Blog
The Internet of Things (IoT)

The Internet of Things (IoT) since its introduction has been a blessing in many facets of our everyday life. Today, we can send information across many boundaries regardless of space, time, or distance or the ability to even conveniently do our grocery purchases from the comfort of our homes and last but not least, the ability to remotely receive medical care be it general medicine or surgical operations remotely via the internet. Such great fetes chalked by the evolution of the Internet of Things (IoT) cannot be without any risk or challenges. Some of these challenges can mostly be security or privacy issues such that, these new technologies, it allows access to major vulnerabilities if the users of these technologies are not security conscious such as using the proper password or encrypting their sensitive information. An improperly secured technology and the use of any IoT services can also cause a huge privacy issue and concern. This is because information when not properly secured can fall into wrong hands which may then be used by these entities to cause harm to an individual or even the country at large. Over the past decade or recently, there have been many security breaches to large corporations such as T-mobile, Credit Bureau companies, and even the government of the United States of America all due to privacy and security issues caused by the use of different IoT platforms.
It is therefore a matter of great concern to educate users of the Internet and technologies on proper security and privacy postures from the individuals level to even the corporate level. Although the IoT has been a blessing for society, it can and will always pose a risk of grave consequences too to its users.
SCADA SYSTEMS
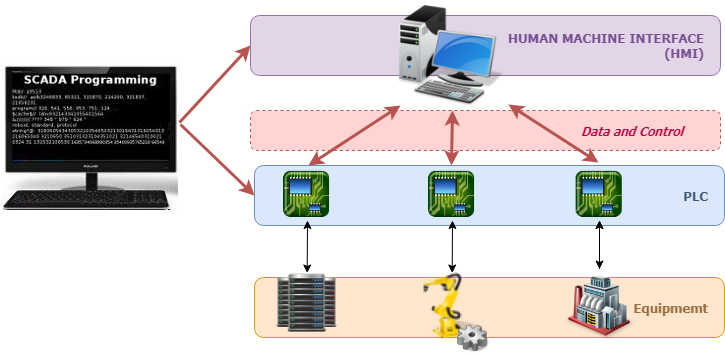
The success of any organization, industry, or entity relies mainly on its system implementations. One of such systems is Supervisory control and data acquisition (SCADA). Which according to an article by scadasystems.net, “is an industrial control system (ICS) that is used to control infrastructure, facility-based, or industrial processes such as water treatment, wastewater treatment, airports, spaces stations, manufacturing, production, refinery and power generation respectively” (scadasystems.net,2021).
The concept of SCADA is primarily to monitor and control an operation from a centralized system, often within a large area or site. There are subsystems within SCADA that help in its successes, such as the type of apparatus used, which humans mainly operate with access to all data, also known as the Human Machine Interface (HMI). There is also the supervisory system which is responsible for the gathering of data about the process. Moreover, the Remote Terminal Units (RTUs) and the Communication infrastructure work together to ensure the operation’s success. It should be noted that the SCADA systems process does not control in real-time, but rather it coordinates the process in real-time by sending command controls to the process. The components of SCADA are hardware and software, making it possible for organizations to control their processes from anywhere remotely. Prior to the use of SCADA, many systems would have people at every stage in the process, such as running a ship’s energy. At every significant point of the energy room, there would be sailors physically turning buttons, pulling plugs, or turning on knobs for the ship’s room to function. However, the use of SCADA has made it simple to reduce the number of human presence due to the software that can coordinate the systems. Such functions are previously controlled by humans on the ground to be monitored and controlled by just clicking on a centralized computer system, a tablet, or even a phone.
The use of SCADA by organizations in industries such as power producers, water and waste management, and some manufacturing companies have experienced tremendous growth and efficiency in their daily operations. SCADA has made it possible for these organizations to receive real–time dates and alerts that can help with the smooth running of their process. Just like most smart systems, SCADA systems are not immune to attacks. On the contrary, increasing cyber-attacks on SCADA systems result in costly damage to the organizations that use them. According to a publication by Security week, “there was an incident in which occurred in March, where cybercriminals used unknown ransomware to target a water facility in Nevada, and the malware affected SCADA and backup systems. However, the agencies noted that the SCADA system only provided monitoring and visibility capabilities, and it was “not a full industrial control system.” (Kovacs,2021). SCADA systems are vulnerable to different forms of attacks; hence it will be prudent for organizations to implement systems that will help in mitigating these attacks and securing any vulnerabilities associated with the SCADA system.
SCADA systems since its inception have contributed significantly to increased production and ensuring quality and on-time delivery of services across major industries. However, there is still work to be done to reduce the numerous attacks on SCADA systems as technology increases daily.
References
Kovacs. E. (2021). Security Week: Ransomware Hit SCADA Systems at 3 Water Facilities in the U.S. Derived from https://www.securityweek.com/ransomware-hit-scada-systems-3-water-facilities-us
SCADA systems. (2021). SCADA Systems: SCADA Systems concepts. Derived from
Workplace deviance
In today’s technology era, especially with the increasing presence of the Internet of Things (IoT) in society and the workplace, many opportunities have been created in the cyberspace of technology. These opportunities have continuously made work more accessible and, to some extent, very efficient. However, the vast opportunities and platforms created by cyber technologies have also created inevitable workplace deviance that adversely affects workplace productivity. Workplace deviance is defined as “voluntary behavior that violates significant organizational norms and, in doing so, is perceived as threatening to the organization’s well-being or its members (Bennett and Robinson, 2000). In this current era of the Covid-19 pandemic, where most organizations have moved from working in their physical building to having their employees work from home, there has been a variety of complaints from customers about how the business has changed, especially when trying to speak with customer service. Due to employees’ ability to manipulate their technologies like laptops and phones to prevent them from work under the guise of malfunction. Also, some employees or employers have created shortcuts to work, creating product issues for the consumers. There is also the case of identity theft by employees not adhering to privacy policies and stealing customer’s personal information like Social security numbers to adversaries and causing grave consequences to their customers. These are just about a few ways cyber technology opportunities have created workplace deviance.