Computer Investigation Entail
As information technology is increasingly develope, many criminals have moved their “working area” from the real world to the digital world. The purpose of computer investigation is to search and analyze data on computers. The computer investigator’s mission is to help the court get the most accurate criminal evidence. The skills that a computer investigator needs are: Technical Aptitude, Attention to Detail, Analytical Skills, Ability to Work with Challenging Material, Comprehension of Cybersecurity Fundamentals.
Computer Investigation Terms
EXIF Metadata: Exchangeable image file format is a standard that specifies the formats for images, sound, and ancillary tags used by digital cameras, scanners and other systems handling image and sound files recorded by digital cameras
OSINT: Open Source Intelligence, anything that is open to the public (Google, Bing, etc.)
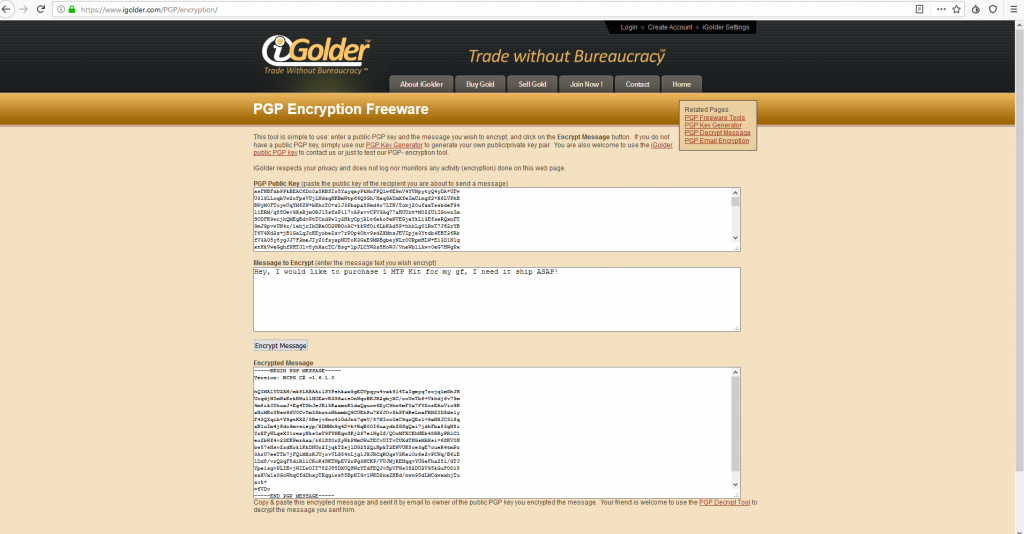
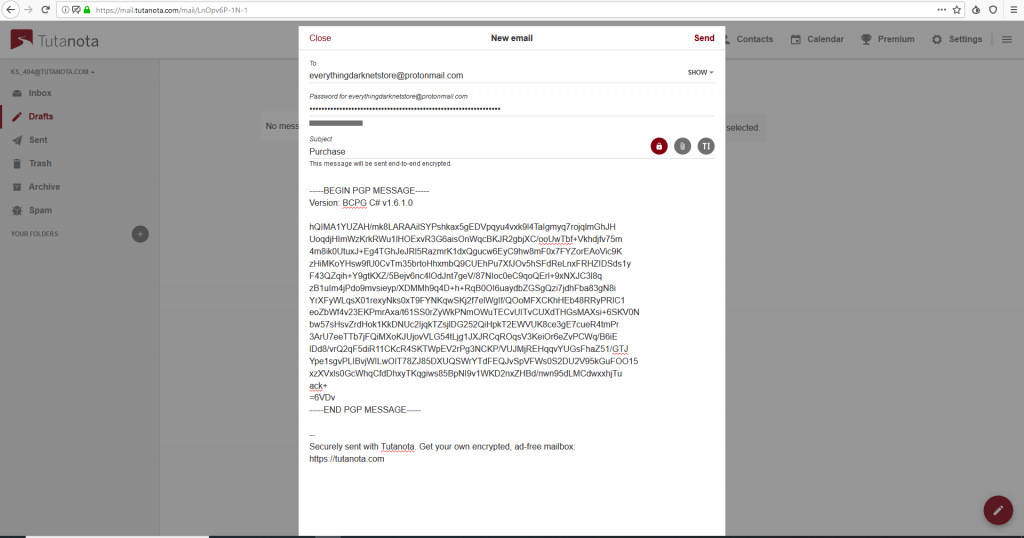
Encryption: the process of encoding a message or information in such a way that only authorized parties can access it and those who are not authorized cannot.
PGP Public/Private Key: Public key use to encrypt data and Private key used to decrypt data. In other words, the Public key turns the original data into the unreadable message, and the Private key turns that message back to the original data.
Steganography: concealing a file, message, image, or video within another file, message, image, or video
Computer Investigation Tools
Autopsy: computer software that helps scan and analyze the subject’s file/data. Some functions of Autopsy are keyword search, email analysis, file type Sorting, tags, etc.
Steganography Decoder: a software to unhide all of the secret data like text or image behind an image.
EXIF Metadata: a software that scan an image and show the record of that image. The data shows information such as camera model, exposure, aperture, ISO, camera mode, flash mode, etc.
Gallery
Below are some examples of my online investigation.