CS170 / CS270: Computer Architecture
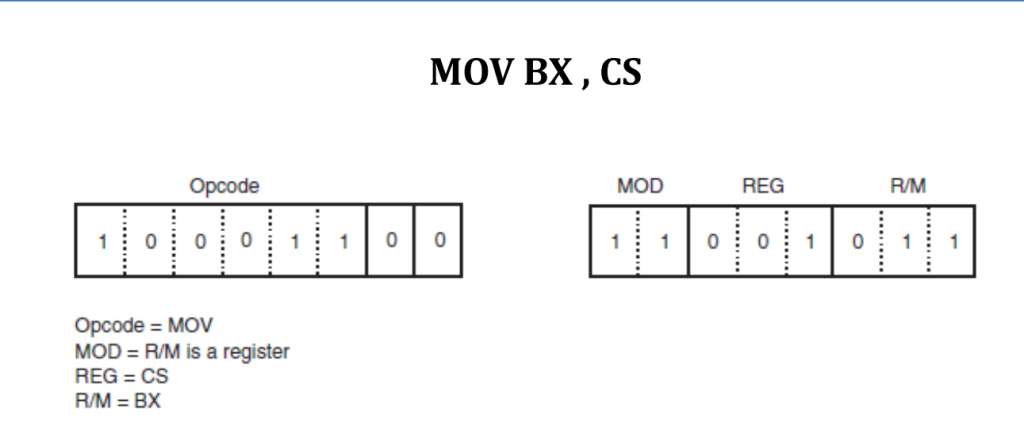
Fundamentals of the basic architecture and operation of modern computers. Subjects such as logical equations, gates, and opcode for processors. Explored mathematical concepts behind computer processes, such as binary, bitwise operation, and floating point representation. The second half of this course discussed the ALU (arithmetic Logic Unit), cache-RAM interaction, branch instructions, design of the control unit, basics of microprogramming, and a pipelined implementation of control unit.
This course was heavy in mathematics and analysis of circuitry, signals, and instruction sets. Many basic operations that are done by computers hundreds of times a second were done by hand, effectively teaching the operation of processors and the functions that enable modern computing. This class was tedious and required detail-minded study to be successful. By understanding the very basics of computer operation, it provides a solid foundation for understanding the complexities inside of computer systems and programs.
CYSE301: Cyber Techniques and Operation
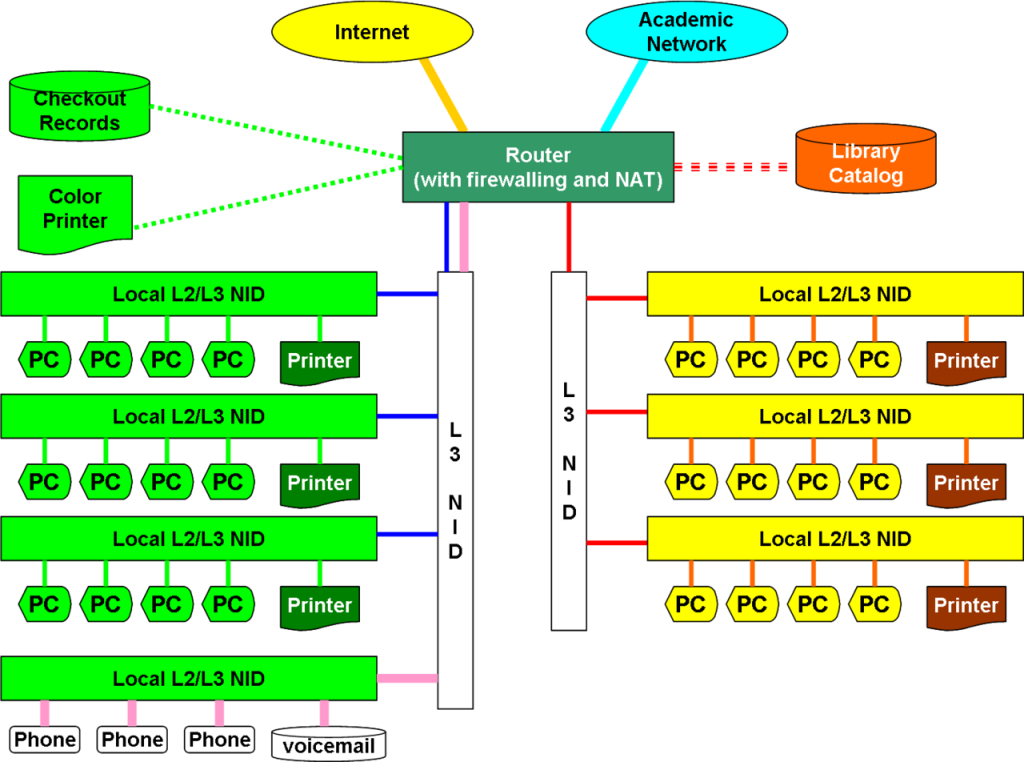
Hands on learning of techniques used by Cybersecurity professionals and researchers. Tools such as Metasploit, Kali Linux, Wireshark, and various network diagnostic tools. Digital forensics and forensics tools were explored, as well as operations to detect and record intrusions into systems. Network defense tools, such as firewalls, were explored and students had hands on projects where these tools would be implemented. Students would create a VLAN of virtual machines connected by a firewall and would analyze interactions between machines to further secure these systems.
CYSE425: Cyber Strategy and Policy

A writing intensive course that required students to research and document different cybersecurity strategies used by businesses, governments, militaries, or private entities. Students would need to explore the differences between private, public, and government cybersecurity policies and the experience needed to develop these plans. This course heavily discussed government standards and cybersecurity policy and practices.
CYSE495: Cyber Risk Management

Explored the need for, the workings of, and the methods of risk management for Cybersecurity systems. Students researched methods for detecting, deterring, and purging threats when identified within a system. Topics such as compliance, NIST, and other security standards were discussed, as well as how to best implement these standards to businesses and entities of all sizes. This was is a highly relevant subject for Cybersecurity majors going into the workforce, as compliance, audits, and security standards are pervasive at all levels of business.
CYSE270 / CYSE280: Windows and Linux Systems Security
Hands on applications course that required students to learn about the inner workings of each operating system, points of attack in said systems, and how to mitigate and deter these risks. Systems management for many versions of these systems, such as Windows Professional, Windows Server, CentOS, Ubuntu, and Red Hat. Both graphical and UI methods were used for managing these systems, so that students will be able to have a full working knowledge of each respective operating system depending on the use case.
CS463: Cryptography

A math-intensive Computer Science course that required students to learn the base level workings behind common encryption and key exchange techniques. Common encryption algorithms, such as RSA, DES and ECC were explored, as well as different methods for digital signature verification and key exchange. Final course project was a program that implemented one of the cryptographic functions that we learned into a working program with a GUI interface and user-selected values.
ECE419: Cyber Physical Systems Security

Research based electrical / computer engineering course where students learned about the functions and uses for IoT devices, how these devices can be implemented within physical systems, and how these devices can be exploited. Students were taught best methods for creating physical systems, as well as exploring emerging topics in the field, such as machine learning and AI. The final project for the course was to plan and create a model of a smart city using emerging IoT technologies.