Mahad Ahmad
Digital Transformation and Technology (DTT) Division at Old Dominion University
CYSE 368 – Cybersecurity Internship – Fall 2025
Prof. Teresa Duvall
December 1, 2025
Contents
- Introduction
- Learning Outcomes and Initial Expectations
- Overview of Old Dominion University and Internship Orientation
- Management Environment and Supervision
- Major Work Duties, Assignments, and Projects
- Use of Cybersecurity Skills and Knowledge
- Curriculum Preparation and Academic Connections
- Evaluation of Internship Outcomes
- Motivating Aspects of the Internship
- Discouraging Aspects of the Internship
- Challenging Aspects of the Internship
- Recommendations for Future Interns
- Conclusion
- Appendix A
Appendix B
Appendix C
1. Introduction
Completing an internship is often the most practical way for a cybersecurity student to bridge academic knowledge with real industry demands. My goal in pursuing an internship was to gain firsthand experience working in a professional technical environment while applying the foundational skills I had learned in coursework and through certification study. I knew that cybersecurity is a field where hands-on exposure matters just as much as theoretical understanding, so gaining real operational experience was important for my development. Entering the internship, I expected to strengthen my applied skills, learn how professional teams collaborate on technical projects, and understand the daily realities of working in a cybersecurity or cloud development organization.
I chose to complete my internship through Old Dominion University’s Digital Transformation and Technology (DTT) division because it offered a unique opportunity to work within a large, diverse institution that relies heavily on secure, stable, and scalable digital infrastructure. As a student, I had interacted with many of ODU’s systems, but I had never seen what happens behind the scenes. The internship promised exposure to authentic development processes, internal tools, and operational practices that support the university’s web services and cloud environments. I expected that working internally at ODU would allow me to participate in meaningful projects rather than hypothetical exercises, which was important for building confidence and practical competence.
Internships in cybersecurity often emphasize professional readiness, collaboration, and adaptability, which are critical traits for emerging analysts and engineers (National Initiative for Cybersecurity Careers and Studies, 2023). This paper provides a comprehensive reflection on my internship experience, including the environment, responsibilities, learning outcomes, challenges, and the way this opportunity will influence both my academic path and professional future.
2. Learning Outcomes and Initial Expectations
Before beginning my internship with the Digital Transformation and Technology (DTT) division at Old Dominion University, I spent time identifying what I hoped to gain from the experience. Because cybersecurity is a field shaped heavily by hands-on practice, I understood that an internship would be one of the most important steps in preparing for my career. Classroom learning and certifications provided foundational knowledge, but I knew that working on real systems and interacting with development workflows would fill the gaps that academic environments cannot fully replicate.
The first learning outcome I set for myself was to gain meaningful technical experience that would be useful in future cybersecurity or cloud security roles. I wanted to work with actual security tools rather than simulated labs and gain exposure to scanning methods, tooling limitations, and the practical challenges that come with identifying and interpreting vulnerabilities. I expected that the internship would push me beyond theoretical concepts and allow me to engage with tools that professionals use in real environments. This objective mattered to me because practical technical skill is a major differentiator when applying for entry-level roles in cybersecurity.
My second learning outcome was to understand how agile development teams operate. I had learned about agile methodology in academic settings, but I wanted to experience how it functions in an actual technical organization. Observing daily standups, sprint planning, retrospectives, and cross-team coordination was important to me. I hoped to understand how workloads are prioritized, how developers communicate about blockers, and how teams adapt when tasks evolve. Developing this understanding would help prepare me for collaborating effectively in professional cloud or security teams, where agile practices are commonly used.
My third learning outcome was to gain hands-on exposure to cloud security. Cloud computing has become central to modern cybersecurity practices, and AWS, Azure, and Google Cloud all have their own security frameworks, policies, and tools. I wanted the internship to give me opportunities to see how cloud infrastructures are managed, what cloud security configurations look like, and how cloud environments support automation, logging, scanning, or continuous integration pipelines. As someone planning a career in cloud-focused cybersecurity, I believed this experience would be a valuable stepping stone.
Beyond these three main learning outcomes, I also entered the internship with general expectations about how the experience would broaden my professional development. I expected to receive structured guidance from supervisors, regular feedback on my progress, and support when navigating new tools. I anticipated working collaboratively with other interns or team members on shared tasks. I also expected that the internship would introduce me to the professional culture of a technical team, including communication habits, decision-making processes, and internal expectations around reporting or documentation.
In addition to technical growth, I hoped that the internship would help me refine my sense of direction within cybersecurity. The field is broad, spanning network security, cloud security, incident response, DevSecOps, governance and compliance, penetration testing, and more. By working in a cloud development environment, I expected to gain clarity about which areas most appealed to me. The opportunity to observe how security integrates with development processes, version control systems, and cloud operations was especially appealing because I wanted to understand how security fits into the full lifecycle of modern applications.
Overall, my expectations for the internship were ambitious but realistic. I understood that as an intern, I might be responsible for introductory tasks, but I expected that the internship environment would support growth, provide mentorship, and expose me to processes that are essential in cybersecurity careers. These expectations shaped the mindset with which I entered the internship and the lens through which I later evaluated the experience and its outcomes.
3. Overview of Old Dominion University and Internship Orientation
Old Dominion University (ODU) is a public research institution located in Norfolk, Virginia. The university was founded in 1930 as the Norfolk Division of the College of William and Mary and has grown over the decades into a major doctoral-granting university that serves students from more than ninety countries (Old Dominion University, 2024). ODU is recognized for its commitment to research, innovation, and community engagement, and it supports a diverse student population across programs in engineering, sciences, business, cybersecurity, and many other fields. The Digital Transformation and Technology division plays an important role in supporting the university’s technological infrastructure and operational systems, including web services, cloud environments, and cybersecurity functions.
My internship orientation was conducted through a scheduled Zoom meeting with DTT staff responsible for onboarding new student workers and interns. During this meeting, I and another intern were guided through the initial setup of our work laptops, including configuring Zoom, Microsoft Teams, email access, and best practices for communication. They also ensured that we were able to connect to the ODU VPN in order to securely access internal web resources. Additionally, the orientation included an overview of ODU’s history, its mission, and the structure of the DTT division. This helped us understand not only where our work fit into the university’s broader operations but also the scale and importance of the systems we were supporting.
The work laptop was shipped directly to me, and the onboarding team was thorough in ensuring that everything functioned properly. My initial impression of the orientation process was very positive. The team was detailed and attentive, which gave me confidence that the internship would be structured and that support would be available as needed.
4. Management Environment and Supervision
The management environment during my internship was unique in that it involved almost no direct supervision. At the beginning of the semester, my supervisor outlined a broad task that the two interns were expected to complete. The task involved researching options for code security scanning tools in GitLab and implementing a solution that could automatically scan code repositories upon commits or merge requests. The requirements were flexible but ambitious, focusing on detecting vulnerabilities such as unsanitized input, dependency risks, cloud configuration issues, and more. Our supervisor emphasized that if fully automated scanning was not possible using free tools, we should aim for the closest achievable solution.
After this initial task description, there was very little follow up. There were no recurring check-ins, deadlines, or structured progress evaluations. Each intern was responsible for independently determining what to research, how to divide the work, and what tools to evaluate. I took responsibility for the dynamic application security testing (DAST) portion of the assignment, while the other intern focused on static analysis. Although I eventually completed my part of the task, the lack of structure created challenges. Without set milestones or feedback, I often worked with the sense that I was building something important but without confirmation that it would actually be implemented or reviewed in depth.
This management approach offered freedom but also uncertainty. In some ways, the independence encouraged creative problem solving. However, in other ways, it limited the clarity and direction typically expected in an internship where the primary purpose is learning. Structure tends to help interns understand expectations, gain timely feedback, and maintain alignment with team goals. Because these elements were largely absent, I often had to rely on my own initiative and problem solving skills to stay on track.
5. Major Work Duties, Assignments, and Projects
My core responsibilities centered on implementing dynamic application security testing for ODU’s preproduction website using OWASP ZAP. The goal was not only to run manual scans but to fully automate the process within GitLab CI so that every new commit or merge request would trigger a scan. The results needed to be summarized and automatically posted as a comment on the merge request, allowing developers to quickly see any potential vulnerabilities before pushing code to production.
To achieve this, I first experimented with the OWASP ZAP packaged scans, which offered quick scanning options but lacked the flexibility needed for the full automation we required. An excerpt from the HTML vulnerability report generated during the active scan on the staging site is provided in Appendix B to illustrate the structure and detail of the scan output. I then transitioned to the ZAP Automation Framework, which is a YAML-based system that allows for detailed configuration of scanning rules, alert filters, and targeted scanning sequences. I developed an automation solution that could detect the target URL, run the appropriate scans, generate JSON and HTML reports, categorize findings by severity, and post a summarized comment to GitLab using its API.
The second major responsibility was integrating this scan output into GitLab merge requests through a Python-based automation script. Appendix C provides a screenshot of the automated passive scan triggered during a merge request, demonstrating how the CI pipeline executed the scan and verified its successful completion within the development workflow. This required handling API tokens, interacting with GitLab’s merge request endpoints, and formatting scan results in a readable and consistent way. The final solution successfully automated both the scanning process and the reporting process, reducing the amount of manual review typically required before merges. The final automated merge request comment generated by the DAST pipeline is shown in Appendix A, which provides a visual example of how the scan results were summarized and integrated into the developer workflow.
These tasks were valuable to the DTT team because they provided a reusable security pipeline concept that could help catch vulnerabilities earlier in development. While it is unclear whether my work will be formally adopted into their standard operating procedures, the results demonstrate the potential for more efficient security integration in their workflow.
6. Use of Cybersecurity Skills and Knowledge
My internship required me to use both my foundational cybersecurity knowledge and new skills that I learned entirely on the job. Before the internship, I had a general understanding of networking and security principles through my Network+ and Security+ certifications. I also had exposure to foundational cybersecurity concepts like the OWASP Top Ten, which helped when evaluating the types of vulnerabilities identified by ZAP. However, I had never used OWASP ZAP itself before this internship, and I had limited exposure to GitLab, APIs, or CI/CD pipelines.
During the internship, most of the technical progress I made involved learning the ZAP Automation Framework and integrating it into GitLab CI pipelines. I learned how to structure YAML configuration files, create alert filters to suppress false positives, parse JSON outputs for meaningful findings, and create automated summary comments that would populate under merge request activity. I also gained experience working with API tokens, refining scan parameters, and using the ZAP packaged scans when necessary.
Another important learning experience involved understanding how to use GitLab effectively. I needed to learn how to push code to branches, troubleshoot pipeline failures, read logs, and identify issues in the CI configuration. Learning this workflow was one of the most challenging parts of the internship because it required both trial and error and detailed log analysis.
Through hands-on use of DAST tooling, I also gained a clearer understanding of how vulnerability scans must be reviewed by human analysts. Many of the ZAP findings were minor or context dependent, and learning to evaluate which findings were truly relevant helped improve my understanding of real-world web security. Appendix B offers a snippet of the HTML report produced by the active scan, which demonstrates the types of findings I analyzed when validating the DAST workflow. This experience reinforced the need for combining automated scanning with professional judgment, a principle emphasized in cybersecurity practice (National Initiative for Cybersecurity Education, 2023).
7. Curriculum Preparation and Academic Connections
The curriculum at Old Dominion University provided several foundational skills that supported my internship experience, even though the work required me to learn many new concepts independently. One of the most directly applicable areas of preparation was the emphasis on Linux concepts and command-line proficiency. During the internship, I frequently interacted with Linux-style tools and commands when running scripts, managing dependencies, reviewing file structures, and troubleshooting errors in the GitLab pipeline. The familiarity I gained through ODU coursework made these tasks easier to approach and reduced the learning curve associated with debugging issues in a technical environment.
Other courses contributed indirectly by supporting my understanding of the security principles behind dynamic testing. For example, courses that introduced the OWASP Top Ten or common web vulnerabilities helped me interpret the findings produced by OWASP ZAP. Even though I had not used ZAP before, having prior knowledge of injection risks, insecure direct object references, cross-site scripting, and misconfiguration made it easier to understand why the tool flagged certain issues. This prepared me to distinguish between meaningful vulnerabilities and findings that were either low impact or expected in an internal environment.
ODU’s networking coursework also played an important role. Understanding core networking principles helped me make sense of how the preproduction website responded to scanning, how traffic flowed between components, and why certain configurations affected scan behavior. Concepts such as HTTP methods, DNS interactions, TCP handshake behavior, and routing made the ZAP results more interpretable. Without this foundational understanding, analyzing or contextualizing scan results would have been much more difficult.
In addition, scripting-oriented courses contributed to my ability to read, modify, and develop automation scripts. Even though the internship required a level of scripting that went beyond introductory coursework, the exposure I had to Python and other languages at ODU gave me enough background to extend my skills during the internship. This allowed me to work with the GitLab API, parse JSON data, and format structured output for merge request comments. Basic programming structures, such as loops, conditionals, and object formatting, became essential tools when adjusting the automation logic.
There were still several areas that the curriculum did not directly prepare me for. Working with GitLab CI/CD pipelines, for example, required knowledge of YAML structures, runtime variables, and pipeline execution behavior that I had never encountered in coursework. Similarly, interacting with GitLab’s API, managing authentication tokens, and troubleshooting pipeline failures were skills that I had to learn independently. While some cybersecurity programs include DevSecOps topics, mine did not, so these were entirely new experiences that required extensive research and trial and error.
Despite these gaps, the internship reinforced several conceptual elements of my academic studies. ODU’s emphasis on secure design principles, system hardening, and vulnerability awareness were all throughout the scanning and automation work. Seeing vulnerabilities identified in real time and learning to interpret them within the context of an operational environment deepened my understanding of why secure coding matters. It also made the theoretical concepts I had studied feel more concrete and practical.
The internship also highlighted how interconnected cybersecurity concepts are in real environments. For example, understanding a ZAP finding sometimes required a mixture of knowledge: networking fundamentals, HTTP behavior, and security principles. This interconnectedness reinforced what coursework had taught me about the layered nature of security, even if these connections were not always obvious when learning them in separate classes.
8. Evaluation of Internship Outcomes
My first objective was to gain valuable technical knowledge that would support my future career. This goal was partially met because the internship allowed me to learn new tools and approaches, particularly in the area of dynamic application security testing. I developed skills related to OWASP ZAP’s Automation Framework, GitLab CI integration, vulnerability reporting, and API-based automation. These are all relevant to modern security workflows and provided a meaningful foundation for future learning. However, the knowledge gained was more broad than deep. Because I had to work independently and without structured guidance, my learning was shaped mostly by trial and error rather than by a sequenced, cumulative progression of skills. While this increased my resourcefulness, it also limited my ability to explore more advanced topics that would have required mentorship or collaborative development.
My second objective was to understand how agile teams function and how their workflows are structured. This goal was fully met. Although my work was largely independent, participation in daily standups, sprint planning, and sprint reviews offered a meaningful window into how tasks are organized, tracked, and communicated within a cloud development team. Observing others coordinate their workload, share updates, adjust priorities, and engage in troubleshooting discussions made the agile process much more concrete. It helped me understand not only the structure of agile workflows but also the rationale behind them. For example, standups demonstrated how teams maintain visibility into each other’s progress, and sprint reviews illustrated the value of showcasing work for transparency and alignment. Seeing these practices in action strengthened my understanding of teamwork in technical environments and helped me recognize the importance of consistent communication in preventing delays or misalignment.
My third objective, which was to gain hands-on experience with cloud security, was not met. While I gained access to AWS environments late in the internship, the limited timeframe and restricted permissions prevented me from working meaningfully within cloud systems. Much of cloud security involves understanding identity and access management, monitoring resources, applying configuration guardrails, and analyzing cloud-native logs or infrastructure. Without hands-on exposure to these elements, the cloud component of my goal remained largely unfulfilled. This was a notable gap because cloud security is one of the fastest-growing areas in the cybersecurity field, and practical exposure would have complemented the automation and DAST work I completed. While this experience still solidified my interest in cloud security, it highlighted the importance of having structured, permission-ready tasks available for interns at the start of the internship rather than the end.
Beyond the specific objectives, the internship also helped reveal new strengths and interests that were not part of my original goals. Working on the ZAP automation pipeline helped reinforce that I enjoy building security tools, writing automation scripts, and integrating different technologies to solve problems. These discoveries expanded my understanding of where my skills might fit within the cybersecurity workforce. By the end of the internship, I gained clarity that my strengths align well with DevSecOps and cloud security roles, where technical understanding and automation intersect.
On a broader level, evaluating my outcomes highlighted the value of adaptability and self-directed learning. Even though I was not able to meet all my initial goals, I gained skills that will influence my career direction and inform decisions about future certifications or roles. The experience also emphasized the importance of structured support in internship programs. With more guidance, the learning outcomes could have been more comprehensive and more closely aligned with my expectations. Despite these limitations, the internship significantly contributed to my technical readiness, my understanding of agile workflow, and my long-term professional interests.
9. Motivating Aspects of the Internship
One of the most motivating aspects of the internship was the level of independence I was given to explore tools, research solutions, and design an automation workflow from scratch. While the lack of structure created some uncertainty, it also opened the door for a deeper type of learning. Instead of following a predefined checklist, I had to figure out how to approach the problem, break it into manageable steps, and make technical decisions that would directly influence the results. This type of autonomy encouraged creative problem solving and made the experience feel more meaningful. The freedom to design and test a solution without strict constraints allowed me to develop a sense of ownership over the work, which increased my motivation to refine it and understand the tools at a deeper level.
It was also motivating to work on a project that had real value, even if it was ultimately unclear whether the team would adopt it long term. Knowing that the ZAP automation pipeline could help identify vulnerabilities before they reached production made the work feel significant. Security is often a behind-the-scenes function, but contributing something that could reduce risks for the university strengthened my interest in pursuing a technical security role. Watching a scan execute in the pipeline, seeing the HTML and JSON reports generate, and then configuring the script to publish a summary directly to the merge request created a clear visual representation of progress. The automated feedback shown in Appendix C, which displays the passive scan running successfully on a merge request, was especially motivating because it provided clear confirmation that the pipeline was functioning as intended. Each improvement became tangible, and that produced a sense of momentum throughout the internship.
Another source of motivation came from moments of successful debugging. Many of the challenges in this internship required persistence and trial-and-error, especially when working with YAML configurations, GitLab’s API, or pipeline variables. Solving these issues reinforced my confidence and demonstrated that I could handle complex, unfamiliar tools independently. The satisfaction of identifying the issue, testing a solution, and watching the pipeline complete successfully made the learning process feel rewarding. These accomplishments built my confidence in a way that traditional coursework does not always provide.
Participating in daily standups and sprint meetings with the cloud development team was motivating as well, because it provided exposure to how real technical teams communicate and operate. Even though my work was largely independent, being involved in these meetings helped me see the bigger picture and understand how my project aligned with the department’s goals. Observing their workflow and discussions also reinforced that security work plays an important role in development environments, especially in organizations that rely on stable and secure web infrastructure.
Finally, the internship strengthened my commitment to pursuing cloud security or DevSecOps in the future. Having the opportunity to build something from scratch, apply security tools in a real environment, and interact with a development team gave me a concrete understanding of what this career path looks like. This clarity alone was highly motivating, because it confirmed that I enjoy the type of work that involves both development logic and security principles. The experience helped refine my professional direction and increased my motivation to continue building skills in automation, cloud technologies, and secure development practices.
10. Discouraging Aspects of the Internship
Although the internship contained meaningful technical learning, several elements were discouraging and affected the overall quality of the experience. The most notable issue was the absence of structured supervision. After receiving the initial task description, there were no check-ins, feedback loops, or clear expectations for progress. Internships are typically designed to provide consistent mentorship and direction, which helps students transition from academic learning to professional environments. In this case, the lack of ongoing communication created an atmosphere of uncertainty. It became difficult to determine whether the approach I was taking aligned with the department’s needs or whether I should adjust my direction. This uncertainty sometimes overshadowed the progress I was making.
Another discouraging factor was the ambiguity surrounding the purpose and long-term value of the work. While I understood the technical importance of a DAST automation pipeline, it was unclear whether the DTT division planned to adopt the solution into their operational practices. Interns generally benefit from seeing how their work contributes to real organizational outcomes because it reinforces the relevance of what they are learning. The possibility that the tool might not be used reduced the motivational impact of the project. It was challenging to sustain a high level of enthusiasm when it appeared that the outcome might remain purely academic rather than operational.
The limited access to certain systems and environments also contributed to discouragement. Because permissions were restricted, particularly within AWS, I was unable to explore cloud components of the task. This was discouraging because cloud security was one of my original learning objectives. Gaining access to AWS only near the end of the internship meant there was not enough time to pursue meaningful cloud-focused tasks, which prevented me from achieving that part of my goal.
Additionally, the absence of guidance meant that mistakes often required extended troubleshooting without support. While independent problem solving is valuable, having no mentor to validate a direction or offer a second opinion slowed progress and occasionally led to frustration. Instead of receiving timely feedback, I had to rely exclusively on documentation, trial and error, and self-directed research to identify what was going wrong. This forced independence became discouraging when encountering issues related to GitLab pipelines or automation logic that would have been resolved much faster with even minimal supervisory input.
Another discouraging element was the sense of disconnection from the rest of the team’s work. Although I participated in standups and sprint meetings, the work assigned to me did not meaningfully intersect with other ongoing projects. The separation created a feeling of working in isolation rather than being integrated into a team environment. Internships are most impactful when students feel included in a larger effort, but in this case, the lack of interaction with team members outside of meetings made the experience feel more solitary.
Finally, the lack of structure also meant there was no established framework for evaluating whether I met expectations. The absence of a midpoint check-in or end-of-internship review made it difficult to measure my success beyond my own internal assessment. This contributed to a discouraging feeling that my work existed without context or evaluation. While I remained motivated to learn and complete the project, the experience highlighted a gap between independent learning and the kind of structured mentorship that typically defines strong internship programs.
11. Challenging Aspects of the Internship
The most challenging aspect of the internship was navigating the work with minimal direction. Technical challenges such as debugging pipelines, addressing API errors, or configuring scan parameters were manageable once I understood the tools. The more difficult part was interpreting expectations, determining the correct next steps, and producing work that met an unspoken standard.
Learning GitLab from scratch was also demanding. Understanding how to push changes, read pipeline failures, and troubleshoot issues required patience and a willingness to experiment. Some failures were not intuitive, and identifying which part of the configuration caused the problem often required digging through logs and researching documentation. While these challenges ultimately helped me grow, the lack of structured guidance amplified the difficulty of these tasks.
12. Recommendations for Future Interns
Future ODU DTT interns would benefit greatly from setting expectations early. I recommend that students entering this internship request a structured timeline of deliverables, follow up meeting schedules, and clarification on how their work will be used within the department. Interns should advocate for clear objectives and confirm what success looks like for each assigned task.
On the technical side, interns should prepare by strengthening their foundational skills. GitLab basics are essential, especially understanding branches, commits, merge requests, and pipeline execution. Learning Git from the first three chapters of the Pro Git book is a good starting point. Students should also review GitLab CI documentation to understand how YAML-based pipelines are structured and executed. For coding preparation, familiarity with JavaScript frameworks like NodeJS, ExpressJS, or React is helpful because they relate to the technology stack used by the DTT division. Interns should also study the OWASP Top Ten and understand basic web application security concepts to make better sense of vulnerability scanning results. Finally, reviewing open-source security tools that integrate with GitLab can help interns begin their work more confidently.
Strong communication is also important. With limited supervision, interns must independently reach out, ask questions, and maintain momentum. Preparing for self-directed learning and planning independent research time is essential for success in this environment.
13. Conclusion
My internship with Old Dominion University’s Digital Transformation and Technology division provided meaningful exposure to dynamic application security testing, automation, and development workflows. Although certain aspects of the internship lacked structure, the experience strengthened my confidence and technical skill set. Completing hands-on projects, especially the GitLab-integrated ZAP scanning pipeline, allowed me to see how cybersecurity tools fit into real development environments. It also highlighted the importance of human review, thoughtful configuration, and clear communication in security work.
As I approach graduation, the internship reinforces the value of practical experience and the need to continuously refine my technical skills. Although I did not gain the cloud security exposure I initially hoped for, my experience helped clarify my career interests. I now feel motivated to pursue a path in cloud security or DevSecOps, where automation, scanning, and secure development practices intersect. The internship demonstrated that I enjoy building useful tools, solving complex problems, and integrating security into existing workflows.
The experience will influence the remainder of my time at ODU by reinforcing the importance of applying classroom knowledge through hands-on projects, and it will guide my professional path by directing me toward cloud-focused cybersecurity roles. Overall, the internship was a valuable component of my academic and professional development.
References
GitLab. (2024). GitLab CI/CD documentation. https://docs.gitlab.com/ci
National Initiative for Cybersecurity Careers and Studies. (2023). Cybersecurity internships: Building practical experience for entry-level professionals. U.S. Department of Homeland Security. https://niccs.cisa.gov
National Initiative for Cybersecurity Education. (2023). Cybersecurity workforce development resources. National Institute of Standards and Technology. https://www.nist.gov
Old Dominion University. (2024). About ODU. https://odu.edu/about
OWASP Foundation. (2023). OWASP Zed Attack Proxy: Official documentation. https://www.zaproxy.org
Appendix A
DAST Automation Output: GitLab Merge Request Comment
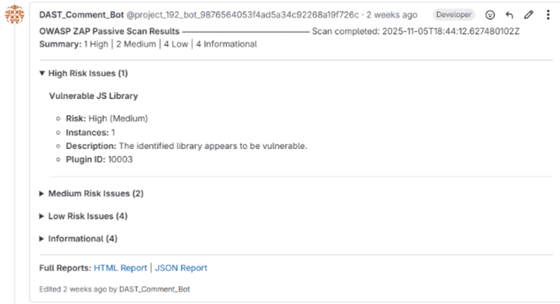
Figure A1: Screenshot of the automated OWASP ZAP merge request comment generated by the CI pipeline.
Appendix B
Snippet of HTML Report from OWASP ZAP Active Scan on Staging Environment
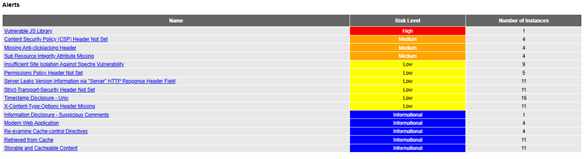
Figure B1: Excerpt from the HTML vulnerability report generated by the active scan executed against the staging site.
Appendix C
Passive Scan Output Automatically Triggered on Each Merge Request
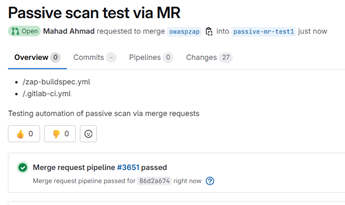
Figure C1: Screenshot of a merge request demonstrating the automated passive scan execution, including the associated pipeline run and confirmation that the passive scan triggered successfully on submission.

Leave a Reply