Phishing is possibly one of the attack vectors that will never go away. It’s low effort, it’s easy, and it works. This is arguably one of the hardest things to defend against. It’s not uncommon for myself to hear someone say “my defense is simply not clicking suspicious links”, but the fact is: it still happens.
There is no shortage of fake websites online. Most can be easily identified very quickly. But some are still convincing enough to trick the technically-savvy without further research into it’s origins. This journal entry was supposed to supply three separate fake websites, but I have two listed. The third is a fake as well, but was created to demonstrate how easy it can be to quickly generate something that is not only convincing, but has the capability to harvest credentials from the victim.
1. A Fake News Site
Initially, I thought this might be a bit harder to just simply look for some fake websites. It’s not something I typically go out of my way to look for, but honestly, it did not take long to find the first one for this entry.
I sometimes have a bit of downtime with much of the traveling I do for work, so I sometimes find myself doom scrolling every once-in-a-while. Very recently, as of this writing, there was a rather tragic news story back home being shared by some of the news agencies on social media. Looking at the comments on the post, it didn’t take long to find the site for the first entry.
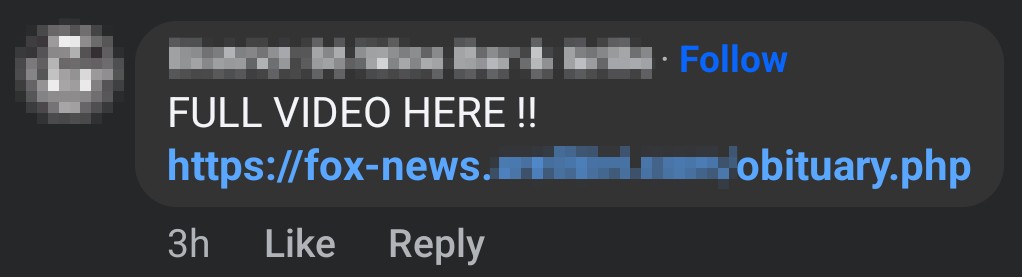
This might be tricky to someone that is not tech-savvy to identify. After all, it has Fox News in the URL. It has to be legitimate, right? In this case, Fox News is actually the sub-domain of the page hosting this content. A domain can have any sub-domain that they wish to have. This is just one of the many tricks some malicious actors will attempt to try to trick individuals into believing the website is legitimate.

Attempting to browse it, for my own curiosity, results in uBlock Origin blocking the page for a “Badware risk”, which it identifies as “programs that have unwanted hidden functionality.”
2. Fake Squishmallow Site
Everyone seems to love Squishmallows. It has become a popular item to collect for both children and adults alike. However, this leads us to the next fake website:
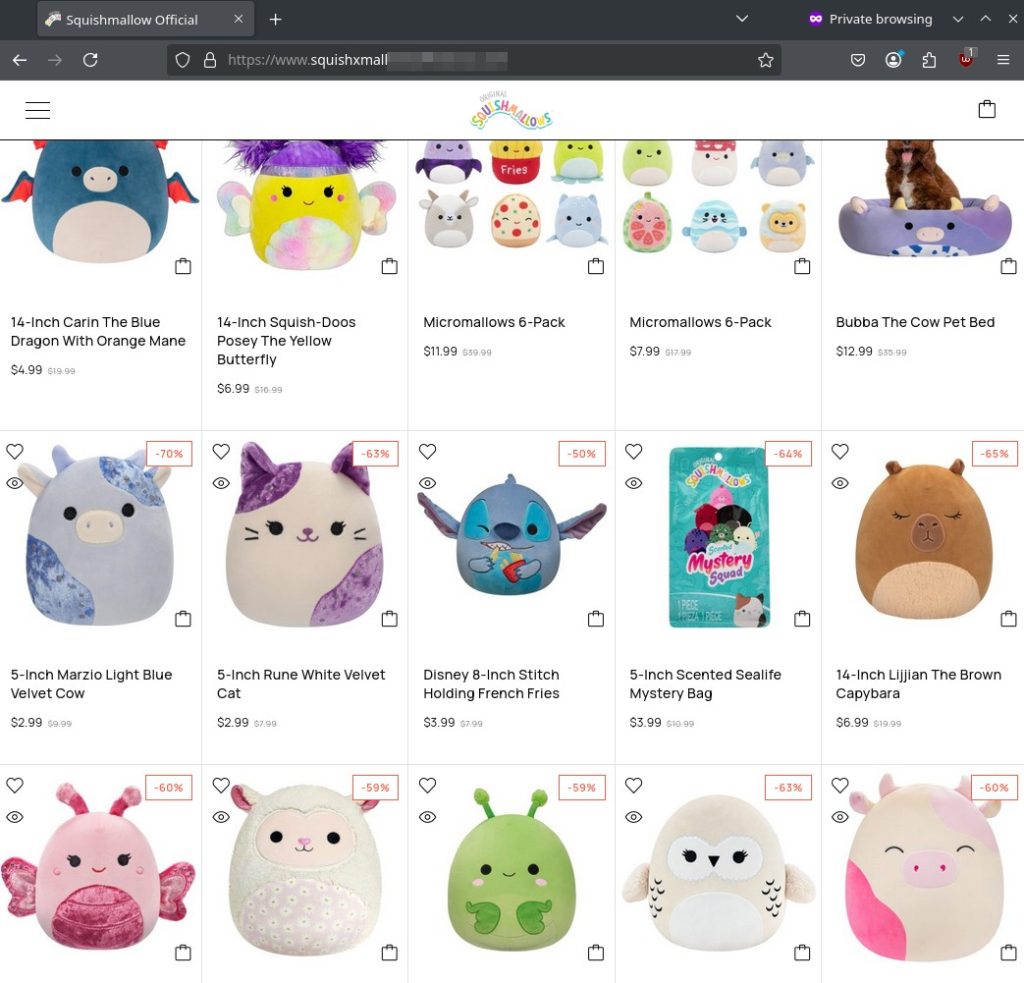
This one, unfortunately, tends to fool a lot of people, and has been for a few months as of this writing. It has it’s own SSL certificate, the URL looks convincing enough. Even the page is organized rather professionally. However, this is not the official Squishmallow store page. Everything on this site is uncharacteristically on sale significantly cheaper than they are usually priced. When doing a quick search about other user’s experiences with the site, it was not long before more red flags were found:
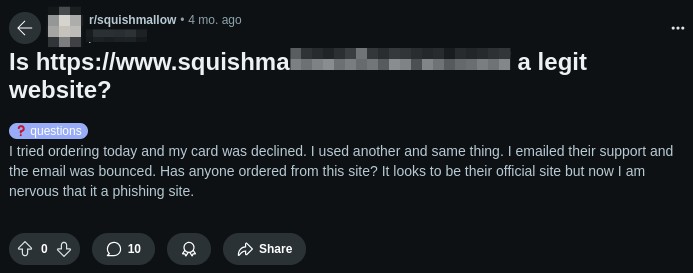
It really goes to show that sometimes, a fake can be very convincing. But, as they say, if it’s too good to be true, then it probably is. I’m unaware of how long this page has been hosted, but even the prices was not enough to make visitors think twice, as it seems this particular page took advantage of the holiday season, leading to a false sense of security with the unusually low prices. For reference, the legitimate page currently looks very similar, minus the steep discounts:
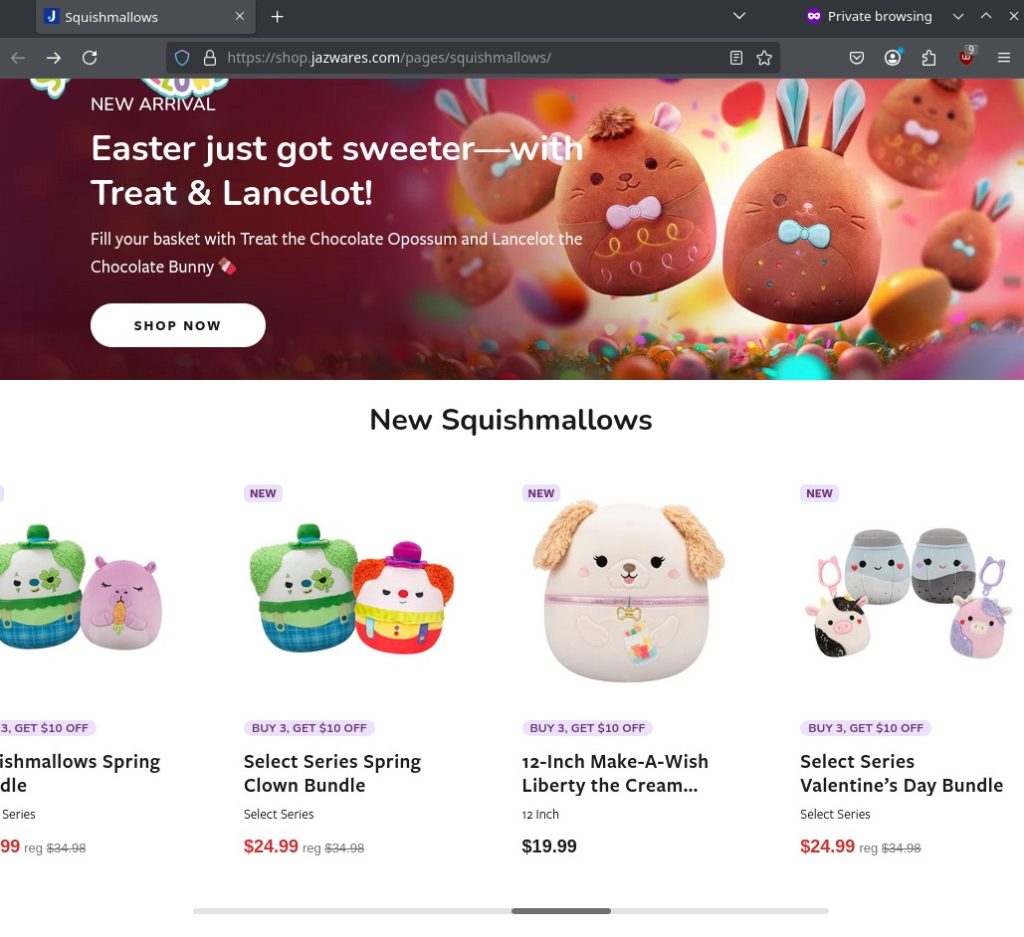
3. Let’s Make Our Own Fake Website
With tools freely available online, it has become simple for a malicious actor to quickly craft a fake website. Instead of trying to locate a third fake website, I’ll instead show how quickly and easily a web page can be created to harvest user accounts and credentials.
The Social-Engineering Toolkit, or SET, is an open-source penetration testing framework designed for social engineering. Designed to generate a variety of custom attack vectors, it allows a user to create and host believable-looking websites quickly.
Once installed and ran, attacks can be crafted using a simple menu-driven interface. From here, we can quickly clone a webpage, or pick from a template.
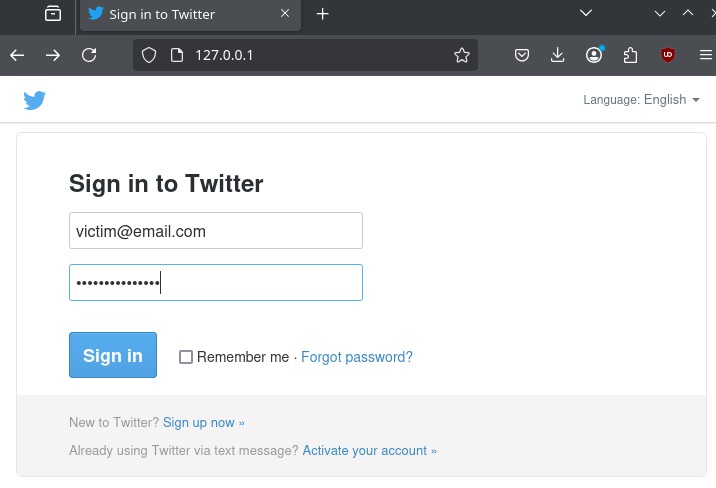
Browsing to the crafted page, it may look legitimate at a quick glance. Aside from the fact that Twitter is no longer called Twitter, the web URL is also a give-away to this being a fake login page. It is also worth noting there is no SSL certificate associated with this crafted-page, self-signed or otherwise (in this instance, I believe it is because I am missing specific packages to deploy SSL certificates in attacks. If utilized, the end user would most likely be prompted with a warning that the page may not be legitimate). However, most modern web browsers will notify the end user that the data provided will be transmitted unencrypted.
Once the victim attempts to login, the credentials are harvested, as identified in the image.