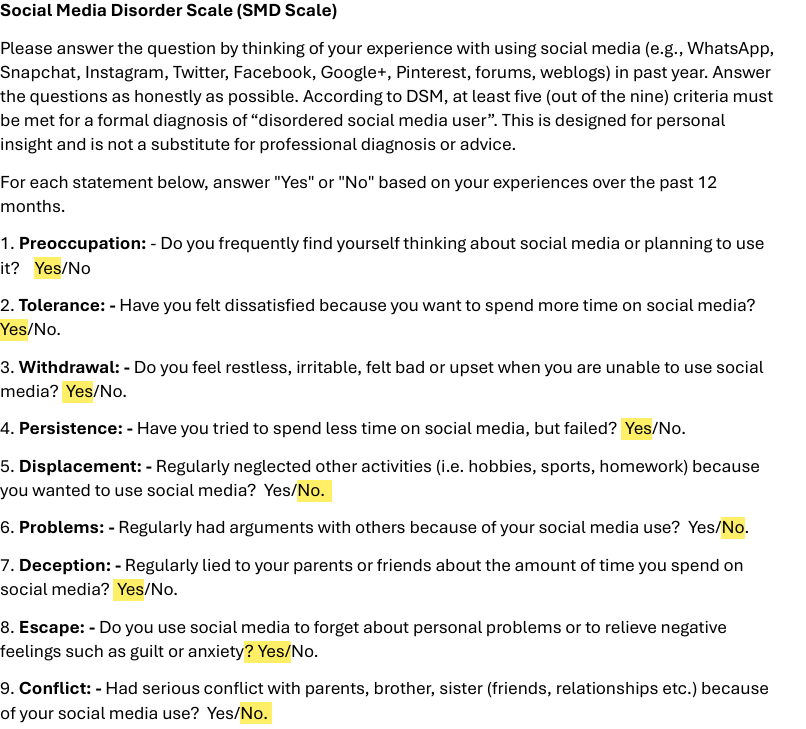
I scored 6/9 on the test and say that I have a problematic usage of it, but I do say it would be
less if I didn’t have such a procrastination problem. The items and the questions on the board
were so very specific, that anybody would a social media problem would feel offended because
it’s something that they cannot control and, we have all pretty much been in the same situation.
It’s different around the world because of the technology usage and how advanced technology
can be across the world. It can be different from a place like Japan to a place like Switzerland
for example because of the many different things they have in their country.
Week 11 – Journal Entry 10 –
After reading the article, talks about cybersecurity within the military. It describes different
usages of it and talks about the self-resilience within the defense of the network and security
system. In reading it, they talk about examples and different strategies on how to protect
sensitive information while having high integrity in the military. A part where they talk about
training their soldiers on social awareness within the cyber world and putting in a defense
mechanism to keep their security up is a very essential step to have. Finally having partners in
the private sectors around the world can also be beneficial because it can help our defense be
even better than before.
Week 11 – Journal Entry 11 –
After finishing the video I found out that a lot of social behaviors can impact us while having a
Cybersecurity Analyst job. Being in the Cybersecurity field not only just comes with technical
skills, you need to have social awareness to communicate with your team or co-workers. You
often work in teams to develop different strategies against cyber attacks so you can keep your
defense up but prevent them from coming through from security breaches. Understanding social
and human behaviors is very important because we can have an attack on the team because of
our mental weaknesses and social engineering.
Week 12 – Journal Entry 12 –
After reading this article and seeing what has happened, I concluded that there are two theories
and social sciences that are being used here. The two theories that are being used in this article
are Marxian and the Laissez faire economic theory. The Marxian used its power to gain control
over the weaker individuals and the Lassiez uses its “economy should not interfere” to protect
individuals. The two political science they use is with social proof to show that they is being
hacked by the website and cant get their information and cyber phishing to get scammed with
the fake website.
Week 12 – Journal Entry 13 –
After reading this article and seeing what it’s about, I came up with a short summary of this. This
article was about a review on a program called “bug bounty” and it was there to help explore
and highlight their findings from their effectiveness and their strengths in helping increase their
defense in cybersecurity. There was a certain data that was reducing their vulnerabilities called
“HackerOne Data” and it was affecting it while they were trying to collaborate between other
organizations and hackers. The programs not only help trying to increase and enhance our
cybersecurity defense but also create some sort of structure for the future of cybersecurity.
Week 13 – Journal Entry 14 –
After reading the Article, here are five what I think are the most serious violations.
● Collecting Information about People Younger Than 13
● Bullying/Trolling
● Faking your identity online
● Recording a VoIP Call without consent
● Sharing passwords, addresses, or photos of others
I feel like these 5 things are serious offenses because they can lead to serious Jail time.
Collecting information about younger people can give a huge jail time, and people will
call you an internet pedophile. Bullying/Trolling can cause kids to have serious
depression and might even commit suicide. Faking your ID online can lead to serious
consequences and might even affect the way people look at you, even if it’s a fake.
Recording calls can lead to the spreading of false information and gathering, and maybe
editing the recording. Sharing personal information on the internet is the number one
thing that you should never do because it can be leaked and you dont know who has
your information or what they can do with the information.
Week 15 – Journal Entry 15 –
After watching this video, I gained insight into what forensic investigators do and an
understanding of them. From what I’ve seen, I notice that it can relate to social science because
it can relate to human behavior. We can use it to help analyze the sense of communication,
online activities, and transactions that approve on this behavior behind closed doors. Not only
must investigators use their technology skills, related to their data recovery, along with the legal
framework. It’s been concluded that a digital forensic investigator is deeply connected with
social science, as it involves the combination of technical and social experiences.