Journal Entry #1
Regarding the NICE Framework, I wish to focus my career upon the “Threat Analysis” area of this framework as I have always been interested in identifying threats, as well as the architecture of a network and how it pertains to an operational picture. This field of cyber security correlates to some of the work I did while serving in the US Navy and is a field that I already possess some skillsets for. Furthermore, I believe this area would appeal most to me after viewing the potential tasks listed in the framework such as “maintaining a common intelligence picture”, “evaluating threat decision making processes” and “Identifying intelligence gaps and shortfalls.” All of these tasks make me think of how I would have high job satisfaction, as well as a sense of accomplishment in analyzing threats and brainstorming ways in which to curb them. Other specialty areas I believe would strike my interest include similar job functions such as Operating and Maintaining the equipment that ensures efficient IT system performance and security. Some of the specialty areas regarding this category that strike my interest are network services, customer service and technical support, and data administration. I view myself as someone who gains satisfaction from the solving of various problems, and thus believe that this category coincides directly with that.
Regarding the categories that strike me as the “least appealing”, I will refer to “securely provision” in which the majority of specialties tend to focus on the research and development aspect of this field. I have never been one to be good at advanced algorithms and math equations and thus I tend to avoid fields that would require me to build a system architecture, develop software, or do any sort of advanced coding. As I progress in my chosen field, these things may start to make more sense to me, but as of now, I wish to focus on the things that interest me, and that I have an understanding for.
Journal Entry #2
The principles of science directly relate to the field of cybersecurity in a multitude of ways. Firstly, a major focus of science that correlates to cybersecurity is the scientific method and data collection. When relating these concepts to cybersecurity, they reveal the importance of monitoring and gathering data on network traffic, as well as the behavior of users in order to ensure the security of a system from various threats and bad actors. Furthermore, another concept of science that relates to cyber security is that of testing hypothesis and experimenting. These coincide as in this field, hypotheses focus on potential vulnerabilities in a system, how a threat will be introduced to a system, and various attack scenarios. Cyber experts form these hypotheses by thinking of how a threat might manifest, or how a systems vulnerability can be exploited for nefarious purposes. After these hypotheses are formed, experimentation may occur in the form of penetration testing to validate or scrap potential hypotheses and allow these experts to further secure the systems they are working on. Thirdly, another concept of science that relates to cyber security is data analysis. We analyze data utilizing tools such as machine learning algorithms, as well as pattern recognition to analyze massive amounts of data. These analysis’ help experts to identify patterns and/or anything out of the ordinary in the datasets that may indicate a cyberattack or any potential vulnerabilities.
Journal Entry #3
Researchers may be able to use information found on ‘privacyrights.org’ by various means. Firstly, they may utilize the information for analyzing the various data breach incidents by researching the manner of attack, the data that was being targeted, and the number of people affected by the breach. Furthermore, they may also utilize this information to document various trends in cybersecurity and utilize this to develop more effective security measures to reduce the risk of future briefs. Another thing researchers may do with the presented information is utilize it to spread awareness and educate the masses on proper cyber hygiene practices to ensure that an individual’s system is better protected from future data breaches. Lastly, researchers may use this data to compare various data breaches to identify any trends or variations in these attacks and use that to implement better security measures based on what the trends are showing as the normal targets, and means of attack.
Journal Entry #4
Relating Maslow’s Hierarchy of Needs to technology is quite easy as the framework of the chart ties into technology and the modern world. We are rapidly evolving in a technological sense to where many forms of technology become almost a necessity to successfully navigate everyday life with the use of personal smart phones, laptops, the internet, and so on. Where these needs fall into my own experiences are as follows: While the first level doesn’t necessarily pertain to me personally, technology can address physiological and biological needs in the form of technological advances such as insulin pumps, medication, pacemakers, and so forth. Secondly, safety as it pertains to my own experiences, may be addressed by various cybersecurity methods I employ on a day-by-day basis to include the utilization of good passwords, anti-malware programs, VPN’s and so forth in order to ensure that my online presence is as secure as possible. Furthermore, in regard to social needs, the obvious answer here is my using of various forms of social media to include Facebook, Instagram, and Reddit to satisfy those social needs to connect to other users and friends. As for my belonging and esteem needs, technology, especially in the form of social media provides me with hits of dopamine in the form of interaction from my peers regarding pictures I’ve posted, status and life updates on social media, happy birthday posts, and so on. As for cognitive and aesthetic needs, I am information driven in that I have a curiosity for how things work. I can easily find an article, video, or testimony and delve into the researching of topics that interest me online. Lastly, self-actualization for me comes in the form of remaining positively engaged in forms of social activism to include anti-racism, anti-disinformation, and staying up to date on various political events via technology.
Journal Entry #5
Individual Motive Ranking For Cyber Crime:
- Multiple reasons: I believe this is the main motive as cybercrime is more nuanced than having a single motivating factor. Cybercriminals tend to commit crimes for a mixture of recognition, money, revenge, and occasionally that will also tie into political motives as well.
- Money: I believe this is an obvious motive and why it places towards the top of my ranking list. Many criminals, cyber and in the real-world commit crimes for the monetary gain. Whether that be to support a lavish lifestyle, or to simply try and support their family to the best of their ability.
- Entertainment: I believe this falls sort of in the center of the ranking as many hackers, especially younger ones tend to hack not for nefarious reasons such as revenge, but rather because its exciting. I, myself as a teenager obtained the administrative password for my school’s laptop network and proceeded to install Minecraft on everyone’s laptops. I of course was caught as I was unaware of the intricacies of security systems at the time.
- Revenge: This one is a bit nuanced and why I ranked it as number four. Revenge can be classified as a multitude of reasons such as hacktivism efforts from groups such as Anonymous on perceived wrongdoings from authorities, political, or corporate entities. However, it also encompasses more nefarious deeds such as the spreading of “revenge porn.”
- Political: Hacking based on political motives is something that is becoming more prevalent in the world. We have seen this in various forms, most notably the Russian government allegedly meddling in past US elections. However, it can also be used as a motive for individual hackers that have a bone to pick with various political figures that do not align with their views. I feel as though this motive isn’t as prevalent as others though.
- Recognition: This one ranks toward the bottom of my motive rankings as I feel as though most hackers, apart from a few outliers, prefer to remain anonymous in regard to hacking, lest they face the consequences for their actions.
- Boredom: Whilst hacking due to boredom can be quite common, I believe that as a motive, it is a bit of a non-starter except for being encompassed into the “multiple reasons” motive at rank one. Typically hacking due to boredom is tame in nature, and whilst some hackers may try to harm others because of boredom, they are few and far in between. Most boredom hacking tends to fall into “trolling” or abusing API systems to collect public data, which while nefarious in nature, is not typically associated with the ruining of someone’s life online.
Journal Entry #6
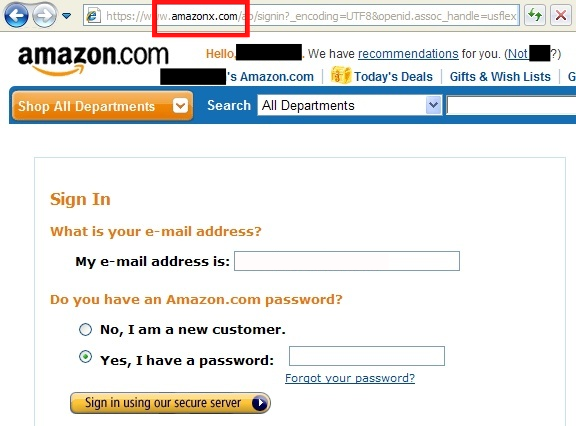
Attached is an example of a fake website, Amazon in this case. The identifier in this one is highlighted in the red box above and is an example of a phishing scam in which hackers attempt to send various means of this link whether by email or text message notifying you to login to your account or reset your password. However, the link is altered to appear as similar to the valid web address as possible with only minor changes such as the one above in which an “x” is inserted. A real example of Amazon is listed below.
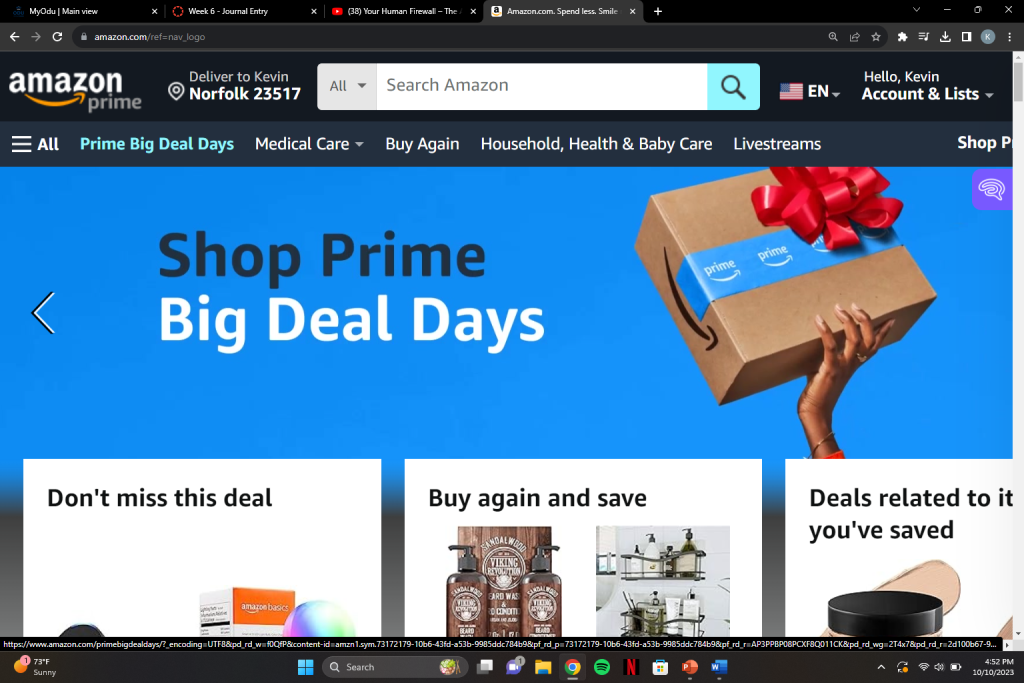
In this picture, the URL is the valid “Amazon.com” URL with no additional characters of any kind.
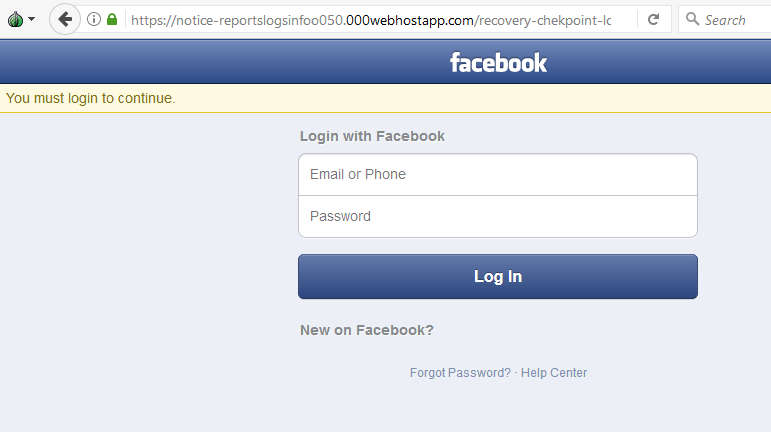
This page is a more obvious example of a fake login for the social media site “Facebook.” Whilst the URL may appear legitimate as a redirected recovery page or external link to Facebook, it is another phishing attempt and illegitimate login page tailored to gather your credentials and take over your profile and potentially other sites in which you may use the same login credentials.
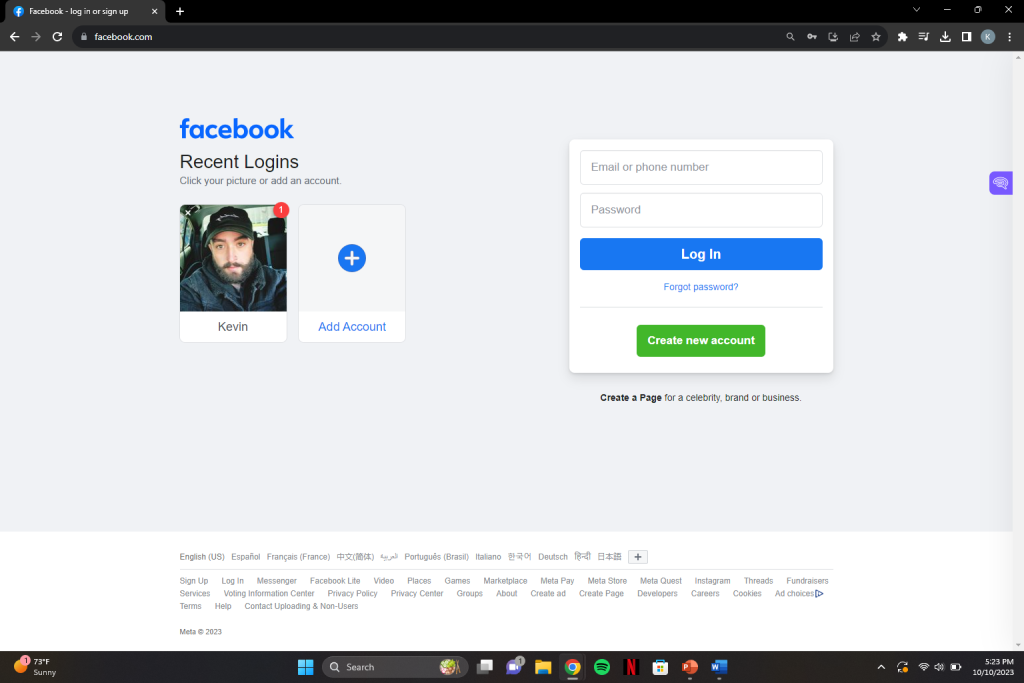
This is a legitimate Facebook login page in which the URL is clearly displayed as “Facebook.com”
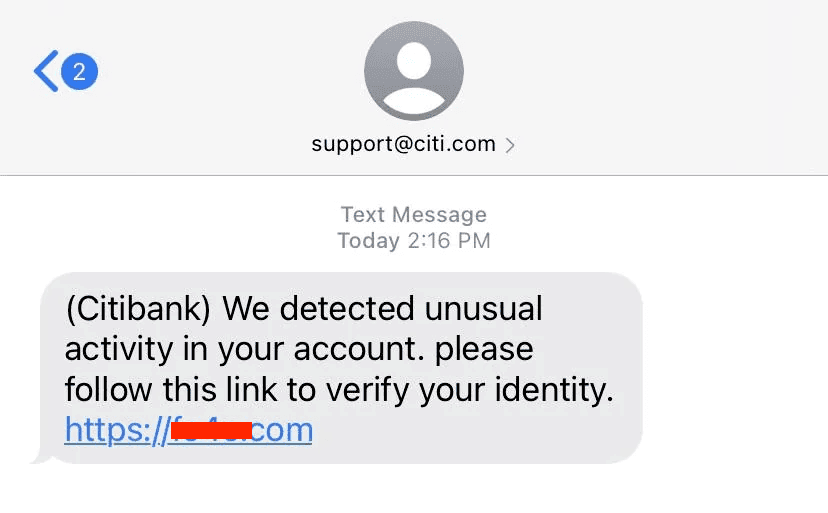
Attached above isn’t necessarily a website but is a common scam in which a hacker will send you a targeted link via text message claiming to be your bank citing that suspicious activity has been detected. It contains a link to a rather obvious looking suspicious URL that has nothing to do with your banking URL and generally contains random characters. However, it feeds into people’s stress in that something is wrong with their finances, and they don’t think about the fact that it may be a scam, thus why it is successful in harvesting user information. Banks generally communicate via phone call, their legitimate website, or in their designated mobile apps if something is wrong with your account.
Journal Entry #8
The media is a big influencer in how an average person may interpret various methods of cybersecurity and hacking. Hollywood has always skirted the edges of realism in favor of action packed or more interesting scenes for their movies. However, that doesn’t mean that they always miss the mark. In movies with inflated budgets such as “The Girl With the Dragon Tattoo”, studios are able to hire on various cybersecurity experts that allow more realism to be injected into the movie scenes. This doesn’t necessarily mean that they will always do so, but it does seem to be becoming more and more common in movie releases dating back to the late 1980s when computer hacking was a cool movie trope. The media does a great job in influencing people to believe that cybersecurity and hacking is a bunch of uber-attractive jack of all trade type people that have access to technology that looks like it came from 100 years into the future. However, the reality is that most hackers and bad actors are indistinguishable from you and I, and that they use more realistic measures such as focusing on easier targets, conducting surveillance of a network prior to engaging in potential hacks, and more or less “eating cold pizza and drinking warm energy drinks” in a room for hours to days in an effort to decrypt a password and gain access to the system. To conclude, the media’s influence on society in how cybersecurity is conducted is rather “hit-or-miss” in that it does a good job of depicting both accurate, as well as far-fetched scenarios in regards to hacking and systems securities and vulnerabilities.
Journal Entry #9
After taking the “Social media disorder scale” I found that I scored a three out of nine. This is not surprising to me as I do acknowledge that I suffer from some form of social media dependency in that I have suffered from withdrawal, as well as that I have failed at maintaining a consistent and impactful absence from social media. My views on the test are that whilst it is a very basic indicator of social media use disorder, it does get the job done and could potentially cause test-takers to reflect on their social media usage, as it has done for me. Often times I find myself procrastinating on homework or other obligations by “doom-scrolling” through apps such as Facebook, Instagram, and Tik-Tok. I have somewhat rectified that by replacing screen time with books, or if I do feel the need for screen time, ensuring that it is beneficial to me by watching videos to gain knowledge of my field and other useful information as opposed to watching meaningless and hollow content that is posted for likes and ad revenue. As for why I believe different patterns are found around the world; I believe it is due to a variety of factors such as how social media has been implemented into a specific society such as how we see the Western World’s culture in which it is considered weird and even off-putting to many if someone has negligible or no social media presence. Furthermore, in other countries and regions of the world that suffer from poverty, social media may be used to raise awareness to their situations, or to perform nefarious activities such as phishing and social engineering as a means to steal from people in order to provide for their families or acquire something to eat. Whatever the reasons may be, I believe social media has some positives and some negatives and it is up to us to police ourselves in its usage and ensure that we are not letting ourselves be absorbed into an online world while ignoring the physical world that we actually reside in.
Journal Entry #11
Laissez-faire Economic Theory: This theory pertains to the sample breach letter as this theory emphasizes minimal government intervention in regard to the economics of private businesses. Regarding the breach letter, the company relied on a third-party platform provider as opposed to the government in how they chose to protect their data. Unfortunately, this approach comes with negative consequences such as the data breach in the aforementioned letter.
Rational Choice Economic Theory: This theory pertains to the sample breach letter as this theory outlines that individuals utilize rational assessment to make decisions, performing cognitive functions such as the weighing of costs and benefits in financial situations. This relates to the breach letter as the company informed their customers of the data breach which will allow the customers to weigh their options and perform damage control such as cancelling cards and potentially terminating their accounts with this company.
Social Exchange Theory: This theory pertains to the sample breach letter because social exchange theory focuses on social interactions as a series of exchanges to maximize potential gains and reduce costs and negative impacts. This relates to the breach letter as the company is providing their customers information regarding the data breach. In exchange, the customers are encouraged to take actions to protect themselves.
Social Learning Theory: This theory pertains to the sample breach letter as this theory suggests that people learn from the observance of others and how their actions lead to certain consequences. Regarding the breach letter, customers were informed of the data breach and learning from previous data breaches in the past, have learned that they need to take action such as cancelling credit cards to avoid further negative consequences.
Journal Entry #12
In the article “Hacking for good: Leveraging HackerOne data to develop an economic model of Bug Bounties” much is discussed regarding a new economic model known as “bug bounties”. This economic model essentially creates a program in which freelance security researchers or “hackers” are “tasked with finding bugs in corporate IT systems and code bases and cogently explaining them to the companies.1 Companies provide hackers with monetary rewards, called bounties, based upon their performance” (Kiran Sridhar, Ming Ng 2021). Regarding the findings, the journal states that there is a low elasticity in prices for these bounties as many hackers that are not well-established care more so about reputation and experience, rather than monetary gain. Furthermore, it was found that certain industries such as Finance and Healthcare showed smaller results in bugs being discovered. This was ascertained to be due to the fact that the information in these fields holds more value and thus bug hunters may in turn omit these from their findings in order to sell in the black market for their own monetary gain. I believe these facts are not surprising as hackers can be wild cards with all sorts of different motivations. I do think the bug bounty approach is a good idea as the article does show positive results, especially for more notable companies. I think it is also a good program for rising hackers to get some experience and build a portfolio by utilizing “white hat” hacking methods, as opposed to resorting to “black hat” methods in order to build their skillset. This program allows them to perform with the methods of the latter and reduces harm to innocent users.
Journal Entry #14
I believe the 5 most serious violations you can commit on the internet are the sharing of passwords, addresses photos, and photos of others due to the violation of an individual’s privacy, as well as the detriment you can cause to someone else with this information to include the hacking of social media, bank accounts, and the potential physical harm that can befall a person who’s address is made public. Secondly, bullying and trolling is another more heinous violation as you are actively causing negative consequences to a person’s social life and mental health which can lead to more serious and deadly consequences. Thirdly, faking your own identity makes the list due to the fact that many crimes can be committed due to anonymity and the diminished fear of getting caught by authorities. Collecting information about children is also heinous as this contributes to aggressively disgusting acts such as the distribution of child pornography, as well as the general detriment to an underage child’s wellbeing throughout life. Lastly, illegal searches on the internet are all encompassing as they can include identity theft, bullying, hacking, child abuse, and so forth, and thus are in my top five.
Journal Entry #15
The pathway that Davin mentioned in his TED talk both encouraged, as well as discouraged me regarding my thinking on the matter. Firstly, it encouraged me as he had mentioned he was simply just an accountant prior to getting into the field of Information technology before essentially getting lucky by putting his skillset out there for his company and achieving a “promotion” of sorts when it came to his work history. This allowed him to join the team in Australia that propelled his career into digital forensics. To iterate on my discouragement in hearing his pathway, I thought back to how excited I was when seeing that the field of cybersecurity (to include digital forensics) had a 100 percent employability rate. However, after scouring various job sites such as Indeed and LinkedIn, I noticed that none of these fields were searching for “entry-level straight out of college” applicants, but rather those with at least 5 years of experience in the field. Davin’s pathway to digital forensics has further strengthened my belief that to break into the field of cybersecurity, a simple college degree and some certifications isn’t necessarily all you need, but rather you must enter into the IT field at a lower level such as help desk in order to look out for the opportunities to excel and network your way into a specific discipline of cybersecurity.