Cybersecurity Analysis
I have developed a majority of my cybersecurity analysis skill through my academic education, my internship experience, and industry certifications. Prior to enrolling with Old Dominion University, I had very little experience with anything related to Cybersecurity since my background was predominately healthcare related. Yet through these opportunities, I have developed the ability to complete cybersecurity analyses with an emphasis on event monitoring, threat detection, and risk/compliance.
Event Monitoring
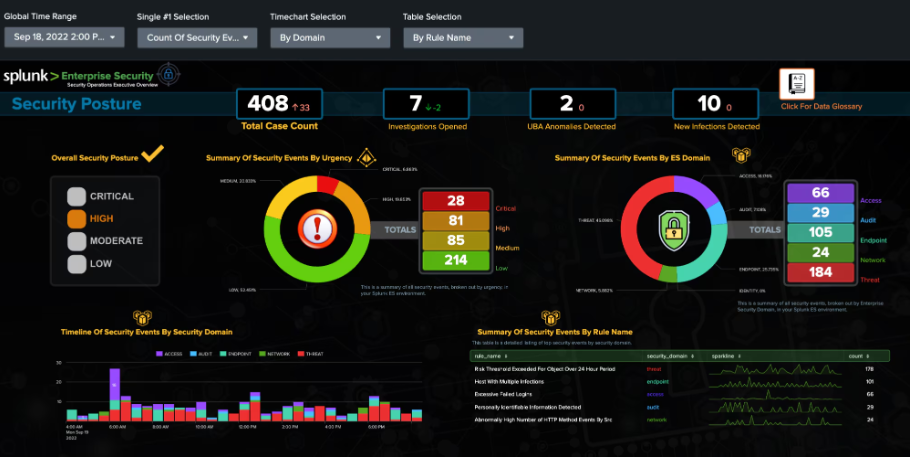
During my education at Old Dominion, one item that was briefly covered was SIEMs (Security Information and Event Management). While interning on the Cybersecurity team at the City of Virginia Beach, I was exposed to and gained experience with two different SIEMs, Splunk and Palo Alto’s XSIAM. Utilizing these two platforms, I gained experience monitoring and tracking cyber event data to utilize in trend analysis and threat-hunting.
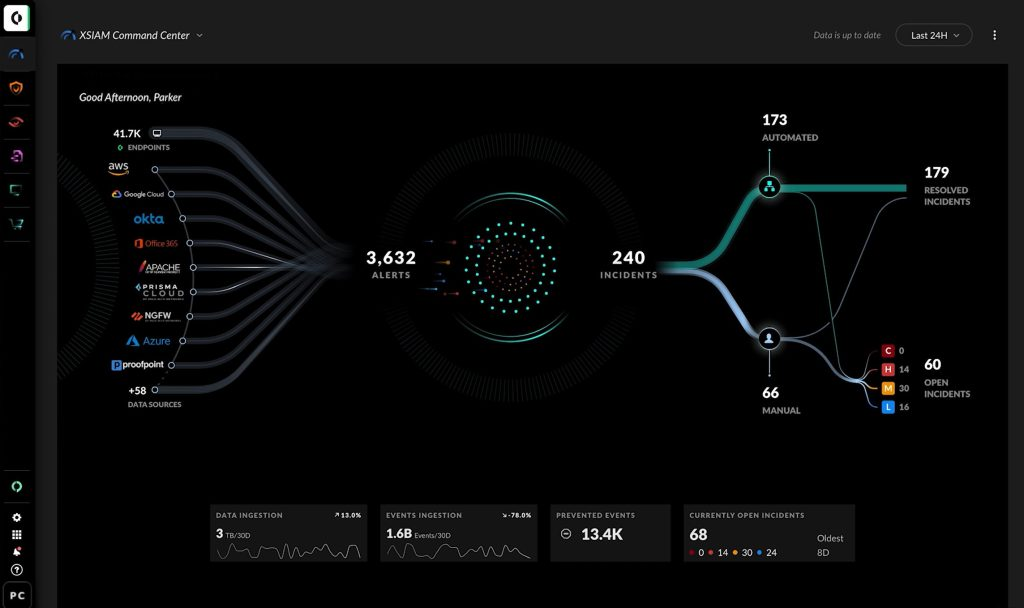
These two artifacts are examples of the SIEM dashboards I utilized for event monitoring during my internship experience. They both illustrate the process of the SIEM taking in raw data from several programs and platforms used throughout the organization and indicating alerts found in that data. If an alert warrants further investigation, it will be escalated to an incident. In some newer SIEM options, like XSIAM, the incident resolution process can be automated, and all other are addressed by the Cybersecurity analyst.
Threat Detection and Investigation
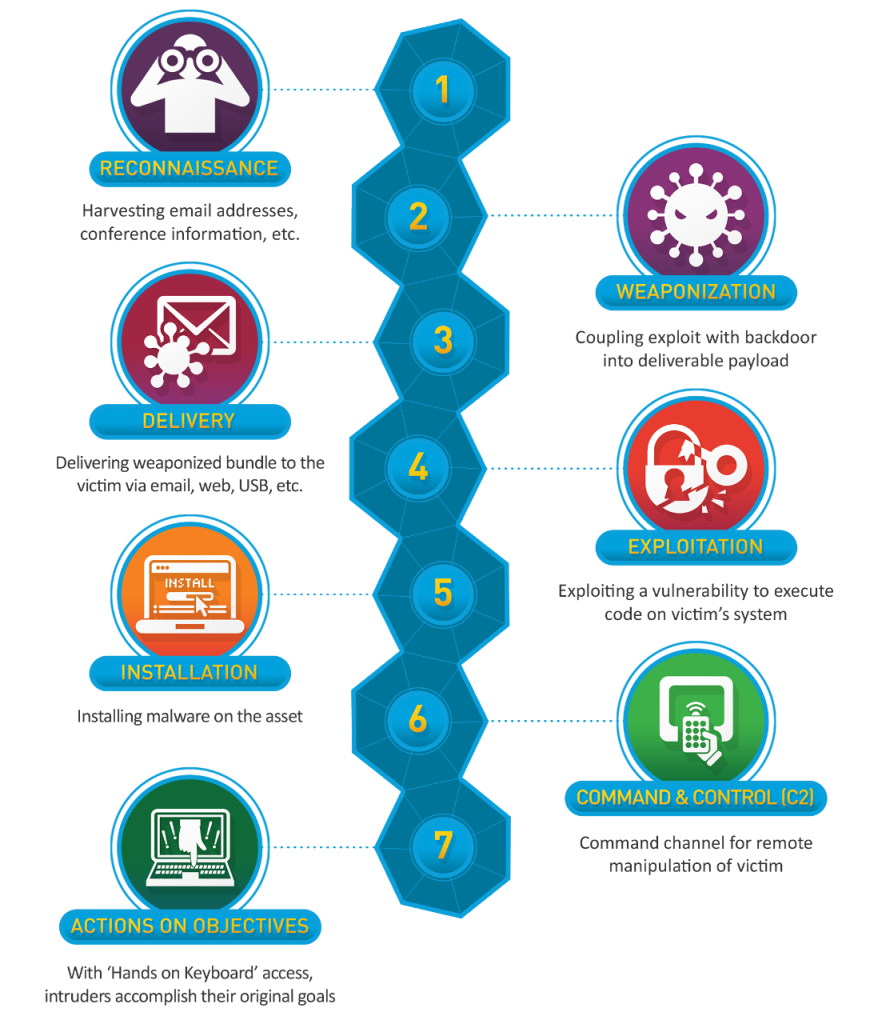
When it comes the investigative process to determine whether or not a threat is credible or not, I utilize my educational background extensively for this skill. One piece of invaluable information I learned about in school, then applied to my role every day as an Intern was the Cyber Kill Chain. This framework details the steps attackers take to when implementing and conducting a cyberattack. This is a piece of knowledge when completing a threat investigation. By understanding what each step looks like, and what the attacker’s next goal might be has helped me detect a credible threat and take action to ensure the attacker is either not able to continue the attack, or limit the extent of damage resulting from the attack.
During my experience at the City of Virginia Beach, I used systems like Microsoft Defender for Endpoint and Microsoft Intune to carry out my threat investigations. For each investigation, I created a detailed report regarding the nature and credibility of the threat, as well as any actions taken as a result of the investigation. These reports were documented using ServiceNow, an IT Service Management (ITSM) platform.
Risk and Compliance
Risk and compliance are two important topics when addressing proactive cybersecurity. By understanding the Cybersecurity best practices, I can detail the risks associated with not maintaining compliance with those best practices. I have demonstrated this skill by obtaining the CompTIA Security + certification. This industry certificate illustrates a knowledge on the topics of:
- Risk management: explaining risk identification, assessment, analysis, register, tolerance, appetite, strategies, reporting, and business impact analysis (BIA).
- Third-party risk: managing vendor assessment, selection, agreements, monitoring, questionnaires, and rules of engagement.
- Security compliance: summarizing compliance reporting, consequences of non-compliance, monitoring, and privacy.