For this course, I did network mapping, network security techniques and components, applications of cryptography, malicious activity detection, countermeasures, and vulnerability scanning in the same way I would for a business (enterprise). Essentially we set up a virtual Windows Server 2016 and secured it through many practical exercises. I also had to learn how to describe potential attacks as well as mitigation methods for each one.
Setting up the firewall rules on an assignment known as “Use and Usefulness of Firewall Rules” helped me get introduced to multiple ways you can secure firewalls catered to what one would typically do in a corporate business setting (in this instance I used pfsense as the firewall). We had to make a tutorial on how to secure the firewall and display screenshots highlighting exactly how the process works. By doing it this way, I learned it and learned how to teach someone the process of securing firewalls. It also helped me learn how to test if firewall rules are working the way they should using a command shell in Windows. I customized the rules using a graphic user interface, which in turn helped me get familiar with GUI for firewalls.
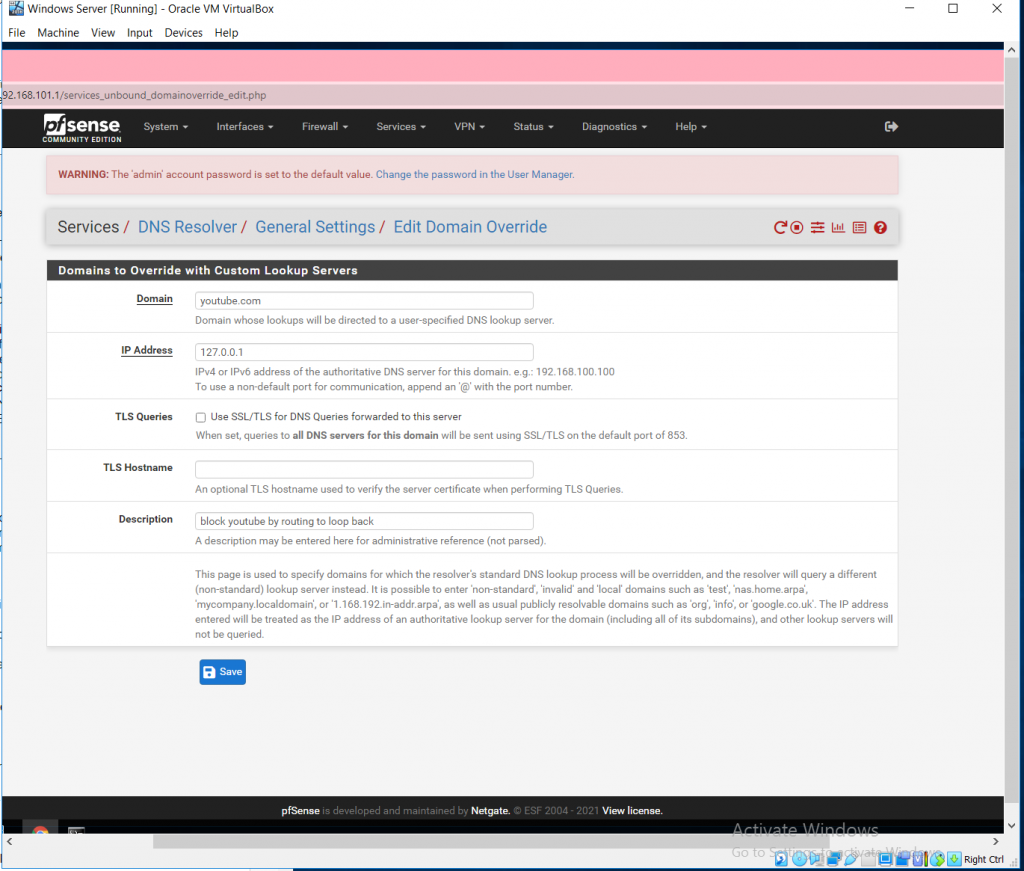
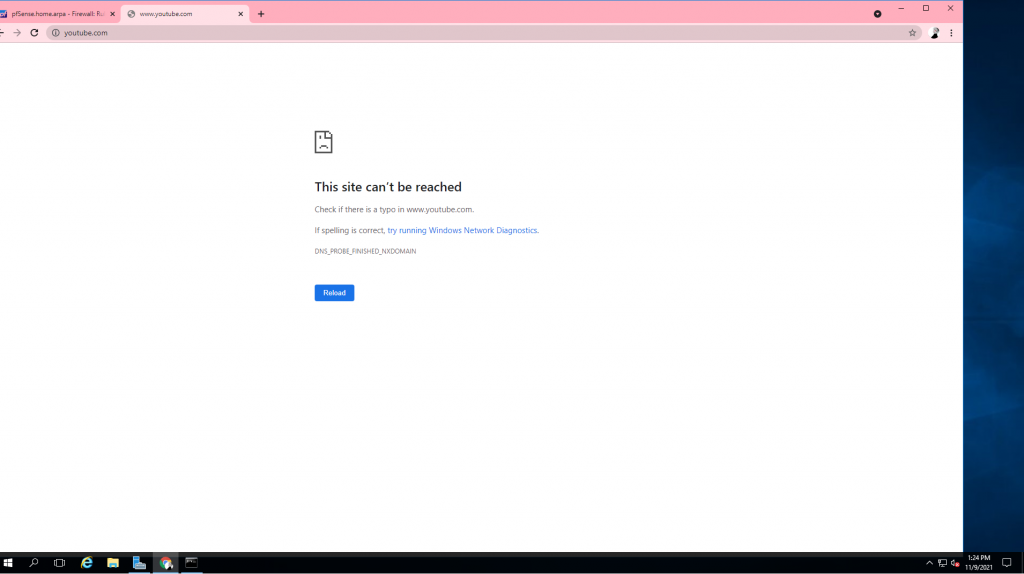
Below is the entire report for securing the firewall and testing each rule after it is made with various methods.
Use-and-Usefulness-of-Firewall-Rules