Journal 3
Visit PrivacyRights.orgLinks to an external site. to see the types of publicly available information about data breaches. How might researchers use this information to study breaches? Enter a paragraph in your journal.
Using data provided by information on privacy.org, researchers can find similar trends in breach tactics, the industries and individuals affected, and the type of data stolen/accessed. This information will allow researchers to develop better methods to protect the most vulnerable groups. Also, seeing breach tactics can help detect vulnerabilities early and build stronger defenses. The databases provided give ideas of breach impact and severity. All of these aspects are important when trying to protect an organization or just our information. Researchers need these statistics to understand the new data breaches and how to prevent them.
Journal 4
Review Maslow’s Hierarchy of Needs and explain how each level relates to your experiences with technology.
Give specific examples of how your digital experiences relate to each level of need.
Note: The word count should be in between 100 -125 words.
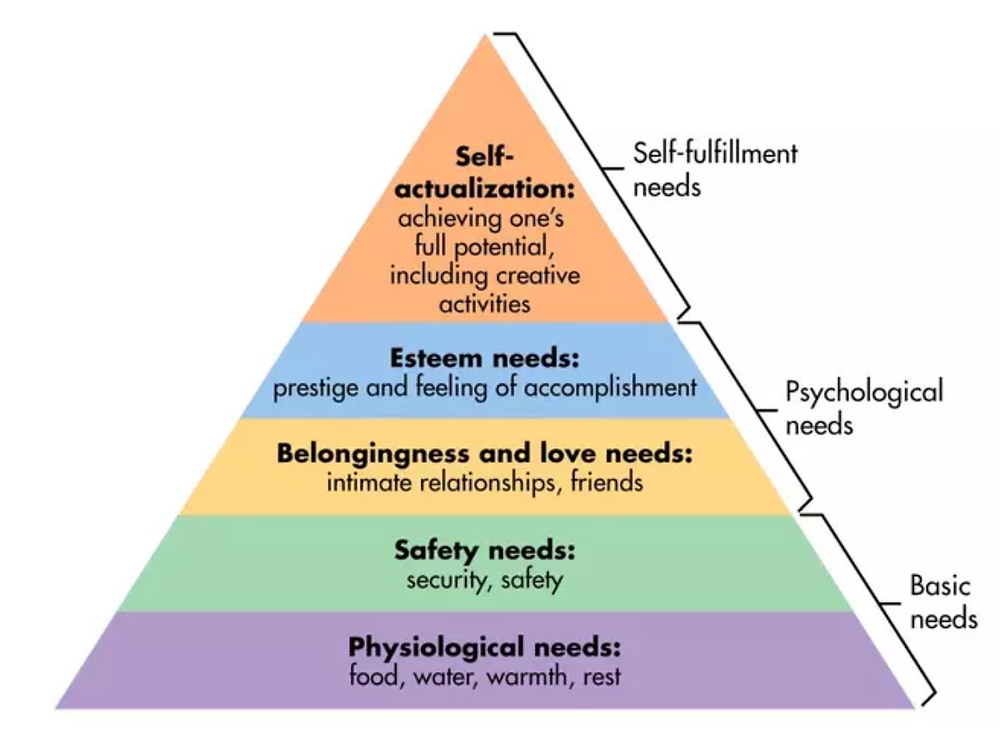
Maslow’s hierarchy of Needs includes physiological needs, safety needs, belongingness and love needs, esteem needs, and self-actualization. Technology is a part of my everyday life, just like many others. Analyzing how technology relates to each level of the hierarchy is a little difficult, but I realized that technology in some way relates to each level Maslow has presented. Below I show how each level relates to my experiences with technology.
Physiological Needs– When It comes to the basic physiological needs technology doesn’t fulfill my basic needs like food, water, and shelter but it does help to achieve the goal of getting the basic needs. For example, I use my phone to order food and search for housing. Although my technology does not directly solve my needs it can be used as a tool to gain these basics.
Safety Needs– To ensure safety needs are met technology helps with strong passwords, anti-theft security systems, data backups, etc. Technological advancements are evident everywhere even in my car where it tells you if you have your seatbelt on or not.
Belongingness and Love Needs– Technology fulfills my need for belongingness and love because my technology allows me to call text and Facetime my loved ones which helps me feel loved and that I belong because being away at college is hard but technology allows us to stay connected.
Esteem Needs– My esteem needs are filled by my social media platforms that allow me to share my achievements online for all to see. I get comments from friends and family that help boost my self-esteem and confidence in myself. The validation is rewarding.
Self-actualization– To help my personal growth, I use online platforms, apps, courses, and tools to expand my knowledge in Cybersecurity and other areas. These tools help me grow in my career path, especially by acquiring new skills and gaining a deeper understanding.
Journal 5
Review the articles linked with each individual motive in the presentation page or Slide #4. Rank the motives from 1 to 7 as the motives that you think make the most sense (being 1) to the least sense (being 7). Explain why you rank each motive the way you rank it.
My ranking is:
- Money
- Multiple reasons
- Entertainment
- Revenge
- Recognition
- Political
- Boredom
I choose money as the first reason because most people’s reason to commit crimes has to do with financial gain. When hacking into a system to steal PII attackers often steal banking information to take money from accounts.
I chose multiple reasons second because sometimes the reason for an individual to commit a crime involves multiple reasons than just one. For example, a hacker can hack into a system to get money, for fun, and to be recognized by others.
I chose entertainment for three because many people with extensive technological skills often attempt to attack vulnerabilities in systems to see where their knowledge is and also the defenses around a system.
I chose revenge as my fourth motive because people tend to use hacking methods to ruin and harm others out of spite. For example, leaking personal images of another to embarrass another.
I chose recognition as my fifth motive because individuals who commit cybercrimes also like to “show off” their abilities and tease that they are unable to be caught. this attention fuels the negative behaviors.
I chose political as sixth because cybercrimes with political motive aren’t as common as financial motives. Although some groups do use hacking to promote political agendas, disrupt government operations, or expose corruption.
I chose boredom last because people may commit cybercrimes due to a lack of engagement but it is rarely a common reason.
Journal 6
Can you spot three fake websites? [Refer Online Security Blogs, Public Awareness Sites, Academic Resources etc., and cite the source].
Compare the three fake websites to three real websites and highlight the features that identify them as fraudulent.
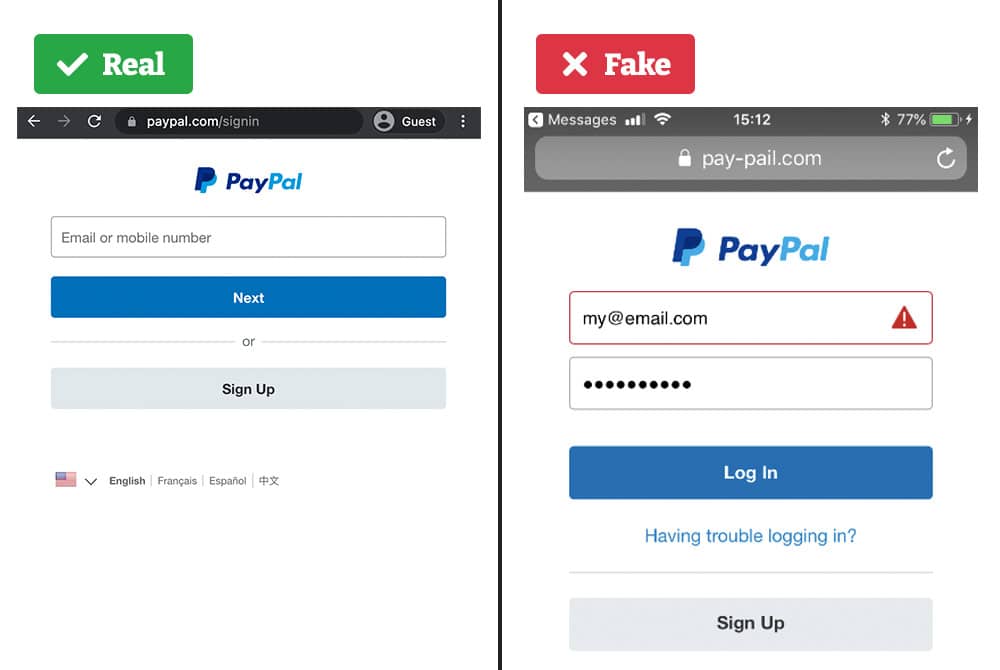
In Figure One, there are two separate PayPal websites shown. The one on the left is the legitimate sign-in page while the right side is spoofed. This means it was created to look legitimate but is owned by an outside party or individual that aims to gain sensitive information. There are many ways to tell if a website is fraudulent. In this case, the spelling of PayPal is incorrect. The left is spelled “Pay-pail” in the address bar.
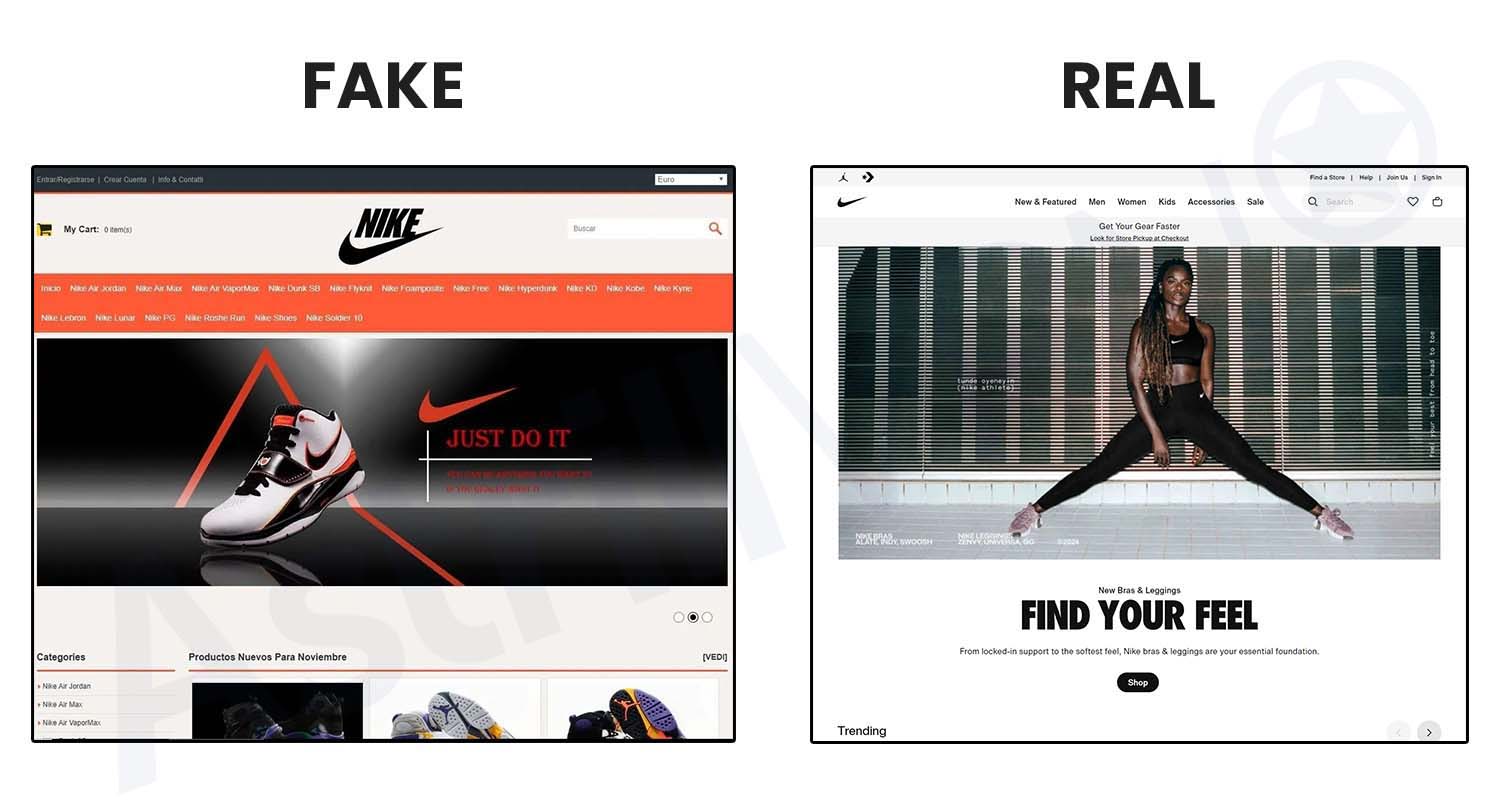
In Figure Two, there are two separate “Nike” websites. The left is the fake site and while we don’t have an incorrect website name like Figure One, we do have two different appearances. The legitimate website (right) has a neat and well-organized appearance with a trademark font and correct spelling. The fraudulent site (left) is sloppy and unorganized.
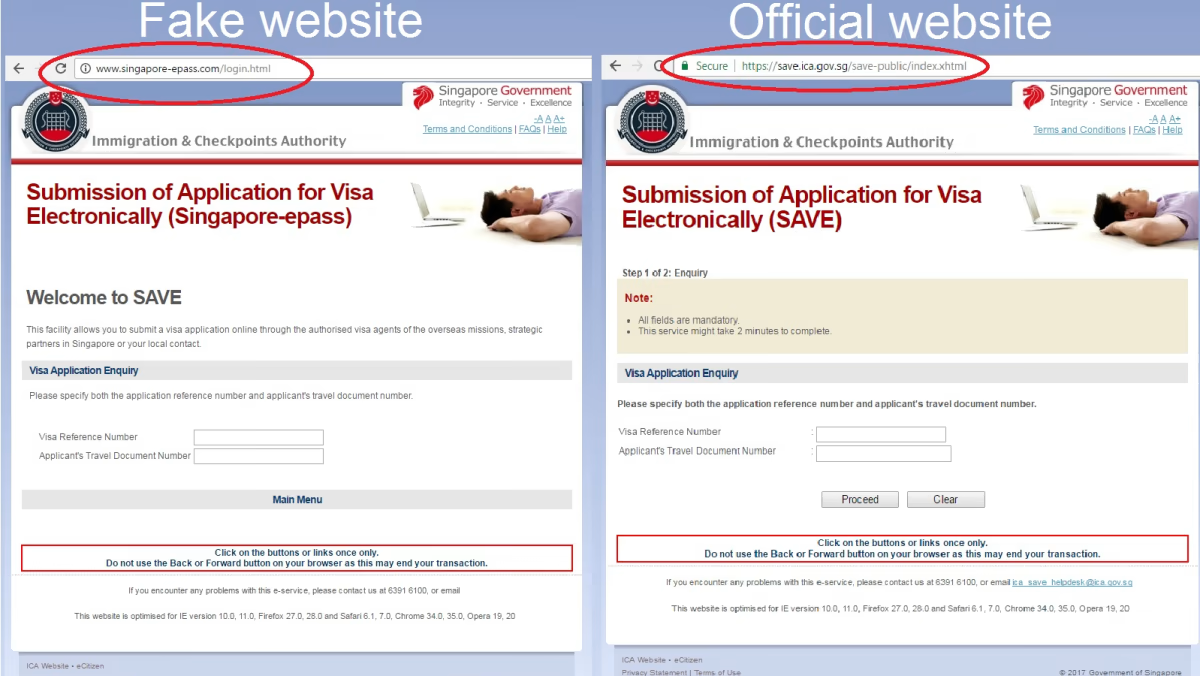
In Figure Three, the real website (right) can be verified by the transfer protocol also the website name and URL are completely different. Often built into devices for security purposes a browser can show whether the site uses HTTP or HTTPS. HTTPS is secure and proves verification of the site. Also, the site is SAVE and the URLs and website names are completely different.
Journal 7
Review the following photos through a human-centered cybersecurity framework. Create a meme for your favorite three, explaining what is going on in the individual’s or individuals’ mind(s).
Explain how your memes relate to Human-centered cybersecurity.
The human-centered Cybersecurity model positions humans as the central element of Cybersecurity and information security procedures, frameworks, designs, and the integration of technology in an effort to reduce human-enabled errors.
In other words, humans are the essential element in cybersecurity. Humans can be the biggest liabilities or the greatest strength of cybersecurity efforts. I created 3 memes to display the human-centered cybersecurity model in everyday images. Each with an explanation of their relation to the human-centered model.

Image #20:
This image shows a woman scrolling through a social media platform. In this meme, she is hoping her password for the app is strong enough to avoid a breach of her account(s).
This relates to the human-centered model because having strong passwords is a vital and basic first step to the security of devices, accounts, networks, etc.

Image #2:
This image shows an individual presenting to a room full of others. In this meme, the individuals are in training about phishing emails.
This relates to the human-centered model because workplace training helps with awareness of cyber threats and how to recognize them. Knowledge is power and having company individuals aware of possible threats helps to prevent attacks from happening.

Image #16:
This image shows a man sitting at multiple screens where he is analyzing the network. He is fixing a breach where an employee connected a personal device to the secure network.
This relates to the human-centered model because most security issues are a result of human error. The connection of the personal device to the network presented a huge security risk and could have been avoided with proper training and security audits.
The human-centered model shows that Cybersecurity starts and ends with us!
Journal 8
Watch this video and pay attention to the way that movies distort hackers.
After watching the video, write a journal entry about how you think the media influences our understanding about cybersecurity
Note: The word count should be in between 100 -125 words.
After watching the YouTube video “Hacker Rates 12 Hacking Scenes In Movies And TV | How Real Is It?” I think the media gives us a semi-realistic view of cybersecurity and its place in our society. The video clips showed highly exaggerated, action-packed scenes of people breaking into systems and illegally obtaining data, which does happen but does not accurately represent cybersecurity. Cybersecurity starts with something as simple as having a complex password but we don’t see that side of the industry on television. I think what is shown on television makes the “outsider” believe cybersecurity is a fantasy just depicted for entertainment when the reality is it plays a part in all of our lives every day.
Journal 9
Watch this Video: Social media and cybersecurityLinks to an external site.
Complete the Social Media Disorder scale
How did you score?
What do you think about the items in the scale?
Why do you think that different patterns are found across the world?
On the Social Media Disorder Scale, I scored a 1. I believe the items in this scale do not pertain to me and can be highly suggestive if not read properly.
Social-Media-Disorder-Scale-2-2I believe there are different patterns found across the world due to many different factors including profession, location, relationship with social media, age, etc. For example, an individual’s profession could require more posting on social media. A TikTok personality will require constant posting, updating, monitoring analytics, and responding to comments versus a top-secret FBI agent who will have little to no posts or information of themselves online.
Journal 10
Read this and write a journal entry summarizing your response to the article on social cybersecurity
In summary, this article “Social Cybersecurity: An emerging national security requirement” is about the realization that cyber warfare is no longer strictly technical but it now it has a information element. in terms of security, Humans our the biggest asset and an even greater liability. We are fighting an information war meaning the knowledge of the people matters to the overall battle. Items such as the influence of the public opinion and discrediting a nation can lead to the win of a war before the physical combat begins. in latent terms, Social cybersecurity is humans using technology to hack other humans.
These humans are bound by society and our devices further connects us. As tiredless as our efforts are to keep unauthorized users at bay and remove improper sources we cannot get them all and those that slip through the cracks have the ability to not only influence war, but have control over an individual’s life. Using propaganda to persuade people and get them to take action is an example of the powers of information war. The use of technology has enabled cyberthreats and only proper training and knowledge can help us fight back.
Journal 11
Watch this video. As you watch the video, think about how the description of the cybersecurity analyst job relates to social behaviors. Write a paragraph describing social themes that arise in the presentation.
In the video “What Does a Cybersecurity Analyst Do? Salaries, Skills & Job Outlook” by Nicole Enesse, there are many social themes within the cybersecurity analyst job that relate to social behaviors. Soft skills such as communication and collaboration play a huge role in the job field. Analysts have to work and communicate with other departments and individuals to ensure an organization is secure and proper defenses are deployed and up-to-date. Another theme is the ability to adapt and commit to the ethical responsibilities. The job is to protect SPII and with access to sensitive information, analysts must be careful and must not share or exploit the data. Human error is a large liability because people who are unaware cause the most damage. Nicole’s description of the position also displays how analysts must provide security against inside and outside threats. Making human error is another theme that plays a role in the cybersecurity analyst role.
Journal 12
Glasswasherparts.com_Read this https://dojmt.gov/wp-content/uploads/Glasswasherparts.com_.pdfLinks to an external site. sample breach letter “SAMPLE DATA BREACH NOTIFICATION” and describe how two different economics theories and two different psychological sciences theories relate to the letter.
In the sample breach letter, two economic theories were explored, including Rational choice and Marxian economic theory.
Rational choice theory is about individuals/businesses making choices in their best
interest (pleasure versus pain). Concerning Cybersecurity this theory relates to whether Individuals and businesses decide to invest in malware. In the data breach notification under the section ” What Are We Doing?” the company tells how they are working with a cybersecurity firm to remove malware. This investment falls under the rational choice theory.
Marxian economic theory is when those with power (e.g., those with a lot of money) exploit those without power (e.g., those who are poor) for economic gain. Concerning Cybersecurity, those with power can collect significant information
about those without power through cyber technology. In the data breach section “What Happened” we are told the intruders gained access to customer information including payment card numbers as customers made transactions on the platform provider’s systems, and had access to historical payment card data. which is a prime example of this theory that proves the powerful will exploit those without it.
It wasn’t only economic theories that were explored, but two different psychological science theories as well. Cognitive theory and Neutralization theory are used in the creation of the data breach notification letter.
Cognitive theory focuses on the way individuals perceive, interpret, think, and
process information based on their cognitive processes. Cognitive theories suggest that individual’s thoughts and beliefs cause their emotions. The sample breach notification uses this theory to help ease the readers and give them a way to ensure their security. From the beginning of the letter, the goal is to reassure the notified individual, clear up confusion, and use the way they believe someone receiving the information would feel and how to ease their minds.
Neutralization theory is a criminological theory suggesting that individuals know right from wrong, and rationalize their behavior before committing a crime. This theory is used the look at why criminals commit crimes, but in this letter, the theory is used to use the right wording to acknowledge the breach, telling actions, and telling their part in taking swift action. The company was able to use neutralization theory to preserve its image further reducing blame.
Journal 13
A later module addresses cybersecurity policy through a social science framework. At this point, attention can be drawn to one type of policy, known as bug bounty policies. These policies pay individuals for identifying vulnerabilities in a company’s cyber infrastructure. To identify the vulnerabilities, ethical hackers are invited to try explore the cyber infrastructure using their penetration testing skills. The policies relate to economics in that they are based on cost/benefits principles. Read this article https://academic.oup.com/cybersecurity/article/7/1/tyab007/6168453?login=trueLinks to an external site. and write a summary reaction to the use of the policies in your journal. Focus primarily on the literature review and the discussion of the findings.
The article “Hacking for Good: Leveraging HackerOne Data to Develop an Economic Model of Bug Bounties,” researches the intersection of cybersecurity policy and economics.
The literature review, emphasizes the incentive given to ethical hackers in the bug bounty programs to identify and report any vulnerabilities found. The foundation of these programs is to bring companies and professional security researchers together to improve security and get paid, so both parties have a win-win situation. Participation motivations are also looked at in the literature review. It was discovered these programs best succeed when incentives are clear and well-defined.
In the findings portion of the article, it is revealed that trust, security, and clarity influence the participation of ethical hackers. They are more likely to participate and provide detailed and quality reports when these factors are there. Inconsistencies are the downfall of the program.
Overall, I have seen that the factors of trust and fairness play a huge role in the structure of cybersecurity. Being that trust and fairness are concepts of social science I can take away that just like regular people being treated like a decent human being will allow for quality work.
Journal 14
Slynchukhas described eleven things Internet users do that may be illegal. Review what the author says and write a paragraph describing the five most serious violations and why you think those offenses are serious.

Clario provided a list of eleven things people unknowingly do that are illegal. Out of these eleven activities, I find sharing passwords, addresses, or photos of others, bullying and trolling, faking your identity online, collecting information about children, and illegal searches on the internet to be the 5 most serious violations. These 5 activities can cause harm to others and for that reason alone are the most serious. The other activities cannot physically or emotionally cause pain to other people. Downloading a movie may be illegal, but in reality, people who do this only open themselves up for attack while bullying and trolling individuals can lead to mental and emotional problems including low self-esteem. The five violations I chose should result in jail time, while the others should not.
Journal 15
Digital Forensics | Davin Teo | TEDxHongKongSalon
Watch this video and think about how the career of digital forensics investigators relate to the social sciences. Write a journal entry describing what you think about the speaker’s pathway to his career.
Stuart Hyde’s talk on his career as a Digital Forensics Investigator was full of passion. It was interesting engaging to see how he merges technical skills with soft skills. The most interesting part for me personally was the transition he made from policing to digital forensics.
He explained, He had to adapt to an increasing number of violent crimes against property or people that happened digitally, and in doing so, he had to learn not just to analyze data, but to think about human behavior in the context of the data being outlined, just like in social sciences. Digital forensics is relates to criminology, psychology, and sociology because the investigator has to deal with motives, not just methods. For example, every case of cyber bullying, fraud, or online exploitation has to be analyzed in terms of underlying motives and social behavior, which is the major point of the social sciences.
I found his journey into the profession relatable. He began as a police officer, not in the cyber or computer science world, and then evolved with the changes in criminal activities. He switched his thinking to that of a lifelong learner and I admire that because I wanted to be a lawyer before deciding on cybersecurity.