SCADAS systems play a key role in managing important services in various industries, but
they’re facing more cybersecurity threats. By knowing where the weaknesses are and using
updated strategies, organizations can lower risks and improve their overall operations.
Infrastructure Operations and Its Relation to SCADA
Supervisory Control and Data Acquisition (SCADA) systems play a key role in controlling and
monitoring essential infrastructure sectors including energy, water, and transportation [Type of
industry. SCADA Systems which according to SCADA Systems document provided with the
course connects different components including Human Machine Interfaces (HMIs), Remote
Terminal Units (RTUs) and Programmable Logic Controllers (PLCs), to monitor and control
assets that are distributed. Real-time, centralized visibility and control of complicated physical
processes is their core strength. SCADA architecture itself, with master-station configurations
and backup systems built in, is intended to minimize service interruptions for critical services.
The design focus for these systems was on reliability and uptime, with less emphasis on
cybersecurity, and as technology and threats have matured, this has created enormous risk.
SCADA and Infrastructure Systems Vulnerabilities
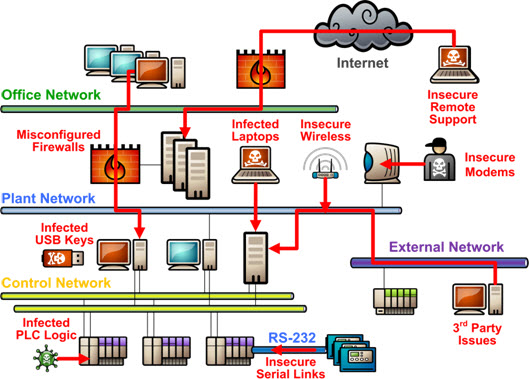
SCADA systems have become more vulnerable to cyber threats as infrastructure networks are
becoming more digitized and interconnected. This stems from two major issues: the vintage of
many SCADA deployments and the way the applications were designed. “Critical infrastructure
needs to be protected from cyber attacks. An article by Claroty about SCADA risk management
states that many systems/solutions continue to rely on reachback with legacy protocols like
Modbus, DNP3, etc, that were designed well-before encryption or authentication features were
considered.” Without these basic security controls in place, it can be easier for attackers to tap,
intercept, or otherwise manipulate communication between control devices. In addition, SCADA
networks often contain aged hardware and software that is out of date, out of date hardware and
software cannot be patched or upgraded to mitigate against a newly discovered weakness.
Physical security is even an issue as physical entry for attackers can be done by taking advantage
of unsecured access points into the control environment. When these systems are more tied to
IT networks and remote access interfaces, they become more susceptible to malware,
ransomware and unauthorized access. The Saturn Partners article, “The Next Generation of SCADA Systems: Is SCADA Obsolete?” talks about how SCADA platforms are changing to deal with new challenges, but they’re also bringing in some new issues. Many modern SCADA systems are moving towards using cloud tech, AI, and open standards. This shift makes them more flexible but can also make them less secure compared to older, closed systems. While these upgrades can lead to better efficiency and predictions, they do rely on a steady internet connection and more complex security measures,
which raises the risk and shows the need for solid cybersecurity planning.
SCADA and Risk Management
Even with some weaknesses, modern SCADA systems are getting better at handling
cybersecurity risks. These systems are now designed with more reliable setups, like backup pathways and automatic switches, so they can keep running even if some parts fail or get attacked. Having backup master stations and double communication paths really helps keep things running smoothly. To deal with communication issues, secure versions of the protocols are being used to ensure the data is authentic and protect against fake signals. Plus, modern SCADA systems are now using security tools to keep an eye out for unusual activity and notify operators if something looks off. Experts point out that using strategies like network segmentation, industrial firewalls, and better authentication can help lower the chances of a
major system breach. While SCADA systems weren’t initially built with security as a priority, they’re being updated to fit into a bigger cybersecurity picture. In summary, SCADA systems are crucial for critical infrastructure, and they need to change to meet increasing security challenges. Older protocols, outdated hardware, and more connections all bring risks to important operations. But with better designs, improved protocols, and careful monitoring, SCADA systems can keep doing their vital jobs while also helping to fend off modern threats. As technology becomes more complicated, SCADA’s future hinges on its ability to adapt and protect the systems we all rely on.
References:
Claroty. (2023). SCADA Risk Management: Protecting Critical Infrastructure. Retrieved from
https://claroty.com/blog/scada-risk-management-protecting-critical-infrastructure
Saturn Partners. (2025). The Next Generation of SCADA Systems: Is SCADA Obsolete?
Retrieved from https://saturnpartners.com/2025/01/the-next-generation-of-scada-systems-is-
scada-obsolete/
SCADA Systems. (n.d.). Supervisory Control and Data Acquisition (SCADA) Overview.
Internal Class Document.