With healthcare organizations having extraordinary storage of and access to all of patient information, hackers view healthcare organizations as prime targets for their black market pay day and cyber-business objectives. It is the responsibility of every healthcare organization to keep their patient’s records secure. Like other cybersecurity challenges, DDoS attacks are especially harmful to healthcare providers who need access to the network to provide proper patient care, send and receive emails, fill prescriptions, access records, and retrieve information. Healthcare is an attractive target for cyber-attacks for a variety of reasons. You should be aware of the reasons why healthcare organizations are more vulnerable to cyber-attacks as a patient or a provider.
The HIPAA Security Rule mandates that health-care providers preserve electronic health records (EHRs) with appropriate physical and technical protections to maintain the security of patient data. Breaches of over 500 records must be notified, whether they are the result of a hacking attack, an accident, lost or stolen equipment, or illegal internal access. This contains ransomware infections as of July. To prevent a hack from occurring in the first place, proper application and network security is critical. Once someone has gained access to healthcare systems, encryption is the greatest approach to keep patient data from being accessed. It’s critical that encryption be used both in transit and at rest, and that third parties and suppliers with access to healthcare networks or databases handle patient data correctly. To prevent data breaches caused by employee mistake, such as a misplaced device or an inadvertent disclosure, training on the usage and management of PHI is suggested.
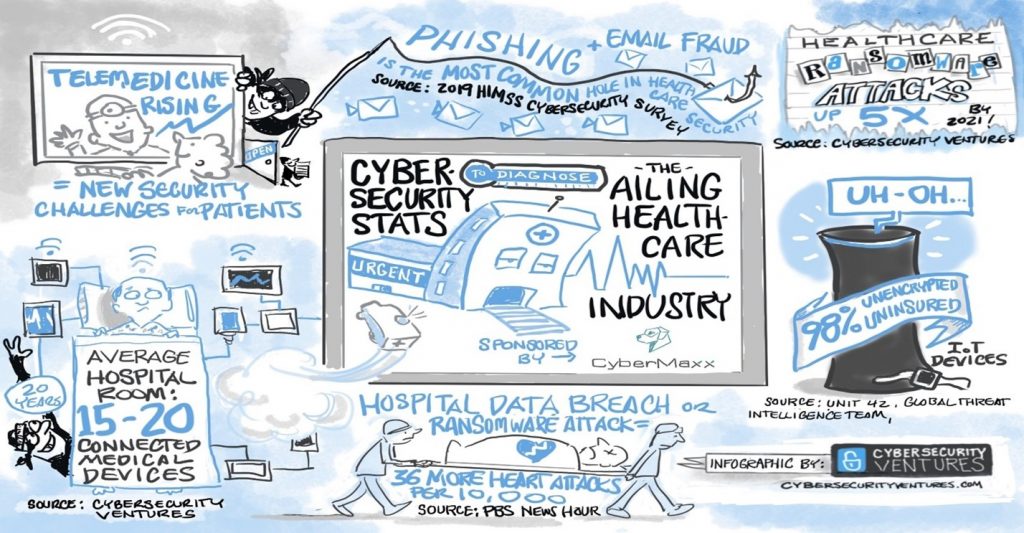
The recent rise of ransomware-related hospital reports is difficult to ignore. The MS-ISAC, in collaboration with our colleagues at the National Health Information Sharing and Analysis Center (NH-ISAC) and the Financial Services Information Sharing and Analysis Center (FS-ISAC), has organized trainings on how to protect against ransomware around the nation. Ransomware infects computers and data, making them unavailable until a ransom is paid. Critical processes in the healthcare business are delayed or entirely shut down when this happens. Hospitals are therefore compelled to revert to pen and paper, slowing down the medical procedure and sapping monies that could have gone into hospital modernization.
In the healthcare industry, breaches are common. Credential-stealing malware, an insider who purposely or mistakenly releases patient data, or stolen laptops or other devices are all examples of situations that might lead to this. On the black market, personal health information (PHI) is more valuable than credit card credentials or standard Personally Identifiable Information (PII). As a result, cyber thieves have a greater motivation to attack medical databases. They can either sell the PHI or utilize it for their own benefit. According to the health and human services breach report, approximately 15 million health records have been affected by data breaches as of this writing (Center for Internet Security).
Hacktivists and cybercriminals utilize distributed denial of service (DDoS) attacks to overwhelm a network and render it unusable. This can be a significant issue for healthcare practitioners who require network connection to offer effective patient care or Internet access to send and receive emails, prescriptions, records, and other information. While some DDoS assaults are purely opportunistic or even unintentional, many others are motivated by a social, political, ideological, or economical motive tied to a scenario that enrages cyber threat actors.
DDoS assaults may take a multitude of forms and knowing which sort of attack is taking place is crucial to appropriately mitigating the situation. Maintaining a successful collaboration with your upstream network service provider, as well as cooperating with organizations who provide DDoS mitigation services, are general advice for protection against DDoS assaults.
Organizations are frequently too busy with safeguarding their company and network from external threats to address the very real and severe risk that may exist within their own walls – insiders. Because of their lawful access to private systems, insiders are immune to typical cybersecurity measures like intrusion detection devices and physical security. They may also have a greater understanding of the network’s structure and weaknesses than practically anybody on the outside, or the capacity to acquire that information. While some insiders are merely inattentive, others are malicious. Insider threats include a wide range of personnel, from those who unwittingly click on a malicious link that compromises the network or lose a work device carrying sensitive data to those who intentionally give away access codes or sell PHI/PII for profit.
Other insiders are frequently the greatest approach to detect an inside threat. The best method to defend your company is to teach your users and workers how to spot and disclose insider threats, as well as how to avoid becoming one accidentally. There are several open source insider threat tools available, including training programs and instructional materials for businesses and their personnel. These contain descriptions of what to watch for in coworkers in terms of suspicious conduct and behavioral changes, as well as when and who to report it to.
Scammers use a faked email or compromised account to deceive employees into making a money transfer to another (fraudulent) account, dubbed the “Billion Dollar Scam” by the Federal Bureau of Investigation (FBI). Scammers usually always pose as a high-ranking employee, such as the CEO or CFO. The scam has grown 1,300 percent since 2015 because the actors usually do some research on their targets first, know how to sound like the person they’re impersonating, and only send the email to a few people (usually those who deal with money), allowing it to bypass basic security measures like email filtering. This fraud comes in many forms, and it affects businesses from all sectors and all over the world. This sort of fraud, which has numerous varieties and can result in lost money, PII/PHI, or products such as prescription medications, should be avoided by hospitals and medical institutes.
Would an employee in your company’s finance department execute a wire transfer or a goods buy if they got an email from your CEO tomorrow? The easiest method to prevent employees from falling for this sort of fraud is to raise their awareness and comprehension of it. Some businesses also use precautionary approval processes or postpone money transfer requests for a longer length of time to ensure their validity. Be wary of abrupt changes in previously conventional corporate procedures, such as virtual and physical addresses. If you usually connect with someone by email and they request something via a “personal” email, utilize other means of communication to be sure you’re still communicating with the right person.
Healthcare firms should also do more, including increasing their cybersecurity investment to protect infrastructure, patch vulnerabilities, and upgrade systems, as well as developing and maintaining the needed degree of cybersecurity awareness and training for their employees. In addition, healthcare institutions must adhere to due diligence and established incident handling procedures. Security must be built into software and security technologies from the start. Human resources are in short supply in the healthcare cybersecurity field. There is a need for more individuals to be trained and deployed. Cybercriminals continue to attack healthcare businesses. Electronic Health Records (EHRs) are frequently sold in bulk or in sections in the cyber underground. The information included in these EHRs can be utilized to purchase unlawful items, including as prescription medicines, construct false identities, or produce fraudulent tax returns.
Patient data stored in EHR software is extremely precious and should be protected at all costs. Providers must concentrate on safeguarding their goods and systems, which includes the electronic health records (EHRs) they maintain. To do so, healthcare providers must inventory all IoT devices linked to the network, ensure that they are patched, and that the default password is no longer used. To mitigate the consequences of data breaches, EHR software providers must provide robust encryption for stored data. In order to prevent unwanted access to data stored remotely, healthcare organizations must update their authentication procedures.
EHRs should be actively secured by healthcare organizations that use EHR software. This may be accomplished by teaching employees who have access to EHRs on the fundamentals of cybersecurity and risk management. These organizations may also enlist the help of security firms to safeguard data housed on their premises. Attackers may be less likely to use the institution’s own network as a gateway into the EHR provider’s network if the institution’s network security is strong.
Cites Referenced:
Asimily. (2021, April 16). Eight Reasons Why Healthcare is the Prime Target for Cyber Attacks. Asimily.Com. https://asimily.com/post/eight-reasons-why-healthcare-is-the-prime-target-for-cyber-attacks
CIS (Center for Internet Security). (2019, January 7). Resources. CIS. https://www.cisecurity.org/blog
Duguin, S. (2021, November 17). If healthcare doesn’t strengthen its cybersecurity, it could soon be in critical condition. World Economic Forum. https://www.weforum.org:443/agenda/2021/11/healthcare-cybersecurity
Fuentes, M. R. (2021). Cybercrime and Other Threats Faced by the Healthcare Industry. TrendMicro. Retrieved October 9, 2021, from https://documents.trendmicro.com/assets/wp/wp-cybercrime-and-other-threats-faced-by-the-healthcare-industry.pdf

Leave a Reply