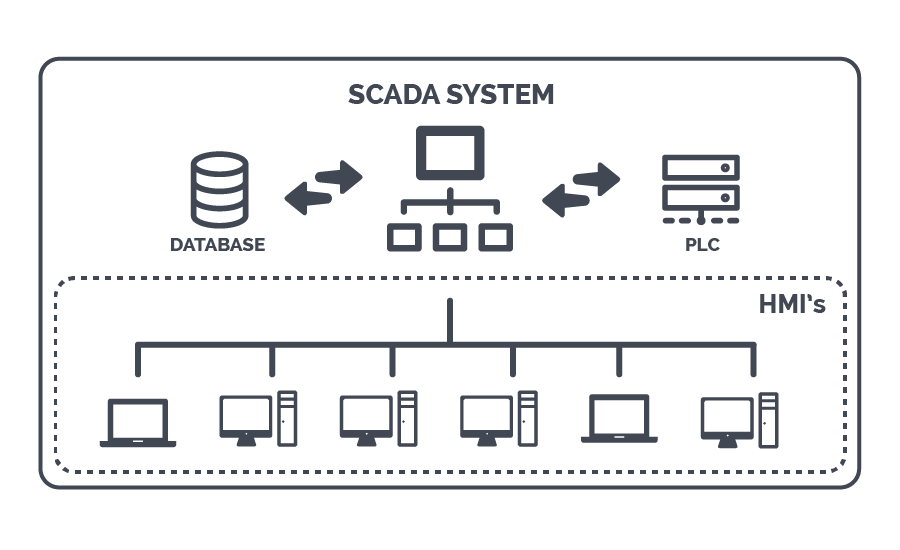
The Supervisory Control and Data Acquisition or SCADA system manages critical infrastructures. These critical infrastructure processes include things such as transportation, electric grids, and water supply related networks like airports, water treatment and or power generation. However, the process systems come with risk from human related issues and cyber attacks that can disrupt society as a whole. The SCADA system plays a key role in mitigating these risks with proper management, advanced security measures and monitoring any threats in real time to function properly during these processes.
Introduction
The SCADA or Supervisory Control and Data Acquisition system implements databases or systems that focus on monitoring both time and controlling data within critical infrastructures. The system supports today’s society industries that we use like water supplies, transportation and energy usages. The system sounds very good once explained but it also has vulnerabilities and potential risk against cyber attacks, operators making mistakes, outdated software and low management with security. The SCADA system will have issues but is naturally seen as safe and secured through a lot of eyes in society. This paper is going to explain the role of how the SCADA system mitigates these risks while also going over potential vulnerability processes it may face.
SCADA System Vulnerabilities
Cyber Attacks
The biggest vulnerability the SCADA system has are potential cyber attacks from hackers. Society today has become more attached towards technology helping since it’s easier and makes things less difficult that we tend to not pay attention to any risk ( Munro, K. 2008 ). The system is connected via the internet to several industry systems so this makes the SCADA system a prime target for hackers to take advantage. Attackers can manipulate operation procedures or disrupt and steal any data in the SCADA System ( Irmak .E, 2018 ).. These attacks can be ransomware, data breaches and or denial of service attacks that can lead to compromising societies water supply, electric fields, and transportation lines that we use in our everyday life.
Operation errors and Outdated Systems
The SCADA system has other vulnerabilities such as old operating systems or bad human interaction with handling the system and its components ( Coffey, K, 2018 ). SCADA technology often are exposed to old field devices due to no updated firmware configuration. This can lead to new cyber attack vectors damaging the systems that are connected to important business and transportation infrastructures, Which can lead to system failure rather than protecting and making sure they’re secured for society usage ( Coffey, K, 2018 ). The operator, who is in charge of handling the system can make errors with access controls, inside threats or ignoring malfunctions. Operators can also be overloaded with alarm messages that the system notifies so they can often miss some or not deal with the malfunction in time before it clears.
Risk Mitigation of the SCADA System
Real Time Monitoring and Automation
The SCADA system already provides real-time monitoring in coordinates while also sending alarm messages to operators to address and fix the issues ( Ali, S. 1970). The SCADA system has communication protocols that use an array of network probes to detect function code scans or any other exploitation ( Ali, S. 1970). Automation can lower operator errors by quickly fixing any compromised data or disruptions in any infrastructure process. Operators can implement firewalls and system updates, which are really powerful security countermeasures but they have to be placed and divided between each endpoint of communication to work against attacks ( Fovino, I. N.,1970).
Physical and Advanced Security Measures
The SCADA system can integrate physical measures to protect the outside of the infrastructure such as cameras, biometric controls and sensors to prevent any unauthorized access. Advanced security measures can protect the inside of the infrastructure by preventing any attackers from data by using IDS sensors, encryption communication protocols or multiple authentication ( Fovino, I. N.,1970). A secured communication protocol can make sure no interruption is occurring when transferring data through networks. A role based access control can mitigate any access depending on the user’s role. The personnel with authorized access to use specific actions with the SCADA components ( Figueroa-Lorenzo, S. 2019 ).
Conclusion
The SCADA system has a huge part in society operating the critical infrastructure but the system does have risks like physical damage and cyber attacks. The line of work requires a lot of attention and learning how to minimize any new risk with new mitigating strategies. The need to use advanced and physical security measures, real-time coordinated monitoring and automation is crucial within operating the SCADA system. Critical infrastructure threats evolve as time goes on, so developing new security features around the system is essential to guard not just the system but public safety as well.
References
————–
Eric, B., Peter, W., & Munro, K. (2008, January 25). SCADA – a critical situation. Network Security. https://www.sciencedirect.com/science/article/abs/pii/S1353485808700059
Irmak, E., & Erkek, I. (2018, May 7). An overview of cyber-attack vectors on SCADA systems | IEEE conference publication | IEEE xplore. An overview of cyber-attack vectors on SCADA systems. https://ieeexplore.ieee.org/abstract/document/8355379/
Coffey, K., Smith, R., Maglaras, L., & Janicke, H. (2018). Vulnerability analysis of network scanning on SCADA systems. Security and Communication Networks, 2018, 1–21. https://doi.org/10.1155/2018/3794603
Ali, S. (1970, January 1). Security in SCADA system: A technical report on cyber attacks and risk assessment methodologies. SpringerLink. https://link.springer.com/chapter/10.1007/978-3-031-54820-8_35
Pidikiti, D. S., Kalluri, R., Kumar, R. K. S., & Bindhumadhava, B. S. (2013, April 19). SCADA communication protocols: Vulnerabilities, attacks and possible mitigations – CSI transactions on ICT. SpringerLink. https://link.springer.com/article/10.1007/s40012-013-0013-5
Fovino, I. N. (1970, January 1). SCADA system Cyber Security. SpringerLink. https://link.springer.com/chapter/10.1007/978-1-4614-7915-4_20
Figueroa-Lorenzo, S., Añorga, J., & Arrizabalaga, S. (2019, October 14). A role-based access control model in Modbus SCADA systems. A centralized model approach. MDPI. https://www.mdpi.com/1424-8220/19/20/4455